Istio部署Addons
部署Addons
查看内置addons
# ls -l samples/addons/
total 288
-rw-r--r-- 1 root root 5194 Oct 8 02:48 README.md
drwxr-xr-x 2 root root 4096 Oct 8 02:48 extras
-rw-r--r-- 1 root root 246979 Oct 8 02:48 grafana.yaml
-rw-r--r-- 1 root root 2533 Oct 8 02:48 jaeger.yaml
-rw-r--r-- 1 root root 11727 Oct 8 02:48 kiali.yaml
-rw-r--r-- 1 root root 14509 Oct 8 02:48 prometheus.yaml部署addons
# kubectl apply -f samples/addons/
serviceaccount/grafana created
configmap/grafana created
service/grafana created
deployment.apps/grafana created
configmap/istio-grafana-dashboards created
configmap/istio-services-grafana-dashboards created
deployment.apps/jaeger created
service/tracing created
service/zipkin created
service/jaeger-collector created
serviceaccount/kiali created
configmap/kiali created
clusterrole.rbac.authorization.k8s.io/kiali-viewer created
clusterrole.rbac.authorization.k8s.io/kiali created
clusterrolebinding.rbac.authorization.k8s.io/kiali created
role.rbac.authorization.k8s.io/kiali-controlplane created
rolebinding.rbac.authorization.k8s.io/kiali-controlplane created
service/kiali created
deployment.apps/kiali created
serviceaccount/prometheus created
configmap/prometheus created
clusterrole.rbac.authorization.k8s.io/prometheus created
clusterrolebinding.rbac.authorization.k8s.io/prometheus created
service/prometheus created
deployment.apps/prometheus created验证部署结果
# kubectl get pods -n istio-system
NAME READY STATUS RESTARTS AGE
grafana-56bdf8bf85-g2vgz 1/1 Running 0 118s
istio-egressgateway-fffc799cf-vt4b7 1/1 Running 0 66m
istio-ingressgateway-7d68764b55-n2wk8 1/1 Running 0 66m
istiod-5456fd558d-7l7xd 1/1 Running 0 67m
jaeger-c4fdf6674-tc9mn 1/1 Running 0 118s
kiali-5ff49b9f69-qlb2s 1/1 Running 0 117s
prometheus-85949fddb-4p4nr 2/2 Running 0 117s# kubectl get svc -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
grafana ClusterIP 10.100.157.116 <none> 3000/TCP 24s
istio-egressgateway ClusterIP 10.100.86.184 <none> 80/TCP,443/TCP 25h
istio-ingressgateway LoadBalancer 10.100.63.147 <pending> 15021:43732/TCP,80:55697/TCP,443:59179/TCP,31400:43335/TCP,15443:33703/TCP 25h
istiod ClusterIP 10.100.50.155 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 25h
jaeger-collector ClusterIP 10.100.28.65 <none> 14268/TCP,14250/TCP,9411/TCP 24s
kiali ClusterIP 10.100.210.78 <none> 20001/TCP,9090/TCP 24s
prometheus ClusterIP 10.100.71.239 <none> 9090/TCP 23s
tracing ClusterIP 10.100.204.40 <none> 80/TCP,16685/TCP 24s
zipkin ClusterIP 10.100.243.124 <none> 9411/TCP 24s通过Ingress-Gateway暴露kiali
若需要在集群外部访问Kiali,可通过为其定义相应的Gateway、VirtualService和DestinationRule资源完成。
查看Ingress-Gateway label
# kubectl get pods -n istio-system --show-labels
NAME READY STATUS RESTARTS AGE LABELS
grafana-56bdf8bf85-nbqbz 1/1 Running 0 53m app.kubernetes.io/instance=grafana,app.kubernetes.io/name=grafana,app=grafana,pod-template-hash=56bdf8bf85,sidecar.istio.io/inject=false
istio-egressgateway-fffc799cf-vt4b7 1/1 Running 1 (4h38m ago) 26h app=istio-egressgateway,chart=gateways,heritage=Tiller,install.operator.istio.io/owning-resource=unknown,istio.io/rev=default,istio=egressgateway,operator.istio.io/component=EgressGateways,pod-template-hash=fffc799cf,release=istio,service.istio.io/canonical-name=istio-egressgateway,service.istio.io/canonical-revision=latest,sidecar.istio.io/inject=false
istio-ingressgateway-7d68764b55-n2wk8 1/1 Running 1 (4h38m ago) 26h app=istio-ingressgateway,chart=gateways,heritage=Tiller,install.operator.istio.io/owning-resource=unknown,istio.io/rev=default,istio=ingressgateway,operator.istio.io/component=IngressGateways,pod-template-hash=7d68764b55,release=istio,service.istio.io/canonical-name=istio-ingressgateway,service.istio.io/canonical-revision=latest,sidecar.istio.io/inject=false
istiod-5456fd558d-7l7xd 1/1 Running 1 (4h38m ago) 26h app=istiod,install.operator.istio.io/owning-resource=unknown,istio.io/rev=default,istio=pilot,operator.istio.io/component=Pilot,pod-template-hash=5456fd558d,sidecar.istio.io/inject=false
jaeger-c4fdf6674-x68jz 1/1 Running 0 53m app=jaeger,pod-template-hash=c4fdf6674
kiali-5ff49b9f69-5vj5g 1/1 Running 0 53m app.kubernetes.io/instance=kiali,app.kubernetes.io/managed-by=Helm,app.kubernetes.io/name=kiali,app.kubernetes.io/part-of=kiali,app.kubernetes.io/version=v1.55.1,app=kiali,helm.sh/chart=kiali-server-1.55.1,pod-template-hash=5ff49b9f69,sidecar.istio.io/inject=false,version=v1.55.1
prometheus-85949fddb-vhrff 2/2 Running 0 53m app=prometheus,chart=prometheus-15.9.0,component=server,heritage=Helm,pod-template-hash=85949fddb,release=prometheus,sidecar.istio.io/inject=false获取Ingress-Gateway pod name
