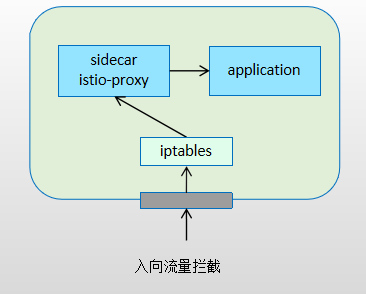
Istio 流量拦截
Sidecar代理方式简介
- Kubernetes平台上,Envoy Sidecar容器与application容器于同一个Pod中共存,它们共享NETWORK、UTS和IPC等名称空间,因此也共用同一个网络协议栈;
- Envoy Sidecar基于init容器(需要使用NET_ADMIN和NET_RAW Capability于Pod启动时设置iptables规则以实现流量拦截
-
入站流量由iptables拦截后转发给Envoy
-
Envoy根据配置完成入站流量代理
-
后端应用程序生成的出站流量依然由iptables拦截并转发给Envoy
-
Envoy根据配置完成出站流量代理
-
- Envoy Sidecar基于init容器(需要使用NET_ADMIN和NET_RAW Capability于Pod启动时设置iptables规则以实现流量拦截
-
流量拦截模式
-
REDIRECT:重定向模式
-
TPROXY:透明代理模式
-
具体操作细节请参考:https://github.com/istio/istio/blob/master/tools/packaging/common/istio-start.sh
-
-
Sidecar Envoy 流量劫持
-
流量的透明劫持
-
流量的透明劫持,用于确保让应用无需事先改造即可获得服务治理和观测能力
-
开启透明劫持功能后,出入应用的业务流量将会被Sidecar Envoy自动拦截
-
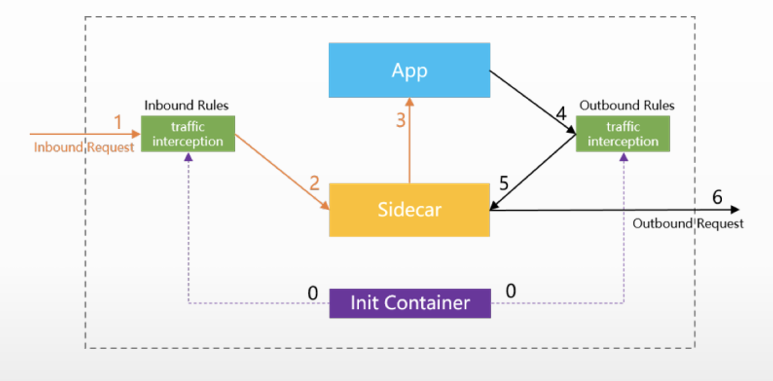
流量劫持过程
- Init流程(0):图中紫色虚线表示Init流程
- Pod启动时,会借助Init Container特权容器开启流量劫持,并设置流量劫持规则
-
劫持规则分为Inbound规则和Outbound规则
- Inbound流程(1、2、3):图中橙色实线代表着Inbound流程
-
请求发给APP前被traffic intercetion劫持
- traffic intercetion根据Inbound规则,将请求转发到Sidecar
-
Sidecar将请求转发给APP
-
- Outbound流程(4、5、6):黑色实线表示Outbound请求
- App发出的Outbound请求被traffic interception劫持
- traffic interception根据Outbound规则将请求转发给Sidecar
-
Sidecar处理之后将请求回复给请求者
Istio注入的Envoy Sidecar
- Istio基于Kubernetes Admission Controller Webhook完成sidecar自动注入,它会为每个微服务分别添加两个相关的容器
- istio-init:隶属于Init Containers,即初始化容器,负责在微服务相关的Pod中生成iptables规则以进行流量拦截并向Envoy Proxy进行转发;运行完成后退出;
-
istio-proxy:隶属于Contianers,即Pod中的正常容器,程序为Envoy Proxy;
istio-init初始化容器
-
istio-init初始化容器基于istio/proxyv2镜像启动,它运行istio-iptables程序以生成流量拦截规则
-
拦截的流量将转发至两个相关的端口
- 15006:由-z选项定义,指定用于接收拦截所有发往当前Pod/VM的入站流量的目标端口,该配置仅用于REDIRECT转发模式;
-
15001:由-p选项定义,指定用于接收拦截的所有TCP流量的目标端口;
-
流量拦截模式由-m选项指定,目前支持REDIRECT和TPROXY两种模式
-
流量拦截时要包含的目标端口列表使用-b选项指定,而要排除的目标端口列表则使用-d选项指定;
- 流量拦截时要包含的目标CIDR地址列表可使用-i选项指定,而要排除的目标CIDR格式的地址列表则使用-x选项指定;
-
- 此前版本中,该初始化容器会运行一个用于生成iptables规则的相关的脚本来生成iptables规则,脚本地址为:https://github.com/istio/cni/blob/master/tools/packaging/common/istio-iptables.sh
~# kubectl get pod
NAME READY STATUS RESTARTS AGE
demoappv10-78b6586d58-gstt2 2/2 Running 2 (7h29m ago) 22h
demoappv10-78b6586d58-qc2wg 2/2 Running 2 (7h29m ago) 22h
demoappv11-78bf898c74-ggfgd 2/2 Running 2 (7h29m ago) 22h
demoappv11-78bf898c74-qscbn 2/2 Running 2 (7h29m ago) 22h~# kubectl describe pod demoappv10-78b6586d58-gstt2
...
