k8s创建StorageClass资源挂载报错:waiting for a volume to be created, either by external provisioner "wangzy-nfs-storage" or manually created by system administrator
背景:
创建StorageClass存储类资源时,挂载pvc时一直显示pending状态
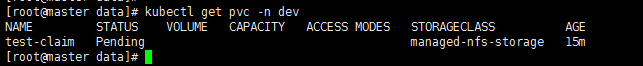
报错信息:
waiting for a volume to be created, either by external provisioner "wangzy-nfs-storage" or manually created by system administrator
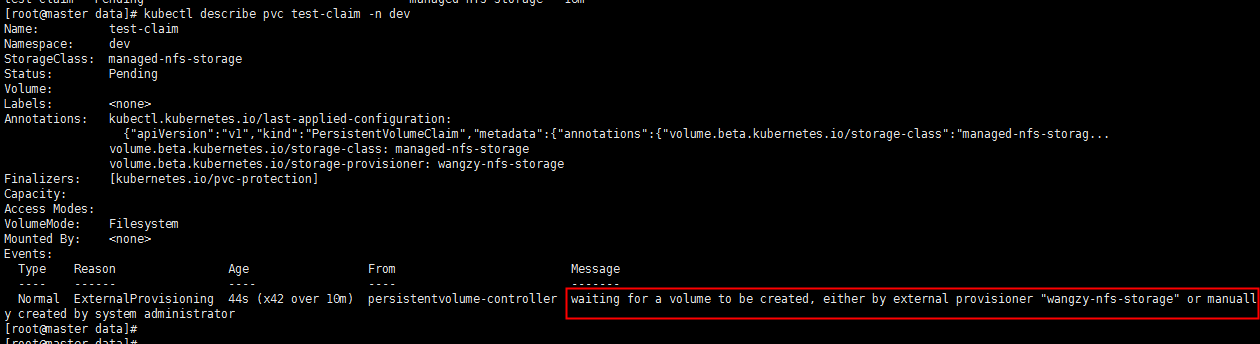
翻译结果:正在等待外部供应器“wangzy nfs storage”或系统管理员手动创建的卷
初步判断是存储供应的问题,也有些网上资料说是selfLink导致,因为kubernetes 1.20版本 禁用了 selfLink导致,本次分别从这两处解决。
一:设置selfLink参数
1.1 添加参数
spec: containers: - command: ... ... - kube-apiserver - --feature-gates=RemoveSelfLink=false #手动添加
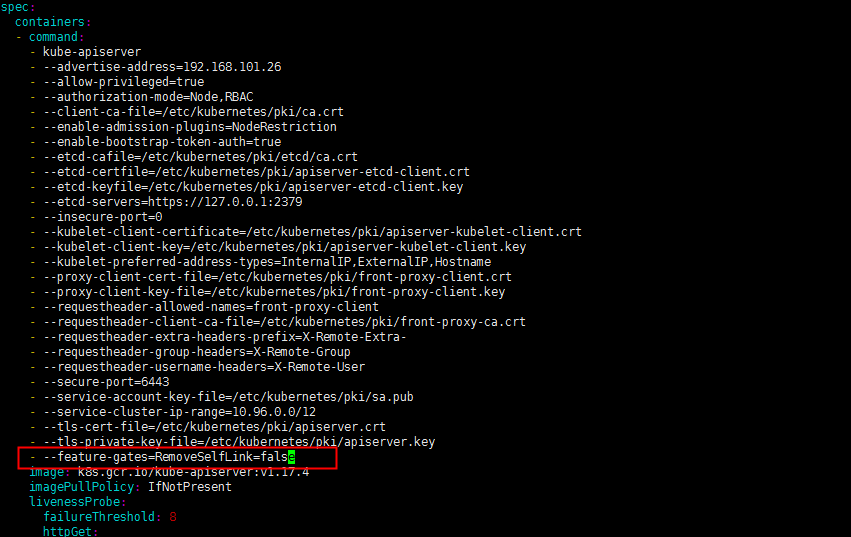
1.2 重启api-server
kubectl apply -f /etc/kubernetes/manifests/kube-apiserver.yaml
1.3 再次查看,发现 pvc 状态依旧是pending
于是查看供应链是否出问题
二:供应链查看
2.1 查看 nfs-client-provisioner,发现报错
[root@master ~]# kubectl get pods -n dev NAME READY STATUS RESTARTS AGE nfs-client-provisioner-68c7ddcdc7-nwx2w 1/1 Running 0 18m [root@master ~]# kubectl logs -f nfs-client-provisioner-68c7ddcdc7-nwx2w -n dev
报错内容如下:
E0414 06:13:35.631549 1 leaderelection.go:234] error retrieving resource lock dev/wangzy-nfs-provisioner: endpoints "wangzy-nfs-provisioner" is forbidden: User "system:serviceaccount:dev:nfs-client-provisioner" cannot get resource "endpoints" in API group "" in the namespace "dev"
在日志中可以得到信息: default的namespace下,default 账户serviceaccount 不能在API group "" 获取endpoints 资源。
因此我们需要创建一个角色,使其拥有对endpoint资源操作的权限,并且角色与账户进行绑定。
2.2 修改rbac,添加权限,网上很多,我这边列出其中权限部分
apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole # 创建集群角色 metadata: name: nfs-client-provisioner-runner # 角色权限 rules: - apiGroups: [""] resources: ["persistentvolumes"] verbs: ["get", "list", "watch", "create", "delete"] - apiGroups: [""] resources: ["persistentvolumeclaims"] verbs: ["get", "list", "watch", "update"] - apiGroups: ["storage.k8s.io"] resources: ["storageclasses"] verbs: ["get", "list", "watch"] - apiGroups: [""] resources: ["events"] verbs: ["watch", "create", "update", "patch"] - apiGroups: [""] resources: ["services"] verbs: ["get"] - apiGroups: ["extensions"] resources: ["podsecuritypolicies"] resourceNames: ["nfs-provisioner"] verbs: ["use"] - apiGroups: [""] resources: ["endpoints"] verbs: ["get", "list", "watch", "create", "update", "patch"]
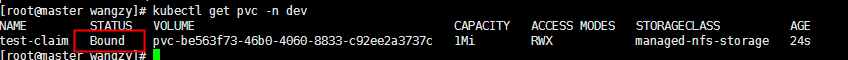
2.3 重启服务,发现状态变为bound
附加:
此处还碰到一个权限问题,也记录一下,报错信息如下
I0414 06:46:50.366392 1 event.go:221] Event(v1.ObjectReference{Kind:"PersistentVolumeClaim", Namespace:"dev", Name:"test-claim", UID:"d4d65bfc-3452-4eca-8629-da1aac58550b", APIVersion:"v1", ResourceVersion:"10396861", FieldPath:""}): type: 'Warning' reason: 'ProvisioningFailed' failed to provision volume with StorageClass "managed-nfs-storage": unable to create directory to provision new pv: mkdir /persistentvolumes/dev-test-claim-pvc-d4d65bfc-3452-4eca-8629-da1aac58550b: permission denied
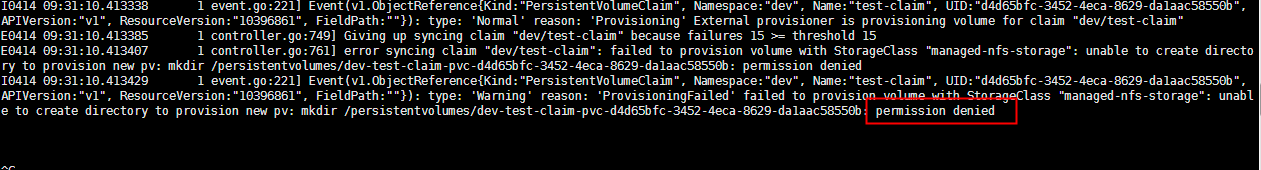
原因是因为共享目录没有权限,给其添加权限,然后重启provisioner服务
[root@master wangzy]# chmod -R 777 /root/data/ #/root/data/为我的共享目录
[root@master wangzy]# kubectl apply -f provisioner-02.yaml






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 【自荐】一款简洁、开源的在线白板工具 Drawnix
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
2020-04-15 Sublime Text 和 Python 结合使用,加快捷方式创建