2020第六届上海市大学生网络安全大赛MISC 复现
链接:https://pan.baidu.com/s/1enmIMnmAGfBC3M4IBHq_hw
提取码:d43k
可乐加冰

用010或pngcheck检测到最后一个IDAT块有问题
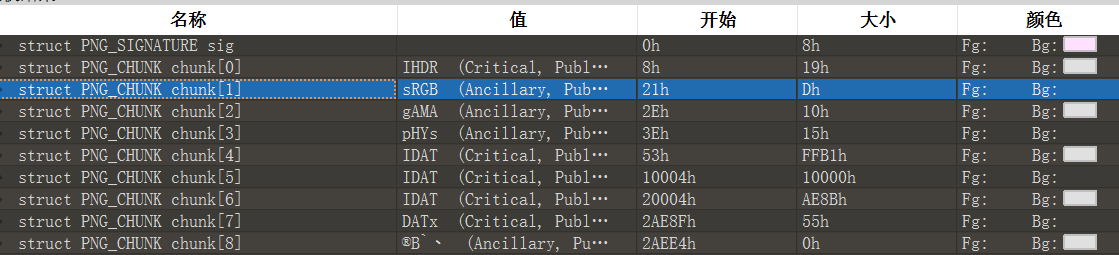
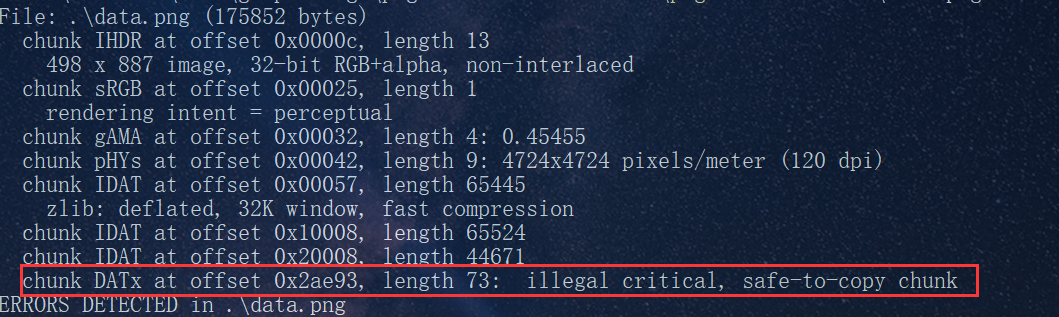
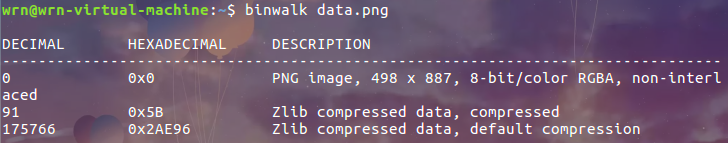
binwak -e提取
其中,2AE96.zlib的16进制是78 9C开头
关于zlib:http://zlib.net/
winhex复制hex,用 python zlibdecompress:
#! /usr/bin/env python2
import zlib
import binascii
IDAT = "789C558EC111C02008049B72AE012736660DDBAF0449800FC7B8B0B89724E65E0259005EDFDE48441BD01CCFF0878BB958B1C38FA9F4532555091F2269C8BABAFEAD6B9B843C6EE000679C4E1C0049454E44AE426082".decode(
'hex')
# print IDAT
result = binascii.hexlify(zlib.decompress(IDAT))
print result
得到:
834636363695438346369595364383469595954383469595364383463636363643834636363695438346369595364383469595364334453443834636953636438346369536954383