Huawei-FW+AC-AP+Eth-Trunk 实验配置
FW+AC-AP+Eth-Trunk 实验配置
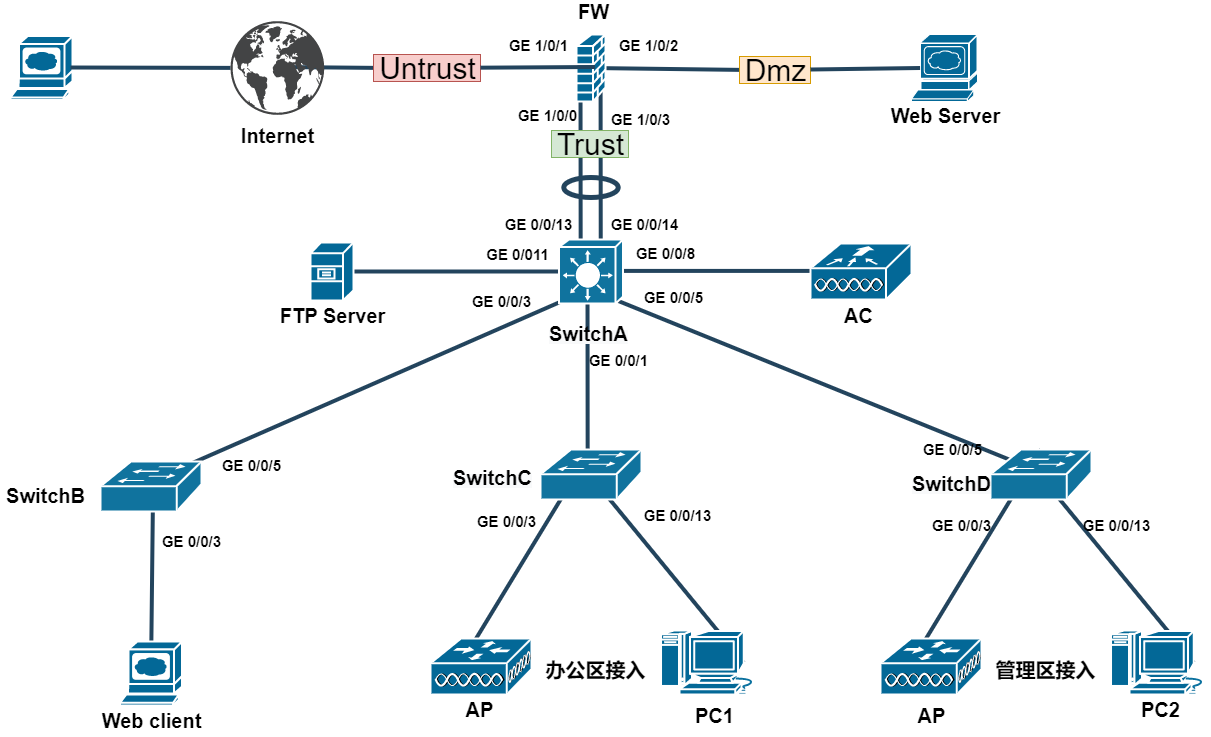
项目说明:某司内部使用防火墙过滤内网和外网的通信,某司内部搭建网站服务器,使用NAT Server对外发布官方网站。由于业务的需要,配置防火墙的NAT功能,实现内部网络访问互联网。内网核心交换机SwitchA和出口防火墙配置Eth-Trunk保证链路的可靠性同时增加带宽,配置AC无线控制器,实现AP上线实现双wlan。使用ACL过滤特定的流量。
VLAN规划表
| VLAN | 描述 |
|---|---|
| 100 | 无线管理VLAN |
| 101 | 访客无线业务VLAN |
| 102 | 员工无线业务VLAN |
| 103 | 员工有线业务VLAN |
| 104 | Web client的VLAN |
| 105 | AP所属VLAN |
| 107 | 对接上行防火墙VLAN |
| 108 | FTP接入VLAN |
IP地址接口规划表
| 本端设备 | 端口 | IP地址 | 对端设备 | 端口 | IP地址或VLKAN |
|---|---|---|---|---|---|
| FW | GE 1/0/1 | 109.1.1.1/27 | Internet | 未知 | 109.1.1.2/27 |
| FW | GE 1/0/2 | 10.106.1.1/24 | Web Server | Ethernet0/0/0 | 10.106.1.200/24 |
| FW | Eth-Trunk1 | 10.107.1.2/24 | SwitchA | Eth-Trunk1 | VLANif107:10.107.1.1/24 |
| SwitchA | GE 0/0/1 | VLANif 101:10.101.1.1/24 | SwitchC | GE 0/0/1 | VLAN 101 |
| GE 0/0/1 | VALNif 102:10.102.1.1/24 | GE 0/0/1 | VLAN 102 | ||
| GE 0/0/1 | VALNif 103:10.103.1.1/24 | GE 0/0/1 | VLAN 103 | ||
| GE 0/0/1 | VALNif 105:10.105.1.1/24 | GE 0/0/1 | VLAN 105 | ||
| SwitchA | GE 0/0/3 | VLANif 104:10.104.1.1/24 | SwitchB | GE 0/0/5 | VLAN 104 |
| SwitchA | GE 0/0/5 | VLAN 101、102、103、105 | SwitchD | GE 0/0/5 | VLAN 101、102、103、105 |
| SwitchA | GE 0/0/8 | VLANif 100:10.100.1.1/24 | AC | GE 0/0/3 | VLANif 100:10.100.1.2/24 |
| SwitchA | GE 0/0/11 | VLANif 108:10.108.1.1/24 | FTP Server | Ethernet0/0/0 | 10.108.1.100/24 |
