HDP 08.Hue4.5 LDAP 配置
1、修改 core-site.xml 配置文件,添加如下参数:
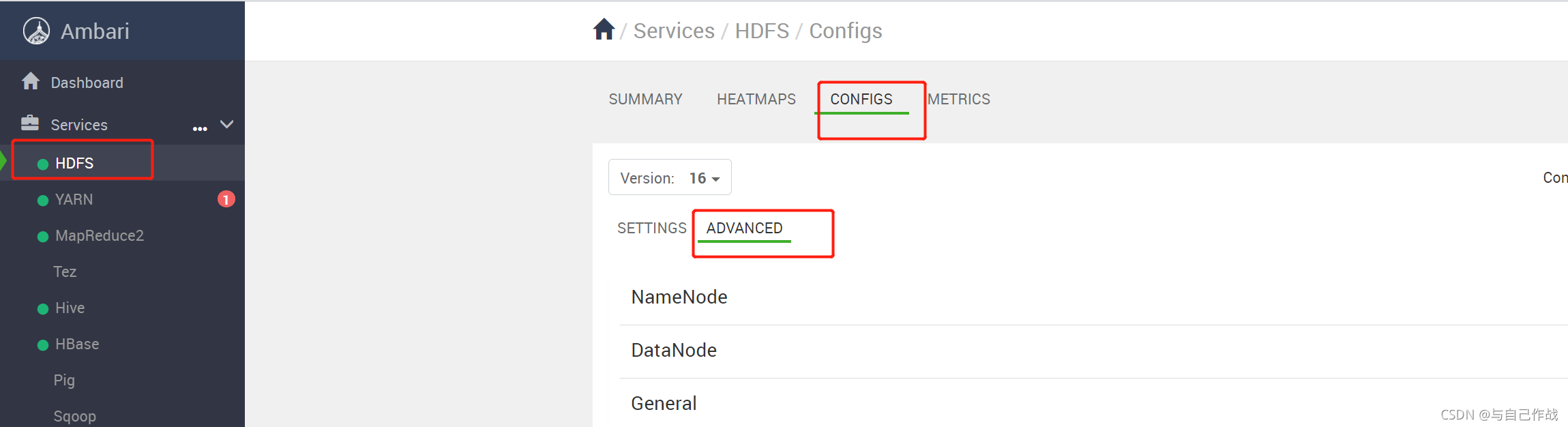
在 Ambari 控制台依次点击 HDFS->CONFIGS->ADVANCED->"Custom core-site"->"Add Property ..." ,
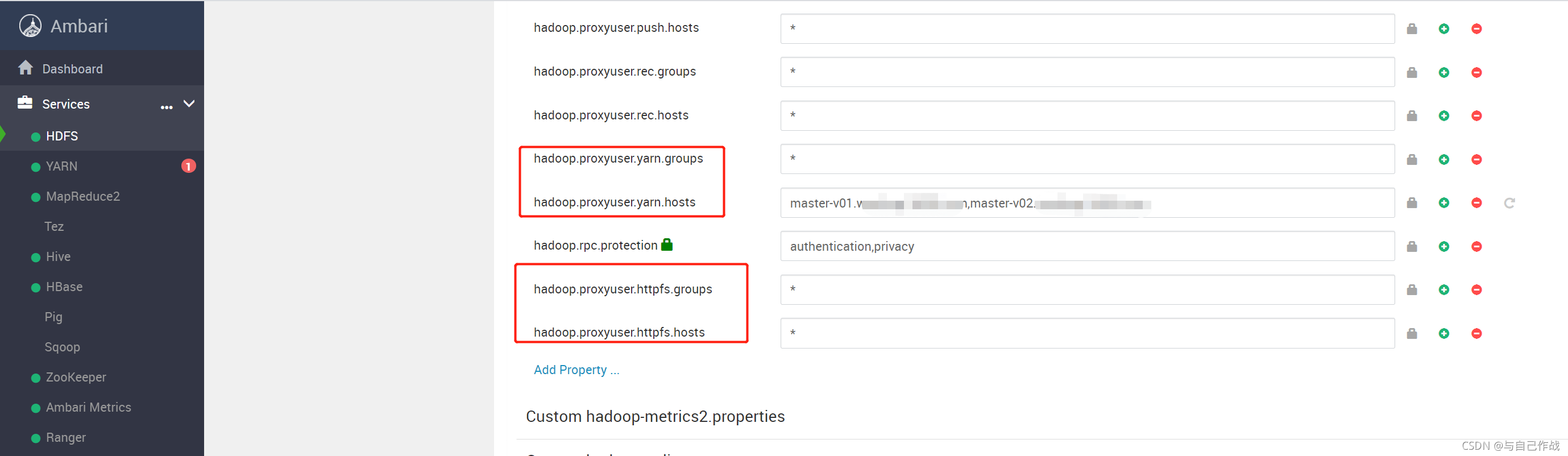
然后在弹出的 "Add Property" 窗口添加如下 4 个参数 ( 后面两个参数 hadoop.proxyuser.hue.groups,hadoop.proxyuser.hue.hosts 可能之前创建 hue 帐号的时候配置了 )
hadoop.proxyuser.httpfs.groups=*
hadoop.proxyuser.httpfs.hosts=*
hadoop.proxyuser.hue.groups=*
hadoop.proxyuser.hue.hosts=*
2、在 client-v01 服务器安装 hadoop-httpfs包
yum -y install hadoop-httpfs
3、创建并编辑 /etc/hadoop-httpfs/conf/httpfs-site.xml 文件
<configuration>
<property>
<name>httpfs.proxyuser.httpfs.hosts</name>
<value>*</value>
</property>
<property>
<name>httpfs.proxyuser.httpfs.groups</name>
<value>*</value>
</property>
<property>
<name>httpfs.hadoop.config.dir</name>
<value>/etc/hadoop/conf</value>
</property>
<property>
<name>httpfs.http.port</name>
<value>14000</value>
</property>
<property>
<name>httpfs.http.host</name>
<value>client-v01.tianlingqun.com</value>
</property>
<property>
<name>httpfs.authentication.type</name>
<value>kerberos</value>