Init Containers:
istio-init:
Container ID: containerd://630aa2dc07c6950d1b8a4a0076d15970ac28867a3af3c4b7912c210b84f2e151
Image: docker.io/istio/proxyv2:1.15.2
Image ID: docker.io/istio/proxyv2@sha256:74a901daca055491e62f167bfbbe24a0880005cd67ae849ed6c09a3a3ec9feb7
Port: <none>
Host Port: <none>
Args:
istio-iptables
-p
15001
-z
15006
-u
1337
-m
REDIRECT
-i
*
-x
-b
*
-d
15090,15021,15020
--log_output_level=default:info
State: Terminated
Reason: Completed
Exit Code: 0
Started: Fri, 28 Oct 2022 09:49:03 +0800
Finished: Fri, 28 Oct 2022 09:49:06 +0800
Ready: True
Restart Count: 1
Limits:
cpu: 2
memory: 1Gi
...Istio中用于流量拦截的iptables规则
root@k8s-node-03:~# crictl ps
CONTAINER IMAGE CREATED STATE NAME ATTEMPT POD ID POD
917370a99e332 25585bdfb0f7a 6 hours ago Running istio-proxy 1 24bb9c2fe2b8d demoappv10-78b6586d58-qc2wg
39f34d79de972 25585bdfb0f7a 6 hours ago Running istio-proxy 1 0e43ddf1d02a7 demoappv11-78bf898c74-qscbn
2a8fe8c88c1f0 258641e274412 6 hours ago Running demoapp 1 0e43ddf1d02a7 demoappv11-78bf898c74-qscbn
c11fc4ca9aa00 3342b7518915f 6 hours ago Running demoapp 1 24bb9c2fe2b8d demoappv10-78b6586d58-qc2wg
276fccc66da4e 5f5175f39b19e 6 hours ago Running calico-node 16 f091078ccf398 calico-node-mdxh6
73de2c09b9142 b6f09c63d6ec6 6 hours ago Running grafana 6 47b8f1c025d96 grafana-56bdf8bf85-qbnwl
f6f02fc18cafe 9d3f84f2ca38b 6 hours ago Running jaeger 6 28ca588056de3 jaeger-c4fdf6674-c7tq8
ede6404fcc5d7 245047de26c06 6 hours ago Running discovery 11 ae4d951f3ba26 istiod-5456fd558d-4djxr
e81b8e9108818 5fafbe4dd936b 6 hours ago Running kiali 6 a25db5dc29a0e kiali-5ff49b9f69-q8gqnroot@k8s-node-03:~# crictl inspect -o json 917370a99e332 |grep pid
"pid": 2818,
"pid": 1
"type": "pid"# root@k8s-node-03:~# nsenter -t 2818 -n iptables -t nat -S
root@k8s-node-03:~# nsenter -t 2818 -n iptables-legacy -t nat -S
