day11.3
day11.3
Google Authenticator介绍
通常我们直接通过ssh输入密码连接服务器,但这样很容易出现暴力破解情况,所以我们可以结合google的动态认证
+ssh密码,这样能够大大的提升登陆的安全。简单来说,就是当用户通过ssh登陆系统时,先输入google的随机验证码,然后在输入服务器的ssh密码
Google Authenticator安装部署
# 1.安装依赖
[root@m01 ~]# yum -y install pam-devel libpng-devel autoconf automake libtool
# 2.下载Google apm插件
[root@m01 ~]# wget http://test.driverzeng.com/other/1.04.tar.gz
# 3.解压插件
[root@m01 ~]# tar xf 1.04.tar.gz
# 4.构建代码
## 进入解压开的目录
[root@m01 ~]# cd google-authenticator-libpam-1.04/
[root@m01 google-authenticator-libpam-1.04]# ll
total 52
-rwxrwxr-x 1 root root 605 Aug 16 2017 bootstrap.sh
drwxrwxr-x 2 root root 24 Aug 16 2017 build
-rw-rw-r-- 1 root root 1932 Aug 16 2017 configure.ac
drwxrwxr-x 2 root root 46 Aug 16 2017 contrib
-rw-rw-r-- 1 root root 1452 Aug 16 2017 CONTRIBUTING.md
drwxrwxr-x 2 root root 20 Aug 16 2017 examples
-rw-rw-r-- 1 root root 2622 Aug 16 2017 FILEFORMAT
-rw-rw-r-- 1 root root 11358 Aug 16 2017 LICENSE
-rw-rw-r-- 1 root root 2231 Aug 16 2017 Makefile.am
drwxrwxr-x 2 root root 140 Aug 16 2017 man
-rw-rw-r-- 1 root root 7155 Aug 16 2017 README.md
drwxrwxr-x 2 root root 158 Aug 16 2017 src
drwxrwxr-x 2 root root 49 Aug 16 2017 tests
-rw-rw-r-- 1 root root 9423 Aug 16 2017 totp.html
drwxrwxr-x 2 root root 41 Aug 16 2017 utc-time
## 执行bootstrap构建
[root@m01 google-authenticator-libpam-1.04]# ./bootstrap.sh
# 5.生成
[root@m01 google-authenticator-libpam-1.04]# ./configure
# 6.编译 && 安装
[root@m01 google-authenticator-libpam-1.04]# make && make install
# 7.检查插件是否安装
[root@m01 google-authenticator-libpam-1.04]# ll /usr/local/lib/security/
-rwxr-xr-x 1 root root 1021 May 25 09:15 pam_google_authenticator.la
-rwxr-xr-x 1 root root 133552 May 25 09:15 pam_google_authenticator.so
# 8.将安装好的插件,拷贝到系统库文件目录中
[root@m01 ~]# cp /usr/local/lib/security/pam_google_authenticator.so /usr/lib64/security/
# 9.生成初始google认证识别码
[root@m01 ~]# google-authenticator
# 以下选项输入
Do you want authentication tokens to be time-based (y/n) y
Do you want me to update your "/root/.google_authenticator" file? (y/n) y
your chances to notice or even prevent man-in-the-middle attacks (y/n) y
Do you want to do so? (y/n) y
Do you want to enable rate-limiting? (y/n) y
# 生成二维码后,扫描二维码
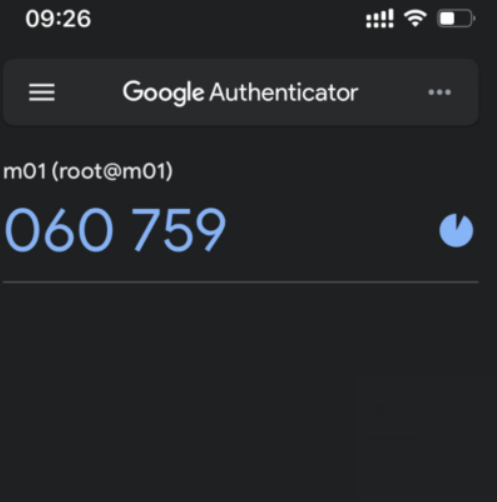
# 生成动态令牌
# 长按可以删除,修改
将Google 2FA接入SSH
# 1.修改ssh认证配置
[root@m01 ~]# vim /etc/pam.d/sshd
auth required pam_google_authenticator.so(在最上面一行插入)
