docker-compose部署consul v1.12.3
系统设置
软件清单
系统:ubuntu20.04
镜像:hashicorp/consul:1.12.3
docker-compose:v2.7.0
系统时间同步
apt -y install chrony
systemctl start chrony
systemctl enable chrony系统要求
硬件要求
| Size | CPU | Memory | Disk Capacity | Disk IO | Disk Throughput |
|---|---|---|---|---|---|
| Small | 2-4 core | 8-16 GB RAM | 100+ GB | 3000+ IOPS | 75+ MB/s |
| Large | 8-16 core | 32-64 GB RAM | 200+ GB | 7500+ IOPS | 250+ MB/s |
网络要求
对于所有 Consul 代理之间发送的数据,必须满足以下延迟要求:
- 所有流量的平均 RTT 不能超过 50 毫秒。
- 99% 的流量的 RTT 不能超过 100 毫秒。
端口列表
| Name | Port / Protocol | Source | Destination | Description |
|---|---|---|---|---|
| RPC | 8300 / TCP | All agents (client & server) | Server agents | 服务器使用它来处理来自其他代理的传入请求。 |
| Serf LAN | 8301 / TCP & UDP | All agents (client & server) | All agents (client & server) | 用于处理局域网中的 gossip 。所有代理都需要。 |
| Serf WAN | 8302 / TCP & UDP | Server agents | Server agents | 服务器代理使用它通过 WAN 向其他服务器代理发送消息。仅用于多集群环境。 |
| HTTP/HTTPS | 8500 & 8501 TCP | Localhost of client or server agent | Localhost of client or server agent | 客户端用于与 HTTP API 通信。默认情况下禁用 HTTPS。 |
| DNS | 8600 TCP & UDP | Localhost of client or server agent | Localhost of client or server agent | 用于解析 DNS 查询。 |
| gRPC (可选) | 8502 TCP | Envoy proxy | Client agent or server agent that manages the sidecar proxies service registration | 用于向 Envoy 代理公开 xDS API。默认禁用。 |
| Sidecar Proxy (可选) | 21000 - 21255 TCP | All agents (client & server) | Client agent or server agent that manages the sidecar proxies service registration | 用于自动分配的 sidecar 服务注册的端口范围。 |
参考文档
https://learn.hashicorp.com/tutorials/consul/docker-container-agents?in=consul/docker
https://github.com/hashicorp/learn-consul-docker.git
准备安全凭证
生成gossip 加密密钥
~# docker run -it --rm -v /data/apps/consul/server1.json:/consul/config/server1.json hashicorp/consul:1.12.3 consul keygen
sbfg+8FFJT0JHoIpTOsQMJgv5Xmnl/Th9rZt+YfXu8I=为 RPC 加密生成 TLS 证书
创建证书颁发机构
Start by creating the CA on your admin instance, using the Consul CLI.
创建命令格式
consul tls ca create -domain <domain>
~# docker run -it --rm -v /data/apps/consul/certs:/consul/config/certs/ hashicorp/consul:1.12.3 sh
/ # cd /consul/config/certs/
/consul/config/certs # consul tls ca create -domain consul
==> Saved consul-agent-ca.pem
==> Saved consul-agent-ca-key.pem创建证书
接下来创建一组证书,每个 Consul 代理一个。您现在需要为您的主数据中心选择一个名称,以便正确命名证书以及您的 Consul 数据中心的域。
~# consul tls cert create -server -dc <dc_name> -domain <domain> #创建格式
~# docker run -it --rm -v /data/apps/consul/certs:/consul/config/certs/ hashicorp/consul:1.12.3 sh
/ # cd /consul/config/certs/
/consul/config/certs # consul tls cert create -server -dc zhongtai -domain consul
==> WARNING: Server Certificates grants authority to become a
server and access all state in the cluster including root keys
and all ACL tokens. Do not distribute them to production hosts
that are not server nodes. Store them as securely as CA keys.