| SwitchB | GE 0/0/3 | VLAN 104 | Web client | Ethernet0/0/0 | 10.104.1.10/24 |
| SwitchC | GE 0/0/3 | VLAN 101、102、105 | AP | GE 0/0/0 | DHCP-获取 |
| SwitchC | GE 0/0/13 | VLAN 103 | PC1 | Ethernet0/0/0 | DHCP-获取 |
| SwitchD | GE 0/0/3 | VLAN 101、102、105 | AP | GE 0/0/0 | DHCP-获取 |
| SwitchD | GE 0/0/13 | VLAN 103 | PC2 | Ethernet0/0/0 | DHCP-获取 |
配置思路
项目实施
一、配置各接口IP地址或所属VLAN
#配置防火墙,同时配置链路聚合(LACP模式)
[USG6000V1]firewall zone untrust
[USG6000V1-zone-untrust]add interface GigabitEthernet 1/0/1
[USG6000V1-zone-untrust]quit
[USG6000V1]interfaceGigabitEthernet1/0/1
[USG6000V1-GigabitEthernet1/0/1]ip address 109.1.1.1 255.255.255.0
#
[USG6000V1]firewall zone dmz
[USG6000V1-zone-dmz]add interface GigabitEthernet1/0/2
[USG6000V1-zone-dmz]quit
[USG6000V1]interface GigabitEthernet 1/0/2
[USG6000V1-GigabitEthernet1/0/2]ip address 10.106.1.1 255.255.255.0
#
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]add interface Eth-Trunk 1
[USG6000V1-zone-trust]quit
[USG6000V1]interface Eth-Trunk 1 #创建逻辑接口Eth-trunk1,组成聚合组
[USG6000V1-Eth-Trunk1]mode lacp-static #配置模式为静态LACP模式
[USG6000V1-Eth-Trunk1]trunkport GigabitEthernet 1/0/0 1/0/3 #添加端口
[USG6000V1-Eth-Trunk1]ip address 10.107.1.2 255.255.255.0
#
[USG6000V1]lacp priority 30000 #配置LACP系统优先级,使其成为主动端
#配置核心交换机SwitchA,同时配置链路聚合(LACP模式)
[SwitchA]vlan batch 100 101 102 103 104 105 107 108
Info: This operation may take a few seconds. Please wait for a moment...done.