-P PREROUTING ACCEPT
-P INPUT ACCEPT
-P OUTPUT ACCEPT
-P POSTROUTING ACCEPT
-N ISTIO_INBOUND
-N ISTIO_IN_REDIRECT
-N ISTIO_OUTPUT
-N ISTIO_REDIRECT
-A PREROUTING -p tcp -j ISTIO_INBOUND
-A OUTPUT -p tcp -j ISTIO_OUTPUT
-A ISTIO_INBOUND -p tcp -m tcp --dport 15008 -j RETURN
-A ISTIO_INBOUND -p tcp -m tcp --dport 15090 -j RETURN
-A ISTIO_INBOUND -p tcp -m tcp --dport 15021 -j RETURN
-A ISTIO_INBOUND -p tcp -m tcp --dport 15020 -j RETURN
-A ISTIO_INBOUND -p tcp -j ISTIO_IN_REDIRECT
-A ISTIO_IN_REDIRECT -p tcp -j REDIRECT --to-ports 15006
-A ISTIO_OUTPUT -s 127.0.0.6/32 -o lo -j RETURN
-A ISTIO_OUTPUT ! -d 127.0.0.1/32 -o lo -m owner --uid-owner 1337 -j ISTIO_IN_REDIRECT
-A ISTIO_OUTPUT -o lo -m owner ! --uid-owner 1337 -j RETURN
-A ISTIO_OUTPUT -m owner --uid-owner 1337 -j RETURN
-A ISTIO_OUTPUT ! -d 127.0.0.1/32 -o lo -m owner --gid-owner 1337 -j ISTIO_IN_REDIRECT
-A ISTIO_OUTPUT -o lo -m owner ! --gid-owner 1337 -j RETURN
-A ISTIO_OUTPUT -m owner --gid-owner 1337 -j RETURN
-A ISTIO_OUTPUT -d 127.0.0.1/32 -j RETURN
-A ISTIO_OUTPUT -j ISTIO_REDIRECT
-A ISTIO_REDIRECT -p tcp -j REDIRECT --to-ports 15001Istio流量拦截的处理机制
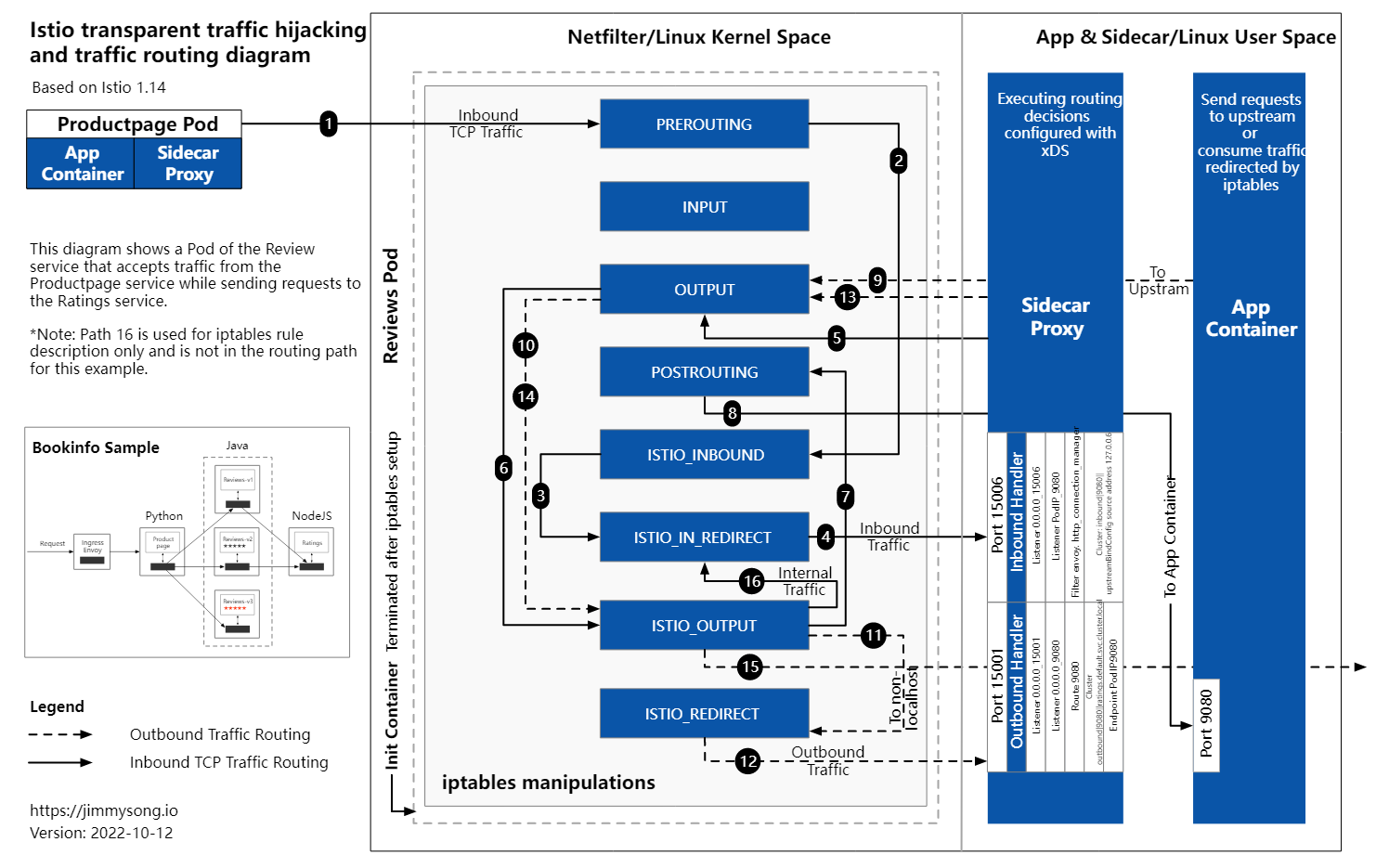
入向流量拦截:PREROUTING -> ISTIO_INBOUND
- RETURN
- 目标端口为TCP协议的15020、15021、15008、15090时将报文返回至上级的PREROUTING链,即不予拦截;
- ISTIO_IN_REDIRECT:其它目标端口的请求报文则由该自定链中的规则(-A ISTIO_IN_REDIRECT -p tcp -j REDIRECT --to-ports 15006)将请求重定向至15006端口;
-
15006端口是为Envoy的VirtualInboundListener绑定的端口,于是请求则转交由Envoy处理;
- Envoy根据报文目标地址匹配入向(Inbound)方向的Listener,若存在,则根据该Listener的配置决定如何将请求转发至Envoy后端的应用程序;
-
出向流量拦截:OUTPUT -> ISTIO_OUTPUT
-
RETURN
-
从lo接口流出,且源地址为127.0.0.6/32的出向流量
- UID Owner为1337的出向流量
-
GID Owner为1337的出向流量
-
从lo接口流出, 且UID Owner非为1337的出向流量
-
从lo接口流出,且GID Owner非为1337的出向流量
-
目标地址是127.0.0.1/32的出向流量
-
- ISTIO_IN_REDIRECT:Sidecar Envoy同其反向代理的本地后端应用程序间的通信
-