==> Using consul-agent-ca.pem and hashii-agent-ca-key.pem
==> Saved zhongtai-server-consul-0.pem
==> Saved zhongtai-server-consul-0-key.pem配置文件
https://www.consul.io/docs/agent/config/config-files
server1配置文件
{
"node_name": "consul-server1",
"datacenter": "zhongtai",
"domain": "consul",
"server": true,
"log_level": "INFO",
"ui_config": {
"enabled" : true
},
"auto_encrypt": {
"allow_tls": true
},
"connect": {
"enabled": true
},
"performance": {
"raft_multiplier": 1
},
"data_dir": "/consul/data",
"addresses": {
"grpc" : "127.0.0.1",
"http" : "0.0.0.0"
},
"retry_join":[
"consul-server2",
"consul-server3"
],
"encrypt": "sbfg+8FFJT0JHoIpTOsQMJgv5Xmnl/Th9rZt+YfXu8I=",
"ports": {
"grpc": 8502,
"http": 8500,
"https": 8501
},
"tls": {
"defaults": {
"ca_file": "/consul/config/certs/consul-agent-ca.pem",
"cert_file": "/consul/config/certs/zhongtai-server-consul-0.pem",
"key_file": "/consul/config/certs/zhongtai-server-consul-0-key.pem",
"verify_incoming": true,
"verify_outgoing": true
},
"internal_rpc": {
"verify_server_hostname": true
}
}
}server2配置文件
{
"node_name": "consul-server2",
"datacenter": "zhongtai",
"domain": "consul",
"server": true,
"log_level": "INFO",
"ui_config": {
"enabled" : true
},
"auto_encrypt": {
"allow_tls": true
},
"connect": {
"enabled": true
},
"performance": {
"raft_multiplier": 1
},
"data_dir": "/consul/data",
"addresses": {
"grpc" : "127.0.0.1",
"http" : "0.0.0.0"
},
"retry_join":[
"consul-server1",
"consul-server3"
],
"encrypt": "sbfg+8FFJT0JHoIpTOsQMJgv5Xmnl/Th9rZt+YfXu8I=",
"ports": {
"grpc": 8502,
"http": 8500,
"https": 8501
},
"tls": {
"defaults": {
"ca_file": "/consul/config/certs/consul-agent-ca.pem",
"cert_file": "/consul/config/certs/zhongtai-server-consul-0.pem",
"key_file": "/consul/config/certs/zhongtai-server-consul-0-key.pem",
"verify_incoming": true,
"verify_outgoing": true
},
"internal_rpc": {
"verify_server_hostname": true
}
}
}server3配置文件
{
"node_name": "consul-server3",
"datacenter": "zhongtai",
"domain": "consul",
"server": true,
"log_level": "INFO",
"ui_config": {
"enabled" : true
},
"auto_encrypt": {
"allow_tls": true
},
"connect": {
"enabled": true
},
"performance": {
"raft_multiplier": 1
},
"data_dir": "/consul/data",
"addresses": {
"grpc" : "127.0.0.1",
"http" : "0.0.0.0"
},
"retry_join":[
"consul-server2",
"consul-server1"
],
"encrypt": "sbfg+8FFJT0JHoIpTOsQMJgv5Xmnl/Th9rZt+YfXu8I=",
"ports": {
"grpc": 8502,
"http": 8500,
"https": 8501
},
"tls": {
"defaults": {
"ca_file": "/consul/config/certs/consul-agent-ca.pem",
"cert_file": "/consul/config/certs/zhongtai-server-consul-0.pem",
"key_file": "/consul/config/certs/zhongtai-server-consul-0-key.pem",
"verify_incoming": true,
"verify_outgoing": true
},
"internal_rpc": {
"verify_server_hostname": true
}
}
}client配置文件
{
"node_name": "consul-client",
"datacenter": "zhongtai",
"domain": "consul",
"data_dir": "/consul/data",
"ui_config": {
"enabled" : true
},
"retry_join":[
"consul-server1",
"consul-server2",
"consul-server3"
],
"encrypt": "sbfg+8FFJT0JHoIpTOsQMJgv5Xmnl/Th9rZt+YfXu8I=",
"tls": {
"defaults": {
"ca_file": "/consul/config/certs/consul-agent-ca.pem",
"verify_incoming": true,
"verify_outgoing": true
},
"internal_rpc": {
"verify_server_hostname": true
}
},
"addresses": {
"grpc" : "127.0.0.1",