#
[SwitchA]interface vlan 101
[SwitchA-Vlanif101] ip address 10.101.1.1 24
#
[SwitchA-Vlanif101]interface vlan 102
[SwitchA-Vlanif102] ip address 10.102.1.1 24
#
[SwitchA-Vlanif102]interface vlan 103
[SwitchA-Vlanif103] ip address 10.103.1.1 24
#
[SwitchA-Vlanif103]interface vlan 104
[SwitchA-Vlanif104] ip address 10.104.1.1 24
#
[SwitchA-Vlanif104]interface vlan 105
[SwitchA-Vlanif105] ip address 10.105.1.1 24
#
[SwitchA-Vlanif105]interface vlan 107
[SwitchA-Vlanif107] ip address 10.107.1.1 24
#
[SwitchA-Vlanif107]interface vlan 108
[SwitchA-Vlanif108] ip address 10.108.1.1 24
#
[SwitchA]interface g0/0/1
[SwitchA-GigabitEthernet0/0/1] port link-type trunk
[SwitchA-GigabitEthernet0/0/1] port trunk allow-pass vlan 101 102 103 105
#
[SwitchA-GigabitEthernet0/0/1]interface g0/0/3
[SwitchA-GigabitEthernet0/0/3] port link-type trunk
[SwitchA-GigabitEthernet0/0/3]port trunk allow-pass vlan 104
#
[SwitchA-GigabitEthernet0/0/3]interface g0/0/5
[SwitchA-GigabitEthernet0/0/5] port link-type trunk
[SwitchA-GigabitEthernet0/0/5] port trunk allow-pass vlan 101 102 103 105
#
[SwitchA-GigabitEthernet0/0/5]interface g0/0/8
[SwitchA-GigabitEthernet0/0/8] port link-type trunk
[SwitchA-GigabitEthernet0/0/8] port trunk allow-pass vlan 100
#
[SwitchA-GigabitEthernet0/0/8]interface g0/0/11
[SwitchA-GigabitEthernet0/0/11] port link-type access
[SwitchA-GigabitEthernet0/0/11] port default vlan 108
#
[SwitchA-GigabitEthernet0/0/11]int eth-trunk 1 #创建逻辑接口Eth-trunk1,组成聚合组
[SwitchA-Eth-Trunk1]mode lacp-static #配置模式为静态LACP模式
[SwitchA-Eth-Trunk1]trunkport GigabitEthernet 0/0/13 0/0/14 #添加端口
[SwitchA-Eth-Trunk1]port link-type access
[SwitchA-Eth-Trunk1]port default vlan 107
#配置AC无线控制器
[AC6005]vlan 100
[AC6005-vlan100]quit
[AC6005]int vlan 100
[AC6005-Vlanif100]ip address 10.100.1.2 255.255.255.0
#
[AC6005-Vlanif100]interface GigabitEthernet0/0/3
[AC6005-GigabitEthernet0/0/3]port link-type trunk
[AC6005-GigabitEthernet0/0/3]port trunk allow-pass vlan 100
#配置SwitchB
[SwitchB]vlan 104
#
[SwitchB-vlan104]int g0/0/3
[SwitchB-GigabitEthernet0/0/3] port link-type access
[SwitchB-GigabitEthernet0/0/3] port default vlan 104
#
[SwitchB-GigabitEthernet0/0/3]int g0/0/5
[SwitchB-GigabitEthernet0/0/5] port link-type trunk
[SwitchB-GigabitEthernet0/0/5] port trunk allow-pass vlan 104
#配置SwitchC and SwitchD
[SwitchC]vlan batch 101 102 103 105
Info: This operation may take a few seconds. Please wait for a moment...done.
[SwitchC]int g0/0/3
[SwitchC-GigabitEthernet0/0/3] port link-type trunk
[SwitchC-GigabitEthernet0/0/3] port trunk allow-pass vlan 101 102 105
[SwitchC-GigabitEthernet0/0/3] port trunk pvid vlan 105
#
[SwitchC-GigabitEthernet0/0/3]int g0/0/5
[SwitchC-GigabitEthernet0/0/5] port link-type trunk
[SwitchC-GigabitEthernet0/0/5] port trunk allow-pass vlan 101 102 103 105
#
[SwitchC-GigabitEthernet0/0/5]int g0/0/13
[SwitchC-GigabitEthernet0/0/13] port link-type access
[SwitchC-GigabitEthernet0/0/13] port default vlan 103
[SwitchD]vlan batch 101 102 103 105
Info: This operation may take a few seconds. Please wait for a moment...done.
