SSHD 服务停用不安全的 Arcfour Cipher
今天帮忙处理一个漏洞,安全检测原文描述为:
引擎检测到远程SSH服务器配置为使用Arcfour流密码或根本不使用密码。由于弱密码的问题,RFC 4253建议不要使用Arcfour。
很少见,以前没见过,不知道是不是新的
查阅了相关资料,是加密算法问题
查询指定目标主机sshd支持的加密算法:encryption_algorithms
zhangwei@zhangwei:~$ nmap --script "ssh2*" 192.168.1.1
Starting Nmap 7.60 ( https://nmap.org ) at 2021-02-03 15:36 CST
Nmap scan report for bogon (192.168.1.1)
Host is up (0.039s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
| ssh2-enum-algos:
| kex_algorithms: (4)
| diffie-hellman-group-exchange-sha256
| diffie-hellman-group-exchange-sha1
| diffie-hellman-group14-sha1
| diffie-hellman-group1-sha1
| server_host_key_algorithms: (2)
| ssh-rsa
| ssh-dss
| encryption_algorithms: (13)
| aes128-ctr
| aes192-ctr
| aes256-ctr
| arcfour256
| diffie-hellman-group-exchange-sha256
| diffie-hellman-group-exchange-sha1
| diffie-hellman-group14-sha1
| diffie-hellman-group1-sha1
| server_host_key_algorithms: (2)
| ssh-rsa
| ssh-dss
| encryption_algorithms: (13)
| aes128-ctr
| aes192-ctr
| aes256-ctr
| arcfour256
| arcfour128
| aes128-cbc
| 3des-cbc
| blowfish-cbc
| cast128-cbc
| aes192-cbc
| aes256-cbc
| arcfour
| aes128-cbc
| 3des-cbc
| blowfish-cbc
| cast128-cbc
| aes192-cbc
| aes256-cbc
| arcfour
| rijndael-cbc@lysator.liu.se
| mac_algorithms: (9)
| hmac-md5
| hmac-sha1
| umac-64@openssh.com
| hmac-sha2-256
| hmac-sha2-512
| hmac-ripemd160
| hmac-ripemd160@openssh.com
| hmac-sha1-96
| hmac-md5-96
| compression_algorithms: (2)
| none
|_ zlib@openssh.com
23/tcp filtered telnet
Nmap done: 1 IP address (1 host up) scanned in 2.06 seconds
其中包含了被认为不安全的 arcfour,arcfour-128,arcfour-256
gg了一下加密算法可以通过Ciphers执行,而sshd_config中默认是没有相关配置的。所以直接问man吧。
man 5 sshd_config
检索到下列内容
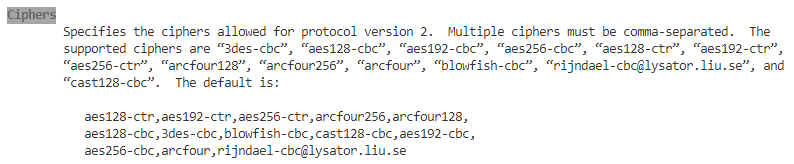
把 arcfour 相关的几个拎出来删除,形成新的配置,追加到 /etc/ssh/sshd_config 中
Ciphers 3des-cbc,aes128-cbc,aes192-cbc,aes256-cbc,aes128-ctr,aes192-ctr,aes256-ctr,blowfish-cbc,rijndael-cbc@lysator.liu.se,cast128-cbc
在 service sshd restart 后,通过 nmap 工具再次查询。嗯,没有了。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号