# kubectl get pods -l app=istio-ingressgateway -n istio-system -o jsonpath={.items[0].metadata.name}
istio-ingressgateway-7d68764b55-n2wk8
# InGW_POD=$(kubectl get pods -l app=istio-ingressgateway -n istio-system -o jsonpath={.items[0].metadata.name})查看Istio api group
# kubectl api-resources |grep istio
wasmplugins extensions.istio.io/v1alpha1 true WasmPlugin
istiooperators iop,io install.istio.io/v1alpha1 true IstioOperator
destinationrules dr networking.istio.io/v1beta1 true DestinationRule
envoyfilters networking.istio.io/v1alpha3 true EnvoyFilter
gateways gw networking.istio.io/v1beta1 true Gateway
proxyconfigs networking.istio.io/v1beta1 true ProxyConfig
serviceentries se networking.istio.io/v1beta1 true ServiceEntry
sidecars networking.istio.io/v1beta1 true Sidecar
virtualservices vs networking.istio.io/v1beta1 true VirtualService
workloadentries we networking.istio.io/v1beta1 true WorkloadEntry
workloadgroups wg networking.istio.io/v1beta1 true WorkloadGroup
authorizationpolicies security.istio.io/v1beta1 true AuthorizationPolicy
peerauthentications pa security.istio.io/v1beta1 true PeerAuthentication
requestauthentications ra security.istio.io/v1beta1 true RequestAuthentication
telemetries telemetry telemetry.istio.io/v1alpha1 true Telemetry定义kiali Gateway
定义kiali Gateway格式
# kubectl explain gw
KIND: Gateway
VERSION: networking.istio.io/v1beta1
DESCRIPTION:
<empty>
FIELDS:
apiVersion <string>
APIVersion defines the versioned schema of this representation of an
object. Servers should convert recognized schemas to the latest internal
value, and may reject unrecognized values. More info:
https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources
kind <string>
Kind is a string value representing the REST resource this object
represents. Servers may infer this from the endpoint the client submits
requests to. Cannot be updated. In CamelCase. More info:
https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds
metadata <Object>
Standard object's metadata. More info:
https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#metadata
spec <Object>
Configuration affecting edge load balancer. See more details at:
https://istio.io/docs/reference/config/networking/gateway.html
status <>kiali-gateway.yaml
apiVersion: networking.istio.io/v1beta1
kind: Gateway
metadata:
name: kiali-gateway
namespace: istio-system
spec:
selector:
app: istio-ingressgateway
servers:
- port:
number: 80
name: http
protocol: HTTP
hosts:
- "kiali.wgs.com"
---创建kiali-gateway资源
# kubectl apply -f kiali-gateway.yaml
gateway.networking.istio.io/kiali-gateway created查看Ingress-gateway配置下发状态
# istioctl proxy-status
NAME CLUSTER CDS LDS EDS RDS ECDS ISTIOD VERSION
istio-egressgateway-fffc799cf-vt4b7.istio-system Kubernetes SYNCED SYNCED SYNCED NOT SENT NOT SENT istiod-5456fd558d-7l7xd 1.15.2
istio-ingressgateway-7d68764b55-n2wk8.istio-system Kubernetes SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-5456fd558d-7l7xd 1.15.2查看Ingress-gateway listeners
~# istioctl proxy-config listeners $InGW_POD -n istio-system
ADDRESS PORT MATCH DESTINATION
0.0.0.0 8080 ALL Route: http.8080 # 80端口自动转为8080端口
0.0.0.0 15021 ALL Inline Route: /healthz/ready*
0.0.0.0 15090 ALL Inline Route: /stats/prometheus*查看Ingress-gateway route
# istioctl proxy-config routes $InGW_POD -n istio-system
NAME DOMAINS MATCH VIRTUAL SERVICE
http.20001 * /* 404
* /healthz/ready*
* /stats/prometheus* 定义kiali VirtualService
kiali vs只生效在ingress-gateway上,不会生效在网格内部。
查看Istio gw
# kubectl get gw -n istio-system
NAME AGE
kiali-gateway 17m查看kiali svc
# kubectl get svc -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
grafana ClusterIP 10.100.157.116 <none> 3000/TCP 81m
istio-egressgateway ClusterIP 10.100.86.184 <none> 80/TCP,443/TCP 26h
istio-ingressgateway LoadBalancer 10.100.63.147 <pending> 15021:43732/TCP,80:55697/TCP,443:59179/TCP,31400:43335/TCP,15443:33703/TCP 26h
istiod ClusterIP 10.100.50.155 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 26h
jaeger-collector ClusterIP 10.100.28.65 <none> 14268/TCP,14250/TCP,9411/TCP 81m
kiali ClusterIP 10.100.210.78 <none> 20001/TCP,9090/TCP 81m
prometheus ClusterIP 10.100.71.239 <none> 9090/TCP 81m
tracing ClusterIP 10.100.204.40 <none> 80/TCP,16685/TCP 81m
zipkin ClusterIP 10.100.243.124 <none> 9411/TCP 81m定义kiali VirtualService格式
# kubectl explain vs.spec
KIND: VirtualService
VERSION: networking.istio.io/v1beta1
RESOURCE: spec <Object>
DESCRIPTION:
Configuration affecting label/content routing, sni routing, etc. See more
details at:
https://istio.io/docs/reference/config/networking/virtual-service.html
FIELDS:
exportTo <[]string>
A list of namespaces to which this virtual service is exported.
