企业防火墙案例(简单)
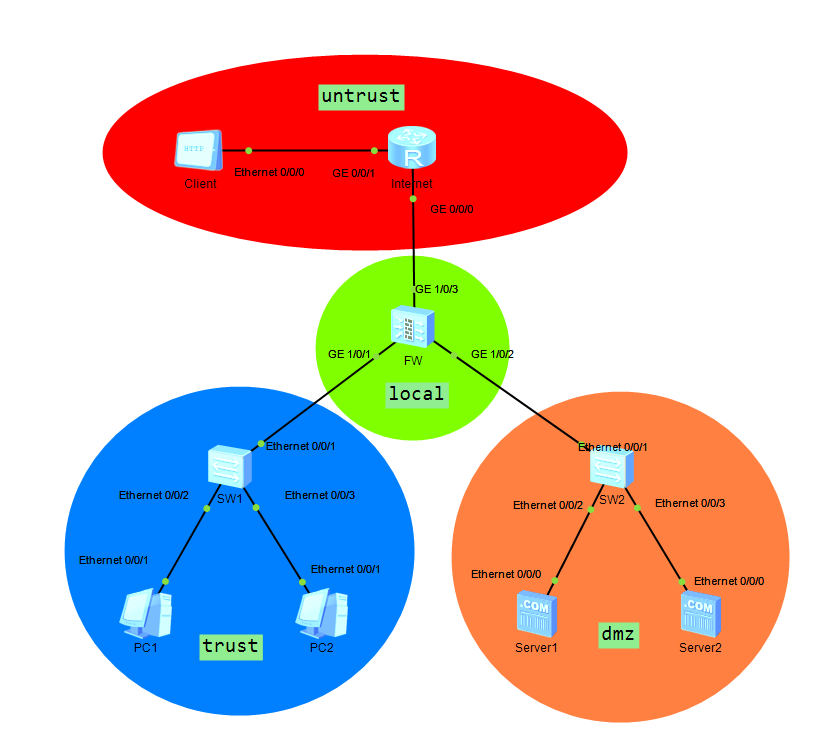
| 设备 |
接口 |
地址 |
| FW(USG6000V) |
GigabitEthernet 1/0/1 |
10.1.1.254/24 |
| FW |
GigabitEthernet 1/0/2 |
10.2.1.254/24 |
| FW |
GigabitEthernet 1/0/3 |
100.1.1.2/28 |
| Internet(AR) |
GigabitEthernet 0/0/0 |
100.1.1.1/28 |
| Internet |
GigabitEthernet 0/0/1 |
192.168.76.254/24 |
| PC1 |
Ethernet0/0/1 |
DHCP获取 |
| PC2 |
Ethernet0/0/1 |
DHCP获取 |
| server1 |
Ethernet0/0/0 |
10.2.1.1/24 |
| server2 |
Ethernet0/0/0 |
10.2.1.1/24 |
| Client |
Ethernet0/0/0 |
192.168.76.1/24 |
零、配置接口区域
- 配置信任(trust)区域:85
| [FW]firewall zone trust |
| [FW-zone-trust]add interface GigabitEthernet 1/0/1 |
- 配置隔离(dmz)区域:50
| [FW]firewall zone dmz |
| [FW-zone-dmz]add interface GigabitEthernet 1/0/2 |
- 配置不信任(untrust)区:5
| [FW]firewall zone untrust |
| [FW-zone-untrust]add interface GigabitEthernet 1/0/3 |
一、USG6000V配置企业内网DHCP
- 开启全局DHCP
[FW]dhcp enable 开启DHCP
- 配置内网接口DHCP下发
| [FW]interface GigabitEthernet 1/0/1 #进入g1/0/1接口 |
| [FW]dhcp select interface #DHCP选择接口下发 |
| [FW]dhcp server ip-range 10.1.1.1 10.1.1.253 #配置地址范围 |
| [FW]dhcp server gateway-list 10.1.1.254 #配置DHCP网关 |
二、配置内网nat实现内网用户访问Internet
- 配置安全策略
| [FW]security-policy #进入安全策略视图 |
| [FW-policy-security]rule name trust_untrust #创建策略,允许内网访问外网 |
| [FW-policy-security-rule-trust_untrust]source-zone trust #设置信任区 |
| [FW-policy-security-rule-trust_untrust]destination-zone untrust #设置非信任区 |
| [FW-policy-security-rule-trust_untrust]source-address 10.1.1.0 mask 255.255.255.0 #设置匹配信任IP地址段 |
| [FW-policy-security-rule-trust_untrust]destination-address 0.0.0.0 mask 0.0.0.0 #设置目标不信任IP |
| [FW-policy-security-rule-trust_untrust]action permit #允许放行 |
- 配置NAT地址池
| [FW]nat address-group 1 #创建地址池 ‘1’ |
| [FW-address-group-1]mode pat #开启允许端口地址转换 |
