使用Scapy回放报文pcap
一、准备环境:
Ubuntu + python2.7
sudo apt-get install python-scapy
二、准备报文:
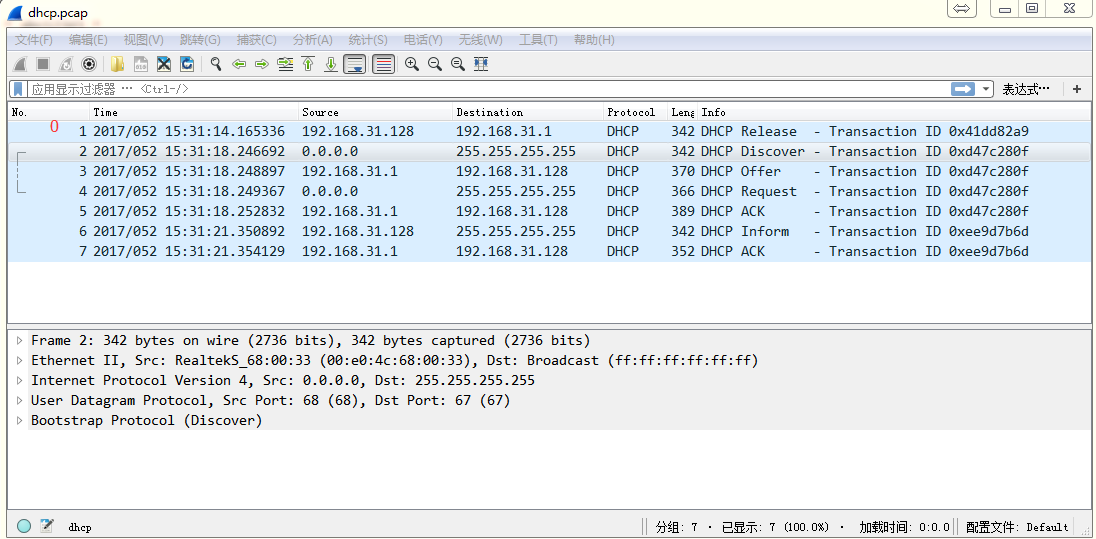
先抓取一些报文,本实验使用的是DHCP的报文。
文件-导出特定分组-选择保存为*.pcap文件,把pcap文件拷贝到Ubuntu电脑上。
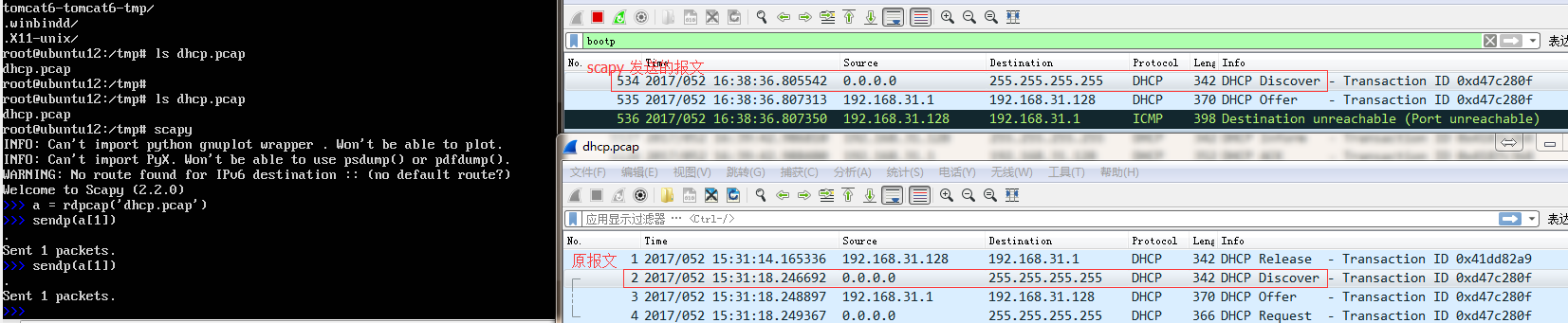
三、启动scapy 并发送dhcp.pcap抓包的第二个报文DHCP Discover
sudo scapy
>>>a = rdpcap('dhcp.pcap')
>>>sendp(a[1])
用wireshark抓包:
四、查看报文信息:
>>>s = a[1]
>>>s.show()
###[ Ethernet ]###
dst= ff:ff:ff:ff:ff:ff
src= 00:e0:4c:68:00:33
type= 0x800
###[ IP ]###
version= 4L
ihl= 5L
tos= 0x0
len= 328
id= 15294
flags=
frag= 0L
ttl= 64
proto= udp
chksum= 0x3de8
src= 0.0.0.0
dst= 255.255.255.255
###[ Ethernet ]###
dst= ff:ff:ff:ff:ff:ff
src= 00:e0:4c:68:00:33
type= 0x800
###[ IP ]###
version= 4L
ihl= 5L
tos= 0x0
len= 328
id= 15294
flags=
frag= 0L
ttl= 64
proto= udp
chksum= 0x3de8
src= 0.0.0.0
dst= 255.255.255.255
>>> s[DHCP]
<DHCP options=[message-type=discover client_id='\x01\x00\xe0Lh\x003' requested_addr=192.168.31.128 hostname='waston-DELL990' vendor_class_id='MSFT 5.0' param_req_list='\x01\x0f\x03\x06,./\x1f!y\xf9+' end pad] |>
<DHCP options=[message-type=discover client_id='\x01\x00\xe0Lh\x003' requested_addr=192.168.31.128 hostname='waston-DELL990' vendor_class_id='MSFT 5.0' param_req_list='\x01\x0f\x03\x06,./\x1f!y\xf9+' end pad] |>
可以通过 s[DCHP] 访问到 DHCP 层(s[Ether]代表二层、s[IP]代表IP层、
s[UDP]代表UDP层等等)。
s[UDP]代表UDP层等等)。
五、修改报文:
>>> s=a[1]
>>> s[DHCP].options
[('message-type', 1), ('client_id', '\x01\x00\xe0Lh\x003'), ('requested_addr', '192.168.31.128'), ('hostname', 'waston-DELL990'), ('vendor_class_id', 'MSFT 5.0'), ('param_req_list', '\x01\x0f\x03\x06,./\x1f!y\xf9+'), 'end', 'pad']
>>> s[DHCP].options.remove(('hostname', 'waston-DELL990'))
>>> s[DHCP].options
[('message-type', 1), ('client_id', '\x01\x00\xe0Lh\x003'), ('requested_addr', '192.168.31.128'), ('vendor_class_id', 'MSFT 5.0'), ('param_req_list', '\x01\x0f\x03\x06,./\x1f!y\xf9+'), 'end', 'pad']
修改报文后需要重新计算报文长度及校验和
>>> s[IP].len=None
>>> s[IP].checksum=None
