《Windows Azure Platform 系列文章目录》
AKS支持使用Azure AD账户进行RBAC访问控制。
主要步骤有:
第一步:设置AKS集群允许Azure AD RBAC认证
第二步:创建Azure AD用户组和用户
第三步:创建namespace,创建Role和Role Binding
第一步:设置AKS集群允许Azure AD RBAC认证
1.首先,我们需要把AKS设置为允许使用Azure AD认证,如下图:
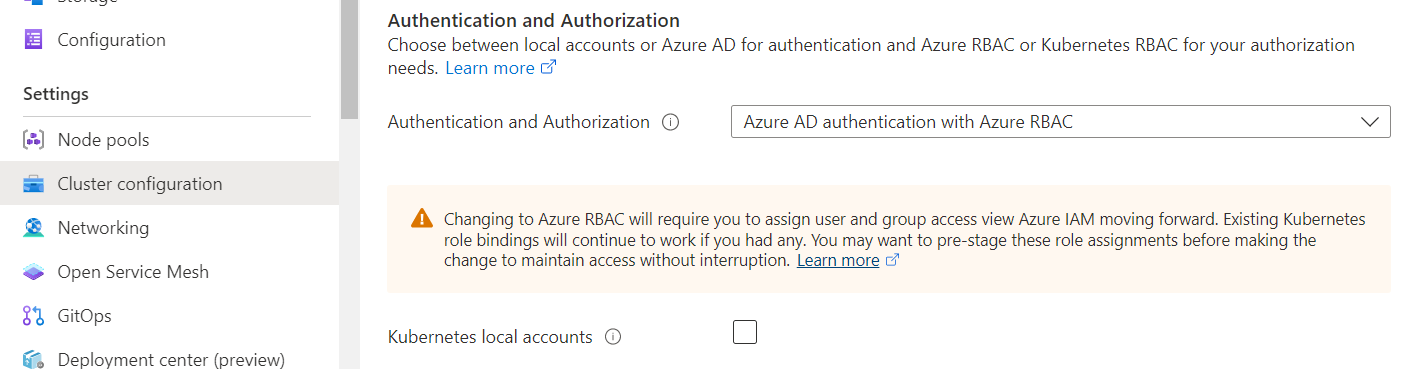
第二步:创建Azure AD用户组和用户
1.我们以Azure AD管理员身份,创建用户组和用户
AKS_ID=$(az aks show \ --resource-group leizha-rg \ --name aks01 \ --query id -o tsv)
2.先创建用户组web group
webgroup_id=$(az ad group create --display-name webgroup --mail-nickname webgroup --query objectId -o tsv) #这里的webgroup_id显示为"076c2ac5-cf30-42e8-9c9d-7450fa48f4eb"
3.再创建web user,把该用户加入到上面创建的web group
#该用户名为:webuser@msftopenhack6889ops.onmicrosoft.com,注意这个账户和你环境的目录有关 webuser_id=$(az ad user create --display-name "web user" \ --user-principal-name "webuser@msftopenhack6889ops.onmicrosoft.com" \ --password "[该账户的密码]" \ --query objectId -o tsv) #这里的webuser_id为"6452c5e2-0baf-47b4-9b0c-d6f7d016a3a3"
4.把用户组(webgroup)权限设置为Azure Kubernetes Service Cluster User Role
az role assignment create \ --assignee $webgroup_id \ --role "Azure Kubernetes Service Cluster User Role" \ --scope $AKS_ID
5.把web User加入到web group里
az ad group member add --group webgroup --member-id $webuser_id
另外我们再创建api user和api group,具体的步骤略。需要记录好api group的object id
第三步:创建namespace,创建Role和Role Binding
1.我们以管理员身份,登录到AKS集群里
az aks get-credentials --resource-group leizha-rg --name aks01
2.创建2个namespace
kubectl create namespace web
kubectl create namespace api
3.准备4个Role
role-api.yaml,可以看到对于api命名空间有完全访问权限
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: api-full-access
namespace: api
rules:
- apiGroups: ["", "extensions", "apps"]
resources: ["services", "endpoints", "pods","deployments","replicasets"]
verbs: ["get", "list", "watch","update","patch", "delete","create"]
role-api-limited.yaml,可以看到对于api命名空间有只读权限
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: api-limited-access
namespace: api
rules:
- apiGroups: ["", "extensions", "apps"]
resources: ["services", "endpoints", "pods","deployments","replicasets"]
verbs: ["get", "list", "watch"]
role-web.yaml,可以看到对于web命名空间有完全访问权限
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: web-full-access
namespace: web
rules:
- apiGroups: ["", "extensions", "apps"]
resources: ["services", "endpoints", "pods","deployments","replicasets"]
verbs: ["get", "list", "watch","update","patch", "delete","create"]
role-web-limited.yaml,可以看到对于web命名空间有只读权限
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: web-limited-access
namespace: web
rules:
- apiGroups: ["", "extensions", "apps"]
resources: ["services", "endpoints", "pods","deployments","replicasets"]
verbs: ["get", "list", "watch"]
4.我们准备2个Role Binding
bind-role-api-dev-group.yaml,可以看到api group对于api 命名空间有完全访问权限(绑定的是api-full-access),对于web命名空间有只读权限(绑定的是web-limited-access)
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: api-group-access-1
namespace: api
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: api-full-access
subjects:
- kind: Group
namespace: api
name: 这里输入api group的objectid,注意不要带双引号
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: api-group-access-2
namespace: web
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: web-limited-access
subjects:
- kind: Group
namespace: web
name: 这里输入api group的objectid,注意不要带双引号
bind-role-web-dev-group.yaml,可以看到api group对于api 命名空间有只读访问权限(绑定的是api-limited-access),对于web命名空间有完全权限(绑定的是web-full-access)
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: web-group-access-1
namespace: web
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: web-full-access
subjects:
- kind: Group
namespace: web
name: 这里输入web group的object id,注意不要带双引号
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: web-group-access-2
namespace: api
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: api-limited-access
subjects:
- kind: Group
namespace: api
name: 这里输入web group的object id,注意不要带双引号
5.我们执行这个role binding
az aks get-credentials --resource-group leizha-rg --name aks01 --admin #设置4个Role kubectl apply -f role-api.yaml kubectl apply -f role-api-limited.yaml kubectl apply -f role-web.yaml kubectl apply -f role-web-limited.yaml
#绑定Role Binding kubectl apply -f bind-role-api-dev-group.yaml kubectl apply -f bind-role-web-dev-group.yaml
6.我们以web user用户登录:
az login
#在弹出的窗口中,输入用户名:webuser@msftopenhack6889ops.onmicrosoft.com和密码
az aks get-credentials --resource-group leizha-rg --name aks01 --overwrite-existing
我们执行访问所有namespace会遇到错误
kubectl get pods --all-namespaces


 浙公网安备 33010602011771号
浙公网安备 33010602011771号