二进制部署k8s集群v1.23.9版本-14-服务暴露Ingress
14.1、简介NodePort和Ingress
K8S的DNS实现了服务在集群“内”被自动发现,那如何使得服务在k8s集群“外”被使用和访问呢?
-
使用NodePort型的Service,无法使用kube-proxy的ipvs模型;
-
使用Ingress资源,Ingress只能调度并暴露7层应用,特指http和https协议;
-
Ingress是K8S API的标准资源类型之一,也是一种核心资源,它其实是一组基于域名和URL路径,把用户的请求转发至指定Service资源的规则;
-
可以将集群外部的请求流量,转发至集群内部,从而实现“服务暴露”;
-
Ingress控制器是能够为Ingress资源监听某些套接字,然后根据Ingress规则匹配机制路由调度流量的一组组件;
-
说白了,Ingress没啥神秘的,就是nginx+一段go脚本而已;
-
常用的Ingress控制器的实现软件:
Ingress-nginx
HAProxy
Traefik
14.2、安装traefik
- 由于 Traefik 2.X 版本和之前的 1.X 版本不兼容,而且1.X 已经停止更新了。我们这里选择功能更加强大的 2.X 版本来和大家进行演示。
- 这里要注意你的k8s版本,从k8s 1.16开始废弃apiextensions.k8s.io/v1beta1,1.22完全删除。
- 对于k8s 1.16 以上版本,使用apiextensions.k8s.io/v1
192.168.1.200操作
准备traefik镜像
mkdir -p /data/k8s-yaml/traefik
cd /data/k8s-yaml/traefik
docker pull traefik:v2.8.0
docker images|grep traefik
docker tag 23b804da4204 harbor.qgutech.com/public/traefik:v2.8.0
docker push harbor.qgutech.com/public/traefik:v2.8.0
14.3、准备资源配置清单
192.168.1.200操作
cd /data/k8s-yaml/traefik
vim ds.yaml
apiVersion: v1
kind: Service
metadata:
name: traefik
namespace: kube-system
labels:
app: traefik
spec:
ports:
- name: web
port: 80
- name: websecure
port: 443
- name: admin
port: 8080
selector:
app: traefik
---
apiVersion: apps/v1
kind: DaemonSet
metadata:
name: traefik-ingress-controller
namespace: kube-system
labels:
app: traefik
spec:
selector:
matchLabels:
app: traefik
template:
metadata:
name: traefik
labels:
app: traefik
spec:
serviceAccountName: traefik-ingress-controller
terminationGracePeriodSeconds: 1
containers:
- image: harbor.qgutech.com/public/traefik:v2.8.0
name: traefik-ingress-lb
ports:
- name: web
containerPort: 80
hostPort: 81 ## 将容器端口绑定所在服务器的 80 端口
- name: websecure
containerPort: 443
hostPort: 443 ## 将容器端口绑定所在服务器的 443 端口
- name: admin
containerPort: 8080 ## Traefik Dashboard 端口
resources:
limits:
cpu: 2000m
memory: 1024Mi
requests:
cpu: 1000m
memory: 1024Mi
