[网鼎杯2020青龙组] you_raise_me_up
解题过程
1. 题目给的代码如下:
1 #!/usr/bin/env python 2 # -*- coding: utf-8 -*- 3 from Crypto.Util.number import * 4 import random 5 6 n = 2 ** 512 7 m = random.randint(2, n-1) | 1 8 c = pow(m, bytes_to_long(flag), n) 9 print 'm = ' + str(m) 10 print 'c = ' + str(c) 11 12 # m = 391190709124527428959489662565274039318305952172936859403855079581402770986890308469084735451207885386318986881041563704825943945069343345307381099559075 13 # c = 6665851394203214245856789450723658632520816791621796775909766895233000234023642878786025644953797995373211308485605397024123180085924117610802485972584499
读完代码可以得到一个表达式:
c = mbytes_to_long(flag) mod n
2. 那么现在已知c, m, n求离散对数:
bytes_to_long(flag) = log(m mod n) (c mod n)
sage中的discrete_log可以帮我们计算出结果[1],使用方法为:
bytes_to_long(flag) = discrete_log((c mod n), (m mod n)) 或
bytes_to_long(flag) = discrete_log(c, (m mod n))
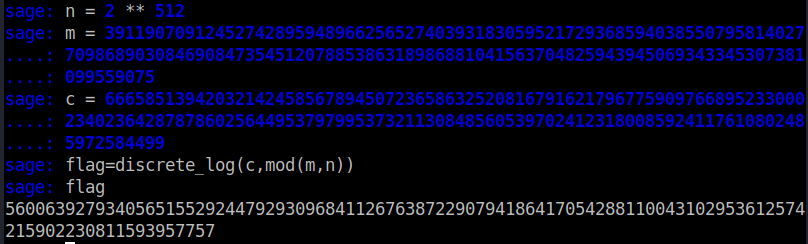
3. 将得到的数值long_to_bytes(flag)即可得到:flag{5f95ca93-1594-762d-ed0b-a9139692cb4a}
1 from Crypto.Util.number import * 2 flag = 56006392793405651552924479293096841126763872290794186417054288110043102953612574215902230811593957757 3 print long_to_bytes(flag)