从lo接口流出,目标地址非为127.0.0.1/32,且UID Owner为1337的出向流量
-
从lo接口流出,目标地址非为127.0.0.1/32,且GID Owner为1337的出向流量
-
- ISTIO_REDIRECT:其它报文则由该自定义链中的规则(-A ISTIO_REDIRECT -p tcp -j REDIRECT --to-ports 15001)重定向至15001端口;
- Envoy根据报文目标地址匹配出向(Outbound)方向的Listener,若存在,则根据该Listener的配置决定如何将报文向外转发;
istio-proxy容器
istio-proxy 进程
-
istio-proxy即所谓的sidecar容器,它运行两个进程
-
pilot-agent
-
基于k8s api server为envoy初始化出可用的boostrap配置文件并启动envoy;
-
监控并管理envoy的运行状态,包括envoy出错时重启envoy,以及envoy配置变更后将其重载等;
-
-
envoy
- envoy由pilot-agent进程基于生成bootstrap配置进行启动,而后根据配置中指定的pilot地址,通过xDS API获取动态配置信息;
-
Sidecar形式的Envoy通过流量拦截机制为应用程序实现入站和出站代理功能;
-
~# kubectl get pod
NAME READY STATUS RESTARTS AGE
demoappv10-78b6586d58-gstt2 2/2 Running 2 (6h3m ago) 21h
demoappv10-78b6586d58-qc2wg 2/2 Running 2 (6h3m ago) 21h
demoappv11-78bf898c74-ggfgd 2/2 Running 2 (6h3m ago) 21h
demoappv11-78bf898c74-qscbn 2/2 Running 2 (6h3m ago) 21h
proxy-649b4d887d-kxmvs 2/2 Running 0 55m~# kubectl exec -it demoappv10-78b6586d58-gstt2 -c istio-proxy -- ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
istio-p+ 1 0.0 1.2 753480 48468 ? Ssl 01:49 0:11 /usr/local/bin/pilot-agent proxy sidecar --domain default.svc.cluster.local --proxyLogLevel=warning --proxyComponentLogLevel=misc:error --log_output_level=default:info --concurrency 2
istio-p+ 17 0.2 1.3 179412 55488 ? Sl 01:49 0:56 /usr/local/bin/envoy -c etc/istio/proxy/envoy-rev.json --drain-time-s 45 --drain-strategy immediate --parent-shutdown-time-s 60 --local-address-ip-version v4 --file-flush-interval-msec 1000 --disable-hot-restart --log-format %Y-%m-%dT%T.%fZ.%l.envoy %n.%v -l warning --component-log-le
istio-p+ 31 0.0 0.0 7060 1560 pts/0 Rs+ 07:52 0:00 ps auxpilot-agent使用帮助
~# kubectl exec -it demoappv10-78b6586d58-gstt2 -c istio-proxy -- pilot-agent --help
Istio Pilot agent runs in the sidecar or gateway container and bootstraps Envoy.
