SSO单点登录 - Authelia
Authelia
贴一下官方描述:
Authelia is an open source authentication and authorization server protecting modern web applications by collaborating with reverse proxies such as NGINX, Traefik and HAProxy. Consequently, no code is required to protect your apps.
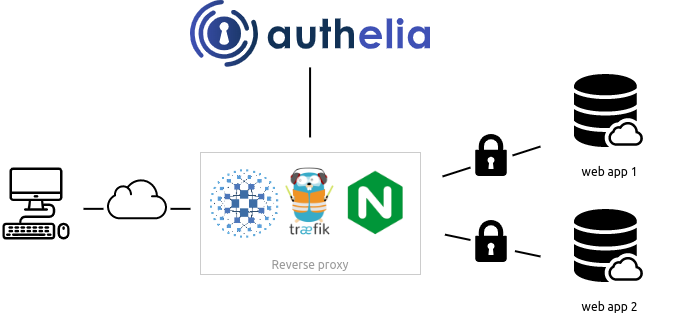
完整的工作流
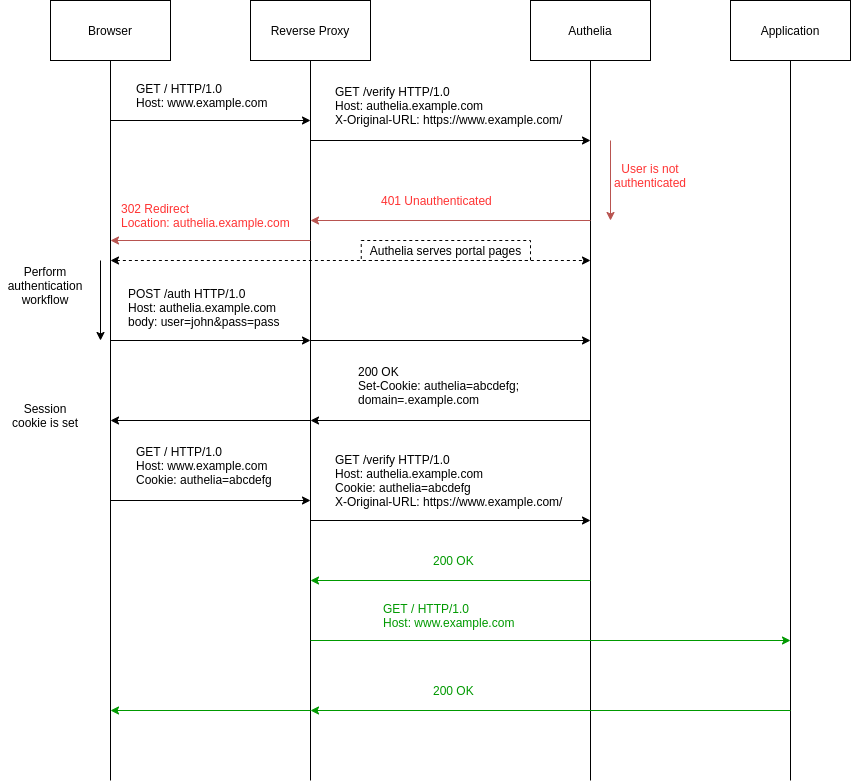
注意这里仅支持HTTPS
因为session cookie只能通过https传输
附一个字签证书的方式
docker run authelia/authelia authelia certificates generate --host example.com --dir /tmp/certs/
Authelia启动方式
# 下载二进制文件
# 下载地址https://github.com/authelia/authelia/releases
./authelia-linux-amd64 --config config.yml
Authelia的配置文件
# config.yml
host: 0.0.0.0
port: 9091
log_level: debug
jwt_secret: a_very_important_secret
default_redirection_url: http://public.xxx.com
totp:
issuer: authelia.com
authentication_backend:
file:
path: /opt/authelia/users_database.yml
access_control:
default_policy: deny
rules:
- domain: public.xxx.com
policy: one_factor # bypass
- domain: api.xxx.com
policy: one_factor
session:
name: authelia_session
secret: unsecure_session_secret
expiration: 3600 # 1 hour
inactivity: 300 # 5 minutes
domain: xxx.com # Should match whatever your root protected domain is
redis:
host: 127.0.0.1
port: 6379
# Password can also be set using a secret: https://docs.authelia.com/configuration/secrets.html
# password: authelia
# This is the Redis DB Index https://redis.io/commands/select (sometimes referred to as database number, DB, etc).
database_index: 0
regulation:
max_retries: 3
find_time: 120
ban_time: 300
storage:
local:
path: /opt/authelia/db.sqlite3
notifier:
filesystem:
filename: /opt/authelia/notification.txt
# users_database.yml
###############################################################
# Users Database #
###############################################################
# This file can be used if you do not have an LDAP set up.
# List of users
users:
wrx:
displayname: "wrx"
password: "$6$rounds=50000$BpLnfgDsc2WD8F2q$Zis.ixdg9s/UOJYrs56b5QEZFiZECu0qZVNsIYxBaNJ7ucIL.nlxVCT5tqh8KHG8X4tlwCFm5r6NTOZZ5qRFN/"
email: wrx@xxx.com
groups:
- admins
- dev
Nginx配置文件
server {
server_name authe.xxx.com;
listen 80;
# listen 443 ssl http2;
# include /config/nginx/ssl.conf;
location / {
set $upstream_authelia http://127.0.0.1:9091; # This example assumes a Docker deployment
proxy_pass $upstream_authelia;
include /etc/nginx/conf.d/proxy.conf;
}
}
server {
server_name api.xxx.com;
listen 443 ssl http2;
# include /config/nginx/ssl.conf;
ssl_certificate /opt/authelia/xxx.pem;
ssl_certificate_key /opt/authelia/xxx.key;
ssl_session_timeout 5m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:HIGH:!aNULL:!MD5:!RC4:!DHE;
ssl_prefer_server_ciphers on;
include /etc/nginx/conf.d/authelia.conf; # Virtual endpoint to forward auth requests
location / {
set $upstream_nextcloud http://127.0.0.1:5000;
proxy_pass $upstream_nextcloud;
include /etc/nginx/conf.d/auth.conf; # Activates Authelia for specified route/location, please ensure you have setup the domain in your configuration.yml
include /etc/nginx/conf.d/proxy.conf; # Reverse proxy configuration
}
}
Nginx - conf.d/
# /etc/nginx/conf.d/auth.conf
# Basic Authelia Config
# Send a subsequent request to Authelia to verify if the user is authenticated
# and has the right permissions to access the resource.
auth_request /authelia;
# Set the `target_url` variable based on the request. It will be used to build the portal
# URL with the correct redirection parameter.
auth_request_set $target_url $scheme://$http_host$request_uri;
# Set the X-Forwarded-User and X-Forwarded-Groups with the headers
# returned by Authelia for the backends which can consume them.
# This is not safe, as the backend must make sure that they come from the
# proxy. In the future, it's gonna be safe to just use OAuth.
auth_request_set $user $upstream_http_remote_user;
auth_request_set $groups $upstream_http_remote_groups;
proxy_set_header Remote-User $user;
proxy_set_header Remote-Groups $groups;
# If Authelia returns 401, then nginx redirects the user to the login portal.
# If it returns 200, then the request pass through to the backend.
# For other type of errors, nginx will handle them as usual.
error_page 401 =302 http://authe.wangruixing.com/?rd=$target_url;
# /etc/nginx/conf.d/authelia.conf
# Virtual endpoint created by nginx to forward auth requests.
location /authelia {
internal;
set $upstream_authelia http://127.0.0.1:9091/api/verify;
proxy_pass_request_body off;
proxy_pass $upstream_authelia;
proxy_set_header Content-Length "";
# Timeout if the real server is dead
proxy_next_upstream error timeout invalid_header http_500 http_502 http_503;
# [REQUIRED] Needed by Authelia to check authorizations of the resource.
# Provide either X-Original-URL and X-Forwarded-Proto or
# X-Forwarded-Proto, X-Forwarded-Host and X-Forwarded-Uri or both.
# Those headers will be used by Authelia to deduce the target url of the user.
# Basic Proxy Config
client_body_buffer_size 128k;
proxy_set_header Host $host;
proxy_set_header X-Original-URL $scheme://$http_host$request_uri;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Host $http_host;
proxy_set_header X-Forwarded-Uri $request_uri;
proxy_set_header X-Forwarded-Ssl on;
proxy_redirect http:// $scheme://;
proxy_http_version 1.1;
proxy_set_header Connection "";
proxy_cache_bypass $cookie_session;
proxy_no_cache $cookie_session;
proxy_buffers 4 32k;
# Advanced Proxy Config
send_timeout 5m;
proxy_read_timeout 240;
proxy_send_timeout 240;
proxy_connect_timeout 240;
}
# /etc/nginx/conf.d/proxy.conf
client_body_buffer_size 128k;
#Timeout if the real server is dead
proxy_next_upstream error timeout invalid_header http_500 http_502 http_503;
# Advanced Proxy Config
send_timeout 5m;
proxy_read_timeout 360;
proxy_send_timeout 360;
proxy_connect_timeout 360;
# Basic Proxy Config
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Host $http_host;
proxy_set_header X-Forwarded-Uri $request_uri;
proxy_set_header X-Forwarded-Ssl on;
proxy_redirect http:// $scheme://;
proxy_http_version 1.1;
proxy_set_header Connection "";
proxy_cache_bypass $cookie_session;
proxy_no_cache $cookie_session;
proxy_buffers 64 256k;
# If behind reverse proxy, forwards the correct IP
set_real_ip_from 10.0.0.0/8;
set_real_ip_from 172.0.0.0/8;
set_real_ip_from 192.168.0.0/16;
set_real_ip_from fc00::/7;
real_ip_header X-Forwarded-For;
real_ip_recursive on;



 浙公网安备 33010602011771号
浙公网安备 33010602011771号