#
[SwitchD]int g0/0/3
[SwitchD-GigabitEthernet0/0/3] port link-type trunk
[SwitchD-GigabitEthernet0/0/3] port trunk allow-pass vlan 101 102 105
[SwitchD-GigabitEthernet0/0/3] port trunk pvid vlan 105
#
[SwitchD-GigabitEthernet0/0/3]int g0/0/5
[SwitchD-GigabitEthernet0/0/5] port link-type trunk
[SwitchD-GigabitEthernet0/0/5] port trunk allow-pass vlan 101 102 103 105
#
[SwitchD-GigabitEthernet0/0/5]int g0/0/13
[SwitchD-GigabitEthernet0/0/13] port link-type access
[SwitchD-GigabitEthernet0/0/13] port default vlan 103
二、配置防火墙策略实现过滤和nat功能
#配置防火墙安全策略实现流量过滤
#配置内网(trust区域)访问外网(untrust区域)的安全策略
[USG6000V1]security-policy
[USG6000V1-policy-security]rule name trust-untrust
[USG6000V1-policy-security-rule-trust-untrust]source-zone trust
[USG6000V1-policy-security-rule-trust-untrust]destination-zone untrust
[USG6000V1-policy-security-rule-trust-untrust]action permit
#配置Webclient和dmz区域服务器之间的互访策略
[USG6000V1-policy-security]rule name dmz-trust_web
[USG6000V1-policy-security-rule-dmz-trust_web]source-zone dmz
[USG6000V1-policy-security-rule-dmz-trust_web]source-zone trust
[USG6000V1-policy-security-rule-dmz-trust_web]destination-zone dmz
[USG6000V1-policy-security-rule-dmz-trust_web]destination-zone trust
[USG6000V1-policy-security-rule-dmz-trust_web]source-address 10.104.1.0 mask 255.255.255.0
[USG6000V1-policy-security-rule-dmz-trust_web]source-address 10.106.1.0 mask 255.255.255.0
[USG6000V1-policy-security-rule-dmz-trust_web]destination-address 10.104.1.0 mask 255.255.255.0
[USG6000V1-policy-security-rule-dmz-trust_web]destination-address 10.106.1.0 mask 255.255.255.0
[USG6000V1-policy-security-rule-dmz-trust_web]action permit
#配置外网访问dmz区域服务器的策略
[USG6000V1-policy-security] rule name untrust-dmz
[USG6000V1-policy-security-rule-untrust-dmz]source-zone untrust
[USG6000V1-policy-security-rule-untrust-dmz]destination-zone dmz
[USG6000V1-policy-security-rule-untrust-dmz]destination-address 10.106.1.0 mask 255.255.255.0
[USG6000V1-policy-security-rule-untrust-dmz]action permit
#配置nat-policy实现内外网的转换
[USG6000V1]nat address-group trust-untrust 19 #配置nat地址此
[USG6000V1-address-group-trust-untrust]section 109.1.1.5 109.1.1.10 #配置地址范围
#
[USG6000V1-policy-nat] rule name trust-untrust
[USG6000V1-policy-nat-rule-trust-untrust]source-zone trust
[USG6000V1-policy-nat-rule-trust-untrust]destination-zone untrust
[USG6000V1-policy-nat-rule-trust-untrust]source-address 10.96.0.0 mask 255.240.0.0
[USG6000V1-policy-nat-rule-trust-untrust]action source-nat address-group trust-untrust
#配置路由黑洞,避免FW和ISP之间路由环路
[USG6000V1]ip route-static 109.1.1.5 32 NULL 0
[USG6000V1]ip route-static 109.1.1.6 32 NULL 0
[USG6000V1]ip route-static 109.1.1.7 32 NULL 0
[USG6000V1]ip route-static 109.1.1.8 32 NULL 0
[USG6000V1]ip route-static 109.1.1.9 32 NULL 0
[USG6000V1]ip route-static 109.1.1.10 32 NULL 0
#配置NATServer实现对外映射公司网站
[USG6000V1]nat server 80 protocol tcp global 109.1.1.15 www inside 10.106.1.200 www unr-route
三、配置静态路由实现网络互通
#配置防火墙静态路由
[USG6000V1]ip route-static 0.0.0.0 0.0.0.0 109.1.1.2
[USG6000V1]ip route-static 10.96.0.0 255.240.0.0 10.107.1.1
#配置核心交换机SwitchA静态路由
[SwitchA]ip route-static 0.0.0.0 0.0.0.0 10.107.1.2
#配置AC无线控制器静态路由
[AC6005]ip route-static 0.0.0.0 0.0.0.0 10.100.1.1
四、配置DHCP服务,下发option和地址。
#SwitchA的DHCP配置
[SwitchA]dhcp enable
#
[SwitchA]ip pool vlan103-work
[SwitchA-ip-pool-vlan103-work]gateway-list 10.103.1.1
[SwitchA-ip-pool-vlan103-work] network 10.103.1.0 mask 255.255.255.0
[SwitchA-ip-pool-vlan103-work]interface Vlanif 103
[SwitchA-Vlanif103]dhcp select global
#
[SwitchA]ip pool ap-work
Info:It's successful to create an IP address pool.
