[2020强网杯]记录
👧除了签到签退,只出了3到签到题(https://shimo.im/docs/QTkJYhjrwq8RQqkJ/)
哈哈哈
想着跟大佬们的wp,复现一下miscstudy
miscstudy
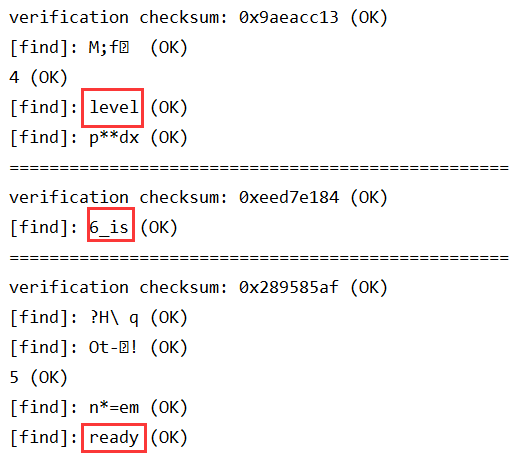
题目说明:本题目flag由7个部分构成,第一个部分为flag{level1...,最后一个部分为 !!!} 每一关都会存有flag的一部分,将所有flag的字符串拼接即为最后flag
👧用wireshark打开就卡死,关闭有道词典,解决!
也过滤http了,就是卡在第一关,哈哈哈,还是
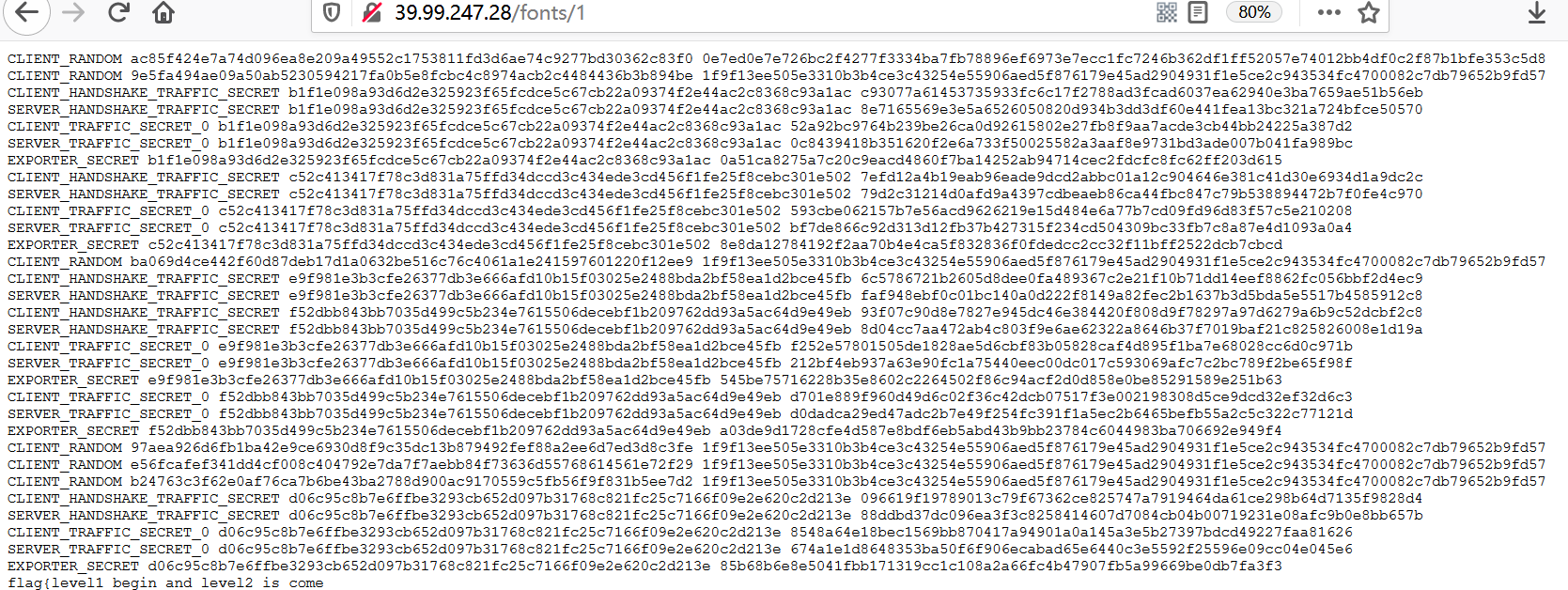
1、过滤http
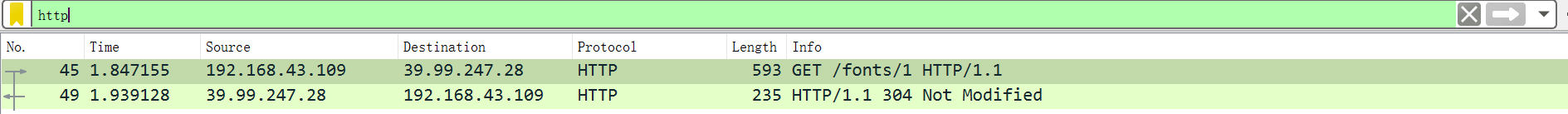
访问http://39.99.247.28/fonts/1
flag{level1_begin_and_level2_is_come
2、
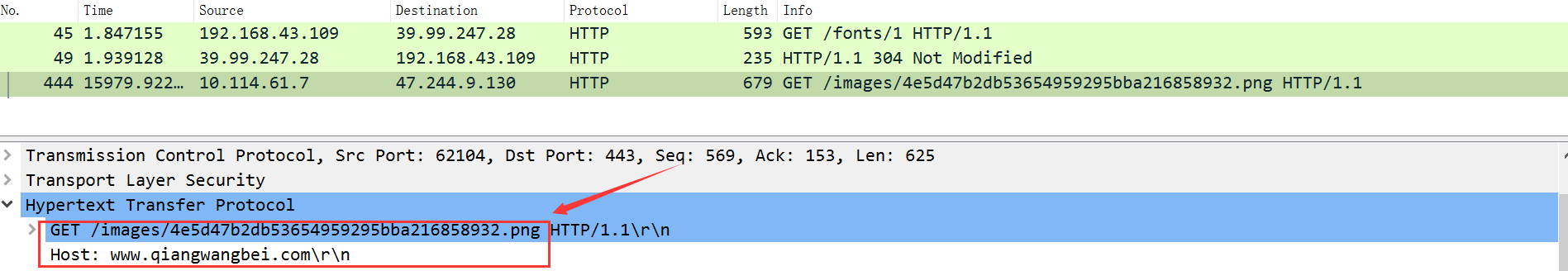
上面是sslkey.log文件,另存为sslkey.log
把sslkey.log导入misc.pcapng:编辑->首选项->Protocols->TLS
此时,多出一条流量
https://www.qiangwangbei.com/images/4e5d47b2db53654959295bba216858932.png
用zsteg命令:
zsteg 4e5d47b2db53654959295bba216858932.png
base64解密,得到3600(60*60)位的2进制和level3_start_it
考虑转二维码,脚本网上有
from PIL import Image
MAX = 60
pic = Image.new("RGB",(MAX, MAX))
str="000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001111111111110000000100110000100000000011100001111111111100001111111111110000000110111000100000000011100001111111111100001100000000110010011111110010000000001100111001000000000100001100000000110010000110110010000000000001111001000000000100001100111100110010000100110010011100000011101001001111100100001100111100110000100000001110011111110010000001001111100100001100111100110000000000001110011110110010000001001111100100001100111100110011100100111111111100110011100000001111100100001100000000110011000000000111100110110110000001000000000100001100000000110010011000000011100011111110011001000000000100001111111111110010011001001001100110110010011001111111111100001111111111110010011001001100000100110010011001111111111100000000000000000010011111110010011000111000100000000000000000000000000000000010001111100010011000011101100000000000000000001110011000111100000001000000011000001111111001111000111000000110000000000000