Usage:
pilot-agent [command]
Available Commands:
completion Generate the autocompletion script for the specified shell
help Help about any command
istio-clean-iptables Clean up iptables rules for Istio Sidecar
istio-iptables Set up iptables rules for Istio Sidecar
proxy XDS proxy agent
request Makes an HTTP request to the Envoy admin API
version Prints out build version information
wait Waits until the Envoy proxy is ready
Flags:
-h, --help help for pilot-agent
--log_as_json Whether to format output as JSON or in plain console-friendly format
--log_caller string Comma-separated list of scopes for which to include caller information, scopes can be any of [ads, all, authn, authorization, ca, cache, citadelclient, controllers, default, delta, dns, gcecred, googleca, googlecas, grpcgen, healthcheck, iptables, klog, mockcred, model, proxyconfig, sds, security, serviceentry, spiffe, stsclient, stsserver, telemetry, token, trustBundle, validation, wasm, wle, xdsproxy]
--log_output_level string Comma-separated minimum per-scope logging level of messages to output, in the form of <scope>:<level>,<scope>:<level>,... where scope can be one of [ads, all, authn, authorization, ca, cache, citadelclient, controllers, default, delta, dns, gcecred, googleca, googlecas, grpcgen, healthcheck, iptables, klog, mockcred, model, proxyconfig, sds, security, serviceentry, spiffe, stsclient, stsserver, telemetry, token, trustBundle, validation, wasm, wle, xdsproxy] and level can be one of [debug, info, warn, error, fatal, none] (default "default:info")
--log_rotate string The path for the optional rotating log file
--log_rotate_max_age int The maximum age in days of a log file beyond which the file is rotated (0 indicates no limit) (default 30)
--log_rotate_max_backups int The maximum number of log file backups to keep before older files are deleted (0 indicates no limit) (default 1000)
--log_rotate_max_size int The maximum size in megabytes of a log file beyond which the file is rotated (default 104857600)