"http" : "0.0.0.0"
},
"auto_encrypt": {
"tls": true
},
"ports": {
"http": 8500,
"https": 8501,
"grpc": 8502
},
"connect": {
"enabled": true
},
"performance": {
"raft_multiplier": 1
}
}检查配置文件
~# docker run -it --rm -v /data/apps/consul/server1.json:/consul/config/server1.json hashicorp/consul:1.12.3 consul validate /consul/config/
Configuration is valid!docker-compose.yml
version: '3.7'
services:
consul-server1:
image: hashicorp/consul:1.12.3
container_name: consul-server1
restart: always
volumes:
- ./server1.json:/consul/config/server1.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-server1:/consul/data
networks:
- consul
ports:
- "8500:8500"
- "8600:8600/tcp"
- "8600:8600/udp"
command: "agent -bootstrap-expect=3 -client=0.0.0.0 -log-file=/consul/logs/consul-01.log"
consul-server2:
image: hashicorp/consul:1.12.3
container_name: consul-server2
restart: always
volumes:
- ./server2.json:/consul/config/server2.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-server2:/consul/data
networks:
- consul
command: "agent -bootstrap-expect=3 -client=0.0.0.0 -log-file=/consul/logs/consul-02.log "
consul-server3:
image: hashicorp/consul:1.12.3
container_name: consul-server3
restart: always
volumes:
- ./server3.json:/consul/config/server3.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-server3:/consul/data
networks:
- consul
command: "agent -bootstrap-expect=3 -client=0.0.0.0 -log-file=/consul/logs/consul-03.log"
consul-client:
image: hashicorp/consul:1.12.3
container_name: consul-client
restart: always
volumes:
- ./client.json:/consul/config/client.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-client:/consul/data
networks:
- consul
command: "agent -client=0.0.0.0 -log-file=/consul/logs/client-01.log"
networks:
consul:
driver: bridge设置consul权限
查看consul用户信息
~# docker run -it --rm -v /data/apps/consul/server1.json:/consul/config/server1.json hashicorp/consul:1.12.3 id consul
uid=100(consul) gid=1000(consul) groups=1000(consul),1000(consul)设置consul目录权限
~# chown -R 100.1000 /data/apps/consul创建 Consul 数据中心
# docker-compose up -d
[+] Running 4/4
⠿ Container consul-client Started 1.3s 0.7s
⠿ Container consul-server1 Started 1.0s
⠿ Container consul-server2 Started 1.2s
⠿ Container consul-server3 Started 查看consul用户界面
在浏览器上访问http://localhost:8500/以访问 Consul UI

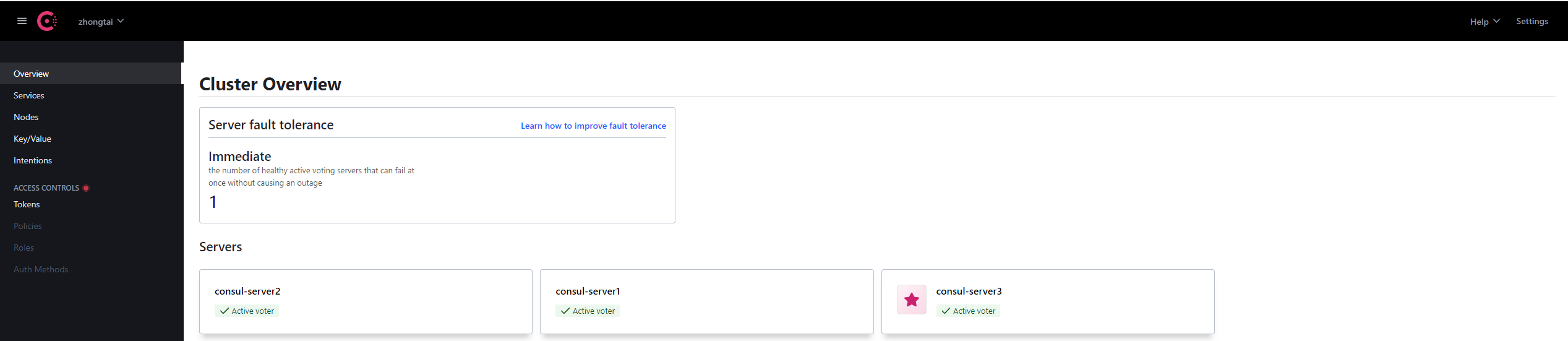
查看consul成员
# docker exec -ti consul-client consul members
Node Address Status Type Build Protocol DC Partition Segment
consul-server1 172.24.0.6:8301 alive server 1.12.3 2 zhongtai default <all>
consul-server2 172.24.0.8:8301 alive server 1.12.3 2 zhongtai default <all>
consul-server3 172.24.0.3:8301 alive server 1.12.3 2 zhongtai default <all>
consul-client 172.24.0.9:8301 alive client 1.12.3 2 zhongtai default <default>添加多个dc
生成 TLS 证书
~# docker run -it --rm -v /data/apps/consul/certs:/consul/config/certs/ hashicorp/consul:1.12.3 sh
/ # cd /consul/config/certs/
/consul/config/certs # consul tls cert create -server -dc hashii
==> WARNING: Server Certificates grants authority to become a
server and access all state in the cluster including root keys
and all ACL tokens. Do not distribute them to production hosts
that are not server nodes. Store them as securely as CA keys.