>>> s[UDP].checksum=None
>>> s[UDP].len=None
>>> sendp(s)
>>> help(s[DHCP].options.insert)
Help on built-in function insert:
insert(...)
L.insert(index, object) -- insert object before index
>>> s[DHCP].options.insert(3,('hostname', 'waston-DELL9902'))
>>> s[DHCP].options
[('message-type', 1), ('client_id', '\x01\x00\xe0Lh\x003'), ('requested_addr', '192.168.31.128'), ('hostname', 'waston-DELL9902'), ('vendor_class_id', 'MSFT 5.0'), ('param_req_list', '\x01\x0f\x03\x06,./\x1f!y\xf9+'), 'end', 'pad']
>>> sendp(s)
六、构造报文:
>>> s
<Ether dst=ff:ff:ff:ff:ff:ff src=00:e0:4c:68:00:33 type=0x800 |<IP version=4L ihl=5L tos=0x0 len=None id=15294 flags= frag=0L ttl=64 proto=udp chksum=0x3de8 src=0.0.0.0 dst=255.255.255.255 options=[] |<UDP sport=bootpc dport=bootps len=None chksum=0x2bb4 |<BOOTP op=BOOTREQUEST htype=1 hlen=6 hops=0 xid=3564906511L secs=0 flags= ciaddr=0.0.0.0 yiaddr=0.0.0.0 siaddr=0.0.0.0 giaddr=0.0.0.0 chaddr='\x00\xe0Lh\x003\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00' sname='\x00\x00\x00\x00\x00\x00\x00' file='\x00\x00\x00\x00\x00' options='c\x82Sc' |<DHCP options=[message-type=discover client_id='\x01\x00\xe0Lh\x003' requested_addr=192.168.31.128 hostname='waston-DELL9902' vendor_class_id='MSFT 5.0' param_req_list='\x01\x0f\x03\x06,./\x1f!y\xf9+' end pad] |>>>>>
>>>
pkt = Ether()/IP()/UDP()/BOOTP()/DHCP(options=[('message-type','discover')])/DHCP(options=['end'])
sendp(pkt)
pkt[Ether].src='00:e0:4c:68:00:36'
pkt[Ether].dst='ff:ff:ff:ff:ff:ff'
pkt[IP].src='0.0.0.0'
pkt[IP].dst='255.255.255.255'
sendp(pkt)
>>> pkt
<Ether dst=ff:ff:ff:ff:ff:ff src=00:e0:4c:68:00:36 type=0x800 |<IP frag=0 proto=udp src=0.0.0.0 dst=255.255.255.255 |<UDP sport=bootps dport=bootpc |<BOOTP options='c\x82Sc' |<DHCP options=[message-type='discover'] |<DHCP options=[end] |>>>>>>
其它:
ipython中使用scapy
ipython
[1]:from scapy.all import *
[2]:a=rdpcap('dhcp.pacp')
[3]:s=a[1]
[4]:sendp(s)

 浙公网安备 33010602011771号
浙公网安备 33010602011771号