</property>
<property>
<name>httpfs.hadoop.authentication.type</name>
<value>kerberos</value>
</property>
<property>
<name>httpfs.authentication.kerberos.principal</name>
<value>HTTP/client-v01.tianlingqun.com@tianlingqun.COM</value>
</property>
<property>
<name>httpfs.authentication.kerberos.keytab</name>
<value>/etc/security/keytabs/spnego.service.keytab</value>
</property>
<property>
<name>httpfs.hadoop.authentication.kerberos.principal</name>
<value>httpfs/client-v01.tianlingqun.com@tianlingqun.COM</value>
</property>
<property>
<name>httpfs.hadoop.authentication.kerberos.keytab</name>
<value>/etc/security/keytabs/httpfs.service.keytab</value>
</property>
<property>
<name>httpfs.authentication.kerberos.name.rules</name>
<value>
RULE:[1:$1@$0](ambari-qa-wfcluster@tianlingqun.COM)s/.*/ambari-qa/
RULE:[1:$1@$0](hbase-wfcluster@tianlingqun.COM)s/.*/hbase/
RULE:[1:$1@$0](hdfs-wfcluster@tianlingqun.COM)s/.*/hdfs/
RULE:[1:$1@$0](spark-wfcluster@tianlingqun.COM)s/.*/spark/
RULE:[1:$1@$0](superset-wfcluster@tianlingqun.COM)s/.*/superset/
RULE:[1:$1@$0](yarn-ats-wfcluster@tianlingqun.COM)s/.*/yarn-ats/