gateways <[]string>
The names of gateways and sidecars that should apply these routes.
hosts <[]string>
The destination hosts to which traffic is being sent.
http <[]Object>
An ordered list of route rules for HTTP traffic.
tcp <[]Object>
An ordered list of route rules for opaque TCP traffic.
tls <[]Object>kiali-vs.yaml
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:
name: kiali-vs
namespace: istio-system
spec:
hosts:
- "kiali.wgs.com"
gateways:
- kiali-gateway
http:
- match:
- uri:
prefix: /
route:
- destination:
host: kiali
port:
number: 20001
---创建kiali vs资源
# kubectl apply -f kiali-vs.yaml
virtualservice.networking.istio.io/kiali-vs created查看kiali vs资源
# kubectl get vs -n istio-system
NAME GATEWAYS HOSTS AGE
kiali-vs ["kiali-gateway"] ["kiali.wgs.com"] 13s查看ingress-gateway路由
~# istioctl proxy-config routes $InGW_POD -n istio-system
NAME DOMAINS MATCH VIRTUAL SERVICE
http.8080 kiali.wgs.com /* kiali-vs.istio-system
* /stats/prometheus*
* /healthz/ready* 查看ingress-gateway cluster
~# istioctl proxy-config clusters $InGW_POD -n istio-system
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
BlackHoleCluster - - - STATIC
agent - - - STATIC
dashboard-metrics-scraper.kubernetes-dashboard.svc.cluster.local 8000 - outbound EDS
grafana.istio-system.svc.cluster.local 3000 - outbound EDS
istio-egressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-egressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 31400 - outbound EDS
istiod.istio-system.svc.cluster.local 443 - outbound EDS
istiod.istio-system.svc.cluster.local 15010 - outbound EDS
istiod.istio-system.svc.cluster.local 15012 - outbound EDS
istiod.istio-system.svc.cluster.local 15014 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 9411 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14250 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14268 - outbound EDS
kiali.istio-system.svc.cluster.local 9090 - outbound EDS
kiali.istio-system.svc.cluster.local 20001 - outbound EDS
kube-dns.kube-system.svc.cluster.local 53 - outbound EDS
kube-dns.kube-system.svc.cluster.local 9153 - outbound EDS
kubernetes-dashboard.kubernetes-dashboard.svc.cluster.local 443 - outbound EDS
kubernetes.default.svc.cluster.local 443 - outbound EDS
prometheus.istio-system.svc.cluster.local 9090 - outbound EDS
prometheus_stats - - - STATIC
sds-grpc - - - STATIC
tracing.istio-system.svc.cluster.local 80 - outbound EDS
tracing.istio-system.svc.cluster.local 16685 - outbound EDS
xds-grpc - - - STATIC
zipkin - - - STRICT_DNS
zipkin.istio-system.svc.cluster.local 9411 - outbound EDS 查看ingress-gateway endpoint
istio-system pods信息
~# kubectl get pods -n istio-system -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
grafana-56bdf8bf85-nbqbz 1/1 Running 1 (15m ago) 23h 172.20.44.214 192.168.174.107 <none> <none>
istio-egressgateway-fffc799cf-vt4b7 1/1 Running 2 (15m ago) 2d 172.20.44.215 192.168.174.107 <none> <none>
istio-ingressgateway-7d68764b55-n2wk8 1/1 Running 2 (15m ago) 2d 172.20.44.217 192.168.174.107 <none> <none>
