Django rest framework源码分析(一) 认证
一、基础
最近正好有机会去写一些可视化的东西,就想着前后端分离,想使用django rest framework写一些,顺便复习一下django rest framework的知识,只是顺便哦,好吧。我承认我是故意的,因为我始终觉得,如果好的技术服务于企业,顺便的提高一下自己。大家都很开心不是不。再次强调一下,真的只是顺便。
安装吧
pip install djangorestframework
1.2.需要先了解的一些知识
理解下面两个知识点非常重要,django-rest-framework源码中到处都是基于CBV和面向对象的封装
(1)面向对象封装的两大特性
把同一类方法封装到类中 将数据封装到对象中
(2)CBV
基于反射实现根据请求方式不同,执行不同的方法
原理:url-->view方法-->dispatch方法(反射执行其它方法:GET/POST/PUT/DELETE等等)
二、简单实例
2.1.settings
先创建一个project和一个app(我这里命名为API)
首先要在settings的app中添加,这里我把正则setting全部贴出来吧
"""
Django settings for API_TEST project.
Generated by 'django-admin startproject' using Django 1.9.7.
For more information on this file, see
https://docs.djangoproject.com/en/1.9/topics/settings/
For the full list of settings and their values, see
https://docs.djangoproject.com/en/1.9/ref/settings/
"""
import os
# Build paths inside the project like this: os.path.join(BASE_DIR, ...)
BASE_DIR = os.path.dirname(os.path.dirname(os.path.abspath(__file__)))
# Quick-start development settings - unsuitable for production
# See https://docs.djangoproject.com/en/1.9/howto/deployment/checklist/
# SECURITY WARNING: keep the secret key used in production secret!
SECRET_KEY = 'r!2z#wgp-v!3afygp=owoie10a(d*p4xwg+z*kcv039#klnp-r'
# SECURITY WARNING: don't run with debug turned on in production!
DEBUG = True
ALLOWED_HOSTS = ['*',] # 这里需要你修改一下,临时用用
# Application definition
INSTALLED_APPS = [
'django.contrib.admin',
'django.contrib.auth',
'django.contrib.contenttypes',
'django.contrib.sessions',
'django.contrib.messages',
'django.contrib.staticfiles',
'API.apps.ApiConfig',
'API_TEST', # 这里需要你添加一下自己的APP名字
'rest_framework', # 这里需要你添加一下
]
MIDDLEWARE_CLASSES = [
'django.middleware.security.SecurityMiddleware',
'django.contrib.sessions.middleware.SessionMiddleware',
'django.middleware.common.CommonMiddleware',
# 'django.middleware.csrf.CsrfViewMiddleware', # 这里需要临时注释一下哦
'django.contrib.auth.middleware.AuthenticationMiddleware',
'django.contrib.auth.middleware.SessionAuthenticationMiddleware',
'django.contrib.messages.middleware.MessageMiddleware',
'django.middleware.clickjacking.XFrameOptionsMiddleware',
]
ROOT_URLCONF = 'API_TEST.urls'
TEMPLATES = [
{
'BACKEND': 'django.template.backends.django.DjangoTemplates',
'DIRS': [os.path.join(BASE_DIR, 'templates')]
,
'APP_DIRS': True,
'OPTIONS': {
'context_processors': [
'django.template.context_processors.debug',
'django.template.context_processors.request',
