tls签名
openssl genrsa -out ca.key 4096
openssl req -new -x509 -days 36500 -subj "/C=CN/ST=Beijing/L=Beijing/O=Qianxin/OU=Zion/CN=QAX-ATS4-CA" -key ca.key -out ca.crt
if [ ! -e "tikv.pem" ] && [ ! -e "tikv.crt" ]; then
openssl genrsa -out tikv.pem 2048
openssl req -new -key tikv.pem -out tikv.csr -subj "/C=CN/ST=Beijing/L=Beijing/O=Qianxin/OU=Zion/CN=tikv-server" -config openssl.cnf
openssl x509 -req -days 365 -CA ca.crt -CAkey ca.key -CAcreateserial -in tikv.csr -out tikv.crt -extensions v3_req -extfile openssl.cnf
fi
if [ ! -e "pd.pem" ] && [ ! -e "pd.crt" ]; then
openssl genrsa -out pd.pem 2048
openssl req -new -key pd.pem -out pd.csr -subj "/C=CN/ST=Beijing/L=Beijing/O=Qianxin/OU=Zion/CN=pd-server" -config openssl.cnf
openssl x509 -req -days 365 -CA ca.crt -CAkey ca.key -CAcreateserial -in pd.csr -out pd.crt -extensions v3_req -extfile openssl.cnf
fi
if [ ! -e "blackbox_exporter.pem" ] && [ ! -e "blackbox_exporter.crt" ]; then
openssl genrsa -out blackbox_exporter.pem 2048
openssl req -new -key blackbox_exporter.pem -out blackbox_exporter.csr -subj "/C=CN/ST=Beijing/L=Beijing/O=Qianxin/OU=Zion/CN=monitor" -config openssl.cnf
openssl x509 -req -days 365 -CA ca.crt -CAkey ca.key -CAcreateserial -in blackbox_exporter.csr -out blackbox_exporter.crt -extensions v3_req -extfile openssl.cnf
fi
if [ ! -e "grafana.pem" ] && [ ! -e "grafana.crt" ]; then
openssl genrsa -out grafana.pem 2048
openssl req -new -key grafana.pem -out grafana.csr -subj "/C=CN/ST=Beijing/L=Beijing/O=Qianxin/OU=Zion/CN=grafana-server" -config openssl.cnf
openssl x509 -req -days 365 -CA ca.crt -CAkey ca.key -CAcreateserial -in grafana.csr -out grafana.crt -extensions v3_req -extfile openssl.cnf
fi
if [ ! -e "prometheus.pem" ] && [ ! -e "prometheus.crt" ]; then
openssl genrsa -out prometheus.pem 2048
openssl req -new -key prometheus.pem -out prometheus.csr -subj "/C=CN/ST=Beijing/L=Beijing/O=Qianxin/OU=Zion/CN=prometheus-server" -config openssl.cnf
openssl x509 -req -days 365 -CA ca.crt -CAkey ca.key -CAcreateserial -in prometheus.csr -out prometheus.crt -extensions v3_req -extfile openssl.cnf
fi
openssl genrsa -out client.pem 2048
openssl req -new -key client.pem -out client.csr -subj "/C=CN/ST=Beijing/L=Beijing/O=Qianxin/OU=Zion/CN=tikv-client"