securityContext:
capabilities:
drop:
- ALL
add:
- NET_BIND_SERVICE
args:
- --api
- --kubernetes
- --logLevel=INFO
- --insecureskipverify=true
- --kubernetes.endpoint=https://192.168.1.196:8443
- --accesslog
- --accesslog.filepath=/var/log/traefik_access.log
- --traefiklog
- --traefiklog.filepath=/var/log/traefik.log
- --metrics.prometheus
- --configfile=/config/traefik.yaml
volumeMounts:
- mountPath: "/config"
name: "config"
readinessProbe:
httpGet:
path: /ping
port: 8080
failureThreshold: 3
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 5
livenessProbe:
httpGet:
path: /ping
port: 8080
failureThreshold: 3
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 5
volumes:
- name: config
configMap:
name: traefik-config
vim ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: traefik-web-ui
namespace: kube-system
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: traefik.qgutech.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: traefik
port:
number: 8080
vim rbac.yaml
## ServiceAccount
apiVersion: v1
kind: ServiceAccount
metadata:
namespace: kube-system
name: traefik-ingress-controller
---
## ClusterRole
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: traefik-ingress-controller
rules:
- apiGroups:
- ""
resources:
- services
- endpoints
- secrets
verbs:
- get
- list
- watch
- apiGroups:
- extensions
- networking.k8s.io
resources:
- ingresses
- ingressclasses
verbs:
- get
- list
- watch
- apiGroups:
- extensions
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- traefik.containo.us
resources:
- ingressroutes
- ingressroutetcps
- ingressrouteudps
- middlewares
- tlsoptions
- tlsstores
- traefikservices
- serverstransports
verbs:
- get
- list
- watch
- apiGroups:
- networking.x-k8s.io
resources:
- gatewayclasses
- gatewayclasses/status
- gateways
verbs:
- get
- list
- watch
- apiGroups:
- networking.x-k8s.io
resources:
- gatewayclasses/status
verbs:
- get
- patch
- update
- apiGroups:
- networking.x-k8s.io
resources:
- gateways/status
verbs:
- get
- patch
- update
- apiGroups:
- networking.x-k8s.io
resources:
- httproutes
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- networking.x-k8s.io
resources:
- httproutes/status
verbs:
- get
- patch
- update
---
## ClusterRoleBinding
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: traefik-ingress-controller
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: traefik-ingress-controller
subjects:
- kind: ServiceAccount
name: traefik-ingress-controller
namespace: kube-system
vim cm.yaml
kind: ConfigMap
apiVersion: v1
metadata:
name: traefik-config
namespace: kube-system
data:
traefik.yaml: |-
ping: "" ## 启用 Ping
serversTransport:
insecureSkipVerify: true ## Traefik 忽略验证代理服务的 TLS 证书
api:
insecure: true ## 允许 HTTP 方式访问 API
dashboard: true ## 启用 Dashboard
debug: false ## 启用 Debug 调试模式
metrics:
prometheus: "" ## 配置 Prometheus 监控指标数据,并使用默认配置
entryPoints:
web:
address: ":80" ## 配置 80 端口,并设置入口名称为 web
forwardedHeaders:
insecure: true
websecure:
address: ":443" ## 配置 443 端口,并设置入口名称为 websecure
forwardedHeaders:
insecure: true
traefik:
address: ":8080" ## 配置 8080 端口,并设置入口名称为 dashboard
metrics:
address: ":8082" ## 配置 8082 端口,作为metrics收集入口
tcp:
address: ":8079" ## 配置 8079 端口,作为tcp访问入口
providers:
kubernetesCRD: "" ## 启用 Kubernetes CRD 方式来配置路由规则
kubernetesIngress: "" ## 启用 Kubernetes Ingress 方式来配置路由规则
kubernetesGateway: "" ## 启用 Kubernetes Gateway API
experimental:
kubernetesGateway: true ## 允许使用 Kubernetes Gateway API
log:
filePath: "" ## 设置调试日志文件存储路径,如果为空则输出到控制台
level: error ## 设置调试日志级别
format: json ## 设置调试日志格式
accessLog:
filePath: "" ## 设置访问日志文件存储路径,如果为空则输出到控制台
format: json ## 设置访问调试日志格式
bufferingSize: 0 ## 设置访问日志缓存行数
filters:
retryAttempts: true ## 设置代理访问重试失败时,保留访问日志
minDuration: 20 ## 设置保留请求时间超过指定持续时间的访问日志
fields: ## 设置访问日志中的字段是否保留(keep 保留、drop 不保留)