'django.contrib.auth.context_processors.auth',
'django.contrib.messages.context_processors.messages',
],
},
},
]
WSGI_APPLICATION = 'API_TEST.wsgi.application'
# Database
# https://docs.djangoproject.com/en/1.9/ref/settings/#databases
# DATABASES = {
# 'default': {
# 'ENGINE': 'django.db.backends.sqlite3',
# 'NAME': os.path.join(BASE_DIR, 'db.sqlite3'),
# }
# }
# 这里是关于数据库相关配置,最好不要使用windows哦,我的环境是python2.7的,安装一下mysql连接器包的时候有问题,所以最好升级一下自己的pip
DATABASES = {
'default': {
'ENGINE': 'django.db.backends.mysql',
'NAME': 'test',
'USER': 'root',
'PASSWORD': 'root1234',
'HOST': '172.26.4.202',
'PORT': '3306',
}
}
# Password validation
# https://docs.djangoproject.com/en/1.9/ref/settings/#auth-password-validators
AUTH_PASSWORD_VALIDATORS = [
{
'NAME': 'django.contrib.auth.password_validation.UserAttributeSimilarityValidator',
},
{
'NAME': 'django.contrib.auth.password_validation.MinimumLengthValidator',
},
{
'NAME': 'django.contrib.auth.password_validation.CommonPasswordValidator',
},
{
'NAME': 'django.contrib.auth.password_validation.NumericPasswordValidator',
},
]
# Internationalization
# https://docs.djangoproject.com/en/1.9/topics/i18n/
LANGUAGE_CODE = 'en-us'
TIME_ZONE = 'UTC' # 这里最好也改一下吧。我是测试,无所谓了,生产上还是需要修改的
USE_I18N = True
USE_L10N = True
USE_TZ = True
# Static files (CSS, JavaScript, Images)
# https://docs.djangoproject.com/en/1.9/howto/static-files/
STATIC_URL = '/static/'
# 这里是和认证相关的,目前这里你用不到哦
REST_FRAMEWORK = {
'DEFAULT_AUTHENTICATION_CLASSES': ['API.utils.auth.Authentication',],
}
2.2.url
from django.contrib import admin
from django.urls import path
from API.views import AuthView
urlpatterns = [
path('admin/', admin.site.urls),
path('api/v1/auth/',AuthView.as_view()),
]
2.3.models
一个保存用户的信息
一个保存用户登录成功后的token
from django.db import models
class UserInfo(models.Model):
USER_TYPE = (
(1,'普通用户'),
(2,'VIP'),
(3,'SVIP')
)
user_type = models.IntegerField(choices=USER_TYPE)
username = models.CharField(max_length=32)
password = models.CharField(max_length=64)
class UserToken(models.Model):
user = models.OneToOneField(UserInfo,on_delete=models.CASCADE)
token = models.CharField(max_length=64)
2.4.views
用户登录(返回token并保存到数据库)
from django.shortcuts import render
from django.http import JsonResponse
from rest_framework.views import APIView
from API import models
def md5(user):
import hashlib
import time
#当前时间,相当于生成一个随机的字符串
ctime = str(time.time())
m = hashlib.md5(user)
m.update(ctime)
return m.hexdigest()
class AuthView(object):