openssl x509 -req -days 36500 -CA ca.crt -CAkey ca.key -CAcreateserial -in client.csr -out client.crt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 | [ alt_names ]DNS.1 = * {% for host in ansible_play_hosts_all %}DNS.{{loop.index+1}} = {{hostvars[host]['ansible_nodename']}}{% endfor %}{% for host in ansible_play_hosts_all %}{% if isuseipv6 is defined and isuseipv6|bool %}IP.{{loop.index}} = {{(hostvars[host]['ansible_'+interface]['ipv6'] | selectattr('scope', 'equalto', 'global') | list | first).address}} {% else %}{% if hostvars[host]['ansible_facts']['default_ipv4'] is defined %}IP.{{loop.index}} = {{hostvars[host]['ansible_facts']['default_ipv4']['address']}} {% else %}IP.{{loop.index}} = {{hostvars[host]['ansible_default_ipv4']['address']}} {% endif %}{% endif %}{% if loop.last %}IP.{{loop.index+1}} = 127.0.0.1{% set dassl_last=loop.index %}{% if global_vip_list != None and global_vip_list != '' %}{%for item in global_vip_list.split(',') %}IP.{{loop.index+dassl_last+1}}={{item}}{% endfor %}{% endif %}{% endif %}{% endfor %}[ v3_ext ]keyUsage=critical, digitalSignature, keyEncipherment, dataEncipherment, keyAgreementextendedKeyUsage=TLS Web Server Authentication, TLS Web Client AuthenticationsubjectKeyIdentifier=hashauthorityKeyIdentifier=keyid, issuer:alwayssubjectAltName=@alt_names |
1 2 3 4 5 6 | openssl genrsa -out 127.0.0.1.key 2048openssl req -new -key 127.0.0.1.key -out 127.0.0.1.csr -subj "/C=CN/ST=Beijing/L=Beijing/O=Qianxin/OU=Zion/CN=127.0.0.1"openssl x509 -req -days 36500 -CA {{da_ssl_oid}}.crt -CAkey {{da_ssl_oid}}.key -CAcreateserial -in 127.0.0.1.csr -out public.crt \ -extensions v3_ext -extfile openssl.conf |
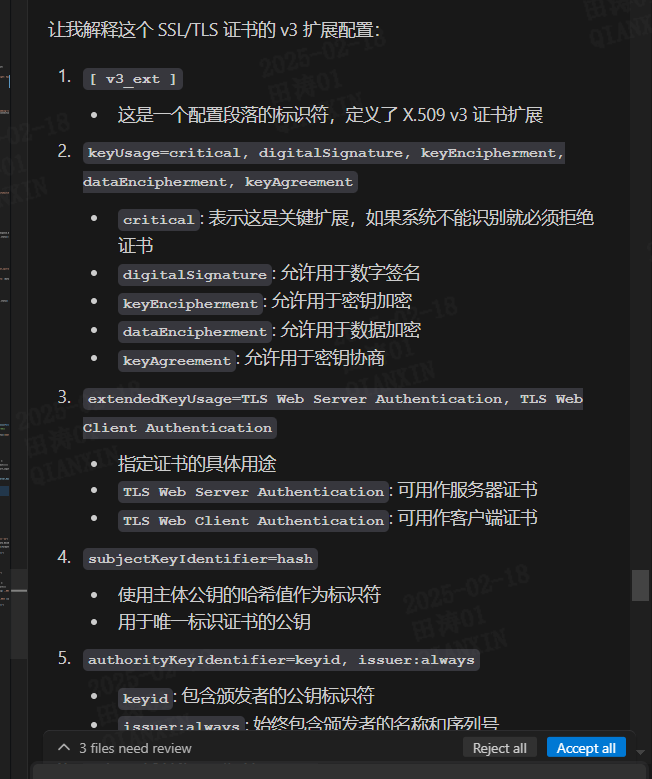
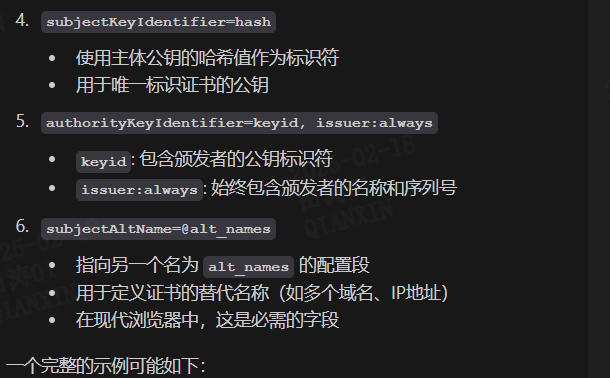
1 2 3 4 5 6 7 8 9 10 11 | [ v3_ext ]keyUsage=critical, digitalSignature, keyEncipherment, dataEncipherment, keyAgreementextendedKeyUsage=TLS Web Server Authentication, TLS Web Client AuthenticationsubjectKeyIdentifier=hashauthorityKeyIdentifier=keyid, issuer:alwayssubjectAltName=@alt_names[ alt_names ]DNS.1 = example.comDNS.2 = *.example.comIP.1 = 192.168.1.1 |





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· AI技术革命,工作效率10个最佳AI工具