defaultMode: keep ## 设置默认保留访问日志字段
names: ## 针对访问日志特别字段特别配置保留模式
ClientUsername: drop
headers: ## 设置 Header 中字段是否保留
defaultMode: keep ## 设置默认保留 Header 中字段
names: ## 针对 Header 中特别字段特别配置保留模式
User-Agent: redact
Authorization: drop
Content-Type: keep
vim crd.yaml
地址如下:
https://github.com/traefik/traefik/blob/v2.8/docs/content/reference/dynamic-configuration/kubernetes-crd-definition-v1.yml
14.4、应用资源配置清单
192.168.1.201操作
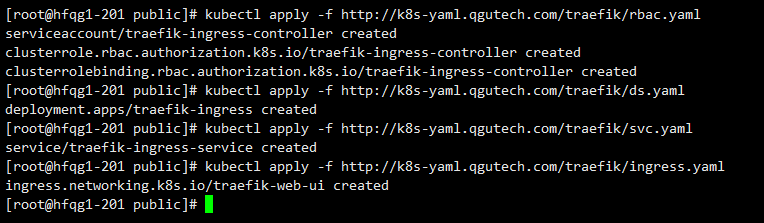
kubectl apply -f http://k8s-yaml.qgutech.com/traefik/crd.yaml
kubectl apply -f http://k8s-yaml.qgutech.com/traefik/rbac.yaml
kubectl apply -f http://k8s-yaml.qgutech.com/traefik/cm.yaml
kubectl apply -f http://k8s-yaml.qgutech.com/traefik/ds.yaml
kubectl apply -f http://k8s-yaml.qgutech.com/traefik/ingress.yaml
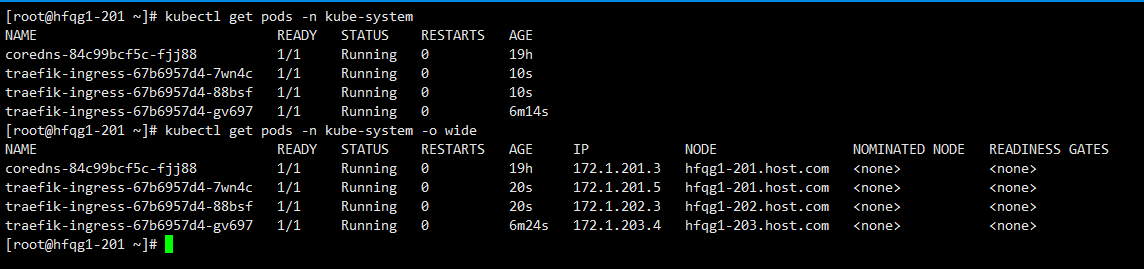
kubectl get pods -n kube-system
kubectl get pods -n kube-system -o wide
netstat -lntup|grep 81
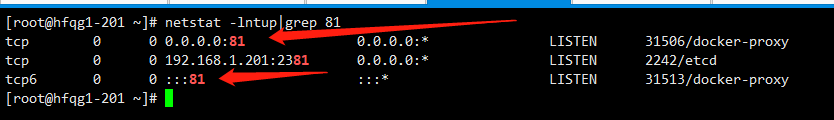
每个宿主机都监听了81端口。所有7层的流量都会从81进,然后通过ingress规则去分配流量,即特定的service。
14.5、配置反向代理
192.168.1.198和192.168.1.199服务器操作
vim /etc/nginx/conf.d/qgutech.com.conf
upstream default_backend_traefik {
server 192.168.1.201:81 max_fails=3 fail_timeout=10s;
server 192.168.1.202:81 max_fails=3 fail_timeout=10s;
server 192.168.1.203:81 max_fails=3 fail_timeout=10s;
}
server {
server_name *.qgutech.com;
location / {
proxy_pass http://default_backend_traefik;
proxy_set_header Host $http_host;
proxy_set_header x-forwarded-for $proxy_add_x_forwarded_for;
}
}
检测语法并重新加载nginx
nginx -t
nginx -s reload
14.6、配置内网域名解析
192.168.1.197服务器操作
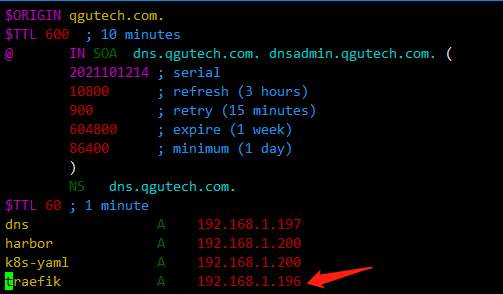
vim /var/named/qgutech.com.zone
traefik A 192.168.1.196
注意要前滚一个序列号
systemctl restart named
页面访问
http://traefik.qgutech.com
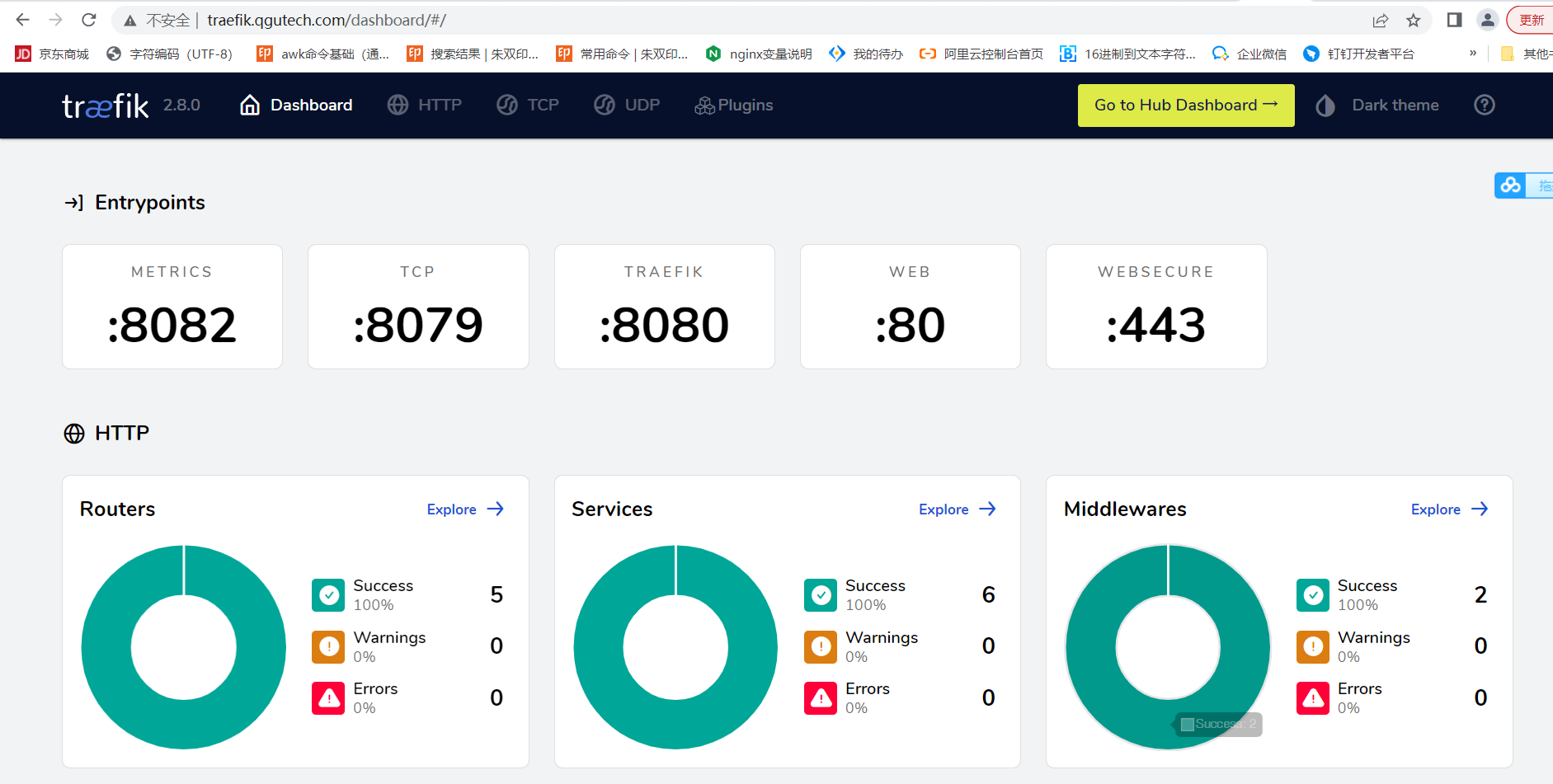
至此,traefik安装完成,感谢观看!
本文来自博客园,作者:霸都运维,转载请注明原文链接:https://www.cnblogs.com/wangjie20200529/p/16615119.html


 浙公网安备 33010602011771号
浙公网安备 33010602011771号