2022中国能源网络安全大赛决赛 WriteUp
F | 01. sign_in
baby_pack取出加密段,循环异或
enc = bytes.fromhex('666D63647F7D3675573879547F3D3E3F20214D7620666F6A')
for i, c in enumerate(enc):
print(chr(c^ i),end='')
F | 02.unsafe_prng
关键函数如下
unsigned __int64 __fastcall sub_55F88296C45E(__int64 input)
{
now = time(0LL); // 初始化的当前时间, 从这里爆破
ptrNow = (unsigned __int64 *)operator new(8uLL);
sub_55F88296C96C(ptrNow, now);
ptrNow2 = ptrNow;
for ( i = 0; i <= 49; ++i )
{
v16 = rol8(ptrNow2); // ptrNow2 = time * n + 1, 下一轮用新的 ptrNow2 运算
// v16 = ptrNow >> 12 rol << 32
copy((__int64)v19, (__int64)&v16); // v16 保存到v19数组中
}
for ( j = 0; j <= 4; ++j )
{
v4 = std::ostream::operator<<(&std::cout, sub_55F88296C940);
v5 = (_QWORD *)sub_55F88296CB5C(v19, j);
v6 = std::ostream::operator<<(v4, *v5);
std::ostream::operator<<(v6, &std::endl<char,std::char_traits<char>>);
}
v7 = std::operator<<<std::char_traits<char>>(&std::cout, "----------------", v3);
std::ostream::operator<<(v7, &std::endl<char,std::char_traits<char>>);
for ( k = 0; k < (unsigned __int64)std::string::length(input); ++k )
{
out = std::ostream::operator<<(&std::cout, sub_55F88296C940);
charK = *(unsigned __int8 *)std::string::operator[](input, k); // input[k]
numV19K = (_QWORD *)sub_55F88296CB5C(v19, k % 50); // v19[k]
v11 = std::ostream::operator<<(out, charK ^ *numV19K); // 异或
std::ostream::operator<<(v11, &std::endl<char,std::char_traits<char>>);
}
}
解题:
from datetime import datetime
rol = lambda val, r_bits, max_bits: \
(val << r_bits % max_bits) & (2 ** max_bits - 1) | \
((val & (2 ** max_bits - 1)) >> (max_bits - (r_bits % max_bits)))
def rand_time(src):
con = 0x5851F42D4C957F2D
dat = src * con + 1 & 0xffffffffffffffff
result = rol(dat >> 12, 32, 64) & 0xffffffffffffffff
return result, dat
# 从output.txt的文件日期前一天开始爆破
def bf_time():
# a = datetime.fromtimestamp(0x6368A47E)
t0 = int(datetime(2022, 10, 27, 1, 1, 1).timestamp())
t1 = int(datetime(2022, 10, 28, 1, 1, 1).timestamp())
delta = t1 - t0
for i in range(t0, t0 + delta * 4, 1):
s1, dat = rand_time(i)
if s1 == 0x7ee4b30800048d22:
print(i) # 1666945270
break
if __name__ == '__main__':
# bf_time()
origin_time = 1666945270
# 初始化个50个数
lst = []
for i in range(50):
result, origin_time = rand_time(origin_time)
lst.append(result)
enc_data = [0x7ee4b30800048d44, 0xf0f8b4ca000523c1, 0xf5d32fb50004f282, 0xd9fa8818000a9958, 0xd5d8575f000cd71b, 0x347e3bea000b4c55, 0x3a573e7e000ed548, 0x72193d40005da83, 0x9f3b86f2000d0310, 0xb6b66a300008acaa, 0x82be2b2000095a0f, 0x9bc03fd20000c7f1, 0x3f051191000b0470, 0xdc0697600003ea04,
0xf9e6be71000b91af, 0xc00aa3e500066551, 0xccd87489000c9c0d, 0x116b1e0c0000ea88, 0x685a732200052b92, 0xd67e3f8d000dc45b, 0x70caba6000005279, 0xd2f05000094ac5, 0x6af1db8100038c8f, 0xde021cb40005b20d, 0xce05d69b0008e66b, 0xc11af8940002ff4c, 0xe6c3e339000b5bbe, 0xc9539e70000832e7,
0xb13a3d78000b247d, 0x2d0e064e00061c60, 0x1655ad0d0000c6a5, 0xa032bbc500042699, 0x84a77b500059307, 0x899a06be000d4ce2, 0x2fdccca10002d4f5, 0x306c66610006aaf1, 0xf7d8724900072c0c, 0xd4f749b200071826, 0xce019c320006aeb7, 0xc94ddd5f000ed5da, 0x2e584a27000981d4, 0x4aca92410004c48e]
for a, b in zip(enc_data, lst):
print(chr(a ^ b), end='')
F | 03.启动程序分析
tag5->tag6->tag8是15s
tag8->tag12是20s
tag8->tag14是15s
取大15+20=35s
flag{35}
F | 06. 损坏的文件
栅栏.zip base64解码为jpg, zip后面还一段key=PihsQ6rnk6olkhod
右击文件属性,提示了 steghide.