istiod-5456fd558d-7l7xd 1/1 Running 2 (15m ago) 2d 172.20.44.216 192.168.174.107 <none> <none>
jaeger-c4fdf6674-x68jz 1/1 Running 1 (15m ago) 23h 172.20.89.146 192.168.174.108 <none> <none>
kiali-5ff49b9f69-5vj5g 1/1 Running 1 (15m ago) 23h 172.20.154.201 192.168.174.106 <none> <none>
prometheus-85949fddb-vhrff 2/2 Running 2 (15m ago) 23h 172.20.154.200 192.168.174.106 <none> <none>ingress-gateway endpoint
~# istioctl proxy-config endpoint $InGW_POD -n istio-system
ENDPOINT STATUS OUTLIER CHECK CLUSTER
10.100.29.132:9411 HEALTHY OK zipkin
127.0.0.1:15000 HEALTHY OK prometheus_stats
127.0.0.1:15020 HEALTHY OK agent
172.20.154.208:8080 HEALTHY OK outbound|80||istio-egressgateway.istio-system.svc.cluster.local
172.20.154.208:8443 HEALTHY OK outbound|443||istio-egressgateway.istio-system.svc.cluster.local
172.20.154.209:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
172.20.154.209:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
172.20.154.209:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
172.20.154.209:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
172.20.154.209:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
172.20.154.210:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
172.20.154.210:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
172.20.154.210:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
172.20.154.210:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
172.20.154.210:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
172.20.154.210:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
172.20.154.211:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
172.20.154.212:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
172.20.154.212:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
172.20.44.232:8000 HEALTHY OK outbound|8000||dashboard-metrics-scraper.kubernetes-dashboard.svc.cluster.local
172.20.44.233:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
172.20.44.233:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
172.20.44.234:8443 HEALTHY OK outbound|443||kubernetes-dashboard.kubernetes-dashboard.svc.cluster.local
172.20.89.157:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
172.20.89.158:15010 HEALTHY OK outbound|15010||istiod.istio-system.svc.cluster.local
172.20.89.158:15012 HEALTHY OK outbound|15012||istiod.istio-system.svc.cluster.local
172.20.89.158:15014 HEALTHY OK outbound|15014||istiod.istio-system.svc.cluster.local
172.20.89.158:15017 HEALTHY OK outbound|443||istiod.istio-system.svc.cluster.local
192.168.174.100:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
192.168.174.101:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
192.168.174.102:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
unix://./etc/istio/proxy/XDS HEALTHY OK xds-grpc
unix://./var/run/secrets/workload-spiffe-uds/socket HEALTHY OK sds-grpcingress-gateway svc 开放kiali端口
查看Ingress-gateway svc资源
~# kubectl get svc -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
grafana ClusterIP 10.100.157.116 <none> 3000/TCP 23h
istio-egressgateway ClusterIP 10.100.86.184 <none> 80/TCP,443/TCP 2d
