x86汇编指令(push,pop,call,ret)
举例这些指令做了什么?
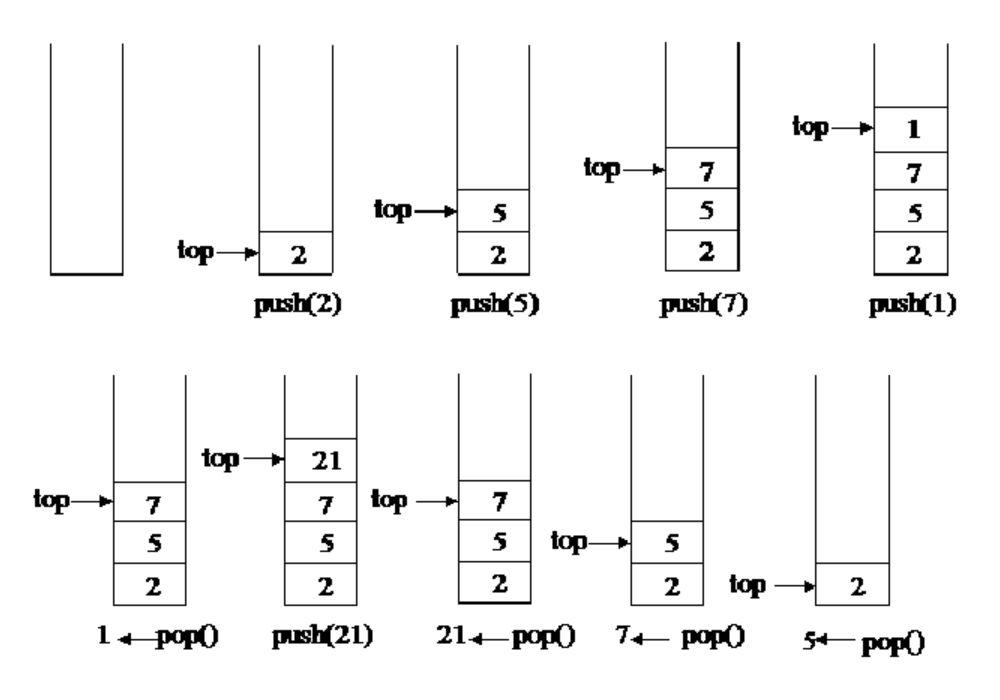
1.push指令
- pushl %eax
将eax数值压入栈中,可分解为: - subl $4, %esp ——> esp = esp - 4
- movl %eax, (%esp) ——> *(int32_t *)esp = eax
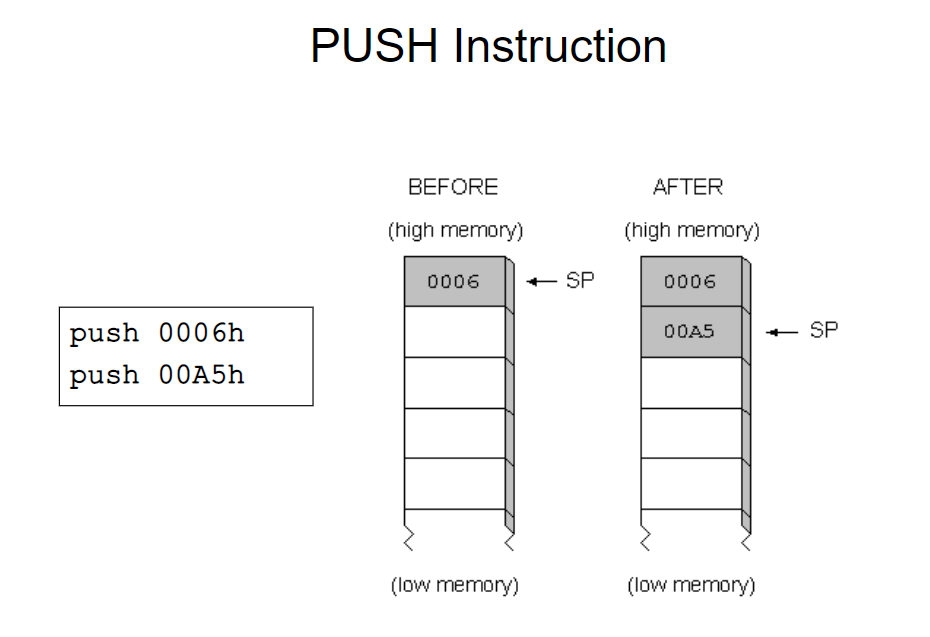
2.popl指令
- pop %eax
将eax数值弹出栈,可分解为: - movl (%esp), %eax ——> eax = *(int32_t *)esp
- addl $4, %esp ——> esp = esp + 4
3.call指令
- call 0x12345
调用0x12345这个地址,可分解为: - pushl %eip ——> 将cpu下一条要执行的指令压入栈中
- movl $0x12345, %eip ——> eip = 0x12345
注意:CPU下一条指令将会从地址0x12345中取。
4.ret指令
- ret 返回call之前的地址,可分解为:
- popl %eip ——> 将call压入栈的指令弹出赋给eip
参考链接:03_x86汇编指令二(push,pop,call,ret)_weixin_39247141的博客-CSDN博客
https://blog.csdn.net/weixin_39247141/article/details/105523427
学习视频:03_x86汇编指令二(push,pop,call,ret).
【关于push和pop,牢记住一点:ESP指向的栈顶top是数值】
Push will add an element to the top of the stack.
Pop will remove the top element of the stack.
PUSH instruction
POP instruction
x86栈
参考文档:
x86-64 下函数调用及栈帧原理 - 知乎 https://zhuanlan.zhihu.com/p/27339191
X86-64寄存器和栈帧_u013982161的专栏-CSDN博客 https://blog.csdn.net/u013982161/article/details/51347944
[翻译]X86-64下的栈帧布局简介-软件逆向-看雪论坛-安全社区|安全招聘|bbs.pediy.com https://bbs.pediy.com/thread-200575.htm
x86 程序内存堆栈模型 - 知乎 https://zhuanlan.zhihu.com/p/180318973
x86-x64寄存器及CallStack调用栈 - tongyishu - 博客园 https://www.cnblogs.com/tongyishu/p/11679829.html
x86汇编函数调用参数传递规则 - 繁荣3000的个人页面-zengfr - OSCHINA - 中文开源技术交流社区 https://my.oschina.net/zengfr/blog/4268091
The x86 microprocessor Assembly language programming - ppt download https://slideplayer.com/slide/14253692/
Kip Irvine: Assembly Language for Intel-Based Computers Overview Stack Operations (PUSH and POP) Procedures Procedure Parameters Software Interrupts MS-DOS. - ppt download https://slideplayer.com/slide/5069076/
Assembly language | the stack https://greysec.net/showthread.php?tid=2008&pid=8029