steghide`` extract -sf 1.jpg -p PihsQ6rnk6olkhod
PihsQ6rnk6olkhod ` 拆成2段栅栏 `Pki6hoslQk6hrond
steghide extract -sf 1.jpg -p Pki6hoslQk6hrond
Flag flag{rf5768ghwaoinfkj}
F | 07.压缩包里的秘密
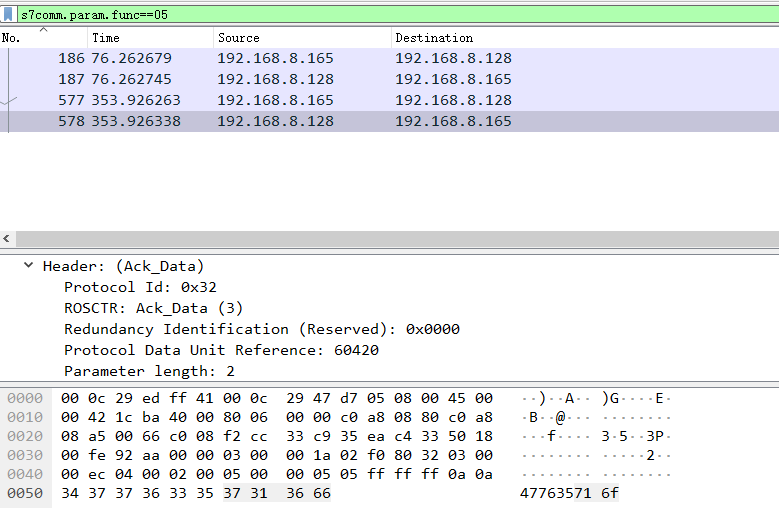
两段5847373458477635716f,解得密码XG74XGv5qo
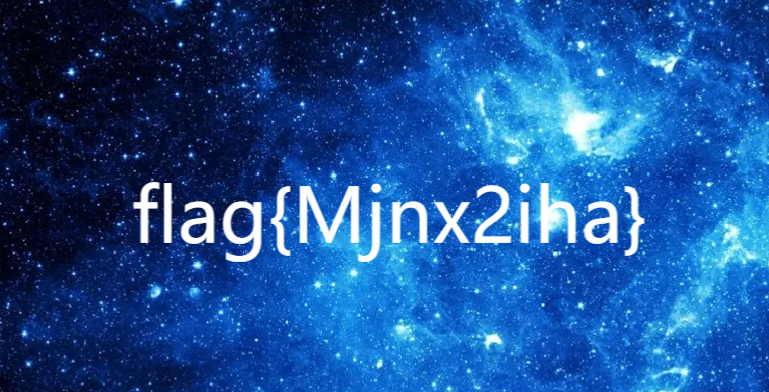
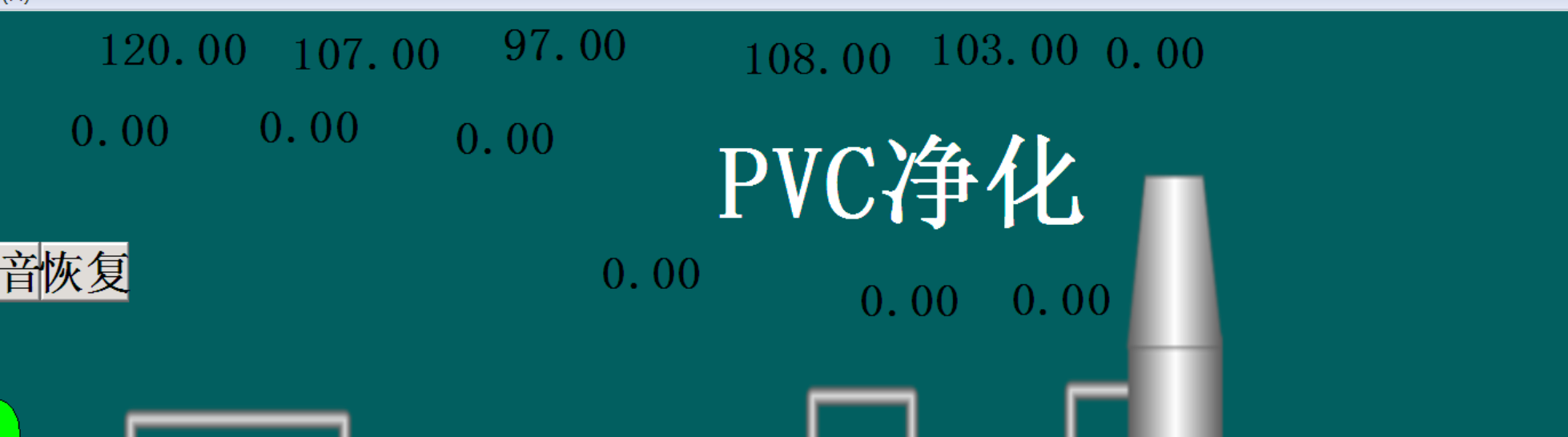
F | 08.scada的错乱显示
全局脚本->动作->应用程序动作,修改为
if a6.PV==1 then
M6.PV=89
else
M6.PV=0
endif
if M6.pv==89 then
M60=60
else
M60=0
endif
if a3.PV==1 then