==> Using consul-agent-ca.pem and hashii-agent-ca-key.pem
==> Saved hashii-server-consul-0.pem
==> Saved hashii-server-consul-0-key.pem配置文件
server_hashii1节点
{
"node_name": "consul-hashii1",
"datacenter": "hashii",
"domain": "consul",
"server": true,
"log_level": "INFO",
"ui_config": {
"enabled" : true
},
"auto_encrypt": {
"allow_tls": true
},
"connect": {
"enabled": true
},
"performance": {
"raft_multiplier": 1
},
"data_dir": "/consul/data",
"addresses": {
"grpc" : "127.0.0.1"
},
"retry_join_wan":[
"consul-server1",
"consul-server2",
"consul-server3"
],
"retry_join":[
"consul-hashii2",
"consul-hashii3"
],
"encrypt": "sbfg+8FFJT0JHoIpTOsQMJgv5Xmnl/Th9rZt+YfXu8I=",
"ports": {
"grpc": 8502,
"http": 8500,
"https": 8501
},
"tls": {
"defaults": {
"ca_file": "/consul/config/certs/consul-agent-ca.pem",
"cert_file": "/consul/config/certs/hashii-server-consul-0.pem",
"key_file": "/consul/config/certs/hashii-server-consul-0-key.pem",
"verify_incoming": true,
"verify_outgoing": true
},
"internal_rpc": {
"verify_server_hostname": true
}
}
}server_hashii2节点
{
"node_name": "consul-hashii2",
"datacenter": "hashii",
"domain": "consul",
"server": true,
"log_level": "INFO",
"ui_config": {
"enabled" : true
},
"auto_encrypt": {
"allow_tls": true
},
"connect": {
"enabled": true
},
"performance": {
"raft_multiplier": 1
},
"data_dir": "/consul/data",
"addresses": {
"grpc" : "127.0.0.1"
},
"retry_join_wan":[
"consul-server1",
"consul-server2",
"consul-server3"
],
"retry_join":[
"consul-hashii1",
"consul-hashii3"
],
"encrypt": "sbfg+8FFJT0JHoIpTOsQMJgv5Xmnl/Th9rZt+YfXu8I=",
"ports": {
"grpc": 8502,
"http": 8500,
"https": 8501
},
"tls": {
"defaults": {
"ca_file": "/consul/config/certs/consul-agent-ca.pem",
"cert_file": "/consul/config/certs/hashii-server-consul-0.pem",
"key_file": "/consul/config/certs/hashii-server-consul-0-key.pem",
"verify_incoming": true,
"verify_outgoing": true
},
"internal_rpc": {
"verify_server_hostname": true
}
}
}server_hashii3节点
{
"node_name": "consul-hashii3",
"datacenter": "hashii",
"domain": "consul",
"server": true,
"log_level": "INFO",
"ui_config": {
"enabled" : true
},
"auto_encrypt": {
"allow_tls": true
},
"connect": {
"enabled": true
},
"performance": {
"raft_multiplier": 1
},
"data_dir": "/consul/data",
"addresses": {
"grpc" : "127.0.0.1"
},
"retry_join_wan":[
"consul-server2",
"consul-server3",
"consul-server1"
],
"retry_join":[
"consul-hashii1",
"consul-hashii2"
],
"encrypt": "sbfg+8FFJT0JHoIpTOsQMJgv5Xmnl/Th9rZt+YfXu8I=",
"ports": {
"grpc": 8502,
"http": 8500,
"https": 8501
},
"tls": {
"defaults": {
"ca_file": "/consul/config/certs/consul-agent-ca.pem",
"cert_file": "/consul/config/certs/hashii-server-consul-0.pem",
"key_file": "/consul/config/certs/hashii-server-consul-0-key.pem",
"verify_incoming": true,
"verify_outgoing": true
},
"internal_rpc": {
"verify_server_hostname": true