def post(self,request,*args,**kwargs):
ret = {'code':1000,'msg':None}
try:
user = request._request.POST.get('username')
pwd = request._request.POST.get('password')
obj = models.UserInfo.objects.filter(username=user,password=pwd).first()
if not obj:
ret['code'] = 1001
ret['msg'] = '用户名或密码错误'
#为用户创建token
token = md5(user)
#存在就更新,不存在就创建
models.UserToken.objects.update_or_create(user=obj,defaults={'token':token})
ret['token'] = token
except Exception as e:
ret['code'] = 1002
ret['msg'] = '请求异常'
return JsonResponse(ret)
2.5.利用postman发请求
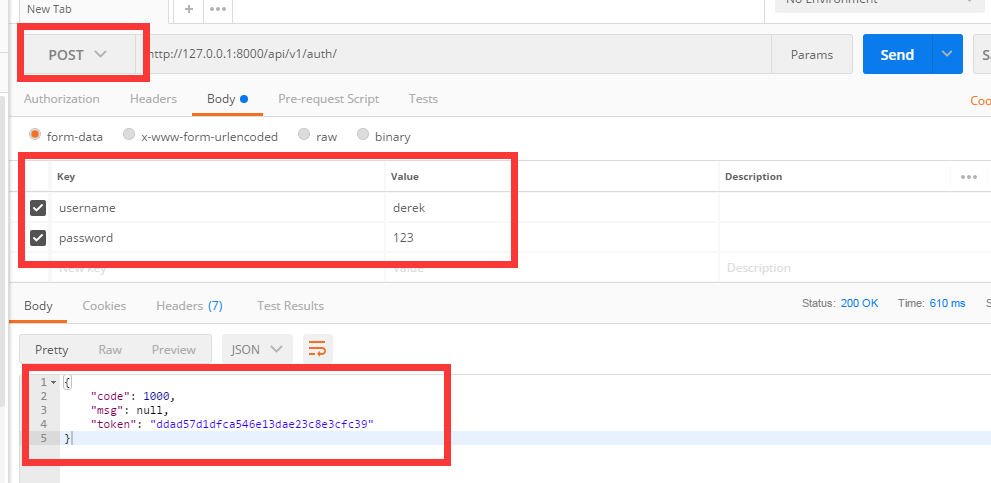
如果用户名和密码正确的话 会生成token值,下次该用户再登录时,token的值就会更新
数据库中可以看到token的值

当用户名或密码错误时,抛出异常
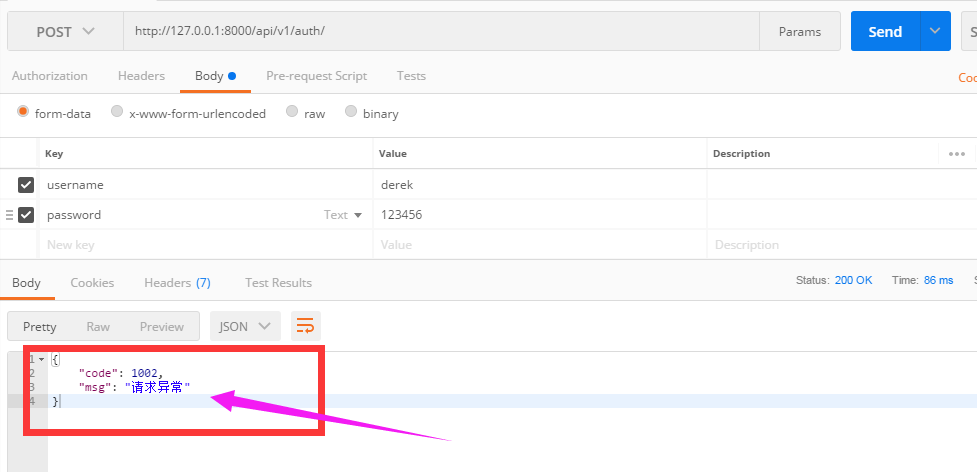
三、添加认证
进入到今天的主角了,开始认证了,认证使用装饰器不,好吧,这里不使用装饰器。
基于上面的例子,添加一个认证的类
3.1.url
from django.conf.urls import url
from django.contrib import admin
from API import views
urlpatterns = [
# url(r'^admin/', admin.site.urls),
url(r'api/v1/auth', views.AuthView.as_view()),
url(r'api/v1/order', views.OrderView.as_view()),
]
views.py
#!/usr/bin/env python
# coding:utf-8
from django.shortcuts import render
from django.http import JsonResponse
from rest_framework.views import APIView
from API import models
from rest_framework.request import Request
from rest_framework import exceptions
from rest_framework.authentication import BasicAuthentication
import hashlib
import time
def md5(user):
ctime = str(time.time())
m = hashlib.md5(user)
m.update(ctime)
return m.hexdigest()
class AuthView(APIView):
authentication_classes = []
def post(self,request,*args,**kwargs):
ret = {'code': 1000,'msg':None}
try:
user = request.POST.get('username')
pwd = request.POST.get('password')
print(user,pwd)
obj = models.UserInfo.objects.filter(username=user,password=pwd).first()
print('=============%s' %(obj))
if not obj:
ret['code'] = 1001
ret['msg'] = '用户名或者密码错误'
# 为用户创建token
token = md5(user)
# 存在就更新,不存在就创建
models.UserToken.objects.update_or_create(user=obj,defaults={'token':token})
ret['token'] = token
except Exception as e:
ret['code'] = 1002
ret['msg'] = '请求异常'
# user = request._request.POST.get('username')
# pwd = request._request.POST.get('password')
# print(user,pwd)
# obj = models.UserInfo.objects.filter(username=user,password=pwd).first()
# print('=============%s' %(obj))
# if not obj:
# ret['code'] = 1001
# ret['msg'] = '用户名或者密码错误'
# # 为用户创建token
# token = md5(user)
# # 存在就更新,不存在就创建
# models.UserToken.objects.update_or_create(user=obj,defaults={'token':token})
# ret['token'] = token
# return JsonResponse(ret)
ORDER_DICT = {