RULE:[1:$1@$0](.*@tianlingqun.COM)s/@.*//
RULE:[2:$1@$0](amshbase@tianlingqun.COM)s/.*/ams/
RULE:[2:$1@$0](amsmon@tianlingqun.COM)s/.*/ams/
RULE:[2:$1@$0](amszk@tianlingqun.COM)s/.*/ams/
RULE:[2:$1@$0](dn@tianlingqun.COM)s/.*/hdfs/
RULE:[2:$1@$0](hbase@tianlingqun.COM)s/.*/hbase/
RULE:[2:$1@$0](hive@tianlingqun.COM)s/.*/hive/
RULE:[2:$1@$0](jhs@tianlingqun.COM)s/.*/mapred/
RULE:[2:$1@$0](jn@tianlingqun.COM)s/.*/hdfs/
RULE:[2:$1@$0](nm@tianlingqun.COM)s/.*/yarn/
RULE:[2:$1@$0](nn@tianlingqun.COM)s/.*/hdfs/
RULE:[2:$1@$0](rangeradmin@tianlingqun.COM)s/.*/ranger/
RULE:[2:$1@$0](rangerkms@tianlingqun.COM)s/.*/keyadmin/
RULE:[2:$1@$0](rangertagsync@tianlingqun.COM)s/.*/rangertagsync/
RULE:[2:$1@$0](rangerusersync@tianlingqun.COM)s/.*/rangerusersync/
RULE:[2:$1@$0](rm@tianlingqun.COM)s/.*/yarn/
RULE:[2:$1@$0](spark@tianlingqun.COM)s/.*/spark/
RULE:[2:$1@$0](yarn@tianlingqun.COM)s/.*/yarn/
RULE:[2:$1@$0](yarn-ats-hbase@tianlingqun.COM)s/.*/yarn-ats/
DEFAULT
</value>
</property>
</configuration>
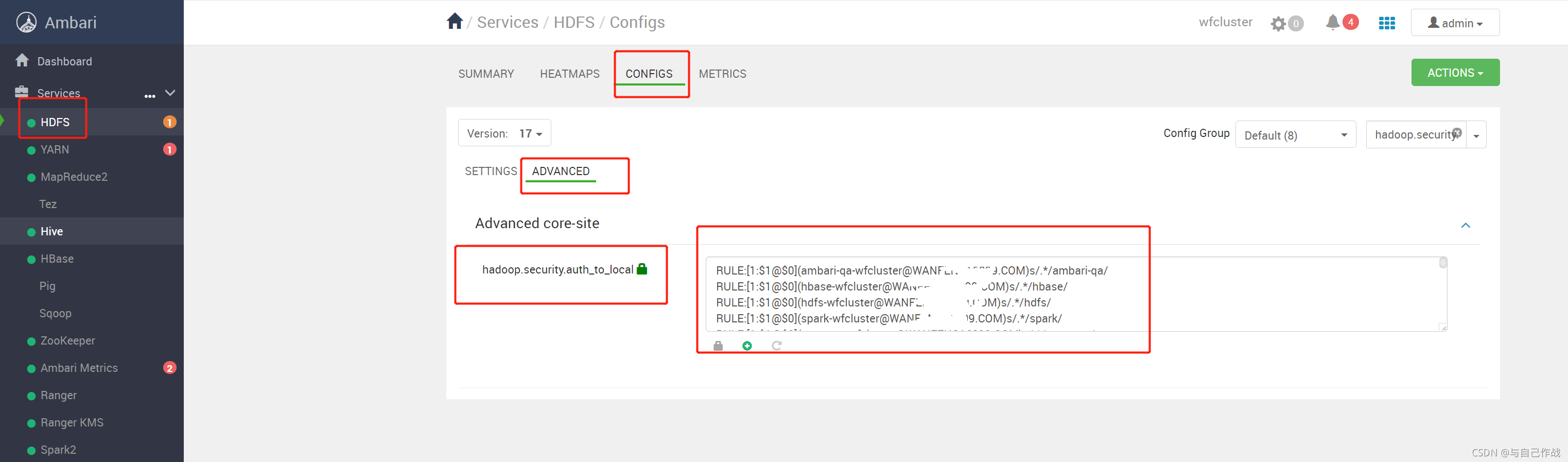