[SwitchA-ip-pool-ap-work]network 10.105.1.0 mask 255.255.255.0 #配置网段和掩码
[SwitchA-ip-pool-ap-work]gateway-list 10.105.1.1 #配置网关
[SwitchA-ip-pool-ap-work]option 43 sub-option 2 ip-address 10.100.1.2 #配置option43字段,使AP通过单播发现AC
[SwitchA-ip-pool-ap-work]interface Vlanif 105
[SwitchA-Vlanif105] dhcp select global #引用全局地址池
#
[SwitchA]ip pool vs-wlan
Info:It's successful to create an IP address pool.
[SwitchA-ip-pool-vs-wlan]network 10.101.1.0 mask 24
[SwitchA-ip-pool-vs-wlan]gateway-list 10.101.1.1
[SwitchA-ip-pool-vs-wlan]interface Vlanif 101
[SwitchA-Vlanif101]dhcp select global
#
[SwitchA]ip pool work-wlan
Info:It's successful to create an IP address pool.
[SwitchA-ip-pool-work-wlan]
[SwitchA-ip-pool-work-wlan]network 10.102.1.0 mask 24
[SwitchA-ip-pool-work-wlan]gateway-list 10.102.1.1
[SwitchA-ip-pool-work-wlan]int vlan 102
[SwitchA-Vlanif102]dhcp select global
五、配置AC无线控制器,实现AP上线下发WLAN
#AC配置AP组,将AP集中管理。
[AC6005]wlan
[AC6005-wlan-view]ap-group name FLOW
#配置无线信号发射标准符合当前国家规定,配置国家代码(可选)
[AC6005-wlan-view]regulatory-domain-profile name CN #配置监管域名提议
[AC6005-wlan-regulate-domain-CN]country-code CN #配置国家代码,限制AP信号发射强度符合设定国家标准
Info: The current country code is same with the input country code.
[AC6005-wlan-view]ap-group name FLOW
[AC6005-wlan-ap-group-FLOW]regulatory-domain-profile CN #应用监管域名提议
Warning: Modifying the country code will clear channel, power and antenna gain configurations of the radio and reset the AP. Continue?[Y/N]:Y
#AC配置CAPWAP,定义发现AP的VLAN接口
#[AC6005]capwap source interface vlanif100
#配置AP上线
[AC6005-wlan-view]ap auth-mode mac-auth #配置AP的认证模式为MAC,其他模式有SN码和无认证
[AC6005-wlan-view]ap-id 1 ap-mac HHHH-HHHH-HHHH
[AC6005-wlan-ap-1]ap-name office #配置AP的名称
[AC6005-wlan-ap-1]ap-group FLOW #将AP添加入AP组
Warning: This operation may cause AP reset. If the country code changes, it will
clear channel, power and antenna gain configurations of the radio, Whether to c
ontinue? [Y/N]:y
Info: This operation may take a few seconds. Please wait for a moment.. done.
#
[AC6005-wlan-view]ap-id 2 ap-mac HHHH-HHHH-HHHH
[AC6005-wlan-ap-1]ap-name manage #配置AP的名称
[AC6005-wlan-ap-1]ap-group FLOW #将AP添加入AP组
Warning: This operation may cause AP reset. If the country code changes, it will
clear channel, power and antenna gain configurations of the radio, Whether to c
ontinue? [Y/N]:y
Info: This operation may take a few seconds. Please wait for a moment.. done.
#配置双WLAN策略
[AC6005-wlan-view] ssid-profile name VS-wlan #配置SSID提议
[AC6005-wlan-ssid-prof-VS-wlan]ssid VS #配置SSID名称
[AC6005-wlan-ssid-prof-VS-wlan] ssid-profile name work-wlan #配置SSID提议
[AC6005-wlan-ssid-prof-work-wlan]ssid work-dd #配置SSID名称
#
[AC6005-wlan-view]security-profile name VS-wlan #配置安全提议
[AC6005-wlan-sec-prof-VS-wlan]security wpa-wpa2 psk pass-phrase huawei@123 aes #配置wlan的密码和相关安全协议
Warning: This action may cause service interruption. Continue?[Y/N]y
Info: This operation may take a few seconds, please wait.done.
[AC6005-wlan-sec-prof-VS-wlan] security-profile name work-wlan #配置安全提议
[AC6005-wlan-sec-prof-work-wlan]security wpa-wpa2 psk pass-phrase huawei@456 aes #配置wlan的密码和相关安全协议
Warning: This action may cause service interruption. Continue?[Y/N]y
Info: This operation may take a few seconds, please wait.done.
#
[AC6005-wlan-view]vap-profile name VS-wlan #创建指定VAP模板,用于射频
[AC6005-wlan-vap-prof-VS-wlan]service-vlan vlan-id 101 #指定业务VLAN,用于下发地址
Info: This operation may take a few seconds, please wait...done.
