HUAWEI-防火墙USG6000 与 Windows2008 R2配置IPSec(防火墙篇)
HUAWEI-防火墙USG6000 与 Windows2008 R2配置IPSec(USG篇)
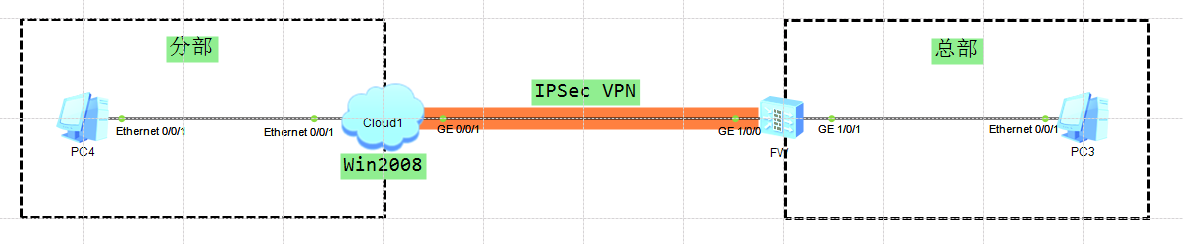
背景说明:某公司想实现总部和分部之间构建一条IPSec实现内部通讯,同时为节约成本不想购置一台用于IPSec的网络设备。于是通过思考使用Windows Server2008 来建立IPSec。实现IPSec的协商构建隧道通信。
IP地址接口规划表:
| 本端设备 | 接口 | IP地址 | 对端设备 | 接口 | IP地址 |
|---|---|---|---|---|---|
| FW | GE 1/0/0 | 202.1.1.2/30 | Win2008 | GE 0/0/1 | 202.1.1.1/30 |
| FW | GE 1/0/1 | 192.168.6.1/24 | PC3 | Ethernet 0/0/1 | 192.168.6.3/24 |
| Win2008 | Ethernet 0/0/1 | 192.168.5.1/24 | PC4 | Ethernet 0/0/1 | 192.168.5.2/24 |
TIPS:华为USG防火墙的GE 0/0/0 接口默认是管理接口,建议在投入使用时是尽量避免作为数据端口。
数据规划:
| 配置项 | 华为USG6000 | Windows Sever 2008 R2 | |
|---|---|---|---|
| IPSEC 安全提议 | 封装模式 | 隧道模式 (Tunnel) | 隧道模式 (Tunnel) |
| 安全协议 | ESP | ESP | |
| ESP协议 验证算法 | SHA1 | SHA1 | |
| ESP协议 加密算法 | 3DES | 3DES | |
| IKE 安全提议 | 身份验证方法 | 预共享密钥 | 预共享密钥 |
| 加密算法 | SHA1 | SHA1 | |
| 认证算法 | 3DES | 3DES | |
| DH Group | GROUP2 | GROUP2 | |
| IKE对等体 | 协商模式 | 主模式 | 主模式 |
| 预共享密钥 | ruankao@huawei | ruankao@huawei | |
| 身份类型 | IP地址 | IP地址 | |
| IKE版本 | V1 | V1 |
防火墙配置步骤:
项目实施:
一、配置接口IP地址,并将接口加入安全区域
- 配置接口地址
[USG6000V1]interface GigabitEthernet1/0/0
[USG6000V1-GigabitEthernet1/0/0] ip address 202.1.1.2 255.255.255.252
#
[USG6000V1-GigabitEthernet1/0/0]interface GigabitEthernet1/0/1
[USG6000V1-GigabitEthernet1/0/1] ip address 192.168.6.1 255.255.255.0
- 配置接口安全区域
[USG6000V1] firewall zone trust
[USG6000V1-zone-trust] add interface GigabitEthernet1/0/1
#
[USG6000V1-zone-trust]firewall zone untrust
[USG6000V1-zone-untrust] add interface GigabitEthernet1/0/0
二、配置去往Internet的缺省路由
[USG6000V1]ip route-static 0.0.0.0 0.0.0.0 202.1.1.1
三、配置域间安全策略
[USG6000V1]security-policy
#
[USG6000V1-policy-security] rule name ipsec-polic-out
[USG6000V1-policy-security-rule-ipsec-polic-out]source-zone trust
[USG6000V1-policy-security-rule-ipsec-polic-out]destination-zone untrust
[USG6000V1-policy-security-rule-ipsec-polic-out]source-address 192.168.6.3 mask 255.255.255.255
[USG6000V1-policy-security-rule-ipsec-polic-out]destination-address 192.168.5.2 mask 255.255.255.255
[USG6000V1-policy-security-rule-ipsec-polic-out]action permit
#
[USG6000V1-policy-security-rule-ipsec-polic-out]rule name ipsec-policy-in