--log_stacktrace_level string Comma-separated minimum per-scope logging level at which stack traces are captured, in the form of <scope>:<level>,<scope:level>,... where scope can be one of [ads, all, authn, authorization, ca, cache, citadelclient, controllers, default, delta, dns, gcecred, googleca, googlecas, grpcgen, healthcheck, iptables, klog, mockcred, model, proxyconfig, sds, security, serviceentry, spiffe, stsclient, stsserver, telemetry, token, trustBundle, validation, wasm, wle, xdsproxy] and level can be one of [debug, info, warn, error, fatal, none] (default "default:none")
--log_target stringArray The set of paths where to output the log. This can be any path as well as the special values stdout and stderr (default [stdout])
--vklog Level number for the log level verbosity. Like -v flag. ex: --vklog=9
Use "pilot-agent [command] --help" for more information about a command.istio-proxy容器Listener
- Envoy的bootstrap配置文件由pilot-agent负责生成,而生效的大多配置则定义成了dynamic resources,并通过xDS静态集群指向的Pilot获取;
-
而这些配置则来自于VirtualService、DestinationRule、Gateway和ServiceEntry资源对象等提供的配置;
-
- 由Pilot基于Kubernetes发现的网格内的各Service均会被自动转换为下发给各Sidecar实例的Listener、Route、Cluster和Endpoint的相关配置
- 为了能够让Sidecar Envoy代理网格内进出各Service的流量,所以需要进行流量劫持,而后由Envoy根据请求特征,将流量派发至合适的Listener,进而完成后续的流量路由、负载均衡等
~# kubectl exec -it demoappv10-78b6586d58-gstt2 -c istio-proxy -- pilot-agent request GET /listeners
d61bf198-79db-47dc-a11f-4c0227603d0e::0.0.0.0:15090
bad902ee-6657-4325-81b8-21b8897cefc8::0.0.0.0:15021
10.100.0.2_53::10.100.0.2:53
10.100.121.95_443::10.100.121.95:443
10.100.145.112_31400::10.100.145.112:31400
10.100.0.1_443::10.100.0.1:443
10.100.149.76_15012::10.100.149.76:15012
10.100.145.112_443::10.100.145.112:443
10.100.149.76_443::10.100.149.76:443
10.100.145.112_15443::10.100.145.112:15443
0.0.0.0_15014::0.0.0.0:15014
0.0.0.0_20001::0.0.0.0:20001
0.0.0.0_16685::0.0.0.0:16685
10.100.126.122_14250::10.100.126.122:14250
10.100.162.68_3000::10.100.162.68:3000
10.100.0.2_9153::10.100.0.2:9153
0.0.0.0_15010::0.0.0.0:15010
10.100.145.112_15021::10.100.145.112:15021
0.0.0.0_8080::0.0.0.0:8080
10.100.107.86_443::10.100.107.86:443
0.0.0.0_80::0.0.0.0:80
0.0.0.0_9090::0.0.0.0:9090
10.100.128.238_8000::10.100.128.238:8000
10.100.126.122_14268::10.100.126.122:14268
0.0.0.0_9411::0.0.0.0:9411
virtualOutbound::0.0.0.0:15001
virtualInbound::0.0.0.0:15006istio-proxy Listener
- Envoy Listener支持绑定于IP Socket或Unix Domain Socket之上,也可以不予绑定,而是接收由其它的Listener转发来的数据
- VirtualOutboundListener通过一个端口接收所有的出向流量,而后再按照请求的端口分别转发给相应的Listener进行处理;
