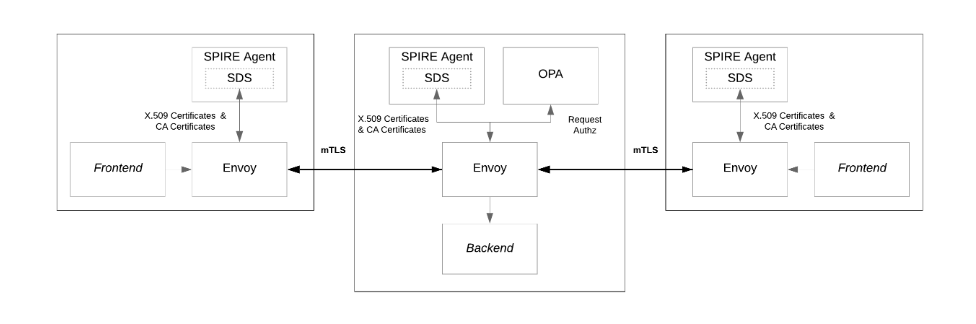
架构示例
envoy.yaml
node:
id: "backend"
cluster: "demo-cluster-spire"
static_resources:
listeners:
- address:
socket_address:
address: 0.0.0.0
port_value: 8000
filter_chains:
- filters:
- name: envoy.filters.network.http_connection_manager
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager
codec_type: AUTO
stat_prefix: ingress_http
route_config:
name: local_route
virtual_hosts:
- name: upstream
domains:
- "*"
routes:
- match:
prefix: "/"
route:
cluster: upstream-service
http_filters:
- name: envoy.filters.http.ext_authz # OPA
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.http.ext_authz.v3.ExtAuthz
with_request_body:
max_request_bytes: 8192
allow_partial_message: true
failure_mode_allow: false
grpc_service:
envoy_grpc:
cluster_name: ext_authz-opa-service
timeout: 0.250s
transport_api_version: V3
- name: envoy.filters.http.router
transport_socket:
name: envoy.transport_sockets.tls # spire
typed_config:
"@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.DownstreamTlsContext
common_tls_context:
tls_certificate_sds_secret_configs:
- name: "spiffe://wgs.com/backend-server"
sds_config:
api_config_source:
api_type: GRPC
grpc_services:
envoy_grpc:
cluster_name: spire_agent
transport_api_version: V3
resource_api_version: V3
combined_validation_context:
# validate the SPIFFE ID of incoming clients (optionally)
default_validation_context:
match_subject_alt_names:
exact: "spiffe://wgs.com/frontend-server"
# obtain the trust bundle from SDS
validation_context_sds_secret_config:
name: "spiffe://wgs.com"
sds_config:
api_config_source:
api_type: GRPC
grpc_services:
envoy_grpc:
cluster_name: spire_agent
transport_api_version: V3
resource_api_version: V3
tls_params:
ecdh_curves:
- X25519:P-256:P-521:P-384
clusters:
- name: spire_agent
connect_timeout: 0.25s
http2_protocol_options: {}
load_assignment:
cluster_name: spire_agent
endpoints:
- lb_endpoints:
- endpoint:
address:
pipe:
path: /tmp/agent.sock
- name: upstream-service
type: STRICT_DNS
lb_policy: ROUND_ROBIN
load_assignment:
cluster_name: upstream-service
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address:
address: 127.0.0.1
port_value: 80
- name: ext_authz-opa-service # openpolicyagent/opa:latest-envoy
type: STRICT_DNS
lb_policy: ROUND_ROBIN
typed_extension_protocol_options:
envoy.extensions.upstreams.http.v3.HttpProtocolOptions:
"@type": type.googleapis.com/envoy.extensions.upstreams.http.v3.HttpProtocolOptions
explicit_http_config:
http2_protocol_options: {}
load_assignment:
cluster_name: ext_authz-opa-service
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address:
address: ext_authz-opa-service
port_value: 9191
policy.rego
package envoy.authz
import input.attributes.request.http as http_request
default allow = false
response := {
"allowed": true,
"headers": {"x-current-user": "OPA"}
}
allow = response {
http_request.method == "GET"
}
allow = response {
http_request.method == "POST"
glob.match("/livez", ["/"], http_request.path)
}
docker-compose.yaml
version: "3.7"
services:
spire-server:
image: uhub.service.ucloud.cn/xk-base/spire-server:1.4.0
hostname: spire-server
volumes:
- ./conf/spire-server.conf /opt/spire/conf/server/server.conf
- ./conf/agent-cacert.crt.pem /opt/spire/conf/server/agent-cacert.pem
tty: true
privileged: true
networks:
envoymesh:
aliases:
- spire-server
front-envoy:
image: envoyproxy/envoy:v1.23-latest
volumes:
- ./front-envoy/front-envoy-zipkin.yaml:/etc/envoy/envoy.yaml
networks:
envoymesh:
aliases:
- front-envoy
- front
ports:
- "8000:8000"
- "9901:9901"
upstream-service:
image: nginx
network_mode: "service:front-envoy"
depends_on:
- front-envoy
ext_authz-opa-service:
image: openpolicyagent/opa:latest-envoy
volumes:
- ./policy.rego:/etc/policy.rego
ports:
- "9191:9191"
command:
- run
- --server
- --addr=localhost:8181
- --diagnostic-addr=0.0.0.0:8282
- --set=services.default.url=http://127.0.0.1:8888
- --set=bundles.default.resource=bundle.tar.gz
- --set=plugins.envoy_ext_authz_grpc.addr=:9191
- --set=plugins.envoy_ext_authz_grpc.path=envoy/authz/allow
- --set=decision_logs.console=true
- --set=status.console=true
- --ignore=.*
- /etc/policy.rego
networks:
envoymesh:
aliases:
- opa
networks:
envoymesh:
driver: bridge
ipam:
config:
- subnet: 172.31.92.0/24



 浙公网安备 33010602011771号
浙公网安备 33010602011771号