1: {
'name': 'apple',
'price': 15,
},
2: {
'name': 'dog',
'price': 100
}
}
class Authentication(APIView):
"""
认证类
"""
def authenticate(self,request):
token = request._request.GET.get('token')
token_obj = models.UserToken.objects.filter(token=token).first()
if not token_obj:
raise exceptions.AuthenticationFailed('用户认证失败')
# 在rest framework内部会将这2个字段赋值给request,以供后续使用
return (token_obj.user,token_obj)
def authenticate_header(self,reqeust):
pass
class OrderView(APIView):
"""订单相关业务"""
# authentication_classes = [] # 添加认证
def get(self,request,*args,**kwargs):
print(request.user)
print(request.auth)
ret = {'code':1000,'msg':None, 'data': None}
try:
ret['data'] = ORDER_DICT
except Exception as e:
pass
return JsonResponse(ret)
3.3用postman发get请求
请求的时候没有带token,可以看到会显示“用户认证失败”
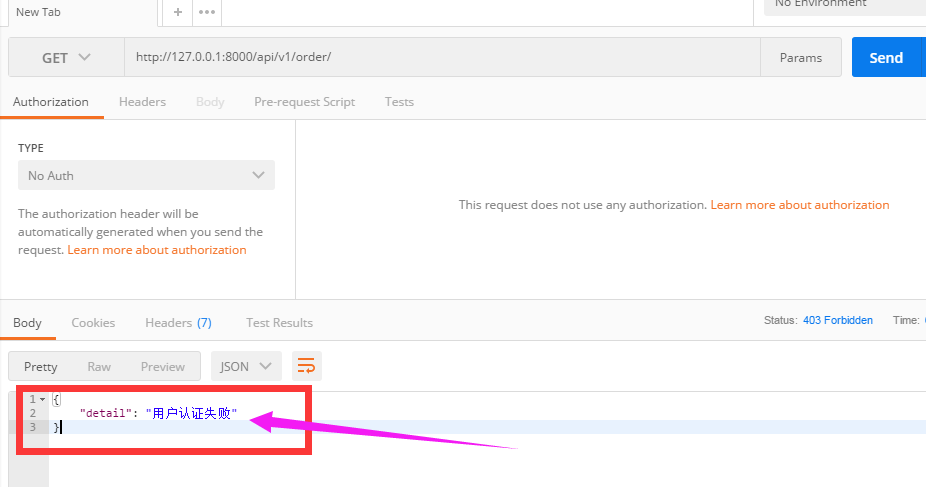
这样就达到了认证的效果,django-rest-framework的认证是怎么实现的呢,下面基于这个例子来剖析drf的源码。
四、drf的认证源码分析
好吧,我是骗你的,上面的还是配角,今天的主角现在才开始出现。
源码流程图
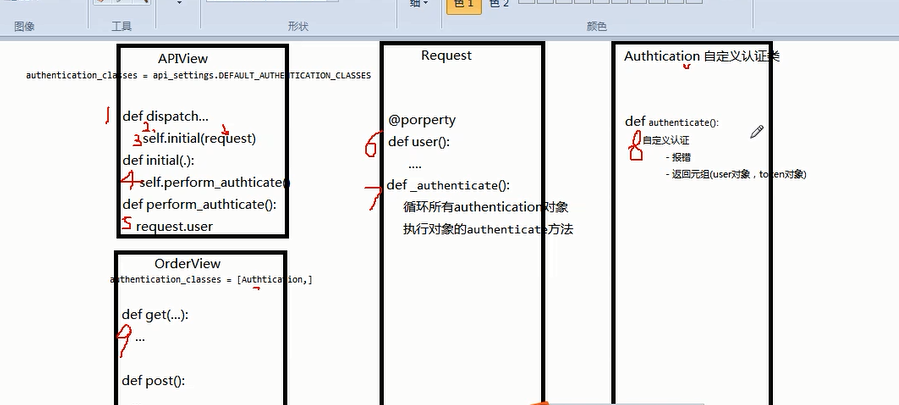
请求先到dispatch
dispatch()主要做了两件事
- 封装request
- 认证
具体看我写的代码里面的注释
def dispatch(self, request, *args, **kwargs):
"""
`.dispatch()` is pretty much the same as Django's regular dispatch,
but with extra hooks for startup, finalize, and exception handling.
"""
self.args = args
self.kwargs = kwargs
#对原始request进行加工,丰富了一些功能
#Request(
# request,
# parsers=self.get_parsers(),
# authenticators=self.get_authenticators(),
# negotiator=self.get_content_negotiator(),
# parser_context=parser_context
# )
#request(原始request,[BasicAuthentications对象,])
#获取原生request,request._request
#获取认证类的对象,request.authticators
#1.封装request
request = self.initialize_request(request, *args, **kwargs)
self.request = request
self.headers = self.default_response_headers # deprecate?
try:
#2.认证
self.initial(request, *args, **kwargs)
# Get the appropriate handler method
if request.method.lower() in self.http_method_names:
handler = getattr(self, request.method.lower(),
self.http_method_not_allowed)
else:
handler = self.http_method_not_allowed
response = handler(request, *args, **kwargs)
except Exception as exc:
response = self.handle_exception(exc)
self.response = self.finalize_response(request, response, *args, **kwargs)
return self.response
4.1.reuqest
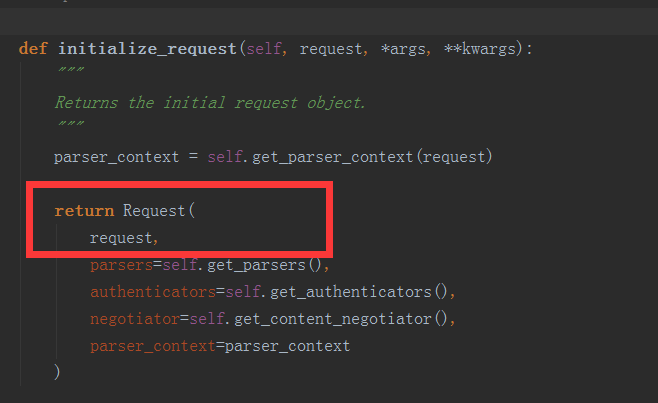
(1)initialize_request()
可以看到initialize()就是封装原始request
def initialize_request(self, request, *args, **kwargs):
"""
Returns the initial request object.