}
}
}client_hashii节点
{
"node_name": "consul-client_hashii",
"datacenter": "hashii",
"domain": "consul",
"data_dir": "/consul/data",
"ui_config": {
"enabled" : true
},
"retry_join":[
"consul-hashii1",
"consul-hashii2",
"consul-hashii3"
],
"encrypt": "sbfg+8FFJT0JHoIpTOsQMJgv5Xmnl/Th9rZt+YfXu8I=",
"tls": {
"defaults": {
"ca_file": "/consul/config/certs/consul-agent-ca.pem",
"verify_incoming": true,
"verify_outgoing": true
},
"internal_rpc": {
"verify_server_hostname": true
}
},
"addresses": {
"grpc" : "127.0.0.1"
},
"auto_encrypt": {
"tls": true
},
"ports": {
"http": 8500,
"https": 8501,
"grpc": 8502
},
"connect": {
"enabled": true
},
"performance": {
"raft_multiplier": 1
}
}docker-compose.yml
查看代码
version: '3.7'
services:
consul-server1:
image: hashicorp/consul:1.12.3
container_name: consul-server1
restart: always
volumes:
- ./server1.json:/consul/config/server1.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-server1:/consul/data
networks:
- consul
command: "agent -bootstrap-expect=3 -client=0.0.0.0 -log-file=/consul/logs/consul-01.log"
consul-server2:
image: hashicorp/consul:1.12.3
container_name: consul-server2
restart: always
volumes:
- ./server2.json:/consul/config/server2.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-server2:/consul/data
networks:
- consul
command: "agent -bootstrap-expect=3 -client=0.0.0.0 -log-file=/consul/logs/consul-02.log "
consul-server3:
image: hashicorp/consul:1.12.3
container_name: consul-server3
restart: always
volumes:
- ./server3.json:/consul/config/server3.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-server3:/consul/data
networks:
- consul
command: "agent -bootstrap-expect=3 -client=0.0.0.0 -log-file=/consul/logs/consul-03.log"
consul-client:
image: hashicorp/consul:1.12.3
container_name: consul-client
restart: always
volumes:
- ./client.json:/consul/config/client.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-client:/consul/data
networks:
- consul
command: "agent -client=0.0.0.0 -log-file=/consul/logs/client-01.log"
consul-hashii1:
image: hashicorp/consul:1.12.3
container_name: consul-hashii1
restart: always
volumes:
- ./server_hashii1.json:/consul/config/server_hashii1.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-hashii1:/consul/data
networks:
- consul
command: "agent -bootstrap-expect=3 -client=0.0.0.0 -log-file=/consul/logs/consul_hashii-01.log"
consul-hashii2:
image: hashicorp/consul:1.12.3
container_name: consul-hashii2
restart: always
volumes:
- ./server_hashii2.json:/consul/config/server_hashii1.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-hashii2:/consul/data
networks:
- consul
command: "agent -bootstrap-expect=3 -client=0.0.0.0 -log-file=/consul/logs/consul_hashii-02.log"
consul-hashii3:
image: hashicorp/consul:1.12.3
container_name: consul-hashii3
restart: always
volumes:
- ./server_hashii3.json:/consul/config/server_hashii1.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-hashii3:/consul/data
networks:
- consul
command: "agent -bootstrap-expect=3 -client=0.0.0.0 -log-file=/consul/logs/consul_hashii-03.log"
consul-client_hashii:
image: hashicorp/consul:1.12.3
container_name: consul-client_hashii
restart: always
ports:
- "8500:8500"
- "8600:8600/tcp"
- "8600:8600/udp"
volumes:
- ./client_hashii.json:/consul/config/client_hashii.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-client_hashii:/consul/data
networks:
- consul
command: "agent -client=0.0.0.0 -log-file=/consul/logs/client_hashii-01.log"
networks:
consul:
driver: bridge查看consul用户界面

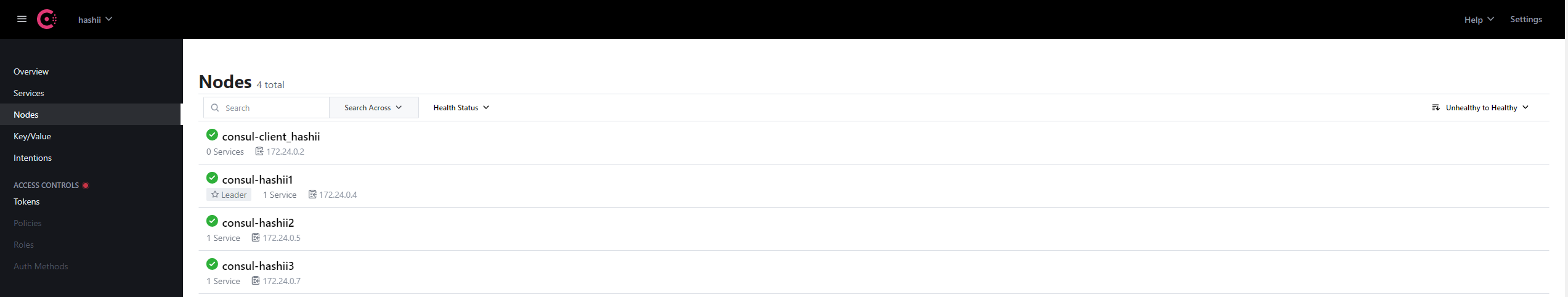
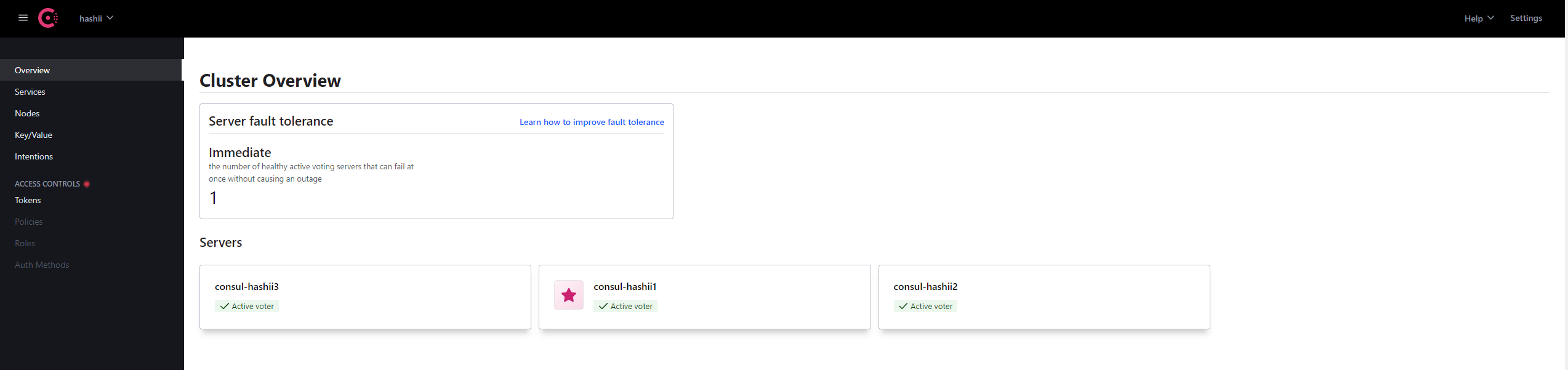
配置ACL
https://learn.hashicorp.com/tutorials/consul/access-control-setup
启用 ACL
consul-acl.json
{
"acl": {
"enabled": true,
"default_policy": "deny",
"down_policy": "extend-cache",
"enable_token_persistence": true
}
}查看consul leader
# docker exec consul-client consul operator raft list-peers
Node ID Address State Voter RaftProtocol
consul-server3 bb5cc200-3aac-d97a-ed6d-f24e9b3672fd 172.26.0.3:8300 leader true 3
consul-server2 61654d76-52db-74e4-8f1d-93677ec76b2e 172.26.0.8:8300 follower true 3
consul-server1 2ae325a8-99c8-a00b-786d-5b9a838d5d77 172.26.0.5:8300 follower true 3查看acl日志信息
查看代码
~# docker logs -f consul-server3
==> Starting Consul agent...
Version: '1.12.3'
Node ID: '90d71c3c-b2a2-bdbd-ede5-2168f8282347'
Node name: 'consul-server3'
Datacenter: 'zhongtai' (Segment: '<all>')
Server: true (Bootstrap: false)
Client Addr: [0.0.0.0] (HTTP: 8500, HTTPS: 8501, gRPC: 8502, DNS: 8600)
Cluster Addr: 172.27.0.8 (LAN: 8301, WAN: 8302)
Encrypt: Gossip: true, TLS-Outgoing: true, TLS-Incoming: true, Auto-Encrypt-TLS: true
==> Log data will now stream in as it occurs:
.....
2022-08-01T09:29:12.481Z [INFO] agent.server: New leader elected: payload=consul-server2
~# docker logs -f consul-server2
==> Starting Consul agent...
Version: '1.12.3'
Node ID: '2c248db0-29f6-116b-31b8-6aba2d860371'
Node name: 'consul-server2'
Datacenter: 'zhongtai' (Segment: '<all>')
Server: true (Bootstrap: false)
Client Addr: [0.0.0.0] (HTTP: 8500, HTTPS: 8501, gRPC: 8502, DNS: 8600)
Cluster Addr: 172.27.0.7 (LAN: 8301, WAN: 8302)
Encrypt: Gossip: true, TLS-Outgoing: true, TLS-Incoming: true, Auto-Encrypt-TLS: true
==> Log data will now stream in as it occurs:
....
2022-08-01T09:29:12.461Z [INFO] agent.server: initializing acls
2022-08-01T09:29:12.465Z [INFO] agent.server: Created ACL 'global-management' policy
2022-08-01T09:29:12.470Z [INFO] agent.server: Created ACL anonymous token from configuration
2022-08-01T09:29:12.470Z [INFO] agent.leader: started routine: routine="legacy ACL token upgrade"
2022-08-01T09:29:12.470Z [INFO] agent.leader: started routine: routine="acl token reaping"
....