istio-ingressgateway LoadBalancer 10.100.63.147 <pending> 15021:43732/TCP,80:55697/TCP,443:59179/TCP,31400:43335/TCP,15443:33703/TCP 2d
istiod ClusterIP 10.100.50.155 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 2d
jaeger-collector ClusterIP 10.100.28.65 <none> 14268/TCP,14250/TCP,9411/TCP 23h
kiali ClusterIP 10.100.210.78 <none> 20001/TCP,9090/TCP 23h
prometheus ClusterIP 10.100.71.239 <none> 9090/TCP 23h
tracing ClusterIP 10.100.204.40 <none> 80/TCP,16685/TCP 23h
zipkin ClusterIP 10.100.243.124 <none> 9411/TCP 23h查看主机ip地址
使用ens36的网卡IP不能使用ens33网卡的IP地址,ens33网卡IP地址用户k8s集群节点地址。
root@k8s-node-03:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:50:56:3b:9c:ae brd ff:ff:ff:ff:ff:ff
altname enp2s1
inet 192.168.174.108/24 brd 192.168.174.255 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80::250:56ff:fe3b:9cae/64 scope link
valid_lft forever preferred_lft forever
3: ens36: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:72:7a:aa brd ff:ff:ff:ff:ff:ff
altname enp2s4
inet 192.168.174.109/24 metric 100 brd 192.168.174.255 scope global dynamic ens36
valid_lft 1790sec preferred_lft 1790sec
inet6 fe80::20c:29ff:fe72:7aaa/64 scope link
valid_lft forever preferred_lft foreverIngress-gateway svc 添加externalIPs
# kubectl patch svc istio-ingressgateway -n istio-system -p '{"spec":{"externalIPs": ["192.168.174.109"]}}'查看externalIPs
# kubectl get svc -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
grafana ClusterIP 10.100.124.243 <none> 3000/TCP 8m22s
istio-egressgateway ClusterIP 10.100.121.95 <none> 80/TCP,443/TCP 22m
istio-ingressgateway LoadBalancer 10.100.145.112 192.168.174.109 15021:32417/TCP,20001:53216/TCP,80:46683/TCP,443:37652/TCP,31400:59146/TCP,15443:30622/TCP 22m
istiod ClusterIP 10.100.149.76 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 22m
jaeger-collector ClusterIP 10.100.122.235 <none> 14268/TCP,14250/TCP,9411/TCP 8m21s
kiali ClusterIP 10.100.48.203 <none> 20001/TCP,9090/TCP 8m21s
prometheus ClusterIP 10.100.42.102 <none> 9090/TCP 8m21s
tracing ClusterIP 10.100.92.199 <none> 80/TCP,16685/TCP 8m21s
zipkin ClusterIP 10.100.29.132 <none> 9411/TCP 8m21s定义kiaki DestinationRule
查看kiali DestinationRule 格式
~# kubectl explain dr
KIND: DestinationRule
VERSION: networking.istio.io/v1beta1
DESCRIPTION:
<empty>
FIELDS:
apiVersion <string>
APIVersion defines the versioned schema of this representation of an
object. Servers should convert recognized schemas to the latest internal
value, and may reject unrecognized values. More info:
https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources
kind <string>
Kind is a string value representing the REST resource this object
represents. Servers may infer this from the endpoint the client submits
requests to. Cannot be updated. In CamelCase. More info:
https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds
metadata <Object>
Standard object's metadata. More info:
https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#metadata
spec <Object>
Configuration affecting load balancing, outlier detection, etc. See more
