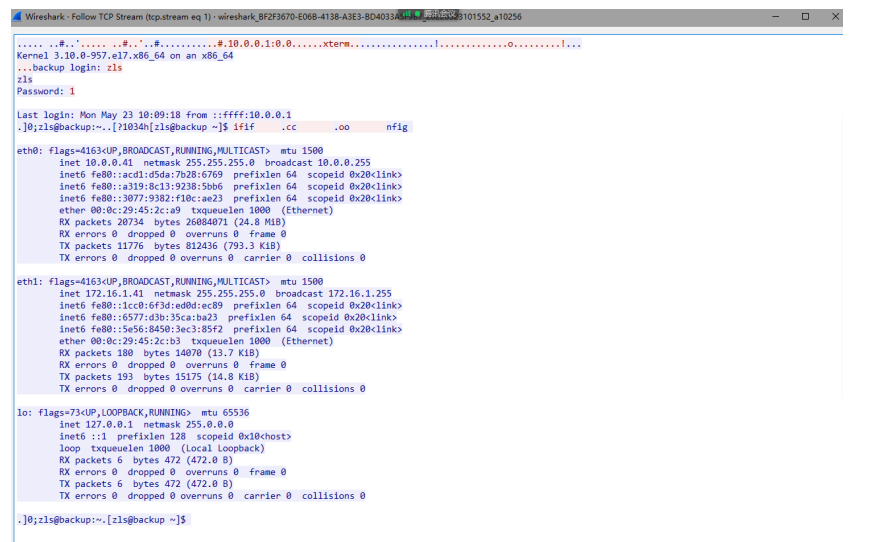
day11.2
day11.2
SSH远程管理
# linux
-ssh 端口:22 加密传输
-telent 端口:23 明文传输(不安全)
# windows
-rdp 端口:3389
抓包演示
ssh数据加密传输

telent明文传输
# 服务与协议端口
ftp 21
ssh 22
telent 23
dns 53
mysql 3306
http 80
HTTPS 443
rsync 873
ssh相关命令及选项
# 选项
-i:指定公钥位置
-p:指定端口
'注意:不加用户@,默认使用当前登录用户'
# ssh远程连接linux服务器
# 不连接服务器,直接执行命令
ssh root@10.0.0.61 'ls -l'
scp相关命令及选项
# scp 远程拷贝数据
-r:递归
-p:拷贝时保存属性
-P:指定端口
结论
1.scp通过ssh协议加密方式进行文件或目录的拷贝
2.scp连接时用户作为 为拷贝文件或目录的权限
3.scp支持数据推送和拉取,每次都是全量拷贝,效率较低
ssh免密连接
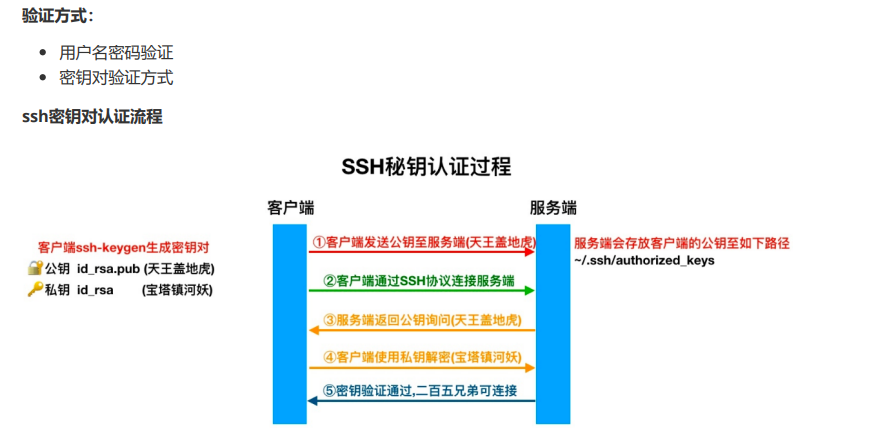
# 1.生成密钥对
[root@backup ~]# ssh-keygen
Generating public/private rsa key pair.