[AC6005-wlan-vap-prof-VS-wlan]ssid-profile VS-wlan #应用SSID提议
[AC6005-wlan-vap-prof-VS-wlan]security-profile VS-wlan #应用安全提议
[AC6005-wlan-vap-prof-VS-wlan]vap-profile name work-wlan #创建指定VAP模板,用于射频
[AC6005-wlan-vap-prof-work-wlan]service-vlan vlan-id 102 #指定业务VLAN,用于下发地址
Info: This operation may take a few seconds, please wait...done.
[AC6005-wlan-vap-prof-work-wlan]ssid-profile work-wlan #应用SSID提议
[AC6005-wlan-vap-prof-work-wlan]security-profile work-wlan #应用安全提议
#
[AC6005-wlan-view]ap-group name FLOW
[AC6005-wlan-ap-group-FLOW]vap-profile VS-wlan wlan 1 radio all #应用VAP模板
[AC6005-wlan-ap-group-FLOW]vap-profile work-wlan wlan 6 radio all #应用VAP模板
六、配置ACL访问控制列表,管控内网流量
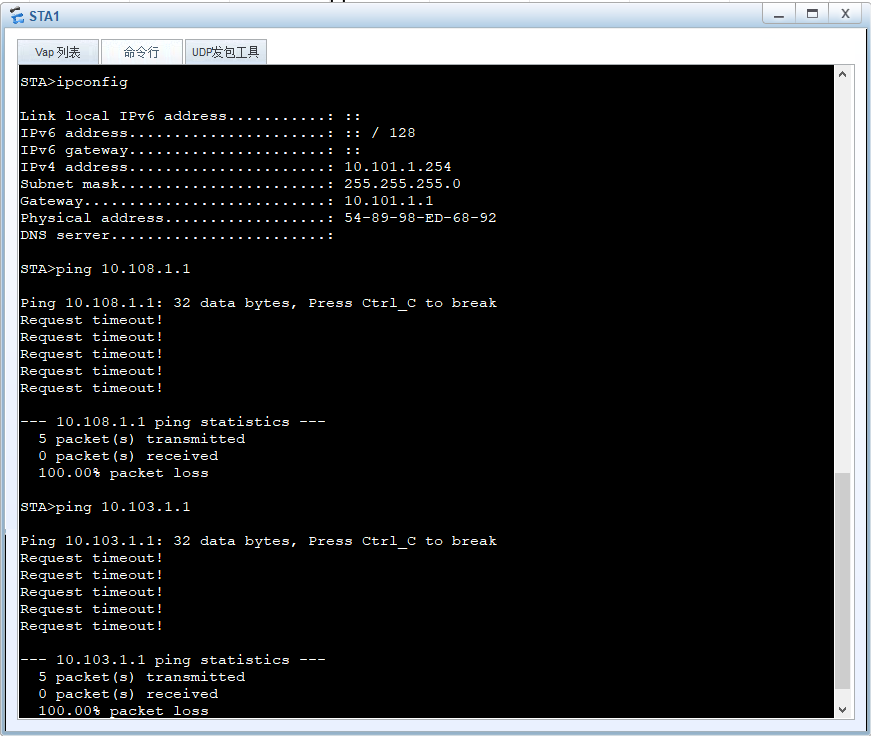
#配置ACL使无线访客止访问业务服务器区和员工有线网络
[SwitchA]acl 3101