[USG6000V1-policy-security-rule-ipsec-policy-in]source-zone untrust
[USG6000V1-policy-security-rule-ipsec-policy-in]destination-zone trust
[USG6000V1-policy-security-rule-ipsec-policy-in]source-address 192.168.5.2 mask 255.255.255.255
[USG6000V1-policy-security-rule-ipsec-policy-in]destination-address 192.168.6.3 mask 255.255.255.255
[USG6000V1-policy-security-rule-ipsec-policy-in]action permit
#
[USG6000V1-policy-security-rule-ipsec-policy-in]rule name ike-policy-out
[USG6000V1-policy-security-rule-ike-policy-out]source-zone local
[USG6000V1-policy-security-rule-ike-policy-out]destination-zone untrust
[USG6000V1-policy-security-rule-ike-policy-out]source-address 202.1.1.2 mask 255.255.255.255
[USG6000V1-policy-security-rule-ike-policy-out]destination-address 202.1.1.1 mask 255.255.255.255
[USG6000V1-policy-security-rule-ike-policy-out]action permit
#
[USG6000V1-policy-security-rule-ike-policy-out]rule name ike-policy-in
[USG6000V1-policy-security-rule-ike-policy-in]source-zone untrust
[USG6000V1-policy-security-rule-ike-policy-in]destination-zone local
[USG6000V1-policy-security-rule-ike-policy-in]source-address 202.1.1.1 mask 255.255.255.255
[USG6000V1-policy-security-rule-ike-policy-in]destination-address 202.1.1.2 mask 255.255.255.255
[USG6000V1-policy-security-rule-ike-policy-in]action permit
四、定义需要保护的数据流、配置IPSec安全提议
[USG6000V1]acl 3000
[USG6000V1-acl-adv-3000]rule 5 permit ip source 192.168.6.3 0 destination 192.168.5.2 0
#
[USG6000V1]ipsec proposal FW-win2008
[USG6000V1-ipsec-proposal-FW-win2008]encapsulation-mode tunnel
[USG6000V1-ipsec-proposal-FW-win2008]transform esp
[USG6000V1-ipsec-proposal-FW-win2008]esp authentication-algorithm sha1
[USG6000V1-ipsec-proposal-FW-win2008]esp encryption-algorithm 3des
五、创建IKE安全提议、配置IKE对等体
[USG6000V1]ike proposal 10
[USG6000V1-ike-proposal-10]authentication-method pre-share
[USG6000V1-ike-proposal-10]encryption-algorithm 3des
Warning: The security level of des/3des is low.
[USG6000V1-ike-proposal-10] dh group2
Warning: The security level of group1/group2/group5 is low.
[USG6000V1-ike-proposal-10] authentication-algorithm sha1
Warning: The security level of md5/sha1 is low.