"""
parser_context = self.get_parser_context(request)
return Request(
request,
parsers=self.get_parsers(),
authenticators=self.get_authenticators(), #[BasicAuthentication(),],把对象封装到request里面了
negotiator=self.get_content_negotiator(), parser_context=parser_context )
(2)get_authenticators()
通过列表生成式,返回对象的列表
def get_authenticators(self):
"""
Instantiates and returns the list of authenticators that this view can use.
"""
return [auth() for auth in self.authentication_classes]
(3)authentication_classes
APIView里面有个 authentication_classes 字段
可以看到默认是去全局的配置文件找(api_settings)
class APIView(View):
# The following policies may be set at either globally, or per-view.
renderer_classes = api_settings.DEFAULT_RENDERER_CLASSES
parser_classes = api_settings.DEFAULT_PARSER_CLASSES
authentication_classes = api_settings.DEFAULT_AUTHENTICATION_CLASSES
throttle_classes = api_settings.DEFAULT_THROTTLE_CLASSES
permission_classes = api_settings.DEFAULT_PERMISSION_CLASSES
content_negotiation_class = api_settings.DEFAULT_CONTENT_NEGOTIATION_CLASS
metadata_class = api_settings.DEFAULT_METADATA_CLASS
versioning_class = api_settings.DEFAULT_VERSIONING_CLASS
4.2.认证
self.initial(request, *args, **kwargs)
def dispatch(self, request, *args, **kwargs):
"""
`.dispatch()` is pretty much the same as Django's regular dispatch,
but with extra hooks for startup, finalize, and exception handling.
"""
self.args = args
self.kwargs = kwargs
#对原始request进行加工,丰富了一些功能
#Request(
# request,
# parsers=self.get_parsers(),
# authenticators=self.get_authenticators(),
# negotiator=self.get_content_negotiator(),
# parser_context=parser_context
# )
#request(原始request,[BasicAuthentications对象,])
#获取原生request,request._request
#获取认证类的对象,request.authticators
#1.封装request
request = self.initialize_request(request, *args, **kwargs)
self.request = request
self.headers = self.default_response_headers # deprecate?
try:
#2.认证
self.initial(request, *args, **kwargs)
# Get the appropriate handler method
if request.method.lower() in self.http_method_names:
handler = getattr(self, request.method.lower(),
self.http_method_not_allowed)
else:
handler = self.http_method_not_allowed
response = handler(request, *args, **kwargs)
except Exception as exc:
response = self.handle_exception(exc)
self.response = self.finalize_response(request, response, *args, **kwargs)
return self.response
(1)initial()
主要看 self.perform_authentication(request),实现认证
def initial(self, request, *args, **kwargs):
"""
Runs anything that needs to occur prior to calling the method handler.
"""
self.format_kwarg = self.get_format_suffix(**kwargs)
# Perform content negotiation and store the accepted info on the request
neg = self.perform_content_negotiation(request)
request.accepted_renderer, request.accepted_media_type = neg
# Determine the API version, if versioning is in use.
version, scheme = self.determine_version(request, *args, **kwargs)
request.version, request.versioning_scheme = version, scheme
# Ensure that the incoming request is permitted
#3.实现认证
self.perform_authentication(request)
self.check_permissions(request)
self.check_throttles(request)
(2)perform_authentication()
调用了request.user
def perform_authentication(self, request):
"""
Perform authentication on the incoming request.
Note that if you override this and simply 'pass', then authentication
will instead be performed lazily, the first time either
`request.user` or `request.auth` is accessed.
"""
request.user
(3)user
request.user的request的位置
点进去可以看到Request有个user方法,加 @property 表示调用user方法的时候不需要加括号“user()”,可以直接调用:request.user
@property
def user(self):
"""
Returns the user associated with the current request, as authenticated
by the authentication classes provided to the request.
"""
if not hasattr(self, '_user'):
with wrap_attributeerrors():
#获取认证对象,进行一步步的认证
self._authenticate()
return self._user
(4)_authenticate()
循环所有authenticator对象,这里的对象还记得是谁传递过来的不,Request那边传过来的,尼玛,今天再看突然看懂了。这里最终是通过settings的配置文件中定义你的认证类的路径,然后找到你的认证类,然后在这边循环的,最终执行你认证类中的认证方法
def _authenticate(self):
"""
Attempt to authenticate the request using each authentication instance
in turn.