| [FW-address-group-1]section 0 100.1.1.10 100.1.1.15 #配置转换地址,从100.1.1.10-100.1.1.15 |
- 配置源NAT策略
| [FW]nat-policy #进入nat策略视图 |
| [FW-policy-nat]rule name trust_untrust_nat_group #创建NAT策略 |
| [FW-policy-nat-rule-trust_untrust_nat_group]source-zone trust #设置信任区 |
| [FW-policy-nat-rule-trust_untrust_nat_group]destination-zone untrust #设置非信任区 |
| [FW-policy-nat-rule-trust_untrust_nat_group]source-address 10.1.1.0 mask 255.255.255.0 #配置匹配IP地址段 |
| [FW-policy-nat-rule-trust_untrust_nat_group]action source-nat address-group 1 #绑定nat地址池 |
- 配置默认路由
ip route-static 0.0.0.0 0.0.0.0 100.1.1.1
- 配置黑洞路由防止,FW和ISP之间产生环路
| [FW]ip route-static 100.1.1.10 32 NULL 0 |
| [FW]ip route-static 100.1.1.11 32 NULL 0 |
| [FW]ip route-static 100.1.1.12 32 NULL 0 |
| [FW]ip route-static 100.1.1.13 32 NULL 0 |
| [FW]ip route-static 100.1.1.14 32 NULL 0 |
| [FW]ip route-static 100.1.1.15 32 NULL 0 |
三、配置natServer实现内网服务器映射到Internet
- 配置安全策略
| [FW-policy-security]rule name server_web |
| [FW-policy-security-rule-server_web]source-zone untrust |
| [FW-policy-security-rule-server_web]destination-zone dmz |
| [FW-policy-security-rule-server_web]destination-address 10.2.1.2 mask 255.255.255.255 |
| [FW-policy-security-rule-server_web]action permit |
| |
- 配置NatServer服务
| nat server 80 protocol tcp global 100.1.1.9 880 inside 10.2.1.2 www unr-route |
| #配置服务名为'80',协议为TCP设置全球,转换公网地址 100.1.1.9 端口880,内部IP地址 10.2.1.2 端口80或www服务, |
| 配置UNR路由防止路由环路 |
实验结果
0、区域验证
| [FW]display zone |
| 2022-03-11 02:15:31.000 |
| local |
| priority is 100 |
| interface of the zone is (0): |
| # |
| trust |
| priority is 85 |
| interface of the zone is (2): |
| GigabitEthernet0/0/0 |
| GigabitEthernet1/0/1 |
| # |
| untrust |
| priority is 5 |
| interface of the zone is (1): |
| GigabitEthernet1/0/3 |
| # |
| dmz |
| priority is 50 |
