ELK(10):ELK-通过syslog收集haproxy的日志
ELK(10):ELK-通过syslog收集haproxy的日志
syslog一般适合收集交换机、路由器这类网络设备的日志
我们这里收集一下haproxy
haproxy的安装,就不说了参考:https://www.cnblogs.com/wangxu01/articles/11196522.html
本文的环境也是根据这个。
Haproxy配置日志
# vim /etc/haproxy/haproxy.cfg #设置local6 这个和rsyslog要一致 log 127.0.0.1 local6 info
创建日志目录
sudo mkdir /var/log/haproxy sudo chown -R haproxy.haproxy /var/log/haproxy
配置rsyslog
# vim /etc/rsyslog.conf # 打开15,16,19,20行注释 $ModLoad imudp $UDPServerRun 514 $ModLoad imtcp $InputTCPServerRun 514 #添加haproxy配置 local6.* /var/log/haproxy/haproxy.log # 日志记录文件 local6.* @@10.6.76.27:1514 # 本地IP和监听端口
重启rsyslog和haproxy
sudo systemctl restart rsyslog sudo systemctl restart haproxy
haproxy日志配置文件输出到控制台
#[admin@pe-jira conf.d]$ cat rsyslog.conf input{ syslog{ port => "1514" type=> "haproxy-log" } } output{ stdout{ codec => "rubydebug" }
测试输出到控制台
sudo /usr/share/logstash/bin/logstash -f rsyslog.conf
我们能看到调起的端口

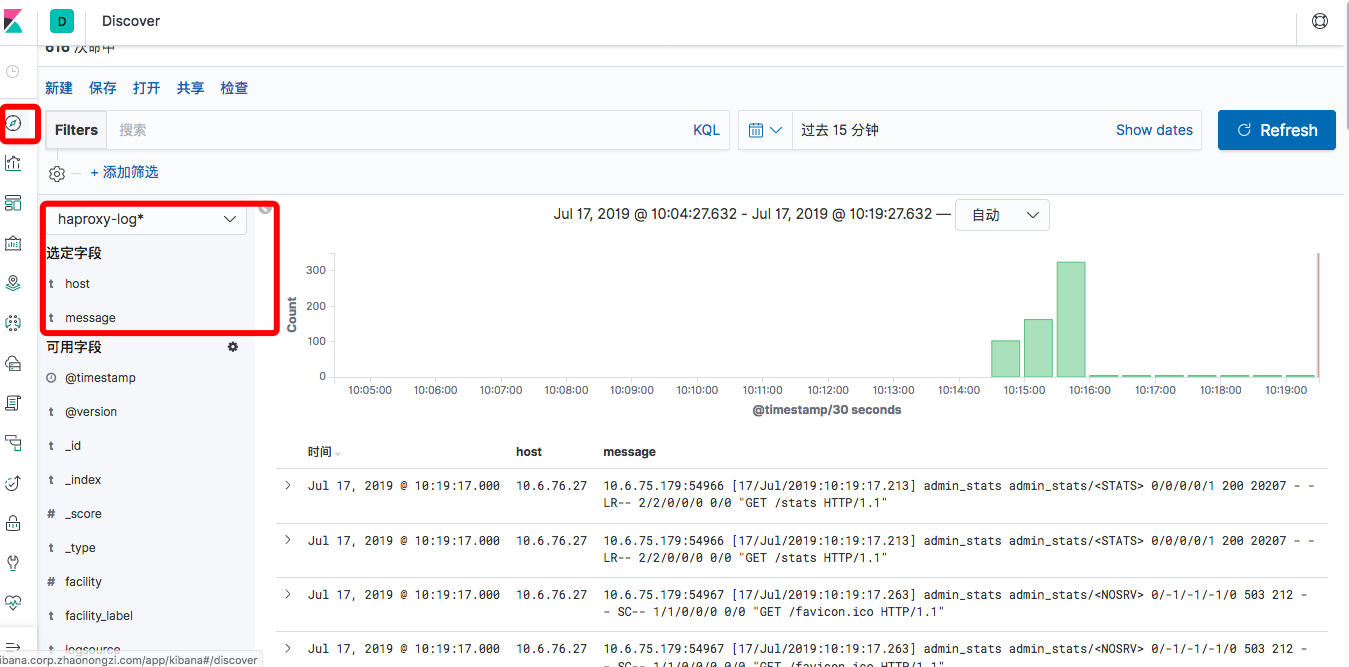