"""
#循环认证类的所有对象
#执行对象的authenticate方法
for authenticator in self.authenticators:
try:
#执行认证类的authenticate方法
#这里分三种情况
#1.如果authenticate方法抛出异常,self._not_authenticated()执行
#2.有返回值,必须是元组:(request.user,request.auth)
#3.返回None,表示当前认证不处理,等下一个认证来处理
user_auth_tuple = authenticator.authenticate(self)
except exceptions.APIException:
self._not_authenticated()
raise
if user_auth_tuple is not None:
self._authenticator = authenticator
self.user, self.auth = user_auth_tuple
return
self._not_authenticated()
返回值就是例子中的:
token_obj.user-->>request.user
token_obj-->>request.auth
这俩货就是
UserInfo object
UserToken object
其实request.user 和 request.auth 都是封装在了Request.py中的2个特殊方法,为啥说他们特殊呢,因为在方法中加入了@property的装饰器,这个装饰器加上,我们在调用的时候就可以像调用属性的写法那样调用方法了,是不是很有意思呢。
@property
def auth(self):
"""
Returns any non-user authentication information associated with the
request, such as an authentication token.
"""
if not hasattr(self, '_auth'):
with wrap_attributeerrors():
self._authenticate()
return self._auth
是2个对象。
#在rest framework内部会将这两个字段赋值给request,以供后续操作使用 return (token_obj.user,token_obj) #例子中的return
当都没有返回值,就执行self._not_authenticated(),相当于匿名用户,没有通过认证
def _not_authenticated(self):
"""
Set authenticator, user & authtoken representing an unauthenticated request.
Defaults are None, AnonymousUser & None.
"""
self._authenticator = None
if api_settings.UNAUTHENTICATED_USER:
self.user = api_settings.UNAUTHENTICATED_USER() #AnonymousUser匿名用户
else:
self.user = None
if api_settings.UNAUTHENTICATED_TOKEN:
self.auth = api_settings.UNAUTHENTICATED_TOKEN() #None
else:
self.auth = None
面向对象知识:
子类继承 父类,调用方法的时候:
- 优先去自己里面找有没有这个方法,有就执行自己的
- 只有当自己里面没有这个方法的时候才会去父类找
因为authenticate方法我们自己写,所以当执行authenticate()的时候就是执行我们自己写的认证
父类中的authenticate方法
def authenticate(self, request):
return (self.force_user, self.force_token)
我们自己写的
class Authentication(APIView):
'''用于用户登录验证'''
def authenticate(self,request):
token = request._request.GET.get('token')
token_obj = models.UserToken.objects.filter(token=token).first()
if not token_obj:
raise exceptions.AuthenticationFailed('用户认证失败')
#在rest framework内部会将这两个字段赋值给request,以供后续操作使用
return (token_obj.user,token_obj)
认证的流程就是上面写的,弄懂了原理,再写代码就更容易理解为什么了。
4.3.配置文件
继续解读源码

默认是去全局配置文件中找,所以我们应该在settings.py中配置好路径
api_settings源码
api_settings = APISettings(None, DEFAULTS, IMPORT_STRINGS)
def reload_api_settings(*args, **kwargs):
setting = kwargs['setting']
if setting == 'REST_FRAMEWORK':
api_settings.reload()
setting中‘REST_FRAMEWORK’中找
全局配置方法:
API文件夹下面新建文件夹utils,再新建auth.py文件,里面写上认证的类
settings.py
#设置全局认证
REST_FRAMEWORK = {
"DEFAULT_AUTHENTICATION_CLASSES":['API.utils.auth.Authentication',] #里面写你的认证的类的路径