[SwitchA-acl-adv-3101] rule 5 deny ip source 10.101.1.0 0.0.0.255 destination 10.108.1.0 0.0.0.255
[SwitchA-acl-adv-3101] rule 10 deny ip source 10.101.1.0 0.0.0.255 destination 10.103.1.0 0.0.0.255
[SwitchA-acl-adv-3101]quit
#
[SwitchA]traffic-filter vlan 101 inbound acl 3101
#配置web client只能于DMZ区的Web服务器互访
[SwitchA]acl number 3104
[SwitchA-acl-adv-3104]rule 5 permit ip source 10.104.1.0 0.0.0.255 destination 10.106.1.0 0.0.0.255
[SwitchA-acl-adv-3104] rule 10 deny ip source 10.104.1.0 0.0.0.255
#
[SwitchA]traffic-filter vlan 104 inbound acl 3104
项目效果
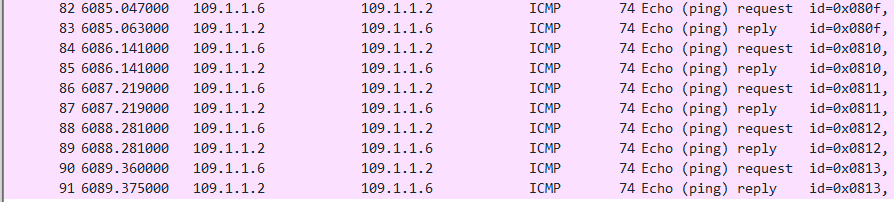
#测试nat效果是否转换地址
命令效果:
[USG6000V1]display firewall session table
2022-04-15 16:38:12.960
Current Total Sessions : 5
icmp VPN: public --> public 10.103.1.254:35487[109.1.1.6:2066] --> 109.1.1.2:
2048
icmp VPN: public --> public 10.103.1.254:34719[109.1.1.6:2063] --> 109.1.1.2:
2048
icmp VPN: public --> public 10.103.1.254:34975[109.1.1.6:2064] --> 109.1.1.2:
2048
icmp VPN: public --> public 10.103.1.254:35231[109.1.1.6:2065] --> 109.1.1.2:
2048
icmp VPN: public --> public 10.103.1.254:35743[109.1.1.6:2067] --> 109.1.1.2:
2048
抓包效果:
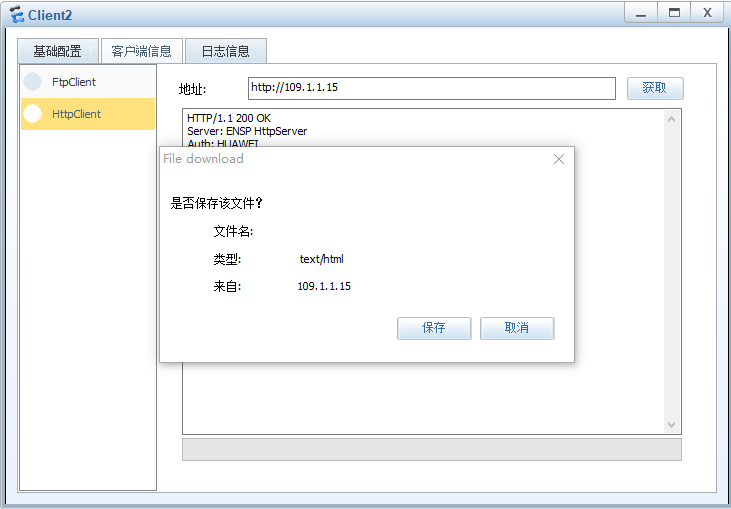
#测试NATServer的效果
命令效果:
[USG6000V1]display firewall session table
2022-04-15 16:40:44.920
Current Total Sessions : 1
http VPN: public --> public 192.168.100.10:2050 --> 109.1.1.15:80[10.106.1.20
0:80]
访问效果:
#无线实验效果
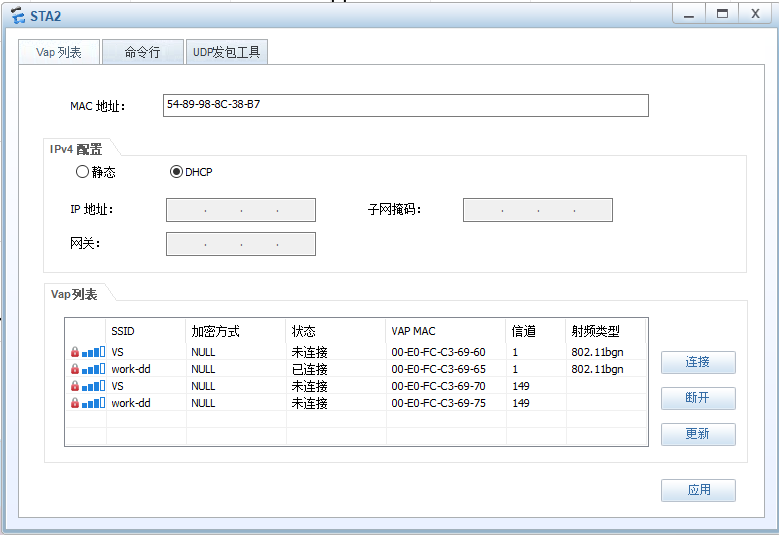
双WLAN效果:
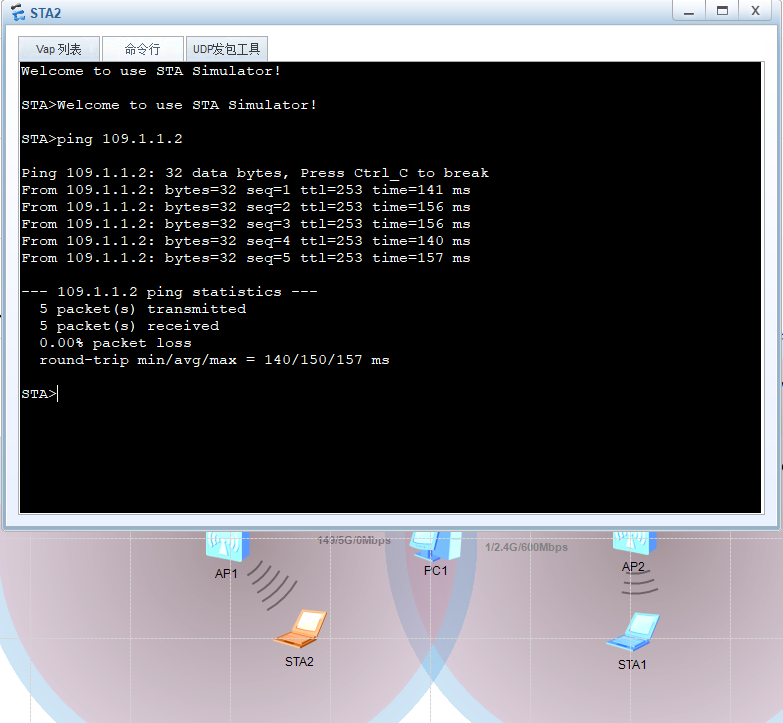
使用WLAN访问外部网络效果:
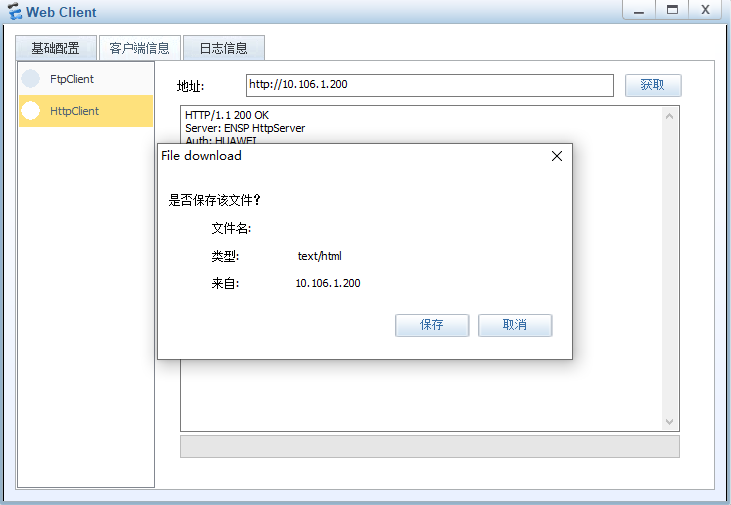
#ACL访问控制列表实验效果
配置对Webclient流量的管控,只能于dmz区域服务器互访。
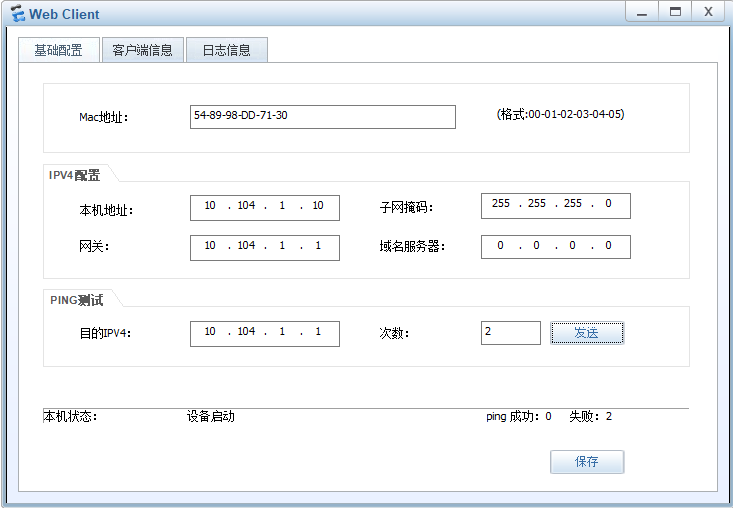
管控访客WLAN的流量不允许访问FTP服务器区和员工有线网络