全国网络安全行业职业技能大赛云南省选拔赛
ezRAS
python pyinstxtractor.py xxx.exe 得到 1.pyc文件, 再用pycdc得到py文件.
直接解
# Source Generated with Decompyle++
# File: 1.pyc (Python 3.10)
import gmpy2
from Cryptodome.Util.number import long_to_bytes
p = 0x3B6311745B1BD50F111D171CC1D5A7FBBFABCBB
q = 0x2B5FDF7118A38EFB3B4F2A0D4E6130E520DD2F9
e = 0x1224B6ADFDD2F4C4350713196000258F5C7D193FACE19E484E027BA4351B796523DF4DCB2CAE5
c = [
0x268BDF69E55B075E519108349569B951FD7FA62B0D9088B476BB66D5CB04630F525CD2B33A3F3,
0x6A1E9C448AD5742B8FCF4F73179C3D1614263000B85EC499BC9E941C95703B8DD7CC21EA77975,
0x7BB14144E91EC9106B1C5CD878F507A07FFAEE4B7B092271DEAA7E5B6EF47FB3FA84425F6D375,
0x8E6D08C60928CA8A65FC971E24C80F256678F476BD2DB28D7174E398C0D81EBF8A20C1FB76B9D,
0x529D680E0851D069FBDF74E81CF20B369CEC53238486C106E0CC0E8741E6C25814DD4ECB28047,
0x805AD716FD54C6FA0D9A162B30055B1C469E37AF7D77C5A71532320AAF47F300C95619A6CCA21,
0x51585D5C3733CE1FA91F7E8722C0A29934B8B12C98B634AABFD126AC2BED5C1A5754EB3A5276D,
0x8B4AC0EF0669E4DFA2E24F96528BCFB8168566FD5FB2DCC1E9DE413DA768258E759C9A073D832,
0x74CCD34986604C0305D16FE7FEB7D40C757990DBCFBBC97E8A8C21A266EAD33E9245ABE8EDF9B,
0x51585D5C3733CE1FA91F7E8722C0A29934B8B12C98B634AABFD126AC2BED5C1A5754EB3A5276D,
0x8B4AC0EF0669E4DFA2E24F96528BCFB8168566FD5FB2DCC1E9DE413DA768258E759C9A073D832,
0x74CCD34986604C0305D16FE7FEB7D40C757990DBCFBBC97E8A8C21A266EAD33E9245ABE8EDF9B,
0x805AD716FD54C6FA0D9A162B30055B1C469E37AF7D77C5A71532320AAF47F300C95619A6CCA21,
0x673A6BEB5E9AFD0BABB9D3D088C226B4FA1D23ADAECC74E2EF45DCEB9C3949E0456188D41F973,
0x8B4AC0EF0669E4DFA2E24F96528BCFB8168566FD5FB2DCC1E9DE413DA768258E759C9A073D832,
0x92B1493A164638E670FE0CB043FC253FCAEAD763776FCBDF987E54AE894DFCC13692BBEE9C29,
0x51585D5C3733CE1FA91F7E8722C0A29934B8B12C98B634AABFD126AC2BED5C1A5754EB3A5276D,
0x8B4AC0EF0669E4DFA2E24F96528BCFB8168566FD5FB2DCC1E9DE413DA768258E759C9A073D832,
0x51585D5C3733CE1FA91F7E8722C0A29934B8B12C98B634AABFD126AC2BED5C1A5754EB3A5276D,
0x8B4AC0EF0669E4DFA2E24F96528BCFB8168566FD5FB2DCC1E9DE413DA768258E759C9A073D832,
0x805AD716FD54C6FA0D9A162B30055B1C469E37AF7D77C5A71532320AAF47F300C95619A6CCA21,
0x673A6BEB5E9AFD0BABB9D3D088C226B4FA1D23ADAECC74E2EF45DCEB9C3949E0456188D41F973,
0x51585D5C3733CE1FA91F7E8722C0A29934B8B12C98B634AABFD126AC2BED5C1A5754EB3A5276D,
0x51585D5C3733CE1FA91F7E8722C0A29934B8B12C98B634AABFD126AC2BED5C1A5754EB3A5276D,
0x673A6BEB5E9AFD0BABB9D3D088C226B4FA1D23ADAECC74E2EF45DCEB9C3949E0456188D41F973,
0x92B1493A164638E670FE0CB043FC253FCAEAD763776FCBDF987E54AE894DFCC13692BBEE9C29,
0x7C04B76E88FDF069BB729410E91792BA182F4CFAA5D2FA7A7829BD9740B78E664C12A784949F0]
phin = (p - 1) * (q - 1)
n = p * q
d = gmpy2.invert(e, phin)
for x in c:
m = pow(x, d, n)
print(long_to_bytes(m).decode(), end='')
# flag{145645613524545134432}
ezSM
from itertools import product
m = bytes.fromhex("c49f4552b22f27969c07d9371d1aa093b54f97ccd44261a5fc92cd3461a38d68d20218a51686a3f9d0cc50679e36cd4f")
key = '4765%sdf%s0170%s44%s'
def sm4_decrypt_ECB_by_gmssl(byt_cipher_text, secret_key):
from gmssl.sm4 import CryptSM4, SM4_ENCRYPT, SM4_DECRYPT
crypt_sm4 = CryptSM4()
crypt_sm4.set_key(secret_key, SM4_DECRYPT)
decrypt_value = crypt_sm4.crypt_ecb(byt_cipher_text)
return decrypt_value
hextable = '0123456789abcdef'
for g in product(hextable, repeat=4):
key1 = key % g
r = sm4_decrypt_ECB_by_gmssl(m, key1.encode())
if b'flag' in r:
print(r)
# b'flag{b9406a169437ed4e0832cb181406e88f}'
hide
改完点点就出来了
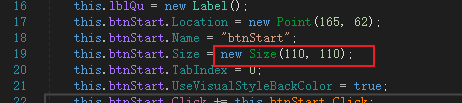
dlp
频域盲水印