}
auth.py
# API/utils/auth.py
from rest_framework import exceptions
from API import models
class Authentication(object):
'''用于用户登录验证'''
def authenticate(self,request):
token = request._request.GET.get('token')
token_obj = models.UserToken.objects.filter(token=token).first()
if not token_obj:
raise exceptions.AuthenticationFailed('用户认证失败')
#在rest framework内部会将这两个字段赋值给request,以供后续操作使用
return (token_obj.user,token_obj)
def authenticate_header(self, request):
pass
在settings里面设置的全局认证,所有业务都需要经过认证,如果想让某个不需要认证,只需要在其中添加下面的代码:
authentication_classes = [] #里面为空,代表不需要认证
#!/usr/bin/env python
# coding:utf-8
from django.shortcuts import render
from django.http import JsonResponse
from rest_framework.views import APIView
from API import models
from rest_framework.request import Request
from rest_framework import exceptions
from rest_framework.authentication import BasicAuthentication
import hashlib
import time
def md5(user):
ctime = str(time.time())
m = hashlib.md5(user)
m.update(ctime)
return m.hexdigest()
class AuthView(APIView):
authentication_classes = []
def post(self,request,*args,**kwargs):
ret = {'code': 1000,'msg':None}
try:
user = request.POST.get('username')
pwd = request.POST.get('password')
print(user,pwd)
obj = models.UserInfo.objects.filter(username=user,password=pwd).first()
print('=============%s' %(obj))
if not obj:
ret['code'] = 1001
ret['msg'] = '用户名或者密码错误'
# 为用户创建token
token = md5(user)
# 存在就更新,不存在就创建
models.UserToken.objects.update_or_create(user=obj,defaults={'token':token})
ret['token'] = token
except Exception as e:
ret['code'] = 1002
ret['msg'] = '请求异常'
# user = request._request.POST.get('username')
# pwd = request._request.POST.get('password')
# print(user,pwd)
# obj = models.UserInfo.objects.filter(username=user,password=pwd).first()
# print('=============%s' %(obj))
# if not obj:
# ret['code'] = 1001
# ret['msg'] = '用户名或者密码错误'
# # 为用户创建token
# token = md5(user)
# # 存在就更新,不存在就创建
# models.UserToken.objects.update_or_create(user=obj,defaults={'token':token})
# ret['token'] = token
# return JsonResponse(ret)
ORDER_DICT = {
1: {
'name': 'apple',
'price': 15,
},
2: {
'name': 'dog',
'price': 100
}
}
# class Authentication(APIView):
# """
# 认证类
# """
# def authenticate(self,request):
# token = request._request.GET.get('token')
# token_obj = models.UserToken.objects.filter(token=token).first()
# if not token_obj:
# raise exceptions.AuthenticationFailed('用户认证失败')
# # 在rest framework内部会将这2个字段赋值给request,以供后续使用
# return (token_obj.user,token_obj)
#
# def authenticate_header(self,reqeust):
# pass
class OrderView(APIView):