# 将密钥保存到文件中,可以指定其它路径(直接回车)
Enter file in which to save the key (/root/.ssh/id_rsa):
Created directory '/root/.ssh'.
# 给密钥对设置密码,不需要设置(直接回车)
Enter passphrase (empty for no passphrase):
# 重复设置密码(直接回车)
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:ZfjrCipf7/RtUmqV48v/BjAJhgsPvpu5eNM6oJnE3zk root@backup
The key's randomart image is:
+---[RSA 2048]----+
| . |
| o ..o |
| . +.oo. . |
| . o+ + |
| . .S . + |
| o . . .= . |
| . = oo*. .= . . |
| = .+E+.o+oo .|
| o+.oB+ooo+o.o.|
+----[SHA256]-----+
# 2.查看生成的密钥对
[root@backup ~]# ll /root/.ssh/
total 8
-rw------- 1 root root 1675 May 23 13:57 id_rsa
-rw-r--r-- 1 root root 393 May 23 13:57 id_rsa.pub
# 3.发送公钥
[root@m01 ~]# ssh-copy-id -i ~/.ssh/id_rsa.pub root@10.0.0.41
# 4. .ssh目录中的know_host作用
[root@m01 ~]# cat ~/.ssh/known_hosts
172.16.1.7 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBI+swA7qDX4fO/E8m+udyuq1RQQq0LO4iA+49P79pc1t4fGflSVJVueH1eU/UAoOcq9vFZdGIJKuEYWFVoEtXN4=
10.0.0.41 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBI+swA7qDX4fO/E8m+udyuq1RQQq0LO4iA+49P79pc1t4fGflSVJVueH1eU/UAoOcq9vFZdGIJKuEYWFVoEtXN4=
'记录过连接过的服务器,连接过上面会有连接过的ip,如果没有连接过,连接是则需要输入yes'
拍错流程
# 生成密钥对命令:ssh-keygen
1.在当前用户下创建了一个隐藏目录 .ssh mkdir ~/.ssh
2.将密钥对存放目录 .ssh 授权为 700 chmod 700 ~/.ssh
3.将公钥内容写入 ~/.ssh/id_rsa.pub 文件中
4.将私钥写入 ~/.ssh/id_rsa 文件中
5.将私钥授权为 600 chmod 600 ~/.ssh/id_rsa
# 发送公钥命令:ssh-copy-id
[root@m01 ~]# ssh-copy-id -i ~/.ssh/id_rsa.pub root@10.0.0.41
输入yes
输入密码:1
1.在远端的指定用户的家目录下创建了一个隐藏目录 .ssh
ssh root@10.0.0.41 'mkdir ~/.ssh'
2.将密钥对存放目录 .ssh 授权为 700
ssh root@10.0.0.41 'chmod 700 ~/.ssh'
3.在远端~/.ssh 目录下创建文件 authorized_keys
/root/.ssh/authorized_keys
4.将 authorized_keys 文件授权为600