#
[USG6000V1]ike peer win2008
[USG6000V1-ike-peer-win2008]undo version 2
[USG6000V1-ike-peer-win2008]exchange-mode main
[USG6000V1-ike-peer-win2008]pre-shared-key ruankao@huawei
[USG6000V1-ike-peer-win2008]ike-proposal 10
[USG6000V1-ike-peer-win2008]remote-address 202.1.1.1
六、配置IPSec策略,在接口上应用IPSec策略
[USG6000V1]ipsec policy map1 10 isakmp
[USG6000V1-ipsec-policy-isakmp-map1-10]ipsec policy map1 10 isakmp
[USG6000V1-ipsec-policy-isakmp-map1-10]security acl 3000
[USG6000V1-ipsec-policy-isakmp-map1-10]ike-peer win2008
[USG6000V1-ipsec-policy-isakmp-map1-10]proposal FW-win2008
#
[USG6000V1]int GigabitEthernet 1/0/0
[USG6000V1-GigabitEthernet1/0/0] ipsec policy map1
项目验证:
接口安全区域验证:
[USG6000V1]dis zone
2022-05-01 01:30:37.180
local
priority is 100
interface of the zone is (0):
#
trust
priority is 85
interface of the zone is (2):
GigabitEthernet0/0/0
GigabitEthernet1/0/1
#
untrust
priority is 5
interface of the zone is (1):
GigabitEthernet1/0/0
#
dmz
priority is 50
interface of the zone is (0):
#
IKE-SA(安全联盟)验证:
[USG6000V1]dis ike sa
2022-04-30 16:25:35.160
IKE SA information :
Conn-ID Peer VPN Flag(s Phase RemoteType RemoteID
------------------------------------------------------------------------------------------------------------------------------------
8 202.1.1.1:500 RD|A v1:1 IP 202.1.1.1
Number of IKE SA : 1
--------------------------------------------------------------------------------
----------------------------------------------------
Flag Description:
RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT
HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP
M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING
IPSec-SA(安全联盟)验证:
[USG6000V1]dis ipsec sa
2022-04-30 14:22:23.630
ipsec sa information:
===============================
Interface: GigabitEthernet1/0/0
===============================
-----------------------------
IPSec policy name: "map1"
Sequence number : 10
Acl group : 3000
Acl rule : 5
Mode : ISAKMP
-----------------------------
Connection ID : 5
Encapsulation mode: Tunnel
Holding time : 0d 3h 27m 19s
Tunnel local : 202.1.1.2:500
Tunnel remote : 202.1.1.1:500
Flow source : 192.168.6.3/255.255.255.255 0/0-65535
Flow destination : 192.168.5.2/255.255.255.255 0/0-65535
[Outbound ESP SAs]
SPI: 197255367 (0xbc1e0c7)
Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128
SA remaining key duration (kilobytes/sec): 10485760/883
Max sent sequence-number: 1
UDP encapsulation used for NAT traversal: N
SA encrypted packets (number/bytes): 0/0
[Inbound ESP SAs]
SPI: 193813908 (0xb8d5d94)
Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128
SA remaining key duration (kilobytes/sec): 10485760/883
Max received sequence-number: 1
UDP encapsulation used for NAT traversal: N
SA decrypted packets (number/bytes): 0/0
Anti-replay : Enable
Anti-replay window size: 1024
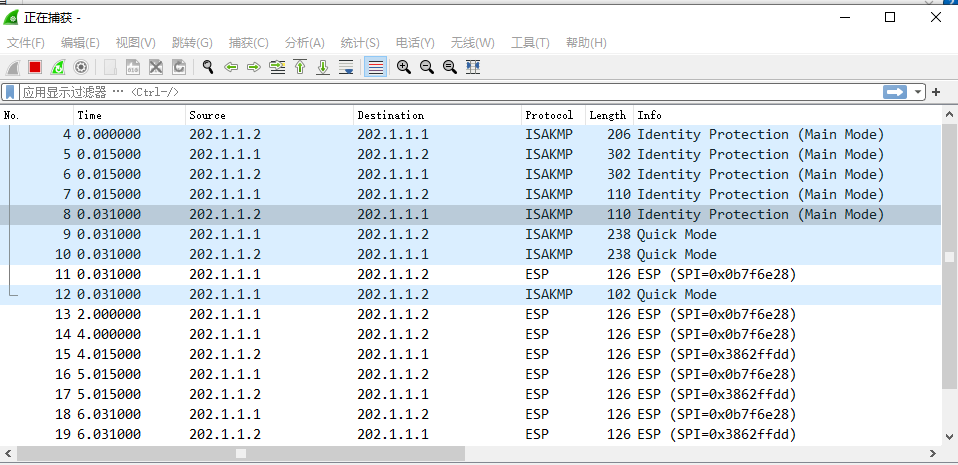
抓包验证协商过程和数据加密: