[Tomcat源码分析] Eclipse中搭建Apache Tomcat源码调试环境
网上很多文章都推荐使用Ant下载编译,但本地实践中屡屡失败,无法下载。
后来参考 https://blog.csdn.net/xiongyouqiang/article/details/78941077 总算把调试环境搭建完成。
以下文章几乎完全copy上述网址,但稍作延展。
下载源码
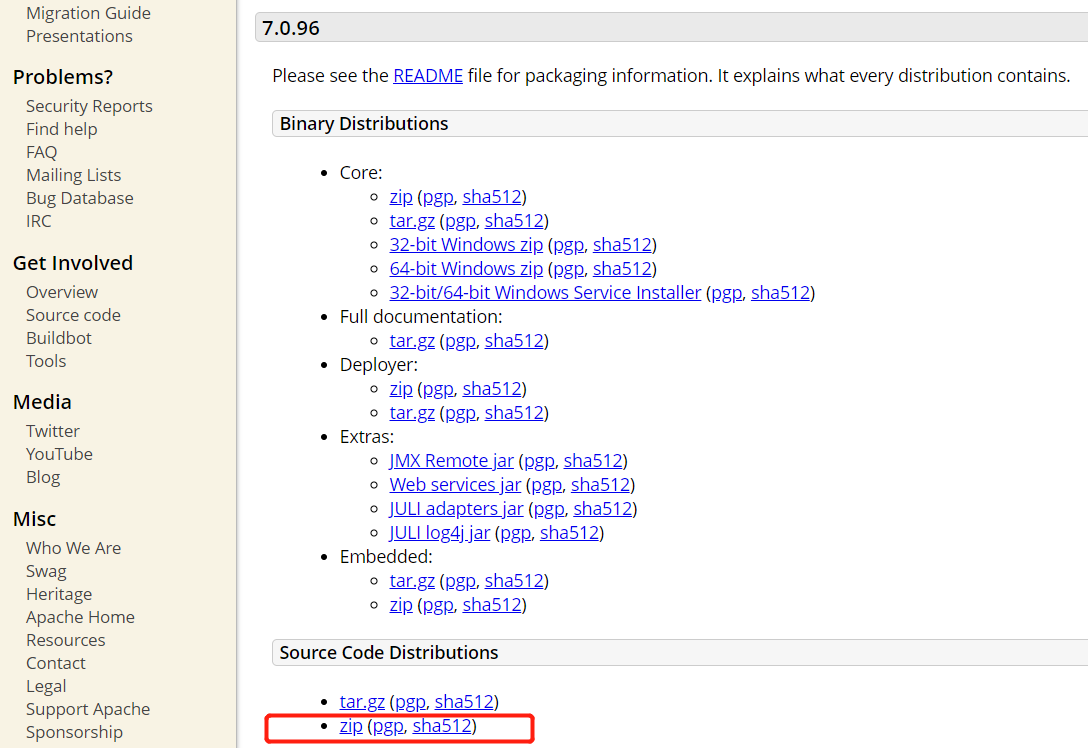
官网直接下载源码
http://tomcat.apache.org/download-70.cgi
源码导入到Eclipse中
第1步:Eclipse中新建一个Java Project,例如名称可以是Tomcat-Src
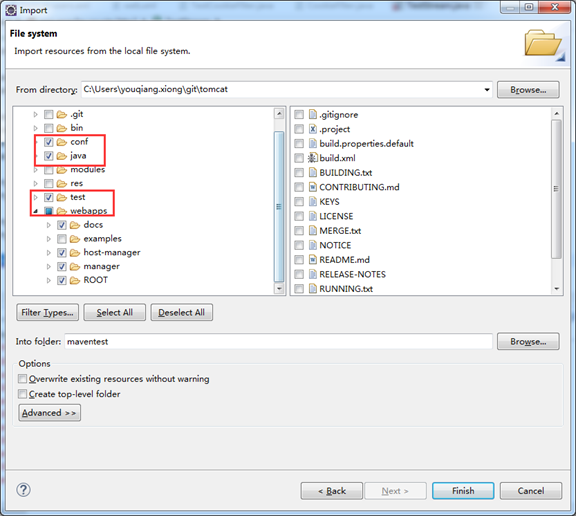
第2步:在工程上点击右键=>Import=>General=>File System,点击Next按钮。
第3步:点击Browser按钮,找到tomcat源码解压路径,勾选java、test、conf和webapps目录(注意不需要勾选examples目录),点击Finish按钮。
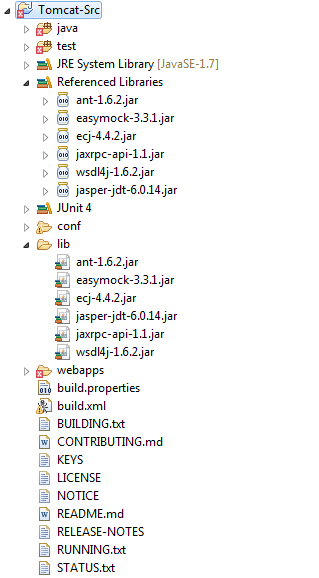
第4步:在java和test目录上点击右键=>Build Path=>Use As Source Folder將这两个目录设为源码目录。同时可以删除工程中原有的src目录了。
第5步:解决导入后工程中出现的编译错误,一般都是由于缺少某些jar导致
主要导入以下几个jar饱
ant.jar
ecj-4.4.2.jar
jaxrpc.jar
wsdl4j-1.5.2.jar
easymock-3.5.1.jar
在工程中新建一个lib目录,將这些jar包放到该目录下,同时添加到build path中。
apache tomcat采用junit作为单元测试工具,我们需要为工程添加Junit支持,在工程上点击右键=>Properties=>Java build path。
点击Add Library按钮,选择Junit4即可。
此时test包中的TestCookieFilter类会报CookieFilter编译异常,这是因为缺少CookieFilter这个类导致,经过一番查找总算找到了CookieFilter源码如下所示:
/* * Licensed to the Apache Software Foundation (ASF) under one or more * contributor license agreements. See the NOTICE file distributed with * this work for additional information regarding copyright ownership. * The ASF licenses this file to You under the Apache License, Version 2.0 * (the "License"); you may not use this file except in compliance with * the License. You may obtain a copy of the License at * * http://www.apache.org/licenses/LICENSE-2.0 * * Unless required by applicable law or agreed to in writing, software * distributed under the License is distributed on an "AS IS" BASIS, * WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. * See the License for the specific language governing permissions and * limitations under the License. */ package util; import java.util.Locale; import java.util.StringTokenizer; /** * Processes a cookie header and attempts to obfuscate any cookie values that * represent session IDs from other web