000001000000011000000000011001000000000000000010000001000011100001000000111100110000011000000010000000001110011001111110000000000000010001001110011111000010011000001110011001111110000000000000011001001110011111000010011000001100111000000011111000000010000100000100100111000000100100000001100000000111011000000111000100001100000111000000000000000011100000111110011000001111111100001100011111110010000000000000111001001100000000001100000111001110011111001000100100000000111001001000000000001000000111001110011111001100100100000011100000110011111111000000011100001111111000001110011100000011000000010011111110000000011100001111111000000110001100000000000100000010000000000000011000001110011001000000100100000000000000000110000000000000000000001110011011100000000000000010001001111110000100000000100000011111111101111100000000000011000000001110000000111111100110000001100000000010000000000011100000001110000000111111100111000000100000000010000000001110000100111111111111000000011100111000011000001100000000001111000110001001100111000000011000011100011000000000000000001111100111001100100101111111111001111100001001110011111100001100000111110000100000000010000000111100011000000011100100001000000111110000100000000010000000111000011000000011100100000011011100000011100000000000000001110000011111000001100100000111111100000011000000000000000011100000001101000000100100001111100000110010000100000000011111000010000000001100010000000111100000000010000110000000000000000110000000001100000000000011100100000010011111000011100000001110000000111000100000001100111000111110011111001111111100001010011111111100011000001000111000111110011111001111111100001110011011111100011000000000000000000010011001001110000001110001111000001100000100000000000000000010011000001100000000110000011000001100000100001111111111110010011000111000