M3.PV=97
else
M3.PV=0
endif
if M3.pv==97 then
M30=30
else
M30=0
endif
if a11.PV==1 then
M11.PV=67
else
M11.PV=0
endif
if M11.pv==67 then
M110=110
else
M110=0
endif
if a5.PV==1 then
M5.PV=103
else
M5.PV=0
endif
if M5.pv==103 then
M50=50
else
M50=0
endif
if a9.PV==1 then
M9.PV=56
else
M9.PV=0
endif
if M9.pv==56 then
M90=90
else
M90=0
endif
if a1.PV==1 then
M1.PV=120
else
M1.PV=0
endif
if M1.pv==120 then
M10=10
else
M10=0
endif
if a8.PV==1 then
M8.PV=78
else
M8.PV=0
endif
if M8.pv==78 then
M80=80
else
M80=0
endif
if a7.PV==1 then
M7.PV=77
else
M7.PV=0
endif
if M7.pv==77 then
M70=70
else
M70=0
endif
if a4.PV==1 then
M4.PV=108
else
M4.PV=0
endif
if M4.pv==108 then
M40=40
else
M40=0
endif
if a10.PV==1 then
M10.PV=64
else
M10.PV=0
endif
if M10.pv==64 then
M100=100
else
M100=0
endif
if a2.PV==1 then
M2.PV=107
else
M2.PV=0
endif
if M2.pv==107 then
M20=20
else
M20=0
endif
if a12.PV==1 then
M12.PV=34
else
M12.PV=0
endif
if M12.pv==34 then
M120=120
else
M120=0
endif
运行,输出m1-m5
得到flag{xkalg}
F | 09. test.pcapng
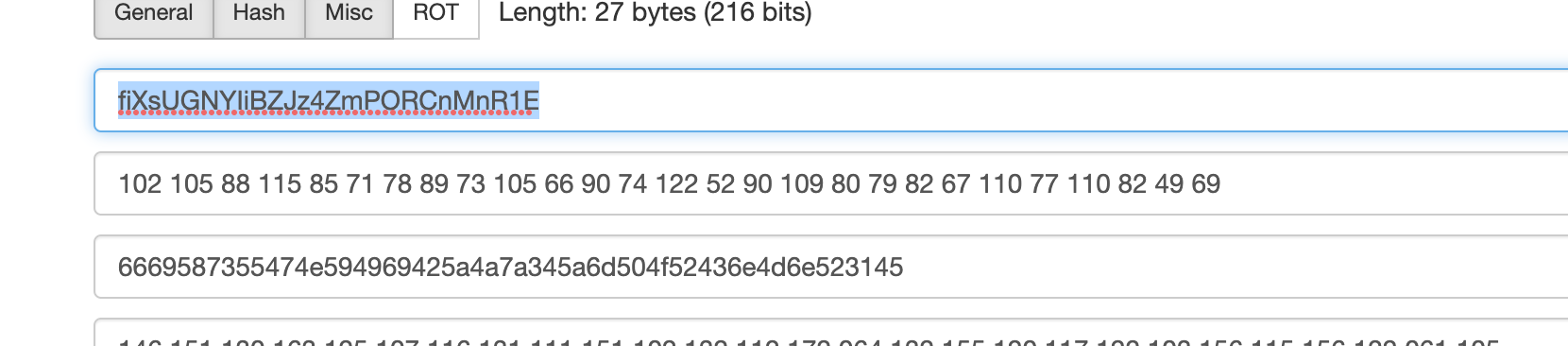
4377 4502号包找到
4969425a4a7a345a
6669587355474e59解出来为
IiBZJz4Z
fiXsUGNY
5917还有个6d504f52436e4d6e523145,mPORCnMnR1E
尝试:
flag{IiBZJz4ZfiXsUGNYmPORCnMn}
flag{IiBZJz4ZfiXsUGNYmPORCnMnR1E}
flag{fiXsUGNYIiBZJz4XmPORCnMnR1E}
A | 10.被攻击的SCADA
解压密码是iron
得到文件
第二层密码MODSIM
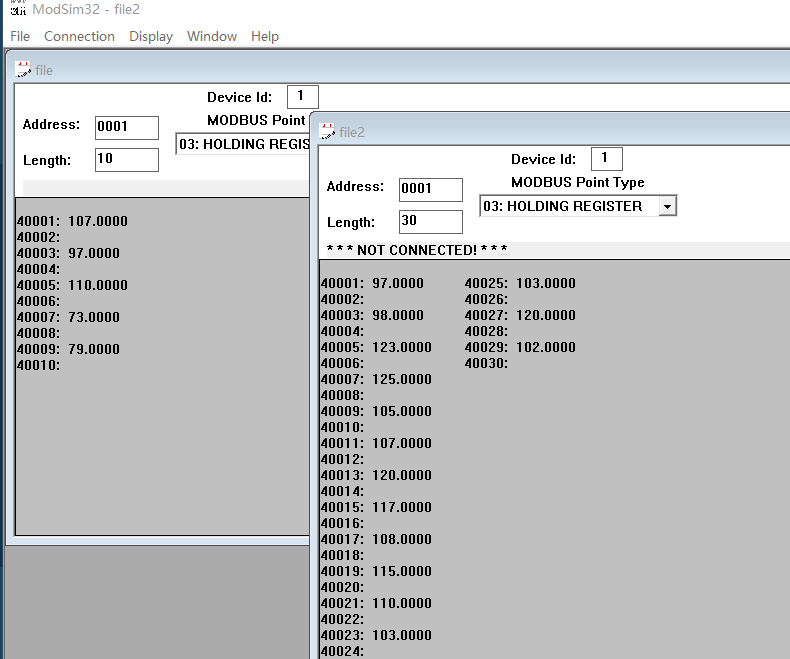
ab{}ikxulsnggxf
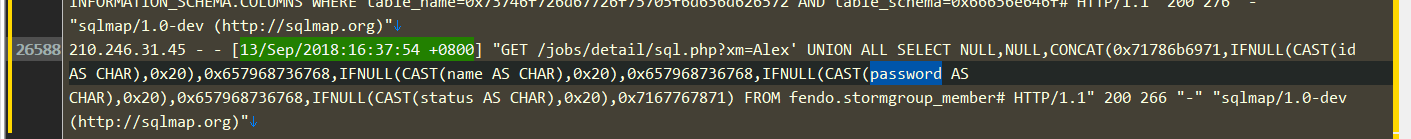
F | 11.系统日志取证
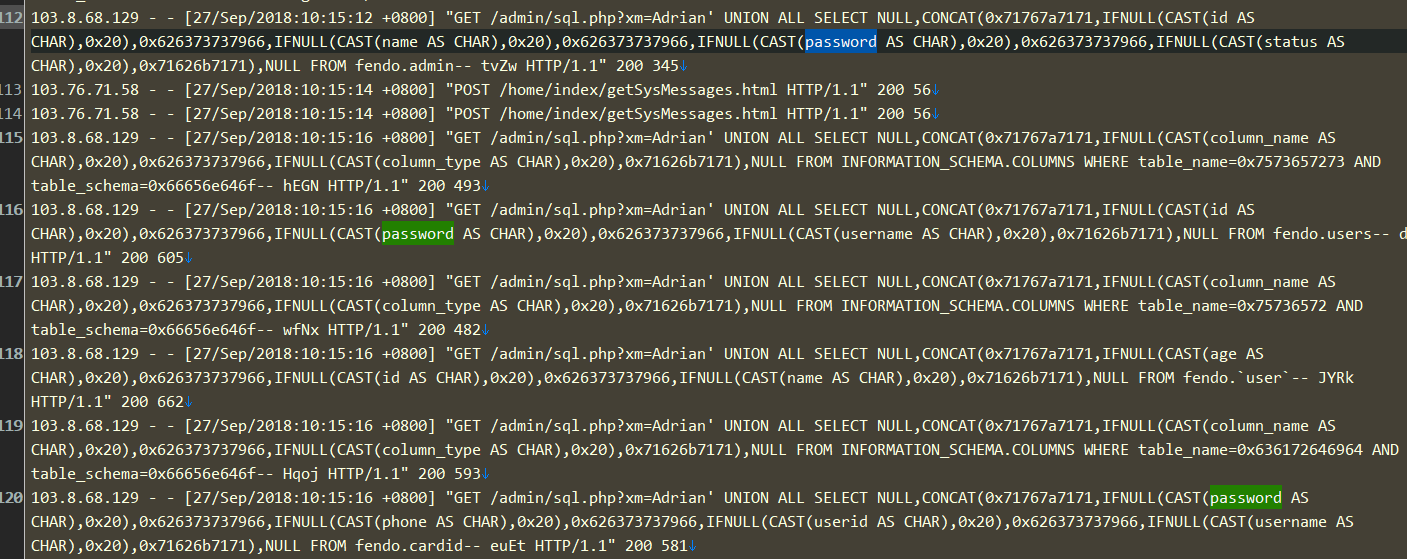
找password关键字
F | 12.图片的高度
修改高度

F | 13.数据加密分析
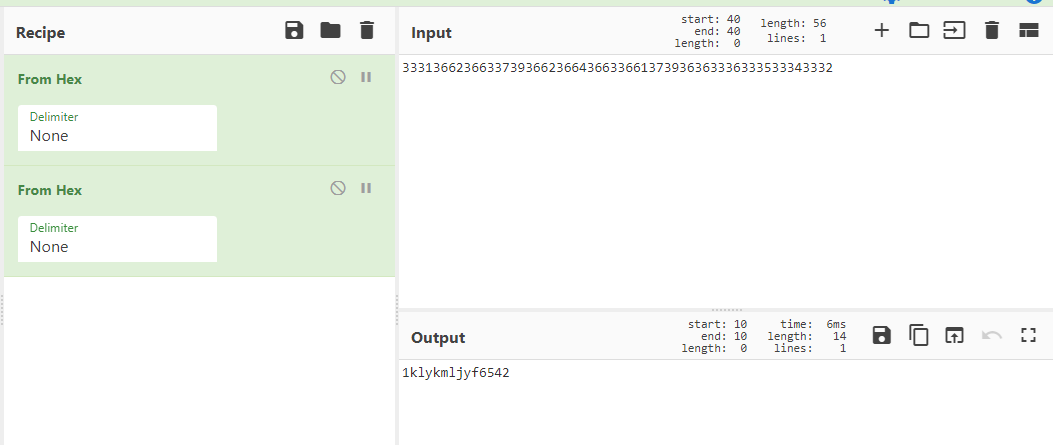
提交不对,后尝试多种,最终凯撒密码 偏移6位得到结果
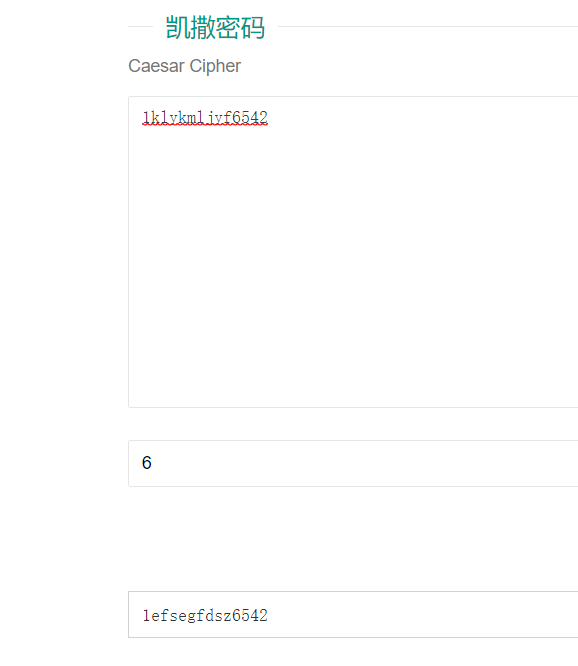
flag{1efsegfdsz6542}
F | 14.神器的编码
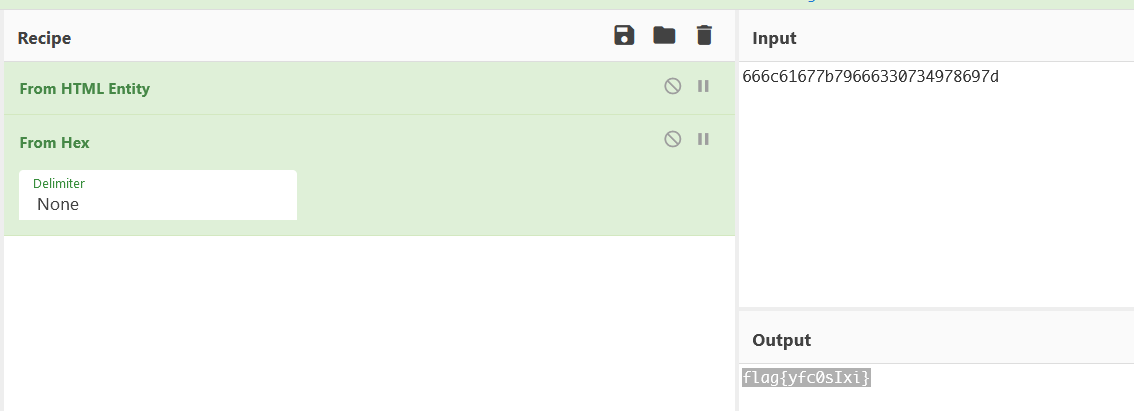
F | 15.入侵时间
检索关键字
F | 04.监测程序分析
某工厂技术员小张在进行石油生产时编写了一条计量监测的程序,你能帮小张算一下程序运行后输油泵在( )秒后启动吗?(精确小数点后一位)
使用Hollysys_Macs6打开工程,可知高电位0.7s,低电位0.9s,整个时序为1.6s,输油泵启动条件是MX0.6为1时可以启动,所以根据MX0.6地址位,MX0.6在MW0中排第7位 即需要加到2的7-1次方,及1+2+4+8+16+32+64=127 最终为127*1.6=203.2
flag{203.2}


