2023工业信息安全技能大赛 - 典型工业行业锦标赛
签到题
s1 = "878C808B985783548D5D5B585555598D9342904741964C4F4D4C9F414D444F81"
hex_values = [int(s1[i:i+2], 16) for i in range(0, len(s1), 2)]
chars = [(value ^ index) - 33 for index, value in enumerate(hex_values)]
flag = ''.join(map(chr, chars))
print(flag)
# flag{1d2d302876ab2a34b9744d9080}
异常的编码
Flag{welcome}
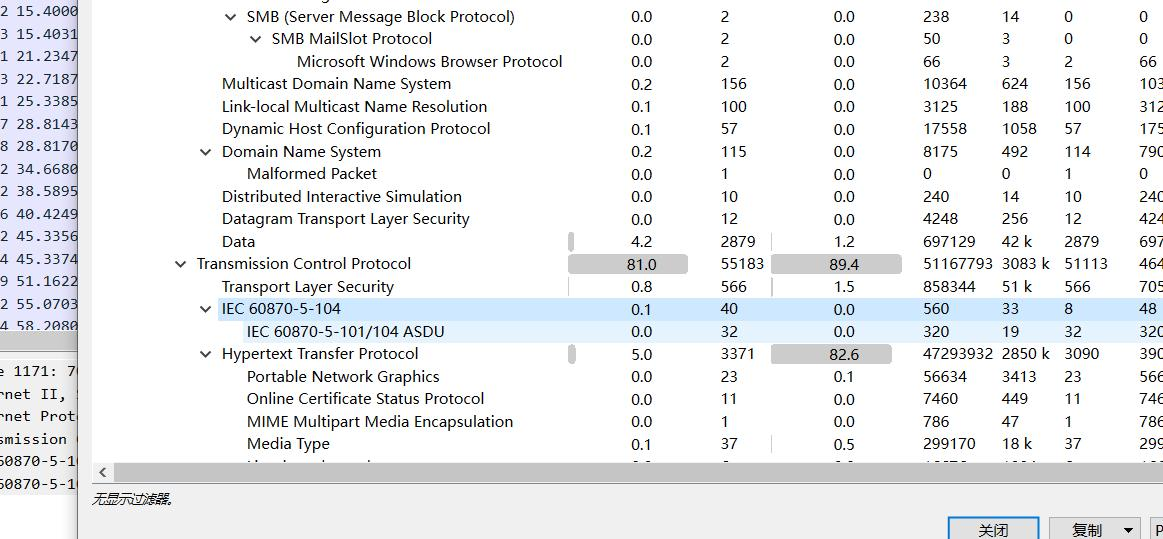
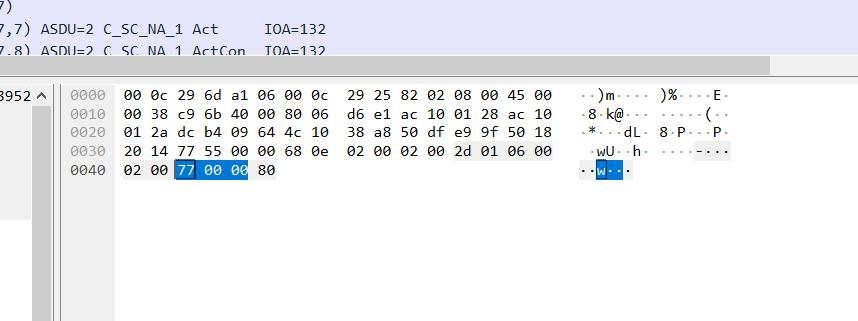
每个包最后一个字符拼一起就是 flag, welcome
需要计算的数值
配置环境, 在仿真软件中运行
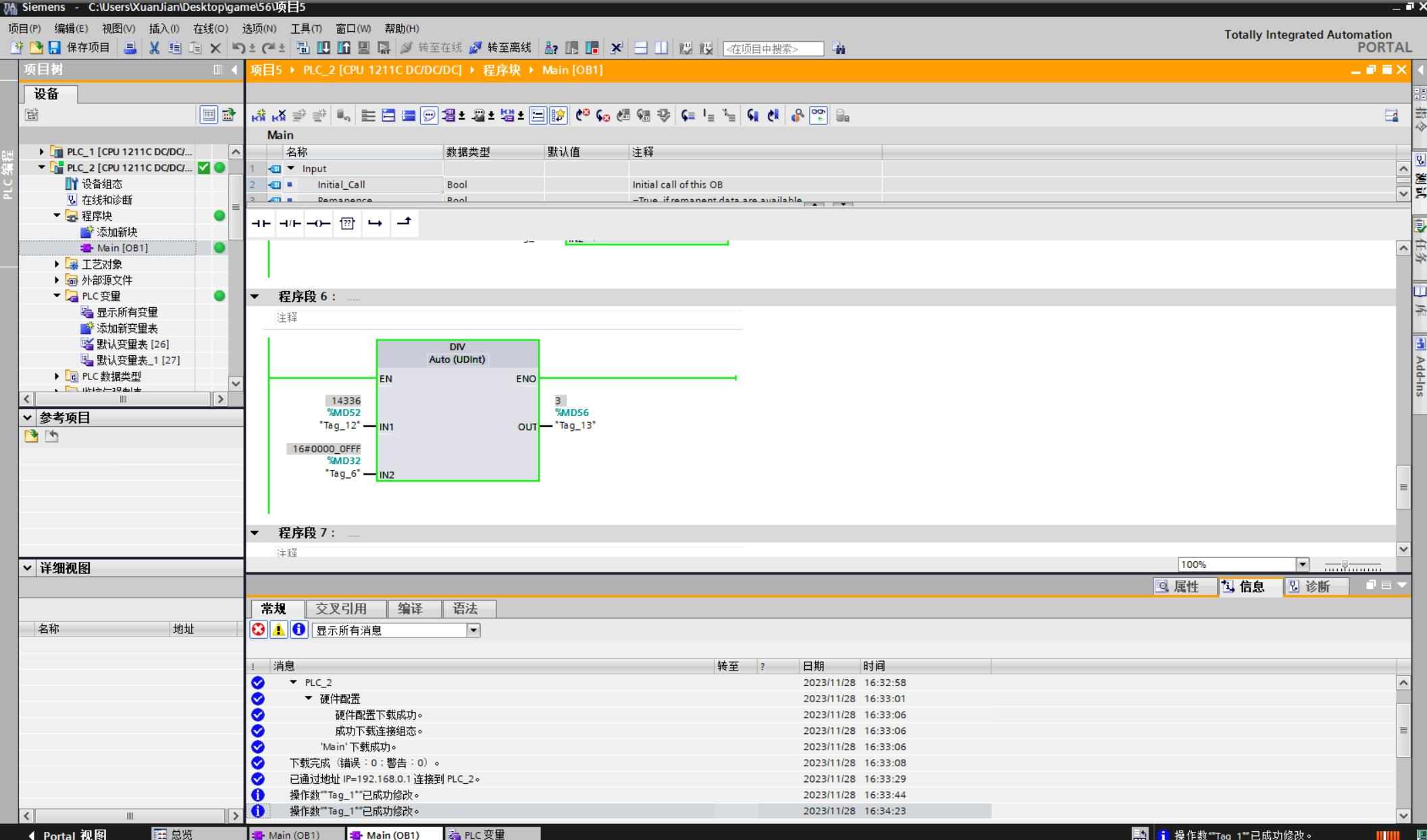
flag{MD56_3}
ez_equation
看pydas 取出字节码...然后z3求解器.
flag{Th1s_1s_4n_funny_ch4llenge_lollllll~}
from natsort import natsorted
from z3 import *
llst = [[154, 209, 184, 205, 152, 173, 85], [219, 163, 159, 245, 245, 245, 3], [244, 244, 153, 245, 164, 191, 126], [136, 241, 132, 245, 188, 173, 93],
[197, 198, 139, 207, 190, 181, 31], [167, 206, 128, 197, 183, 183, 76], [157, 223, 145, 198, 180, 165, 87]]
m = [BitVec('s1_%d' % i, 8) for i in range(42)] # 有时得用int值好使
pad = [BitVec('o_%d' % i, 8) for i in range(8)] # 有时得用int值好使
solver = Solver()
solver.add(m[0] == ord('f'))
solver.add(m[1] == ord('l'))
solver.add(m[2] == ord('a'))
solver.add(m[3] == ord('g'))
solver.add(m[4] == ord('{'))
solver.add(m[41] == ord('}'))
for i,tp in enumerate(llst):
solver.add(m[i*6 + 0] ^ m[i*6 + 1] ^ m[i*6 + 2] ^ pad[0] == tp[0])
solver.add(m[i*6 + 3] ^ m[i*6 + 4] ^ pad[1] ^ pad[2] == tp[1])
solver.add(pad[5] ^ m[i*6 + 5] ^ pad[1] ^ pad[3] == tp[2])
solver.add(m[i*6 + 3] ^ pad[3] ^ pad[4] ^ pad[1] == tp[3])
solver.add(m[i*6 + 5] ^ pad[0] ^ m[i*6 + 4] ^ pad[1] == tp[4])
solver.add(m[i*6 + 2] ^ m[i*6 + 4] ^ pad[0] ^ pad[1] == tp[5])
solver.add(m[i*6 + 2] ^ m[i*6 + 0] ^ m[i*6 + 4] ^ pad[4] == tp[6])
print(solver.check())
res = solver.model()
# lst = natsorted([(k, res[k]) for k in res], key=lambda x: x)
lst = natsorted([(k, res[k]) for k in res], lambda x: str(x[0]))
for k, v in lst:
print(chr(v.as_long()), end='')
异常的工程
力控恢复工程发现编码
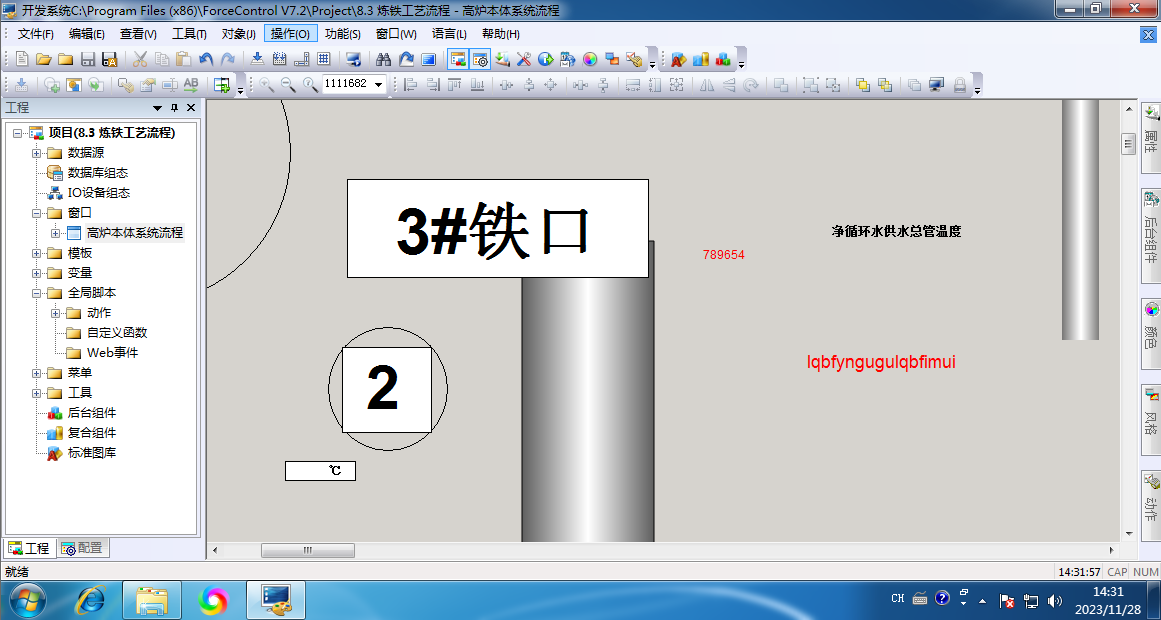
http://www.atoolbox.net/Tool.php?Id=912
解密 lqbfyngugulqbfimui 789654 得到正确flag
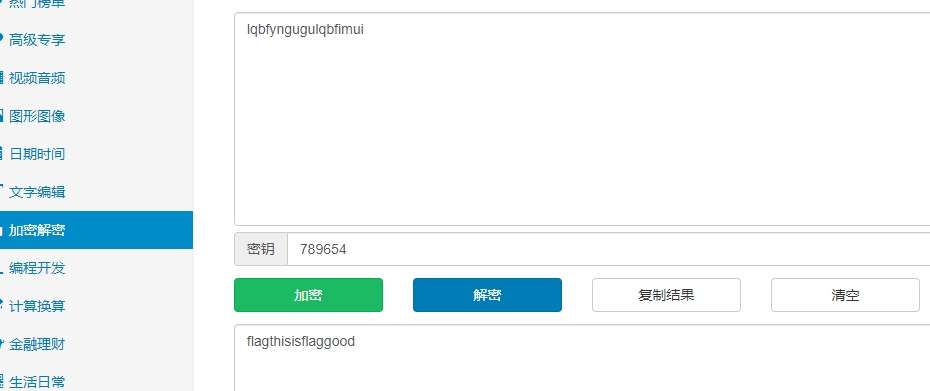
ez_crypt
ez_crpt rc4加密..直接找到加密位置.将密文输入内存.
923117B560C8486423FA0ABBC53493ECB9616C5D899BA01B47E267BBC7CBD8FE1C67BF98E2EE
自动解flag db 'flag{6cd72bd931a381ddca4e810224bd6d06}',0
babygo
Base32换表加密
enc= 'N2XHD244PSVED53BHG2W7ZSVNK5W7ZSVPOTUHNU6'
table ACDEFGHIJKLMNOPQRSTUVWXYZ234567B
flag{th1s_1s_b4by_b4se32}
magic_book
sting打印可见字符
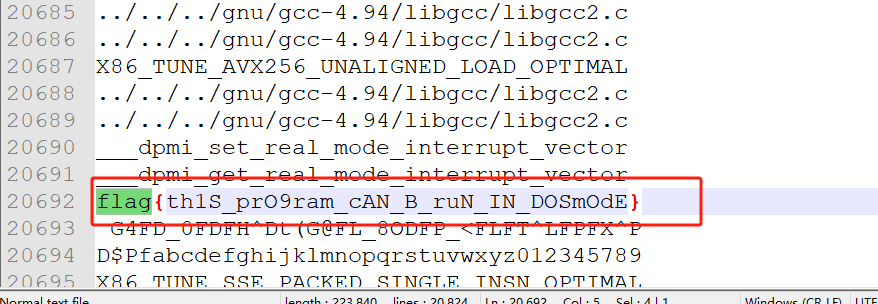
流量分析
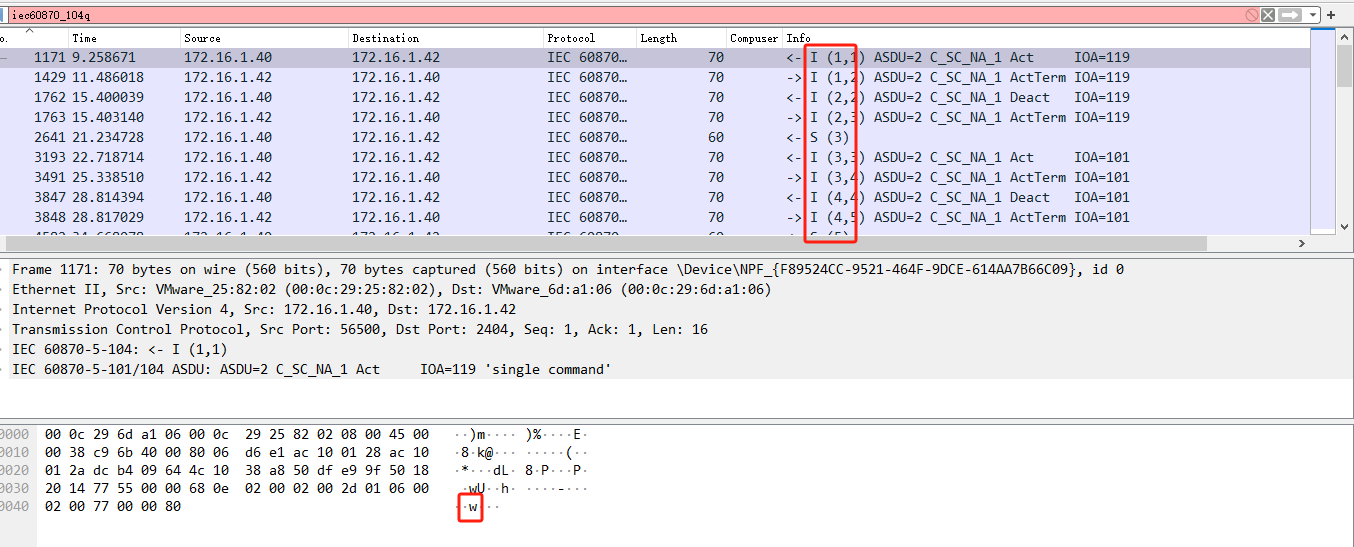
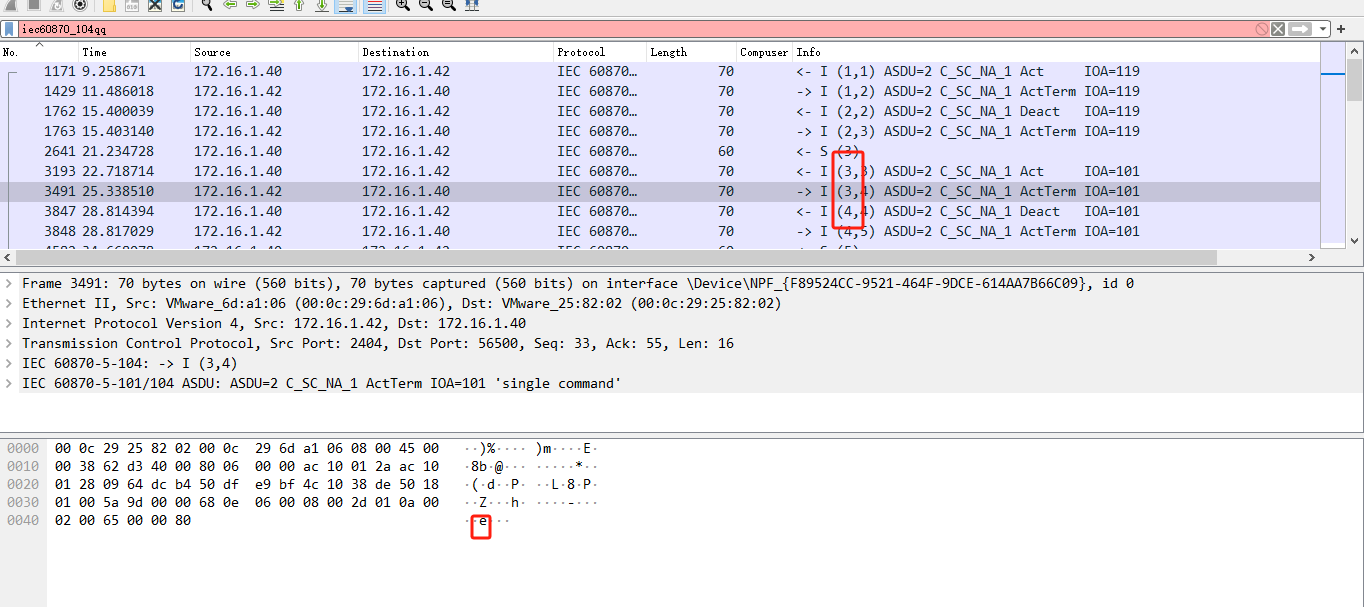
flag{welcome}