details at:
https://istio.io/docs/reference/config/networking/destination-rule.html
status <>kiali-dr.yaml
apiVersion: networking.istio.io/v1beta1
kind: DestinationRule
metadata:
name: kiali
namespace: istio-system
spec:
host: kiali
trafficPolicy:
tls:
mode: DISABLE
---创建kiali dr资源
# kubectl apply -f kiali-dr.yaml
destinationrule.networking.istio.io/kiali created查看kiali dr资源
# kubectl get dr -n istio-system
NAME HOST AGE
kiali kiali 45s查看DestinationRule
~# istioctl proxy-config cluster $InGW_POD -n istio-system
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
BlackHoleCluster - - - STATIC
agent - - - STATIC
dashboard-metrics-scraper.kubernetes-dashboard.svc.cluster.local 8000 - outbound EDS
grafana.istio-system.svc.cluster.local 3000 - outbound EDS
istio-egressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-egressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 20001 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 31400 - outbound EDS
istiod.istio-system.svc.cluster.local 443 - outbound EDS
istiod.istio-system.svc.cluster.local 15010 - outbound EDS
istiod.istio-system.svc.cluster.local 15012 - outbound EDS
istiod.istio-system.svc.cluster.local 15014 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 9411 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14250 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14268 - outbound EDS
kiali.istio-system.svc.cluster.local 9090 - outbound EDS kiali.istio-system
kiali.istio-system.svc.cluster.local 20001 - outbound EDS kiali.istio-system
kube-dns.kube-system.svc.cluster.local 53 - outbound EDS
kube-dns.kube-system.svc.cluster.local 9153 - outbound EDS
kubernetes-dashboard.kubernetes-dashboard.svc.cluster.local 443 - outbound EDS
kubernetes.default.svc.cluster.local 443 - outbound EDS
prometheus.istio-system.svc.cluster.local 9090 - outbound EDS
prometheus_stats - - - STATIC
sds-grpc - - - STATIC
tracing.istio-system.svc.cluster.local 80 - outbound EDS
tracing.istio-system.svc.cluster.local 16685 - outbound EDS
xds-grpc - - - STATIC
zipkin - - - STRICT_DNS
zipkin.istio-system.svc.cluster.local 9411 - outbound EDS 查看Ingress-gateway svc
# kubectl get svc -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
grafana ClusterIP 10.100.124.243 <none> 3000/TCP 21h
istio-egressgateway ClusterIP 10.100.121.95 <none> 80/TCP,443/TCP 21h
istio-ingressgateway LoadBalancer 10.100.145.112 192.168.174.250 15021:32417/TCP,80:46683/TCP,443:37652/TCP,31400:59146/TCP,15443:30622/TCP 21h
istiod ClusterIP 10.100.149.76 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 21h
jaeger-collector ClusterIP 10.100.122.235 <none> 14268/TCP,14250/TCP,9411/TCP 21h
kiali ClusterIP 10.100.48.203 <none> 20001/TCP,9090/TCP 21h
prometheus ClusterIP 10.100.42.102 <none> 9090/TCP 21h
tracing ClusterIP 10.100.92.199 <none> 80/TCP,16685/TCP 21h
zipkin ClusterIP 10.100.29.132 <none> 9411/TCP 21h添加hosts
192.168.174.109 kiali.wgs.com访问kiali
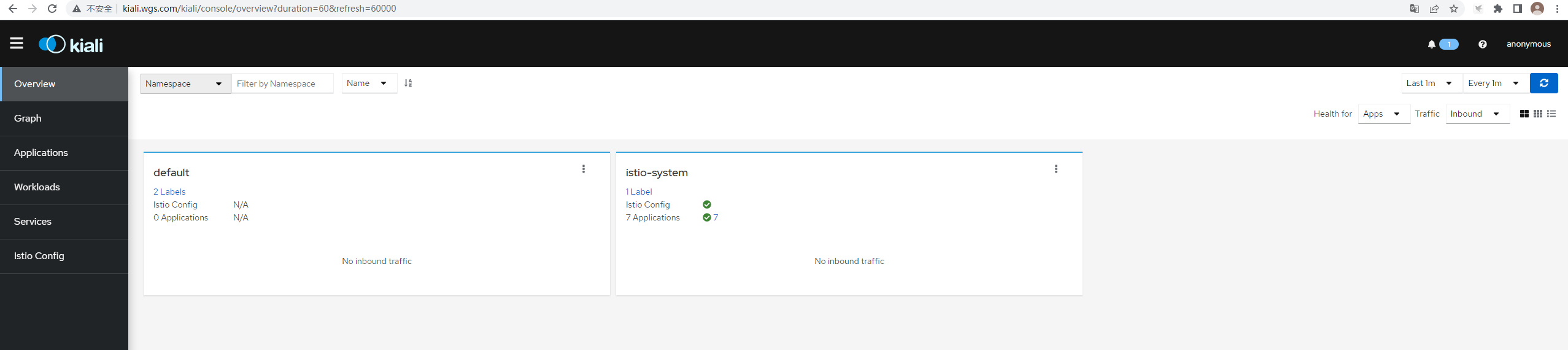
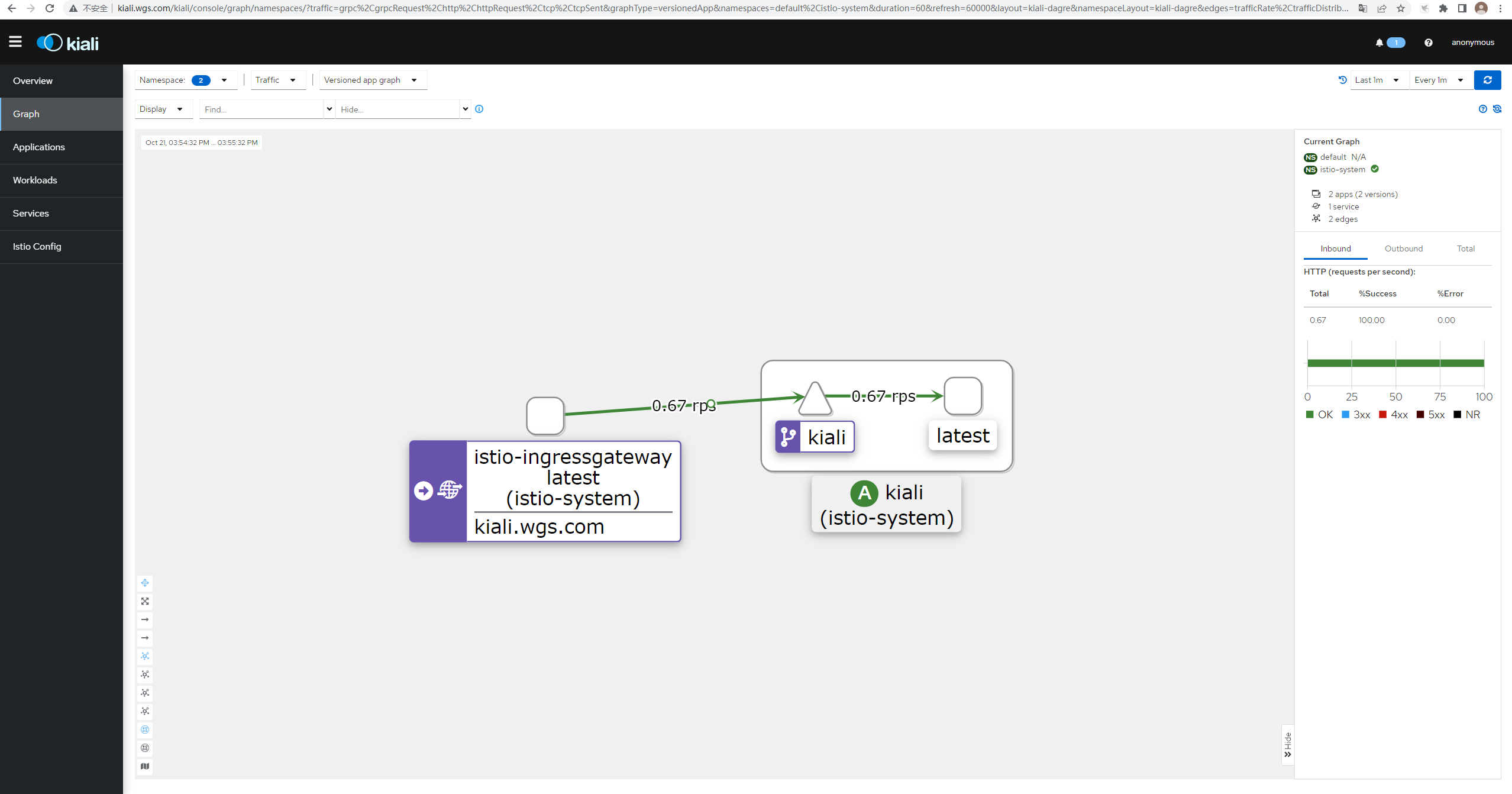
通过Ingress-Gateway暴露grafana