ssh root@10.0.0.41 'chmod 600 /root/.ssh/authorized_keys'
# 将公钥内容,保存到 /root/.ssh/authorized_keys 文件中
[root@web01 ~]# cat /root/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDGLqHqOuG5q3S4lcBsp7e6foin6fKza5RMhll67j09C83okjSy1MDxs6b27gyY4eYG2nOs5YV/5oylbHq8gyIBUv/3wkhHCAPDvb/NPDVNCqDCHOm6L4nWqOcSptgj+dke++OWGqoPTrF6PS2l3IXs1yzYpvd1IarObGbO6ovIEuNu/rR6xpLco2ywqqOohFhMy/76RmRNdxXnc43hShVwVD5fng1baoaJNlYzrX0sQi8SZ1OxBs3sIPakjfR07dbD93LW5FOuiSlTTOdrE5fKtgx7i8eEOvma0oGyzQnhcAkot5/jd+V4SeCx9fbrVIlVglR5q3Qp5Rla5VfZWXex root@m01
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDb9nqFzkxq02pc3BgZir75+iHLEAT2fvpL4uQbuMfNWB2+E/VA4aullA3wtXUFzHEX9YbYTLzKElXPef+w7mLWftT7TW8RBFj60ALM/vPWBJn1sCP4kO/dEqvPylpf3KB+1JAhvjZRfdDQFlsZ/LO0tsixBlmbU6q5ooNEG0EQUQwyBkFgOhAZtt8hYgg710Y0mvd3R58wI9shW5EsPqGOy3I/vlVxt0jwpL20KY2T8g3FSHOvDg2PFuUzJ9L4ircuLtmoFbzgX7Wb61n7Yji8EWppnhgiBPQemSiaVBWlOt/ANYdX2KRZuFNvhORiHpTXnf0IQgjzMBPnIrEnikWn root@web02
'保存进去的,下次登录就是免交互登录'
免密使用场景
# 批量查看服务器信息
编写脚本
[root@web01 ~]# vim check_host.sh
#!/bin/bash
[ $# -ne 1 ] && echo "请输入执行的命令" && exit 1
for i in 7 8
do
echo "#########172.16.1.$i#####"
ssh root@172.16.1.$i "$1"
done
# 跳板机
#!/bin/bash
#jumpserver
lb01=10.0.0.5
lb02=10.0.0.6
web01=10.0.0.7
web02=10.0.0.8
web03=10.0.0.9
nfs=10.0.0.31
backup=10.0.0.41
db01=10.0.0.51
m01=10.0.0.61
zabbix=10.0.0.71
menu(){
cat <<-EOF
+-------------------------+
| 1) lb01 |
| 2) lb02 |
| 3) web01 |
| 4) web02 |
| 5) web03 |
| 6) nfs |
| 7) backup |
| 8) db01 |
| 9) m01 |
| 10) zabbix |
| h) help |
+-------------------------+
EOF
}
#菜单函数
menu
#连接函数
connect(){
ping -c 1 -w 1 $1 &>/dev/null
if [ $? -eq 0 ];then