| interface of the zone is (1): |
| GigabitEthernet1/0/2 |
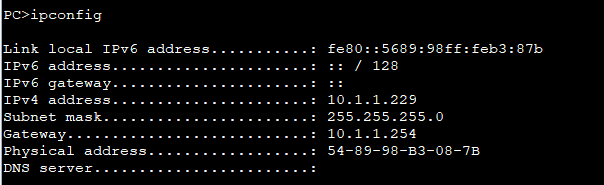
1、PC机-DHCP
| [FW]display dhcp server statistics |
| 2022-03-11 02:16:23.890 |
| DHCP Server Statistics: |
| |
| Client Request : 4 |
| Dhcp Discover : 2 |
| Dhcp Request : 2 |
| Dhcp Decline : 0 |
| Dhcp Release : 0 |
| Dhcp Inform : 0 |
| Server Reply : 4 |
| Dhcp Offer : 2 |
| Dhcp Ack : 2 |
| Dhcp Nak : 0 |
| Bad Messages : 0 |
| |
2、NAT
| [FW]display firewall session table |
| 2022-03-11 02:35:59.750 |
| Current Total Sessions : 5 |
| icmp VPN: public --> public 10.1.1.162:42677[100.1.1.11:2062] --> 2.2.2.2:204 |
| 8 |
| icmp VPN: public --> public 10.1.1.162:41909[100.1.1.11:2059] --> 2.2.2.2:204 |
| 8 |
| icmp VPN: public --> public 10.1.1.162:41653[100.1.1.11:2058] --> 2.2.2.2:204 |
| 8 |
| icmp VPN: public --> public 10.1.1.162:42165[100.1.1.11:2060] --> 2.2.2.2:204 |
| 8 |
| icmp VPN: public --> public 10.1.1.162:42421[100.1.1.11:2061] --> 2.2.2.2:204 |
| 8 |
| |

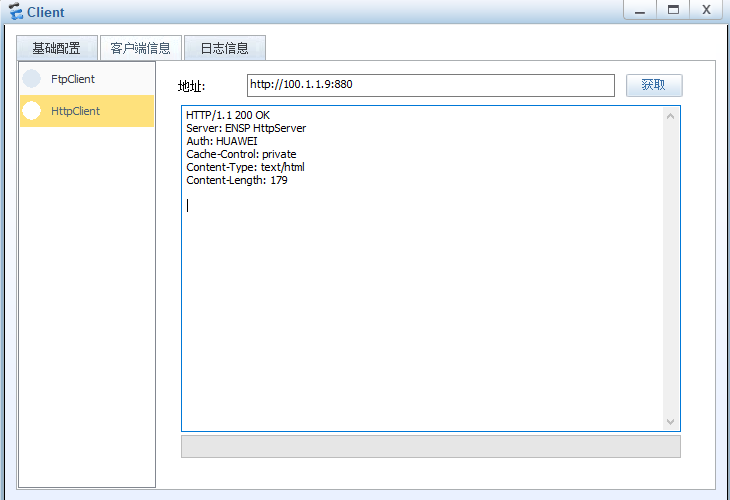
3、NATServer
| [FW]dis nat server name 80 |
| 2022-03-11 02:19:36.350 |
| Server in private network information: |
| Total 1 NAT server(s) |
| server name : 80 |
| id : 0 zone : |
| global-start-addr : 100.1.1.9 global-end-addr : 100.1.1.9 |
| inside-start-addr : 10.2.1.2 inside-end-addr : 10.2.1.2 |
| global-start-port : 880 global-end-port : 880 |
| inside-start-port : 80(www) inside-end-port : 80 |
| globalvpn : public insidevpn : public |
| vsys : public protocol : tcp |
| no-revers : 0 interface : |
| unr-route : 1 description : |
| nat-disable : 0 |
| |
此案例出网络工程师2021年下半年下午试题(二),配置参照网上资料和华为官方文档。









【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 上周热点回顾(3.3-3.9)
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· AI 智能体引爆开源社区「GitHub 热点速览」