查看Ingress-Gateway label
# kubectl get pods -n istio-system --show-labels
NAME READY STATUS RESTARTS AGE LABELS
grafana-56bdf8bf85-nbqbz 1/1 Running 0 53m app.kubernetes.io/instance=grafana,app.kubernetes.io/name=grafana,app=grafana,pod-template-hash=56bdf8bf85,sidecar.istio.io/inject=false
istio-egressgateway-fffc799cf-vt4b7 1/1 Running 1 (4h38m ago) 26h app=istio-egressgateway,chart=gateways,heritage=Tiller,install.operator.istio.io/owning-resource=unknown,istio.io/rev=default,istio=egressgateway,operator.istio.io/component=EgressGateways,pod-template-hash=fffc799cf,release=istio,service.istio.io/canonical-name=istio-egressgateway,service.istio.io/canonical-revision=latest,sidecar.istio.io/inject=false
istio-ingressgateway-7d68764b55-n2wk8 1/1 Running 1 (4h38m ago) 26h app=istio-ingressgateway,chart=gateways,heritage=Tiller,install.operator.istio.io/owning-resource=unknown,istio.io/rev=default,istio=ingressgateway,operator.istio.io/component=IngressGateways,pod-template-hash=7d68764b55,release=istio,service.istio.io/canonical-name=istio-ingressgateway,service.istio.io/canonical-revision=latest,sidecar.istio.io/inject=false
istiod-5456fd558d-7l7xd 1/1 Running 1 (4h38m ago) 26h app=istiod,install.operator.istio.io/owning-resource=unknown,istio.io/rev=default,istio=pilot,operator.istio.io/component=Pilot,pod-template-hash=5456fd558d,sidecar.istio.io/inject=false
jaeger-c4fdf6674-x68jz 1/1 Running 0 53m app=jaeger,pod-template-hash=c4fdf6674
kiali-5ff49b9f69-5vj5g 1/1 Running 0 53m app.kubernetes.io/instance=kiali,app.kubernetes.io/managed-by=Helm,app.kubernetes.io/name=kiali,app.kubernetes.io/part-of=kiali,app.kubernetes.io/version=v1.55.1,app=kiali,helm.sh/chart=kiali-server-1.55.1,pod-template-hash=5ff49b9f69,sidecar.istio.io/inject=false,version=v1.55.1
prometheus-85949fddb-vhrff 2/2 Running 0 53m app=prometheus,chart=prometheus-15.9.0,component=server,heritage=Helm,pod-template-hash=85949fddb,release=prometheus,sidecar.istio.io/inject=false获取Ingress-Gateway pod name
# kubectl get pods -l app=istio-ingressgateway -n istio-system -o jsonpath={.items[0].metadata.name}
istio-ingressgateway-7d68764b55-n2wk8
# InGW_POD=$(kubectl get pods -l app=istio-ingressgateway -n istio-system -o jsonpath={.items[0].metadata.name})查看Istio api group
# kubectl api-resources |grep istio
wasmplugins extensions.istio.io/v1alpha1 true WasmPlugin
istiooperators iop,io install.istio.io/v1alpha1 true IstioOperator
destinationrules dr networking.istio.io/v1beta1 true DestinationRule
envoyfilters networking.istio.io/v1alpha3 true EnvoyFilter
gateways gw networking.istio.io/v1beta1 true Gateway
proxyconfigs networking.istio.io/v1beta1 true ProxyConfig
serviceentries se networking.istio.io/v1beta1 true ServiceEntry
sidecars networking.istio.io/v1beta1 true Sidecar
virtualservices vs networking.istio.io/v1beta1 true VirtualService
workloadentries we networking.istio.io/v1beta1 true WorkloadEntry
workloadgroups wg networking.istio.io/v1beta1 true WorkloadGroup
authorizationpolicies security.istio.io/v1beta1 true AuthorizationPolicy