"""订单相关业务"""
# authentication_classes = [] # 添加认证
def get(self,request,*args,**kwargs):
print(request.user)
print(request.auth)
ret = {'code':1000,'msg':None, 'data': None}
try:
ret['data'] = ORDER_DICT
except Exception as e:
pass
return JsonResponse(ret)
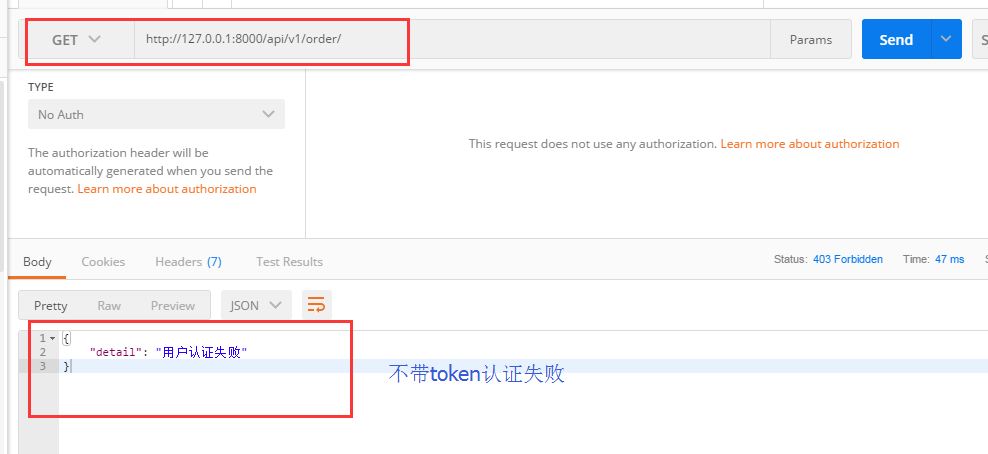
再测试一下我们的代码
不带token发请求
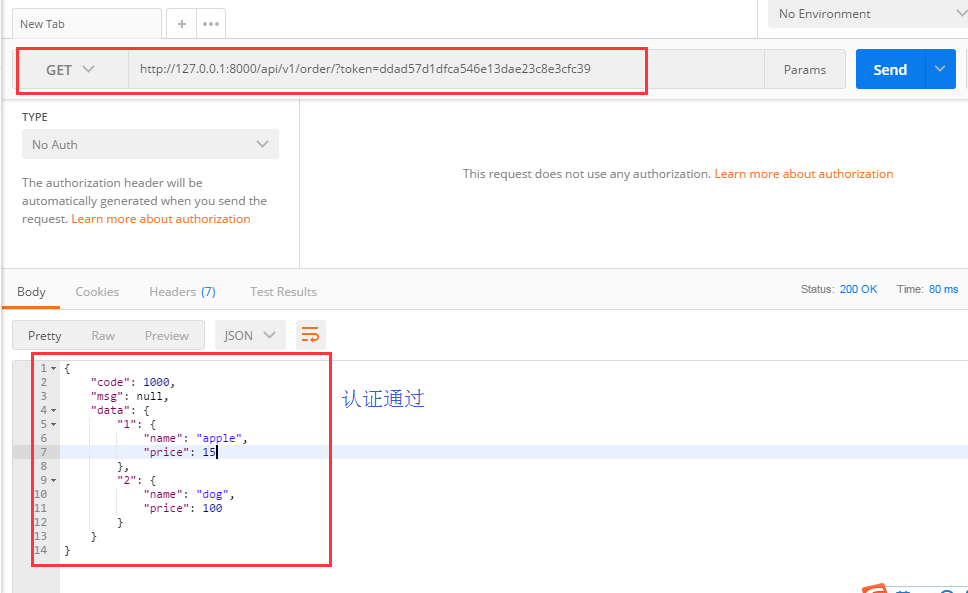
带token发请求
五、drf的内置认证
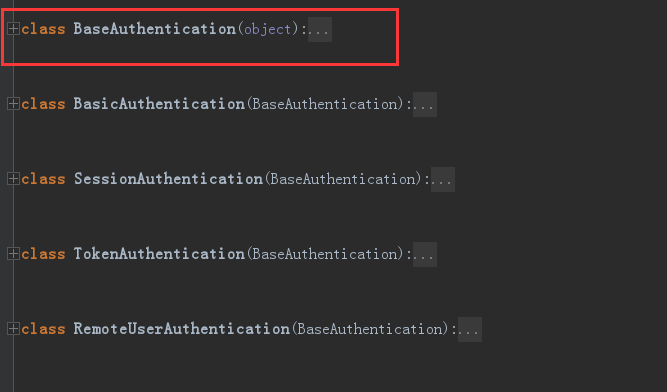
rest_framework里面内置了一些认证,我们自己写的认证类都要继承内置认证类 "BaseAuthentication"
4.1.BaseAuthentication源码:
class BaseAuthentication(object):
"""
All authentication classes should extend BaseAuthentication.
"""
def authenticate(self, request):
"""
Authenticate the request and return a two-tuple of (user, token).
"""
#内置的认证类,authenticate方法,如果不自己写,默认则抛出异常
raise NotImplementedError(".authenticate() must be overridden.")
def authenticate_header(self, request):
"""
Return a string to be used as the value of the `WWW-Authenticate`
header in a `401 Unauthenticated` response, or `None` if the
authentication scheme should return `403 Permission Denied` responses.
"""
#authenticate_header方法,作用是当认证失败的时候,返回的响应头
pass
4.2.修改自己写的认证类
自己写的Authentication必须继承内置认证类BaseAuthentication
# API/utils/auth/py
from rest_framework import exceptions
from API import models
from rest_framework.authentication import BaseAuthentication
class Authentication(BaseAuthentication):
'''用于用户登录验证'''
def authenticate(self,request):
token = request._request.GET.get('token')
token_obj = models.UserToken.objects.filter(token=token).first()
if not token_obj:
raise exceptions.AuthenticationFailed('用户认证失败')
#在rest framework内部会将这两个字段赋值给request,以供后续操作使用
return (token_obj.user,token_obj)
def authenticate_header(self, request):
pass
4.3.其它内置认证类
rest_framework里面还内置了其它认证类,我们主要用到的就是BaseAuthentication,剩下的很少用到
六、总结
自己写认证类方法梳理
(1)创建认证类
- 继承BaseAuthentication --->>1.重写authenticate方法;2.authenticate_header方法直接写pass就可以(这个方法必须写)
(2)authenticate()返回值(三种)
- None ----->>>当前认证不管,等下一个认证来执行
- raise exceptions.AuthenticationFailed('用户认证失败') # from rest_framework import exceptions
- 有返回值元祖形式:(元素1,元素2) #元素1复制给request.user; 元素2复制给request.auth
(3)局部使用
- authentication_classes = [BaseAuthentication,]
(4)全局使用
#设置全局认证
REST_FRAMEWORK = {
"DEFAULT_AUTHENTICATION_CLASSES":['API.utils.auth.Authentication',]
}
源码流程
--->>dispatch
--封装request
---获取定义的认证类(全局/局部),通过列表生成式创建对象
---initial
----peform_authentication
-----request.user (每部循环创建的对象)
终于抄写完成了哈哈。写到这里,听到一个好玩的事情,一个开发问:公司怎么FQ啊? 同事回答:“你觉得应该怎么翻,当然是用你的手和你的脚FQ了”。
今天抽烟突然想通了很多事情,有些人注定逝去,有些人在你的生命中昙花一现,有些人在你的生命中来来回回。所以,抽烟有害健康,及时戒烟可以不要胡思乱想。

 浙公网安备 33010602011771号
浙公网安备 33010602011771号