# 2.修改SSH配置文件,关联Google认证
[root@m01 ~]# vim /etc/ssh/sshd_config
69 ChallengeResponseAuthentication yes
# 3.重启sshd服务
[root@m01 ~]# systemctl restart sshd
# 修改登录的配置
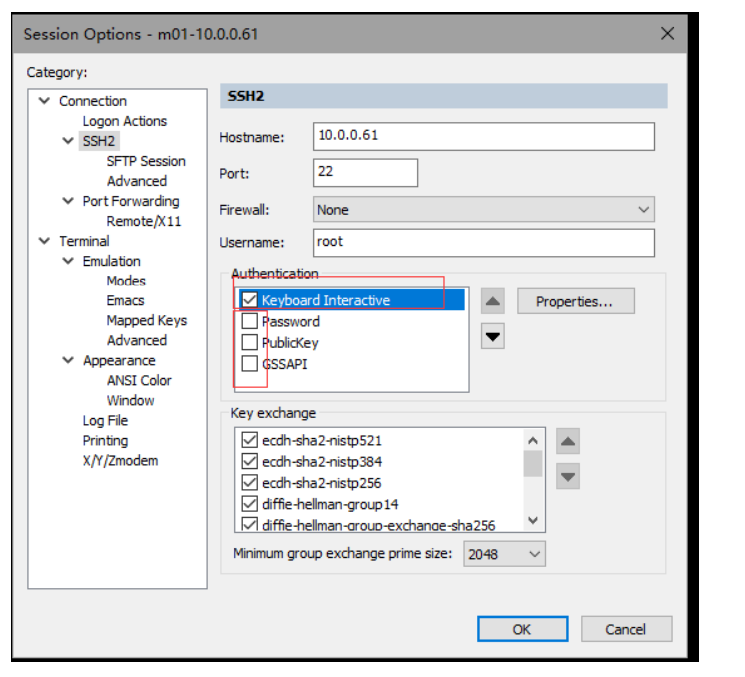
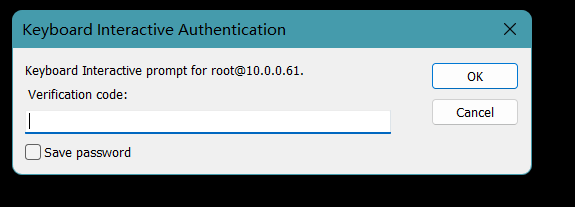
# 登录
1.输入动态密码
2.输入roo密码
使用Python脚本登录CRT
# 修改以下配置
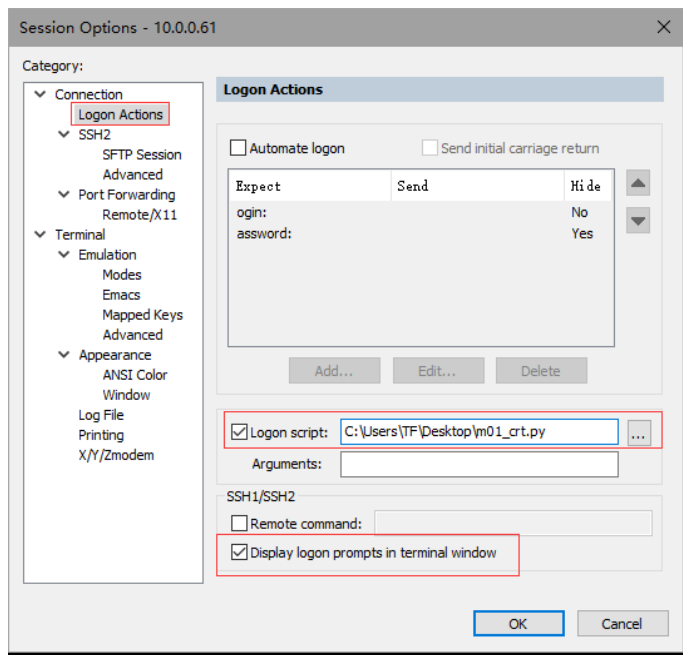
# 修改谷歌生成码与密码即可
'脚本'
# $language = "python"
# $interface = "1.0"
import hmac, base64, struct, hashlib, time,re
#获取当前脚本所在的tab对象
objTab = crt.GetScriptTab()
#objTab = crt.GetActiveTab()
objTab.Screen.Synchronous = True
objTab.Screen.IgnoreEscape = True
#获取终端名字
tabName=objTab.Caption
reIp=r'\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}'
hostIp=re.findall(reIp,tabName)[0]
secretKey="Your new secret key is:"
def calGoogleCode(secretKey):
#secreKey 需要是8的倍数
t = int(time.time())//30
lens = len(secretKey)
lenx = 8 - (lens % 4 if lens % 4 else 4)
secretKey += lenx * '='
key = base64.b32decode(secretKey)
msg = struct.pack(">Q", t)
googleCode = hmac.new(key, msg, hashlib.sha1).digest()
o = ord(str(googleCode[19])) & 15
googleCode = str((struct.unpack(">I", googleCode[o:o+4])[0] & 0x7fffffff) % 1000000)
return googleCode.zfill(6)
def get_string(objTab,szStart,szPrompt):
objTab.Screen.WaitForStrings(szStart)
return objTab.Screen.ReadString(szPrompt)
def send_string(objTab,waitString,strings,selfSleepTime=20):
objTab.Screen.WaitForStrings(waitString)
time.sleep(0.0001)
for i in strings:
crt.Sleep(5)
objTab.Screen.Send(i)
# time.sleep(0.0001)
objTab.Screen.WaitForStrings(strings)
if strings[-1] != '\r':
objTab.Screen.Send('\r')
#msg(objTab.Screen.ReadString('[ q ]'))
# time.sleep(0.0001)
def send_pass(objTab,waitString,strings):
objTab.Screen.WaitForStrings(waitString)
for i in strings:
crt.Sleep(5)
objTab.Screen.Send(i)
if strings[-1] != '\r':
objTab.Screen.Send('\r')
time.sleep(0.01)
#发送2fa
send_pass(objTab,'Verification code:',calGoogleCode(secretKey))
## 发送密码
send_pass(objTab,'Password: ','1') # '1' 是服务器的密码
#发送登录ip
send_string(objTab,'Opt> ',hostIp)
#objTab.Screen.WaitForStrings("[MFA auth]: ","")
#if objTab.Screen.WaitForStrings("Opt> ",1):
# #发送登录ip 克隆会话,不需要二次验证码
# send_string(objTab,'Opt> ',hostIp)
#else:
# #发送2fa
# send_pass(objTab,'[MFA auth]: ',calGoogleCode(secretKey))
# #发送登录ip
# send_string(objTab,'Opt> ',hostIp)





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了