463636953643834636369543344534438346369595438346369536954383463636363643834636363643344534438346369595364383463695953643834636369543834695363643344534438346363695364383463695369543834636369536438346369595954383469595364383469536954383463636363643834636953643834636369543834695369543834636959543834636369536
10进制转ascii:
with open('test.txt','r') as file:
content = file.read()
for i in range(0,len(content),2):
print(chr(int(content[i:i+2])),end="")
得到:
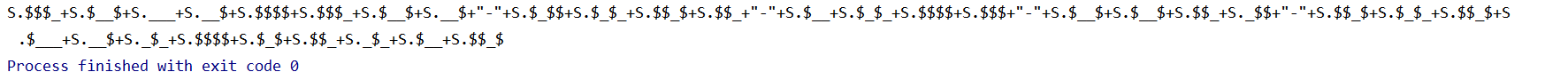
和jjencode长得比较像,S替换为$
把这个copy到jjencode网站给的那段后面,再放控制台运行一下
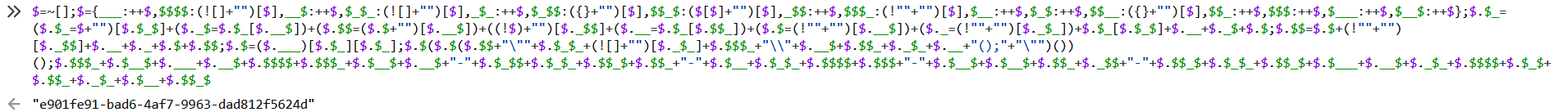
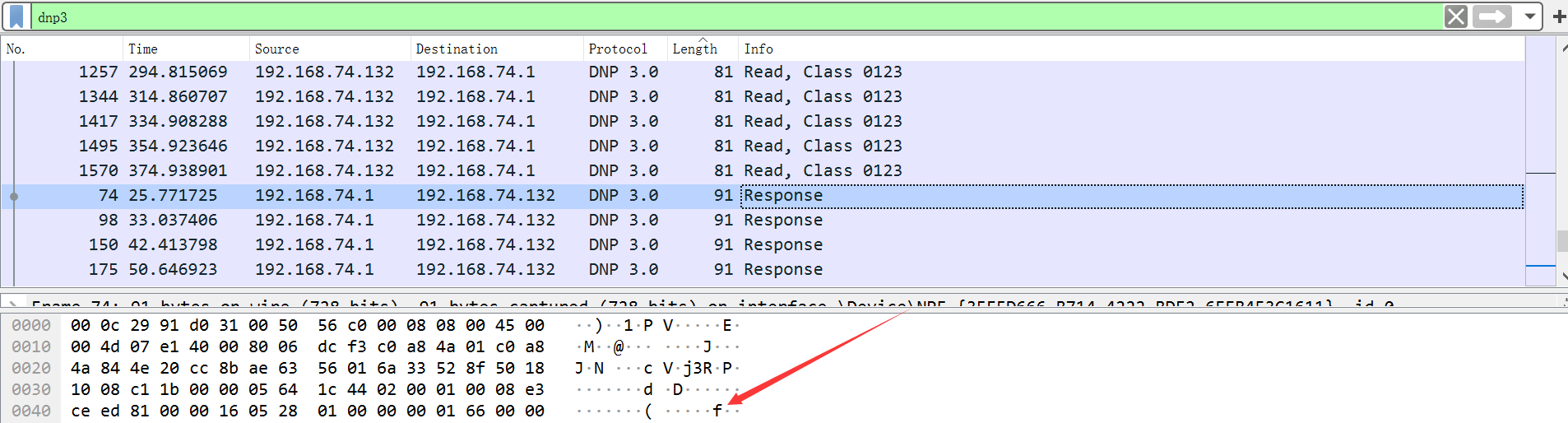
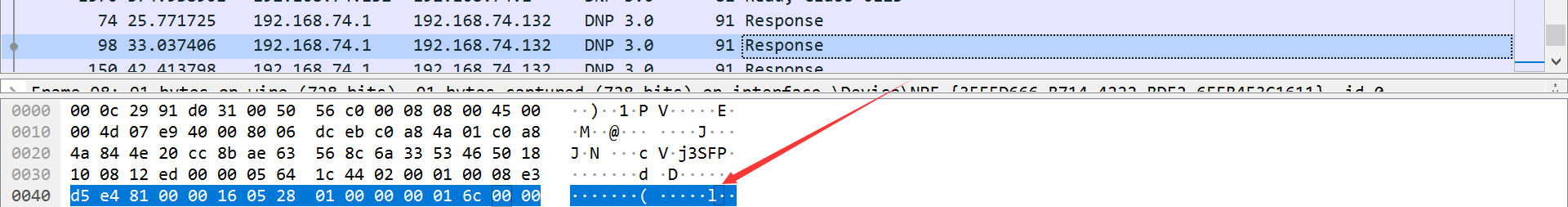
pcap
DNP3协议解析 —— 利用Wireshark对报文逐字节进行解析详细解析Modbus所含功能码
工控安全入门(四)—— DNP3协议
看了看协议结构,对解这俩没有什么用,过滤协议按长度排后也没再看了
仔细观察,在长度为91的response刚好各有一个flag字符。。。