注意:上面文件中的 httpfs.authentication.kerberos.name.rules 参数值就是 HDFS 的 core-site.xml 配置文件中hadoop.security.auth_to_local 参数值。
4、添加 httpfs相关服务(可以直接在client-v01服务器执行)
kinit admin
Wfipaadmin123456
ipa service-add httpfs/client-v01.tianlingqun.com
ipa-getkeytab -s ipa-v01.tianlingqun.com -p HTTP/client-v01.tianlingqun.com \
-k /etc/security/keytabs/spnego.service.keytab
ipa-getkeytab -s ipa-v01.tianlingqun.com -p httpfs/client-v01.tianlingqun.com \
-k /etc/security/keytabs/httpfs.service.keytab
5、创建相关目录:
mkdir -p /var/log/hadoop/httpfs
mkdir -p /var/run/hadoop/httpfs
chown -R httpfs:httpfs /var/log/hadoop/httpfs
chown -R httpfs:httpfs /var/run/hadoop/httpfs
touch /usr/hdp/3.1.4.0-315/hadoop/conf/httpfs-signature.secret
6、启动方法:
ln -s /usr/hdp/3.1.4.0-315/hadoop-httpfs/etc/rc.d/init.d/hadoop-httpfs /etc/rc.d/init.d/hadoop-httpfs
必须重启服务器后执行下面命令:
systemctl start hadoop-httpfs.service
netstat -anlp |grep 14000
注意:如果需要重启的话,先 kill 原来的进程
也可以通过执行如下命令启的(如果上面命令启的失败的话)
touch /etc/hadoop-httpfs/conf/httpfs-signature.secret
cd /usr/hdp/3.1.4.0-315/hadoop-httpfs/sbin
nohup ./httpfs.sh run &
netstat -anlp |grep 14000
7、执行如下命令,添加 hue 相关服务(可以直接在client-v01服务器执行)