-
VirtualInboundListener的功能相似,但它主要用于处理入向流量;
-
VirtualOutbound Listener
- iptables将其所在的Pod中的外发流量拦截后转发至监听于15001的Listener,而该Listener通过在配置中将use_origin_dest参数设置为true,从而实现将接收到的请求转交给同请求原目标地址关联的Listener之上;
- 若不存在可接收转发报文的Listener,则Envoy将根据Istio的全局配置选项outboundTrafficPolicy参数的值决定如何进行处理
- ALLOW_ANY:允许外发至任何服务的请求,无论目标服务是否存在于Pilot的注册表中;此时,没有匹配的目标Listener的流量将由该侦听器上tcp_proxy过滤器指向的Passthrough Cluster进行透传;
- REGISTRY_ONLY:仅允许外发请求至注册于Polit中的服务;此时,没有匹配的目标Listener的流量将由该侦听器上tcp_proxy过滤器指向的BlackHoleCluster将流量直接丢弃;
istio-proxy Outbound Listener
-
Envoy将按需为其所处网格中的各外部服务按端口创建多个Listener以处理出站流量,
-
0.0.0.0_9080 :处理发往details、reviews和rating等服务的流量
-
0.0.0.0_9411:处理发往zipkin的流量
-
0.0.0.0_3000:处理发往grafana的流量
-
0.0.0.0_9090:处理发往prometheus的流量;
-
VirtualInbound Listener
入向流量劫持
- 较早版本的Istio基于同一个VirtualListener在15001端口上同时处理入站和出站流量
- 自1.4版本起,Istio引入了REDIRECT代理模式,它通过监听于15006端口的专用VirtualInboundListener处理入向流量代理以规避潜在的死循环问题;
入向流量处理
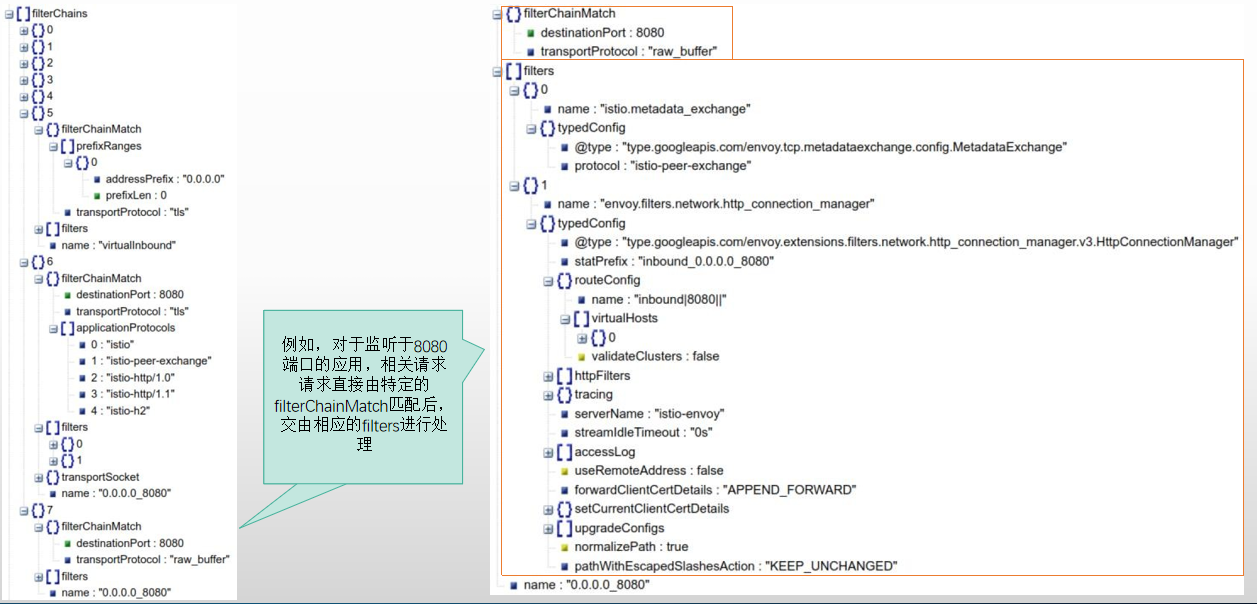
- 对于进入到侦听器“0.0.0.0:15006”的流量,VirtualInboundListener会在filterChains中,通过一系列的filter_chain_match对流量进行匹配检测,以确定应该由哪个或哪些过滤器进行流量处理
~# kubectl exec -it demoappv10-78b6586d58-gstt2 -c istio-proxy -- pilot-agent request GET /config_dump- 事实上,入向流量的相关过滤器匹配条件及流量处理机制,也可以简单地通过istioctl proxy-config命令来获取
-
仍然以监听于8080/tcp端口提供服务的demoapp应用的某实例为例
-
命令:istioctl proxy-config listeners $DEMOAPP_POD --port 15006
-
-
它的15006侦听器上相关配置如下
-
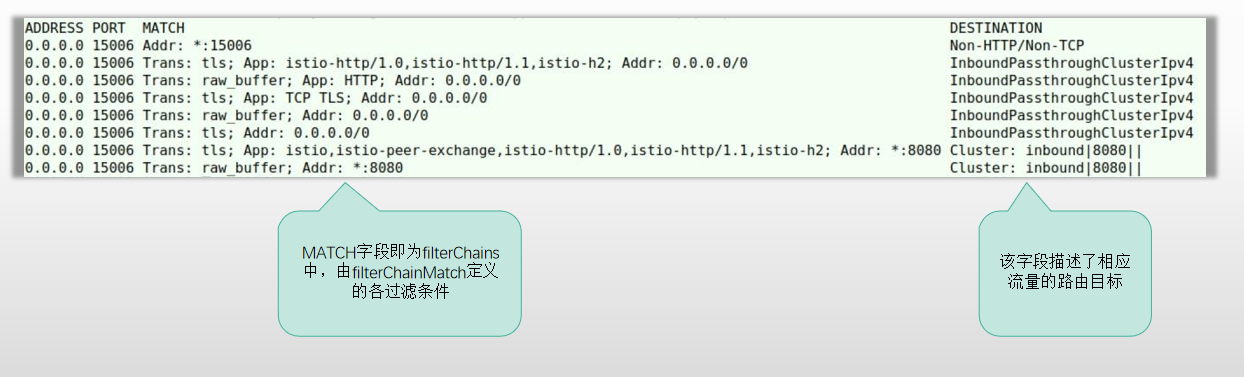
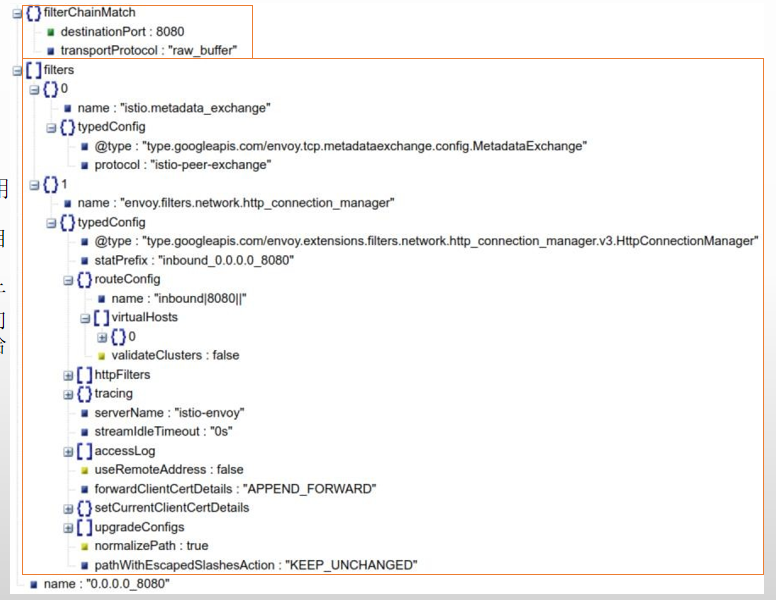
入向流量处理机制
- VirtualInboundListener会将接收到请求将直接采用一系列filter_chain_match对入站流量进行匹配检测,匹配到的流量,将由相应的filters进行处理
- 例如,对于监听于8080端口的应用,相关请求请求直接由特定的filter_chain_match匹配后,交由相应的filters进行处理,
- 这有别于VirtualOutboundListener对入向流量的处理方式,并非将流量分发给独立的Egress Listener进行处理;
istio-proxy Clusters
- Istio网格中的Cluster分别由static_resources提供的静态配置集群以及dynamic_resources提供的动态配置集群组成;
- 静态集群由envoy-rev0.json的初始化配置中的prometheus_stats、xDS server和zipkin server等组成;
- 动态集群则是由通过xDS API从Pilot获取的配置信息生成;
- 对于网格内的一个特定Pod来说,其集群可主要分为两类
- inbound:该Pod内的Sidecar Envoy直接代理的服务
-
outbound:网格内的所有服务
~# kubectl exec demoappv10-78b6586d58-gstt2 -c istio-proxy -- curl -s 127.0.0.1:15000/clusters | grep -o "^[^:]\+" | sort -u
BlackHoleCluster
InboundPassthroughClusterIpv4
PassthroughCluster
agent
inbound|8080||
outbound|14250||jaeger-collector.istio-system.svc.cluster.local