访问haproxy之后控制台输出
{ "logsource" => "localhost", "timestamp" => "Jul 17 10:10:49", "type" => "haproxy-log", "program" => "haproxy", "pid" => "5359", "priority" => 182, "@timestamp" => 2019-07-17T02:10:49.000Z, "@version" => "1", "severity_label" => "Informational", "severity" => 6, "message" => "10.6.75.179:54486 [17/Jul/2019:10:10:49.404] admin_stats admin_stats/<NOSRV> 0/-1/-1/-1/0 503 212 - - SC-- 1/1/0/0/0 0/0 \"GET /favicon.ico HTTP/1.1\"\n", "facility_label" => "local6", "host" => "10.6.76.27", "facility" => 22 }
haproxy日志配置文件输出到elasticsearch
#[admin@pe-jira conf.d]$ cat rsyslog.conf input{ syslog{ port => "1514" type=> "haproxy-log-1514" } } output{ if [type] == "haproxy-log-1514"{ elasticsearch { hosts => ["10.6.76.27:9200"] index => "haproxy-log-1514-%{+YYYY.MM.dd}" } } }
重启logstash
sudo systemctl restart logstash
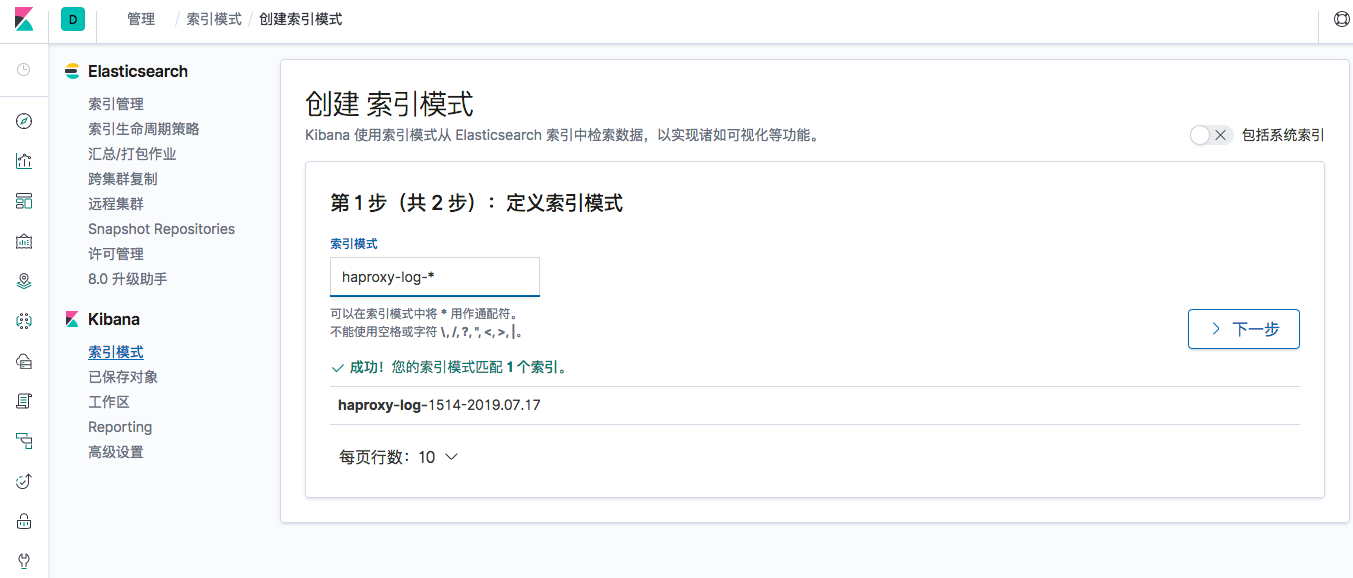
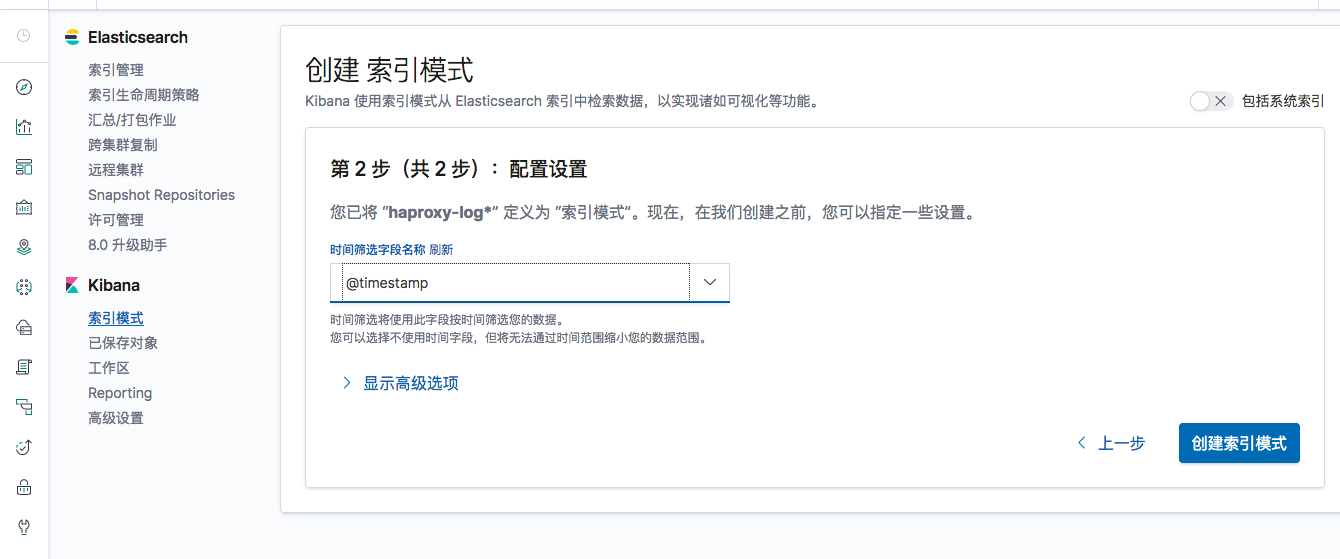
配置kibana