110000111100011001001100111100001100000000110000111100000011111111001110001000001100111000001100000000110000111100000011111111001110011000001100111000001100111100110000100001000000100001001110011111111100000000001100111100110000100001000001100001001100001111111000000000001100111100110010011000111111111000111110000111000011011100001100111100110000011000110000000000000110000000000011011100001100111100110000011111110000000100001110011000000000011100001100000000110011100100111000011001111100011111111111100000001100000000110011100100111000011001111100011111111111100000001011111111010010011111110011111001001110011111100000011000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000"
i=0
for y in range (0,MAX):
for x in range (0,MAX):
if(str[i] == '1'):
pic.putpixel([x,y],(0, 0, 0))
else:
pic.putpixel([x,y],(255,255,255))
i = i+1
pic.save("res.png")
链接:https://pan.baidu.com/s/1wVJ7d0RLW8Rj-HOTL9Shug
提取码:1lms
3、下载后得到level4.jpg
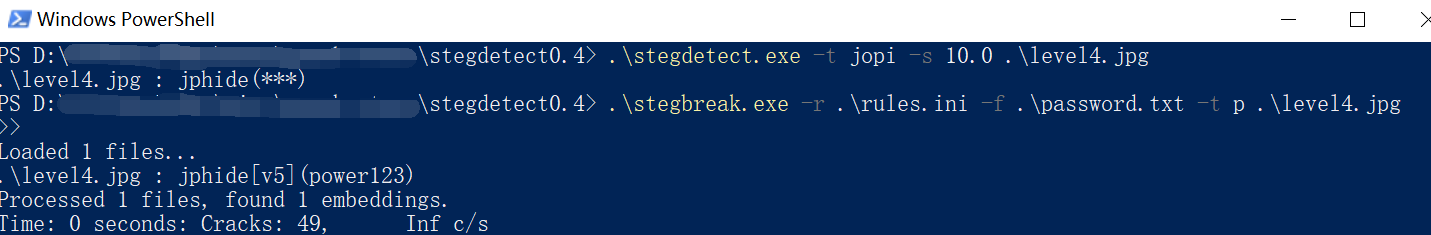
用stegdetect检测到图片是jphide加密(我感觉这工具一般只能检测jphide)
.\stegdetect.exe -t jopi -s 10.0 .\level4.jpg
用stegbreak爆破一下
.\stegbreak.exe -r .\rules.ini -f .\password.txt -t p .\level4.jpg
https://pan.baidu.com/s/1o43y4UGkm1eP-RViC25aOw
mrpt
level4_here_all
4、下载后是leve5.zip(level5.png 1.png level6.zip level7.zip)
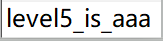
level5.png直接是第5段
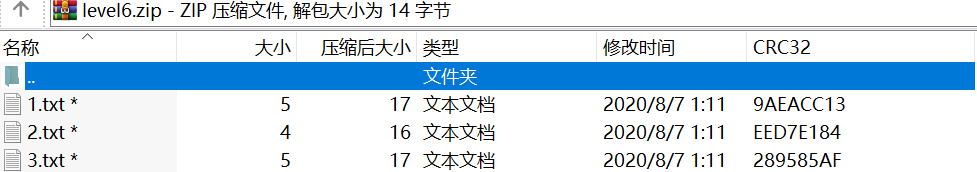
level6.zip
level7.zip(1.png 4.png 5.png)
直接明文攻击(不到一分钟就可以停了),4.png和5.png是一样的,尝试盲水印(py2都没结果,用里面的py3)

得到:level7ishere和39.99.247.28/final_level
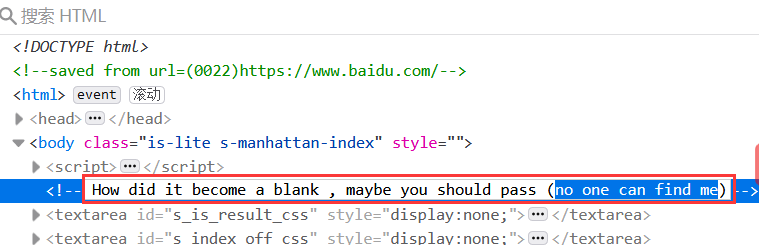
根据提示blank,查看页面源代码,发现前2行有空格和tab,html snow隐写,http://fog.misty.com/perry/ccs/snow/snow/snow.html
the_misc_examaaaaaaa_!!!}
连起来,flag{level1_begin_and_level2_is_comelevel3_start_itlevel4_here_alllevel5_is_aaalevel_isreadylevel7isherethe_misc_examaaaaaaa_!!!}