outbound|14268||jaeger-collector.istio-system.svc.cluster.local
outbound|15010||istiod.istio-system.svc.cluster.local
outbound|15012||istiod.istio-system.svc.cluster.local
outbound|15014||istiod.istio-system.svc.cluster.local
outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
outbound|16685||tracing.istio-system.svc.cluster.local
outbound|20001||kiali.istio-system.svc.cluster.local
outbound|3000||grafana.istio-system.svc.cluster.local
outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
outbound|443||istio-egressgateway.istio-system.svc.cluster.local
outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
outbound|443||istiod.istio-system.svc.cluster.local
outbound|443||kubernetes-dashboard.kubernetes-dashboard.svc.cluster.local
outbound|443||kubernetes.default.svc.cluster.local
outbound|53||kube-dns.kube-system.svc.cluster.local
outbound|8000||dashboard-metrics-scraper.kubernetes-dashboard.svc.cluster.local
outbound|8080||demoappv10.default.svc.cluster.local
outbound|8080||demoappv11.default.svc.cluster.local
outbound|80||istio-egressgateway.istio-system.svc.cluster.local
outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
outbound|80||proxy.default.svc.cluster.local
outbound|80||tracing.istio-system.svc.cluster.local
outbound|9090||kiali.istio-system.svc.cluster.local
outbound|9090||prometheus.istio-system.svc.cluster.local
outbound|9153||kube-dns.kube-system.svc.cluster.local
outbound|9411||jaeger-collector.istio-system.svc.cluster.local
outbound|9411||zipkin.istio-system.svc.cluster.local
prometheus_stats
sds-grpc
xds-grpc
zipkinistio-proxy上的动态集群
动态集群类型
-
Inbound Cluster:Sidecar Envoy直接代理的应用,同一Pod中,由Sidecar Envoy反向代理的应用容器;
- Outbound Cluster:网格中的所有服务,包括当前Sidecar Envoy直接代理的服务,该类Cluster占了Envoy可用集群中的绝大多数;
- PassthroughCluster和InboundPassthroughClusterIpv4:发往此类集群的请求报文会被直接透传至其请求中的原始目标地址,Envoy不会进行重新路由;
- BlackHoleCluster:Envoy的一个特殊集群,它没有任何可用的endpoint,接收到的请求会被直接丢弃;未能正确匹配到目标服务的请求通常会被发往此Cluster;
参考文档
https://istio.io/latest/zh/blog/2019/data-plane-setup/#traffic-flow-from-application-container-to-sidecar-proxy
pilot-agent::https://istio.io/latest/zh/docs/reference/commands/pilot-agent/
eBPF代替iptables实现: https://istio.io/latest/blog/2022/merbridge/



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
· 【自荐】一款简洁、开源的在线白板工具 Drawnix