2022-08-01T09:30:00.556Z [WARN] agent: Coordinate update blocked by ACLs: accessorID=00000000-0000-0000-0000-000000000002创建初始管理令牌
注意:SecretID是用于验证 API 和 CLI 请求的 ACL 令牌。
# docker exec consul-server1 consul acl bootstrap
AccessorID: e0f4b0fa-8a65-fee4-8781-4f50421035e2
SecretID: fdff7efd-7ded-76fb-7cf5-086a4ed19dda
Description: Bootstrap Token (Global Management)
Local: false
Create Time: 2022-08-01 10:11:19.019795176 +0000 UTC
Policies:
00000000-0000-0000-0000-000000000001 - global-management验证令牌
# docker exec consul-server1 consul members -token "fdff7efd-7ded-76fb-7cf5-086a4ed19dda"
Node Address Status Type Build Protocol DC Partition Segment
consul-server1 172.27.0.6:8301 alive server 1.12.3 2 zhongtai default <all>
consul-server2 172.27.0.7:8301 alive server 1.12.3 2 zhongtai default <all>
consul-server3 172.27.0.8:8301 alive server 1.12.3 2 zhongtai default <all>创建代理令牌策略
在创建新令牌之前,您需要创建其关联的策略。策略是一组可用于指定细粒度权限的规则。
注意,策略文件不应添加到 Consul 代理配置目录。
查看代码
~# docker exec -ti consul-server1 sh
/ # cat agent-policy.hcl
node_prefix "" {
policy = "write"
}
service_prefix "" {
policy = "read"
}
/ # export CONSUL_HTTP_TOKEN=fdff7efd-7ded-76fb-7cf5-086a4ed19dda
/ # consul acl policy create -name "agent-token" -description "Agent Token Policy" -rules @agent-policy.hcl
ID: 7e9ba2ed-1e92-8035-5dcb-df2ffd09db27
Name: agent-token
Description: Agent Token Policy
Datacenters:
Rules:
node_prefix "" {
policy = "write"
}
service_prefix "" {
policy = "read"
}
/ # 创建 Consul 代理令牌
注意:接上一步,在docker容器里执行
查看代码
/ # consul acl token create -description "Agent Token" -policy-name "agent-token"
AccessorID: d9a0ff38-50ff-c4b1-33d3-bde49501bcde
SecretID: 6b43aa4e-8b89-1a57-fa11-88e60bf7365c
Description: Agent Token
Local: false
Create Time: 2022-08-01 10:21:13.060318298 +0000 UTC
Policies:
7e9ba2ed-1e92-8035-5dcb-df2ffd09db27 - agent-token将代理令牌添加到所有 Consul 服务器
# cat consul-acl.json
{
"primary_datacenter": "zhongtai",
"acl": {
"enabled": true,
"default_policy": "deny",
"down_policy": "extend-cache",
"enable_token_persistence": true,
"tokens": {
"agent": "6b43aa4e-8b89-1a57-fa11-88e60bf7365c"
}
}
}附加 ACL 配置
查看consul节点
查看代码
# docker exec -it consul-server1 sh
/ # consul members
/ # CONSUL_HTTP_TOKEN=6b43aa4e-8b89-1a57-fa11-88e60bf7365c consul members