kinit admin
ipa service-add hue/client-v01.tianlingqun.com
ipa-getkeytab -s ipa-v01.tianlingqun.com -p hue/client-v01.tianlingqun.com \
-k /etc/security/keytabs/hue.service.keytab
chown hue:hue /etc/security/keytabs/hue.service.keytab
chmod 400 /etc/security/keytabs/hue.service.keytab
8、修改 /usr/local/hue/desktop/conf/hue.ini 文件,配置 Hue LDAP, Hive 等相关参数
9、以 hue 用户尝试启动 Hue服务创建 /var/run/hue 目录,用于缓存 kerberos 票据
mkdir -p /var/run/hue/;
chown hue:hue /var/run/hue/;
10、以 hue 用户尝试启动 Hue服务
killall -u hue; # 该命令是删除 hue 用户的所有进程,如果你的 hue 用户还有其他服务请小心操作;先 kill hue 相关进程,方便“重启”
su - hue
cd /usr/local/hue/desktop/;
rm -rf /usr/local/hue/logs/*;
rm -rf ./nohup.out;
nohup /usr/local/hue/build/env/bin/supervisor &
启动成功后,检查 /usr/local/hue/logs 里的日志是否有报错
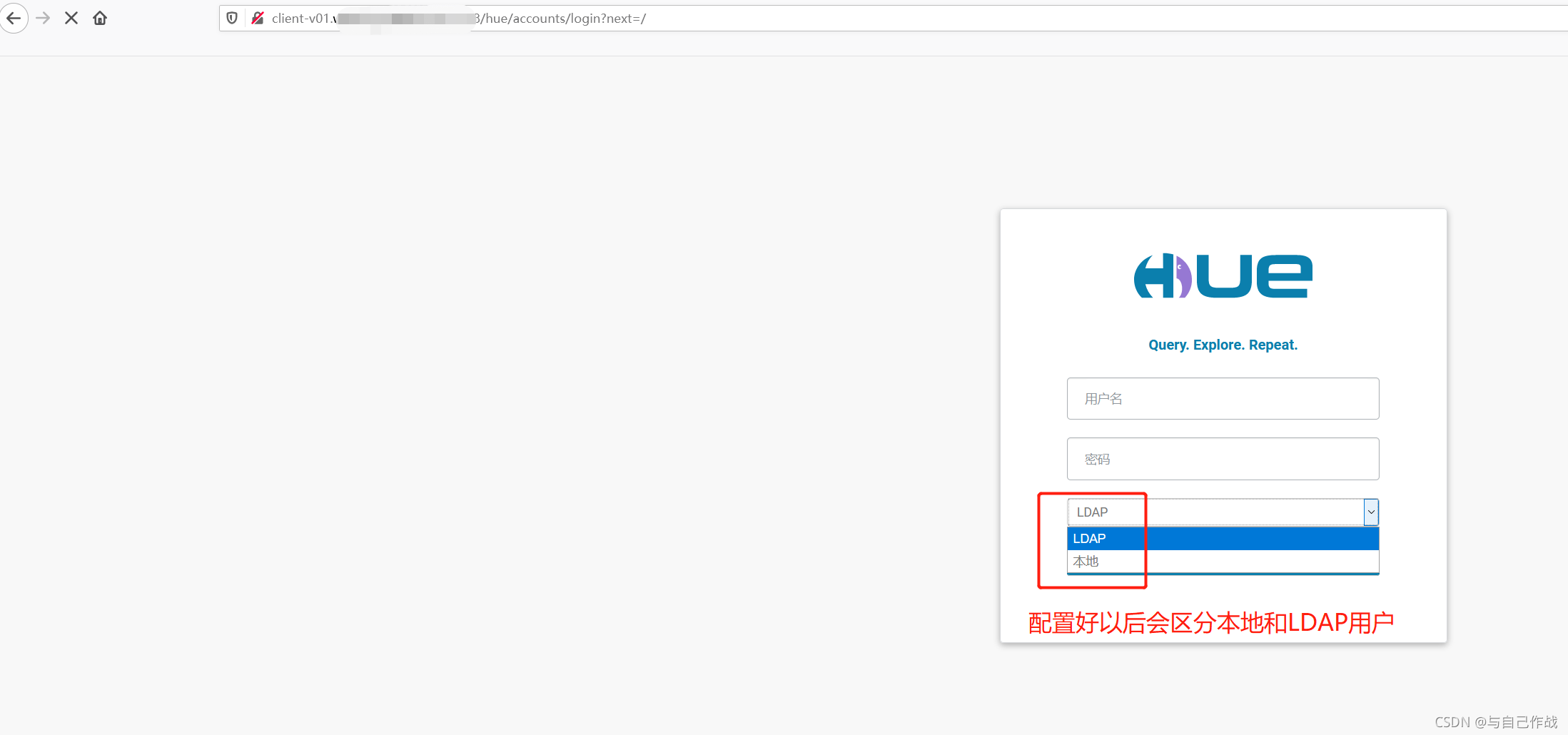
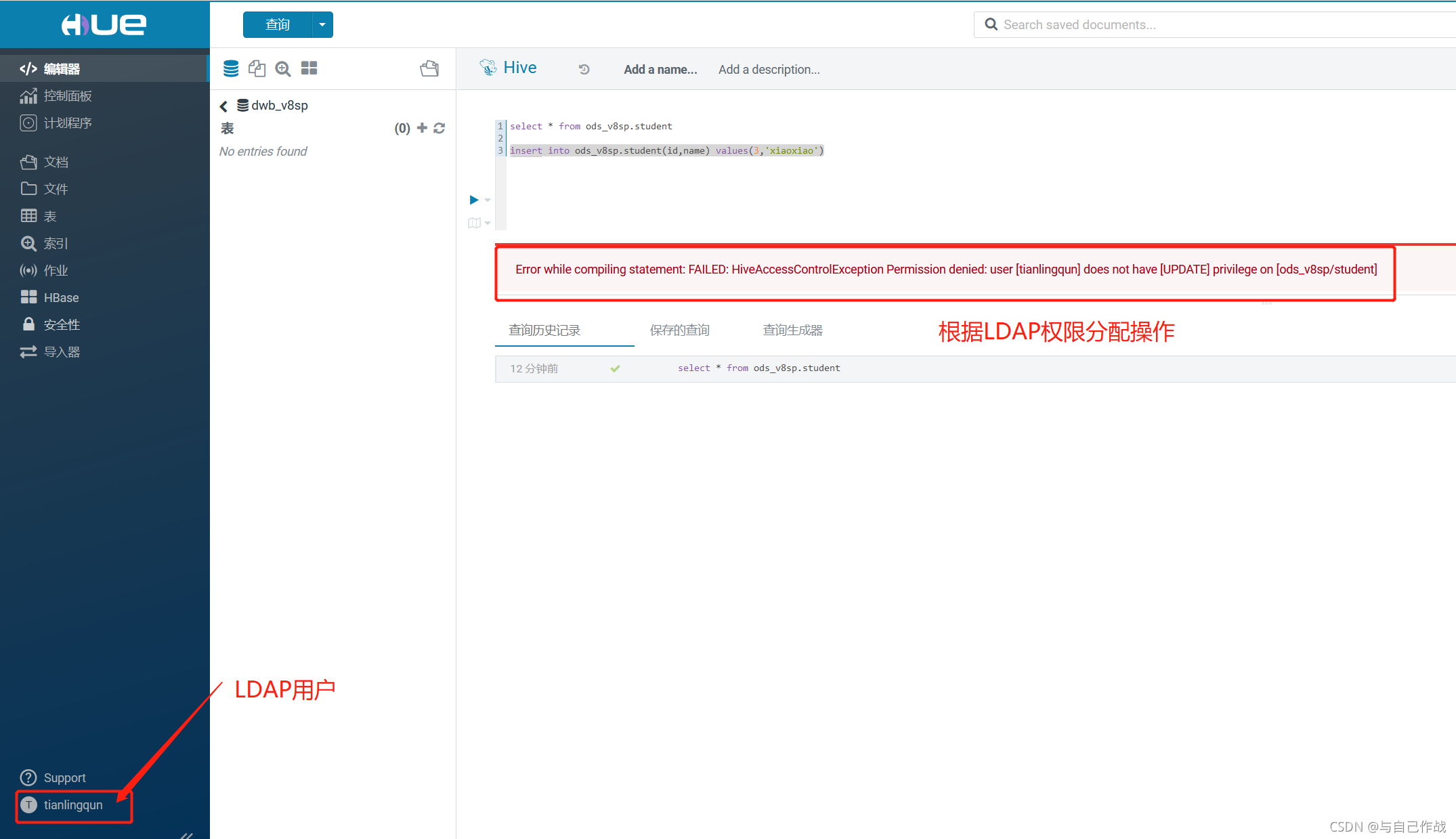
11、我们尝试登陆 Hue Web UI,链接是:http://client-v01.tianlingqun.com:8888/ 输入 g_hue 组的 LDAP 帐号即可登陆查询





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· SQL Server 2025 AI相关能力初探
· AI编程工具终极对决:字节Trae VS Cursor,谁才是开发者新宠?
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南