applications. Since session cookie names * are configurable, as are session ID lengths, this filter is not expected to * be 100% effective. * * It is required that the examples web application is removed in security * conscious environments as documented in the Security How-To. This filter is * intended to reduce the impact of failing to follow that advice. A failure by * this filter to obfuscate a session ID or similar value is not a security * vulnerability. In such instances the vulnerability is the failure to remove * the examples web application. */ public class CookieFilter { private static final String OBFUSCATED = "[obfuscated]"; private CookieFilter() { // Hide default constructor } public static String filter(String cookieHeader, String sessionId) { StringBuilder sb = new StringBuilder(cookieHeader.length()); // Cookie name value pairs are ';' separated. // Session IDs don't use ; in the value so don't worry about quoted // values that contain ; StringTokenizer st = new StringTokenizer(cookieHeader, ";"); boolean first = true; while (st.hasMoreTokens()) { if (first) { first = false; } else { sb.append(';'); } sb.append(filterNameValuePair(st.nextToken(), sessionId)); } return sb.toString(); } private static String filterNameValuePair(String input, String sessionId) { int i = input.indexOf('='); if (i == -1) { return input; } String name = input.substring(0, i); String value = input.substring(i + 1, input.length()); return name + "=" + filter(name, value, sessionId); } public static String filter(String cookieName, String cookieValue, String sessionId) { if (cookieName.toLowerCase(Locale.ENGLISH).contains("jsessionid") && (sessionId == null || !cookieValue.contains(sessionId))) { cookieValue = OBFUSCATED; } return cookieValue; } }
此时仍有部分error,但不影响调试
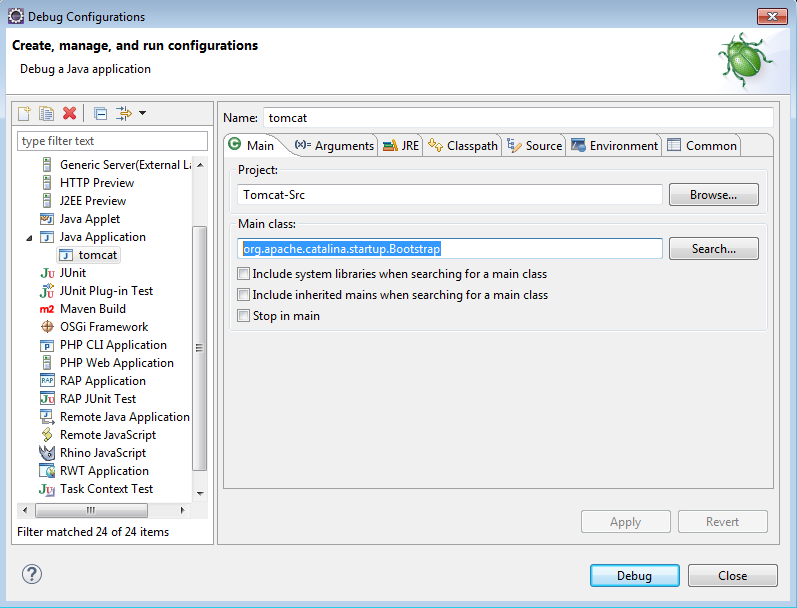
设置Debug Configuration,设定程序入口,开始调试!
————————————————
原文链接:https://blog.csdn.net/xiongyouqiang/article/details/78941077


 浙公网安备 33010602011771号
浙公网安备 33010602011771号