Node Address Status Type Build Protocol DC Partition Segment
consul-server1 192.168.32.6:8301 alive server 1.12.3 2 zhongtai default <all>
consul-server2 192.168.32.2:8301 alive server 1.12.3 2 zhongtai default <all>
consul-server3 192.168.32.8:8301 alive server 1.12.3 2 zhongtai default <all>
consul-client 192.168.32.7:8301 alive client 1.12.3 2 zhongtai default <default>
/ # 查看consul UI
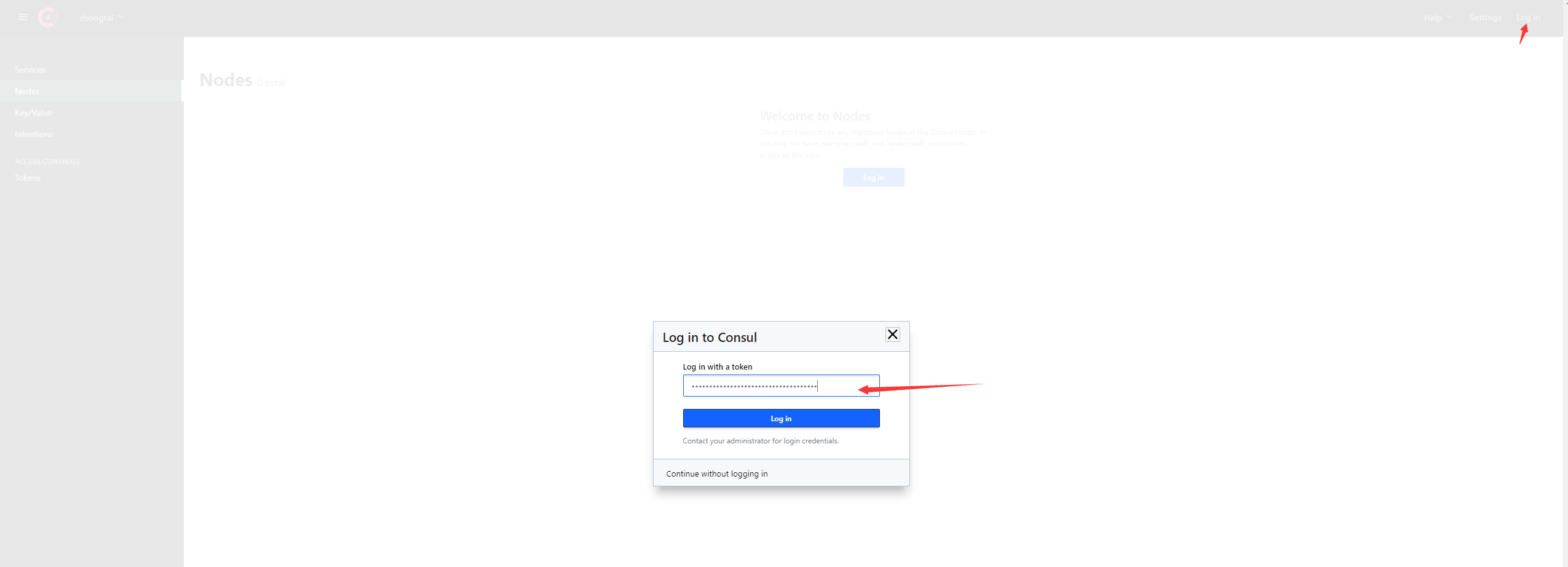
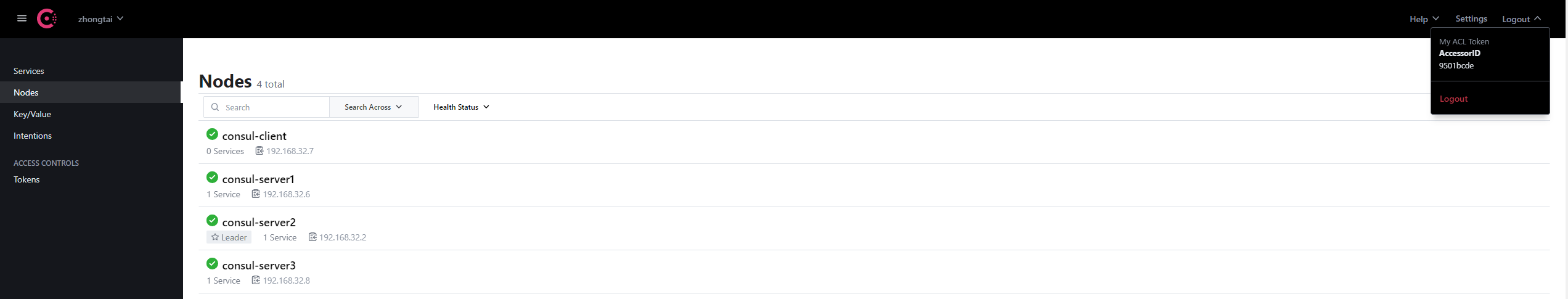
docker-compose.yml样例
查看代码
version: '3.7'
services:
consul-server1:
image: hashicorp/consul:1.12.3
container_name: consul-server1
restart: always
volumes:
- ./server1.json:/consul/config/server1.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-server1:/consul/data
- ./consul-acl.json:/consul/config/consul-acl.json:ro
networks:
- consul
command: "agent -bootstrap-expect=3 -client=0.0.0.0 -log-json -log-file=/consul/logs/consul-01.log"
consul-server2:
image: hashicorp/consul:1.12.3
container_name: consul-server2
restart: always
volumes:
- ./server2.json:/consul/config/server2.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-server2:/consul/data
- ./consul-acl.json:/consul/config/consul-acl.json:ro
networks:
- consul
command: "agent -bootstrap-expect=3 -client=0.0.0.0 -log-json -log-file=/consul/logs/consul-02.log "
consul-server3:
image: hashicorp/consul:1.12.3
container_name: consul-server3
restart: always
volumes:
- ./server3.json:/consul/config/server3.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-server3:/consul/data
- ./consul-acl.json:/consul/config/consul-acl.json:ro
networks:
- consul
command: "agent -bootstrap-expect=3 -client=0.0.0.0 -log-json -log-file=/consul/logs/consul-03.log"
consul-client:
image: hashicorp/consul:1.12.3
container_name: consul-client
restart: always
ports:
- "8500:8500"
- "8600:8600/tcp"
- "8600:8600/udp"
volumes:
- ./client.json:/consul/config/client.json:ro
- ./certs/:/consul/config/certs/:ro
- ./logs/:/consul/logs/
- ./data/consul-client:/consul/data
- ./consul-acl.json:/consul/config/consul-acl.json:ro
networks:
- consul
command: "agent -client=0.0.0.0 -log-json -log-file=/consul/logs/client-01.log"
networks:
consul:
driver: bridge