ssh root@$1
else
echo -e "\033[5;4;40;31m 别连了,我的哥,$2:$1机器都没开!!!\033[0m"
fi
}
#控制不让输入ctrl+c,z
trap "" HUP INT TSTP
while true
do
read -p "请输入要连接的主机编号:" num
case $num in
1|lb01)
connect $lb01 lb01
;;
2|lb02)
connect $lb02 lb02
;;
3|web01)
connect $web01 web01
;;
4|web02)
connect $web02 web02
;;
5|web03)
connect $web03 web03
;;
6|nfs)
connect $nfs nfs
;;
7|backup)
connect $backup backup
;;
8|db01)
connect $db01 db01
;;
9|m01)
connect $m01 m01
;;
10|zabbix)
connect $zabbix zabbix
;;
h|help)
clear
menu
;;
close)
break
;;
esac
done
ssh安全优化
# ssh配置文件
vim /etc/ssh/sshd_config
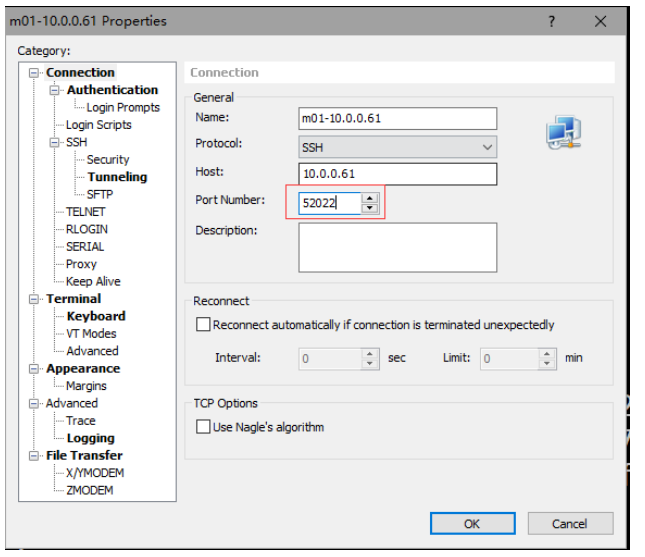
Port 52022 # 变更SSH服务远程连接端口
PermitRootLogin no # 禁止root用户直接远程登录
PasswordAuthentication no # 禁止使用密码直接远程登录
UseDNS no # 禁止ssh进行dns反向解析,影响ssh连接效率参数
GSSAPIAuthentication no # 禁止GSS认证,减少连接时产生的延迟
# 重启服务
[root@m01 ~]# systemctl restart sshd
# 解决方案
优化完ssh,发现以下问题
1.没有普通用户
useradd wc (无法创建,进入单用户模式)
2.windows上密钥没有推送
- 使用windows的命令执行 ssh-keygen
- 使用xshell
使用xshell生成密钥对
密码可写可不写
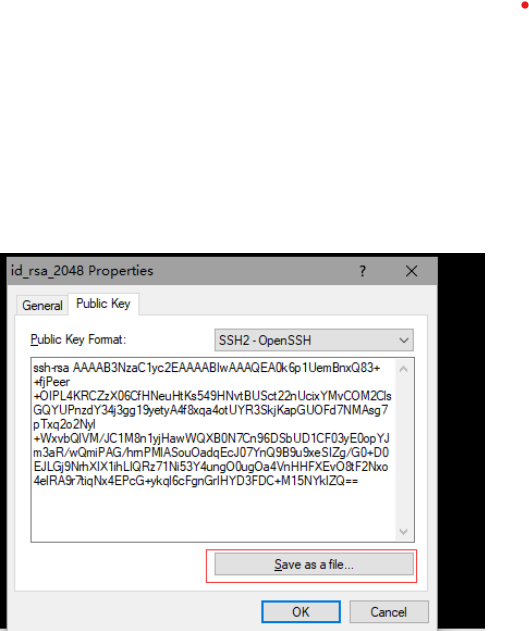
生成密钥对
将密钥复制进创建的目录下
[zls@m01 ~]$ mkdir .ssh
[zls@m01 ~]$ chmod 700 .ssh/
[zls@m01 ~]$ vim .ssh/authorized_keys
ssh-rsa
AAAAB3NzaC1yc2EAAAABIwAAAQEAuNorYRb3u0gM8RvxeZqGZJjptceVYpZz3ADLzTpF92DZlmGjEScnbmEfZaIVhER
F0nTvd79aixEP97V2l/B7p30b4+oaFugCR0ZDJRmypZUIKXnNYwbDjwT7k/4/V3DTYjS+0OkNLbKghlDDX0ntOoClGb
y2zV87draCqOQ6F4AAHWcrZi72gflKEShRKULKOGjcr3ZzDZfyKH6IxWLxa3EJO3v/tUFOatqDDj2j+aNswgbEDf0iC
Ynaw5h+SiTkVV6zY44TEEM+h9aVXjY1ufyAAePRDcuOnHBB1VzE38TMLEYl94VEUartDwE2TMnVOk5MhRYm4Q09zrPj
VM0J3w==
[zls@m01 ~]$ chmod 600 .ssh/authorized_keys
修改登录端口
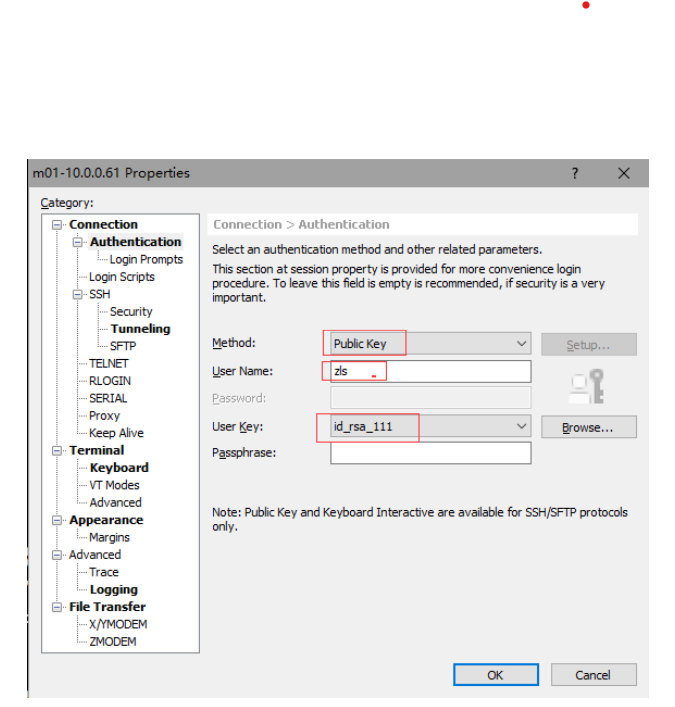
免交互生成密钥对命令