peerauthentications pa security.istio.io/v1beta1 true PeerAuthentication
requestauthentications ra security.istio.io/v1beta1 true RequestAuthentication
telemetries telemetry telemetry.istio.io/v1alpha1 true Telemetry定义grafana Gateway
grafana-gateway.yaml
apiVersion: networking.istio.io/v1beta1
kind: Gateway
metadata:
name: grafana-gateway
namespace: istio-system
spec:
selector:
app: istio-ingressgateway
servers:
- port:
number: 80
name: http
protocol: HTTP
hosts:
- "grafana.wgs.com"
---创建grafana-gateway资源
# kubectl apply -f grafana-gw.yaml
gateway.networking.istio.io/grafana-gateway created查看Ingress-gateway listeners
~# istioctl proxy-config listeners $InGW_POD -n istio-system
ADDRESS PORT MATCH DESTINATION
0.0.0.0 8080 ALL Route: http.8080 # 80端口自动转为8080端口
0.0.0.0 15021 ALL Inline Route: /healthz/ready*
0.0.0.0 15090 ALL Inline Route: /stats/prometheus*查看Ingress-gateway routes
~# istioctl proxy-config routes $InGW_POD -n istio-system
NAME DOMAINS MATCH VIRTUAL SERVICE
http.8080 * /* 404
* /stats/prometheus*
* /healthz/ready* 定义grafana VirtualService
grafana-vs.yaml
apiVersion: networking.istio.io/v1beta1
kind: VirtualService
metadata:
name: grafana-vs
namespace: istio-system
spec:
hosts:
- "grafana.wgs.com"
gateways:
- grafana-gateway
http:
- match:
- uri:
prefix: /
route:
- destination:
host: grafana
port:
number: 3000
---创建grafana vs资源
# kubectl apply -f grafana-vs.yaml
virtualservice.networking.istio.io/grafana-vs created查看Ingress-gateway routes
~# istioctl proxy-config routes $InGW_POD -n istio-system
NAME DOMAINS MATCH VIRTUAL SERVICE
http.8080 grafana.wgs.com /* grafana-vs.istio-system
* /stats/prometheus*
* /healthz/ready* 定义grafana DestinationRule
grafana-dr.yaml
apiVersion: networking.istio.io/v1beta1
kind: DestinationRule
metadata:
name: grafana
namespace: istio-system
spec:
host: grafana
trafficPolicy:
tls:
mode: DISABLE
---创建grafana dr资源
# kubectl apply -f grafana-dr.yaml
destinationrule.networking.istio.io/grafana created查看Ingress-gateway svc
# kubectl get svc -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
grafana ClusterIP 10.100.124.243 <none> 3000/TCP 20h
istio-egressgateway ClusterIP 10.100.121.95 <none> 80/TCP,443/TCP 21h
istio-ingressgateway LoadBalancer 10.100.145.112 192.168.174.250 15021:32417/TCP,80:46683/TCP,443:37652/TCP,31400:59146/TCP,15443:30622/TCP 21h
istiod ClusterIP 10.100.149.76 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 21h
jaeger-collector ClusterIP 10.100.122.235 <none> 14268/TCP,14250/TCP,9411/TCP 20h
kiali ClusterIP 10.100.48.203 <none> 20001/TCP,9090/TCP 20h
prometheus ClusterIP 10.100.42.102 <none> 9090/TCP 20h
tracing ClusterIP 10.100.92.199 <none> 80/TCP,16685/TCP 20h
zipkin ClusterIP 10.100.29.132 <none> 9411/TCP 20h添加hosts
192.168.174.109 grafana.wgs.com访问grafana
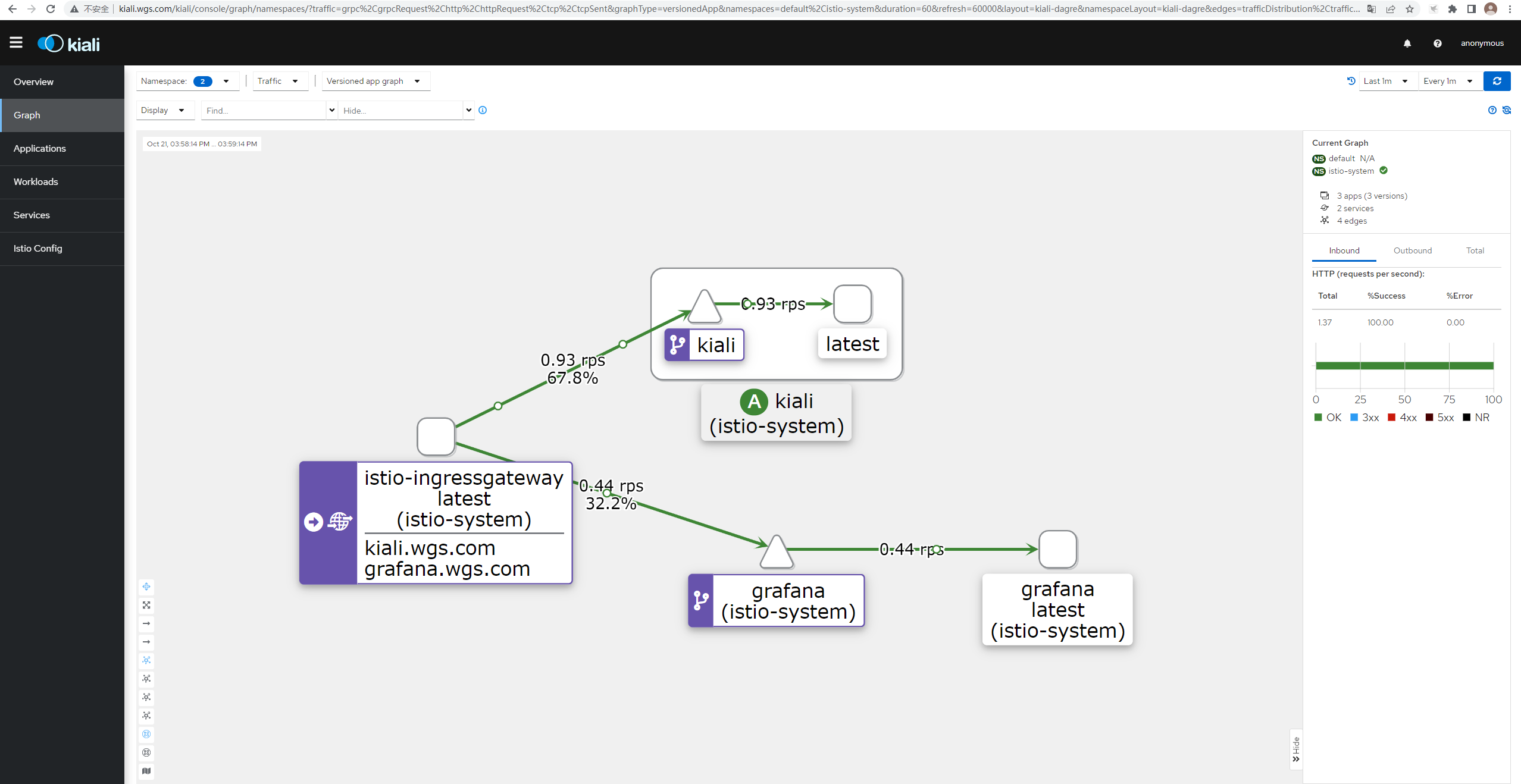
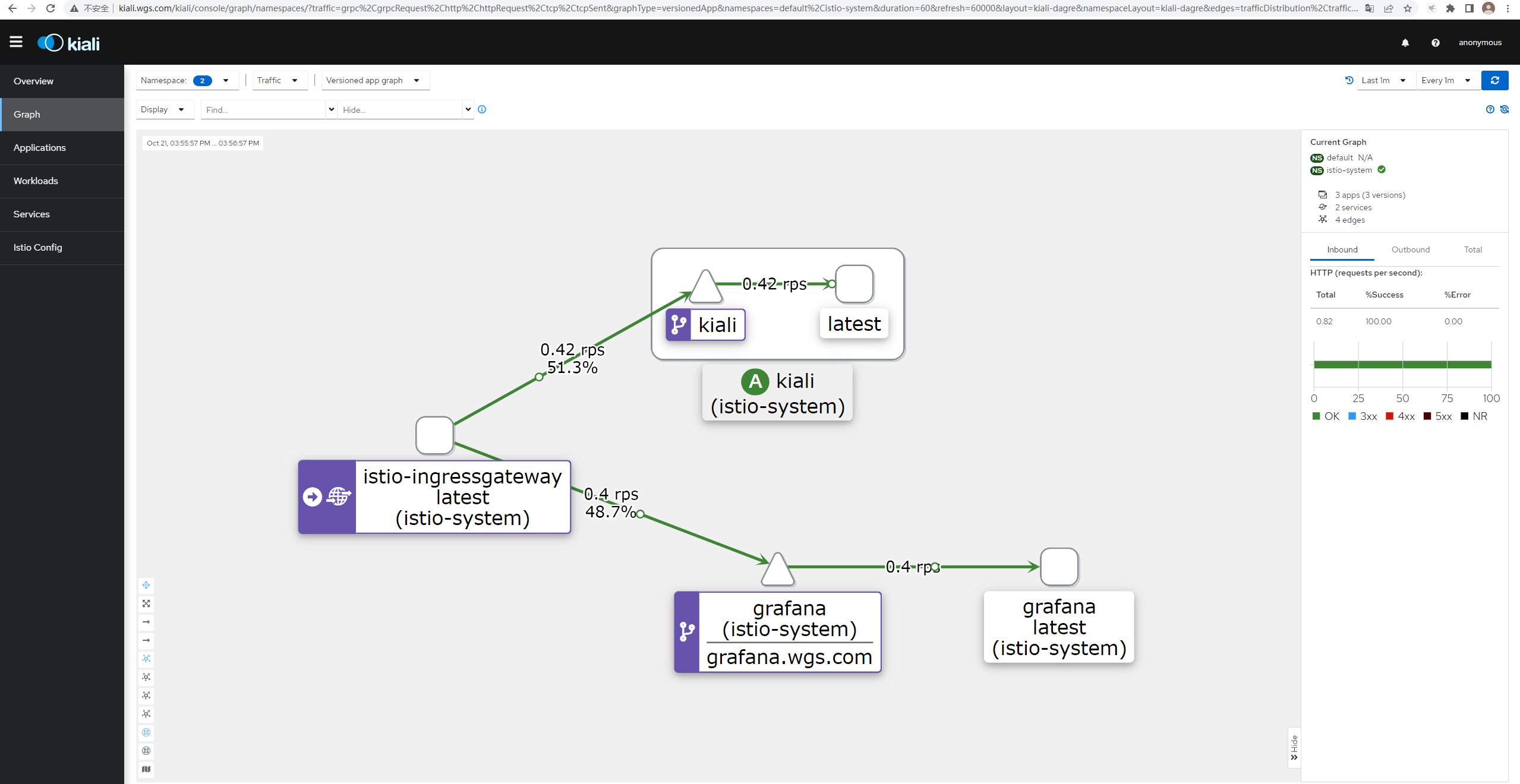
访问kiali
参考文档
流量管理:https://istio.io/latest/docs/reference/config/networking/



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· Manus的开源复刻OpenManus初探
· 写一个简单的SQL生成工具
· AI 智能体引爆开源社区「GitHub 热点速览」