[root@m01 ~]# ssh-keygen -t rsa -P '' -f ~/.ssh/id_rsa
# 选项
-t:指定加密类型
-p:空密码
-f:密钥生成位置
免交互推送公钥
# [root@m01 ~]# cat /root/1.txt
172.16.1.8
172.16.1.7
'先生成一个存放ip的文件'
[root@m01 ~]# vim lob.sh
ls -l ~/.ssh/id_rsa &>/dev/null || ssh-keygen -t rsa -P '' -f ~/.ssh/id_rsa &>/dev/null
ssh-copy-id -i ~/.ssh/id_rsa.pub root@172.16.1.8
ssh-copy-id -i ~/.ssh/id_rsa.pub root@172.16.1.7
for ip in `cat /root/1.txt`;do
ssh-copy-id -i ~/.ssh/id_rsa.pub root@${ip}
done
解决密码交互问题
# 使用expect解决
[root@m01 ~]# yum install -y expect
[root@m01 ~]# vim ec.sh
set ip 172.16.1.61
set pass 1
set timeout 30
spawn ssh-keygen
expect {
"id_rsa):" {send "\r"; exp_continue}
"passphrase):" {send "\r"; exp_continue}
"again:" {send "\r"}
}
expect eof
spawn ssh-copy-id -i /root/.ssh/id_rsa.pub root@$ip
expect {
"(yes/no)" {send "yes\r"; exp_continue}
"password:" {send "$pass\r"}
expect eof
#!/bin/bash
. /etc/init.d/functions
ls -l ~/.ssh/id_rsa &>/dev/null || ssh-keygen -t rsa -P '' -f ~/.ssh/id_rsa &>/dev/null
for n in `cat /root/1.txt`;do
pass=`echo $n|awk -F ':' '{print $2}'`
ip=`echo $n|awk -F ':' '{print $1}'`
sshpass -p $pass ssh-copy-id -o 'StrictHostKeyChecking no' -i ~/.ssh/id_rsa.pub root@$ip
&>/dev/null
if [ $? -eq 0 ];then
action "$ip send public key " /bin/true
else
action "$ip send public key " /bin/false
fi
done
# 使用sshpass解决
[root@m01 ~]# yum install -y sshpass
# ssh不需要输入yes的选项
#!/bin/bash
ls -l ~/.ssh/id_rsa &>/dev/null || ssh-keygen -t rsa -P '' -f ~/.ssh/id_rsa &>/dev/null
for n in `cat /root/1.txt`;do
shpass -p 1 ssh-copy-id -o 'StrictHostKeyChecking no' -i ~/.ssh/id_rsa.pub root@$ip
done





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了